HTTP verbs can also be fuzzed using Burp Suite Intruder by clicking the Intruder tab and opening the Positions sub-tab. Burp Suite will automatically mark any value matching the [parameter]=[value] format with the § payload marker. Anything within the payload marker will be considered a fuzz vector by Burp Suite. Burp Suite Intruder supports four attack types: Sniper, Battering Ram, Pitchfork, and Cluster Bomb. To learn more about the attack types, please refer to https://portswigger.net/burp/documentation/desktop/tools/intruder/positions.
Let's clear the fuzz vector position by clicking the Clear § button, as we can see in the following screenshot:
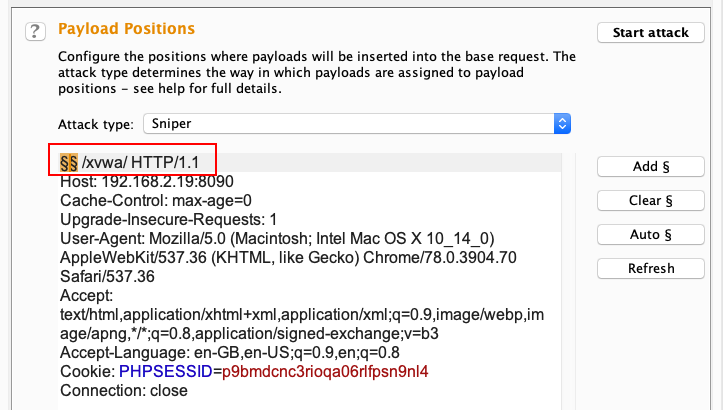
To fuzz the HTTP request methods, let's add the payload marker (§) by clicking the Add § button, as we can see in the following screenshot:
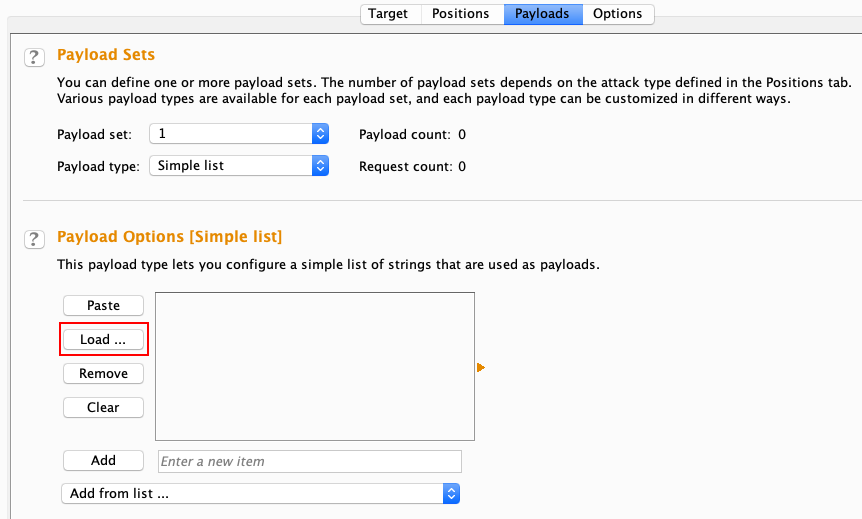
Now that the payload marker is set, we need to define the payloads that should be used by Intruder for fuzzing. This can be done by clicking on the Payloads tab (as we can see in the following screenshot). In this case, we'll be using a wordlist that contains some of the common HTTP request methods. The wordlist can be used by first setting the Payload type to Simple list and then loading the list by clicking the Load … button:
Once the wordlist is loaded, we can click on the Start attack button to begin the fuzzing:

A new window will open with the fuzzing results, as we can see in the following screenshot:
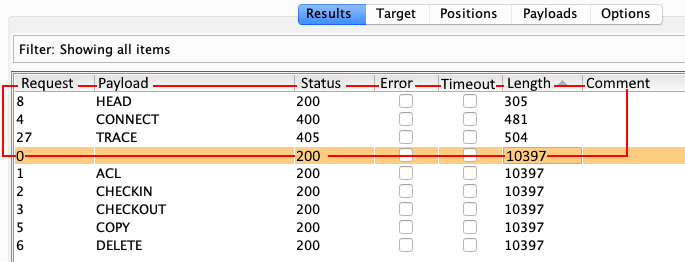
In the preceding screenshot, we can observe that the server responds with HTTP 400 (Bad Request) and HTTP 405 (Method Not Allowed) codes when HTTP CONNECT and TRACE methods are used, respectively. This shows us the behavior of the web application server regarding these two request headers.