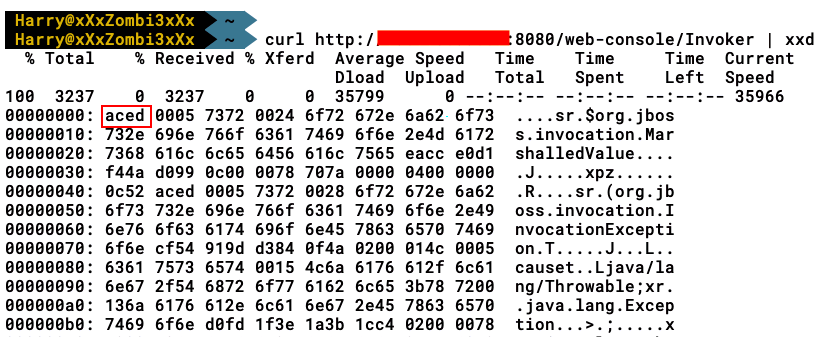
Another way of exploiting a JBoss AS instance is via the web console's Invoker method. Executing a curl command while requesting the /web-console/Invoker URI path will get us a response from the server with the 0xAC and 0xED hex code characters (aced) in the first 4 bytes of the file. We can see this at the beginning of any Java serialized object, as follows:
The Invoker servlet can be found in the web console or Invoker at http://example.com/web-console/Invoker. This can mostly be accessed without authentication. We can send a serialized post request to this Invoker to execute commands on the server.
Here's the breakdown of the bytes in the preceding screenshot:
- ac ed: STREAM_MAGIC specifies that this is a serialization protocol.
- 00 o5: STREAM_VERSION specifies the serialization version in use.
- 0x73: TC_OBJECT specifies that this is a new object.
- 0x72: TC_CLASSDESC specifies that this is a new class.
- 00 24: This specifies the length of the class name.
- {6F 72 67 2E 6A 62 6F 73 73 2E 69 6E 76 6F 63 61 74 69 6F 6E 2E 4D 61 72 73 68 61 6C 6C 65 64 56 61 6C 75 65} org.jboss. invocation.MarshalledValue: This specifies the class name.
- EA CC E0 D1 F4 4A D0 99: SerialVersionUID specifies the serial version identifier of this class.
- 0x0C: This specifies the tag number.
- 00 00: This specifies the number of fields in this class.
- 0x78: TC_ENDBLOCKDATA marks the end of block objects.
- 0x70: TC_NULL represents the fact that there are no more superclasses because we have reached the top of the class hierarchy.
- Exploitation via the web console using a third-party tool.
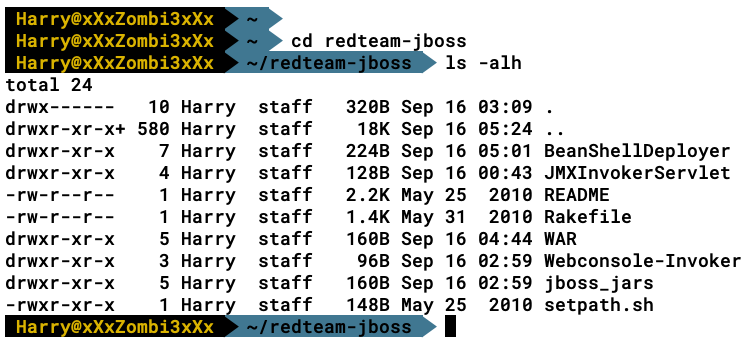
Before jumping into Metasploit's module, let's look at another set of scripts developed by RedTeam Pentesting. The archive can be downloaded from their website at https://www.redteam-pentesting.de/files/redteam-jboss.tar.gz.
The archive contains the following files:
- BeanShellDeployer/mkbeanshell.rb
- WAR/shell.jsp
- WAR/WEB-INF/web.xml
- Webconsole-Invoker/webconsole_invoker.rb
- JMXInvokerServlet/http_invoker.rb
- JMXInvokerServlet/jmxinvokerservlet.rb
- jboss_jars/console-mgr-classes.jar
- jboss_jars/jbossall-client.jar
- README
- setpath.sh
- Rakefile
The following screenshot shows the different scripts released by the team:
We can use this tool to create custom BSH scripts, deploy the BSH scripts via the web console Invoker, create a JMXInvokerServlet payload, and so on. Let's see how we can use this tool to create a BSH script.