Log Analytics allows us to generate alerts on the ingested data. It does so by running a pre-defined query composed of conditions on the incoming data. If it finds any records that fall within the ambit of the query, it generates an alert. Log Analytics provides a highly configurable environment for determining the conditions for generating alerts, time windows in which the query should return the records, time windows in which the query should be executed, and actions to be taken when the query returns results as alerts.
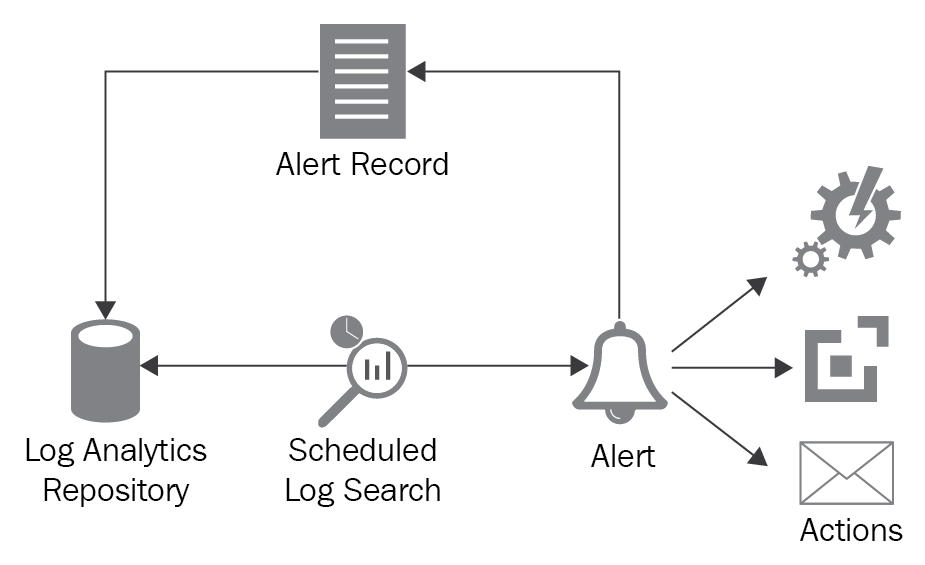
The first step in configuring an alert is to create a saved search. A saved search is simply a search query against Log Analytics, as shown below:

Save the query by providing a name for it. After saving the query, click on the Alert button from the Log Search menu. It provides the user an interface for defining and adding a new alert rule:

Within this single screen, all configurations related to an alert rule can be performed. You need to provide a name, description, severity, and the query to be executed as part of the rule evaluation within their respective fields.
The time window specifies the data interval in which the query should be executed. In the screenshot, whenever the rule is executed, it processes data from the last 15 minutes.
The schedule section helps you configure the frequency of rule execution. It answers the question, How frequently should the query run? In the previous screenshot, the rule is executed every 15 minutes. The time window should be more than the alert frequency. The alerts can be further configured based on the number of results found. It need not be that an alert is generated for every instance of data found based on the query. It can further be quantified to accumulate a certain quantity of results before raising the requests. The alerts can also be generated based on metric measurements. Additional configuration to suppress alerts can be done. You can create a time interval that should elapse before the action is executed. In this case, alerts are generated but the action is executed only after the configured interval has elapsed.
The Actions section allows us to configure things that should follow an alert. Generally, there should be a remedial and/or notification action. Log Analytics provides four different ways to create a new action. They can be combined in any way. An alert will execute any and all the following configured actions:
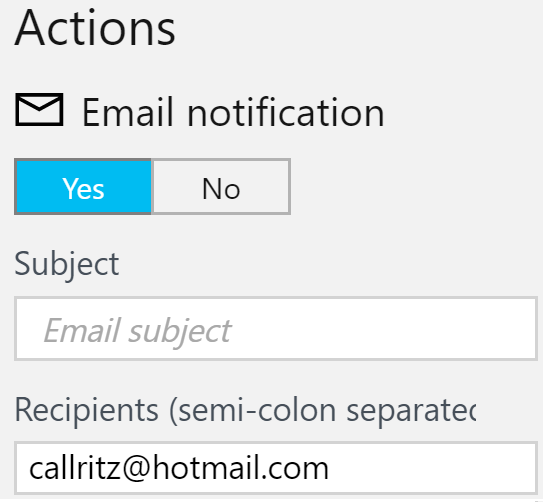
- Email notification: This is the simplest, and sends an email to the configured recipients:
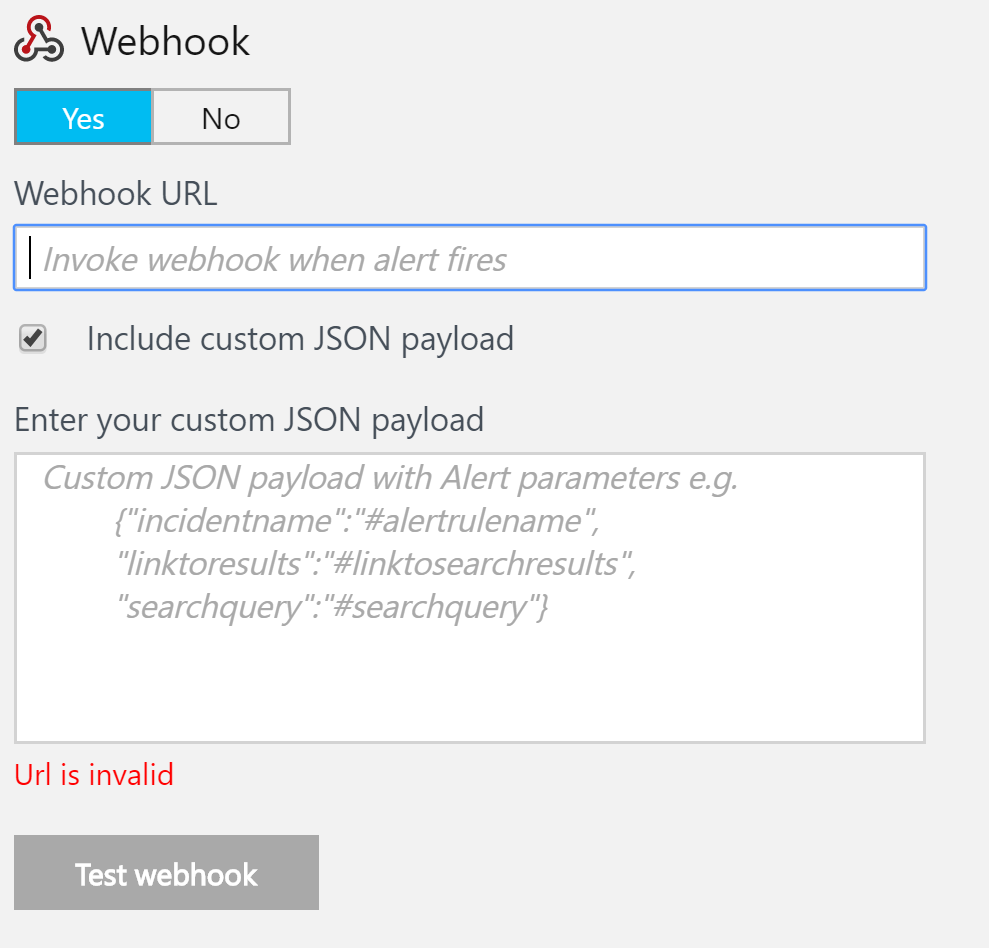
- Webhook: A webhook executes an arbitrary external process using a HTTP POST mechanism. For example, a REST API can be executed, or the Service Manager/ServiceNow APIs can be invoked to create a ticket:
- Runbooks: This action executes Azure Automation runbooks. In the next section, we will see the entire process of executing an Azure Automation runbook.
- ITSM actions: ITSM solutions should be provisioned before using this option. It helps with connecting and sending information to ITSM systems.