WMAP allows us to add our own modules. This could be modules from the MSF or we can make our own module entirely from scratch. Let's use an example of the SSL module. The following screenshot shows that we have two modules that are currently being used by WMAP:
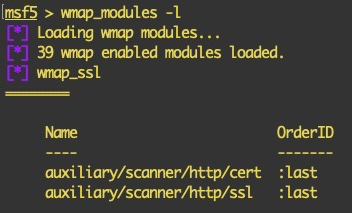
We can add another SSL-based scanner module as well (apart from the SSL Labs modules that are available in the MSF):
- We will use the ssllabs_scan module, which will perform an SSL scan using Qualys SSL Labs' online SSL scanner via the public API provided by Qualys:
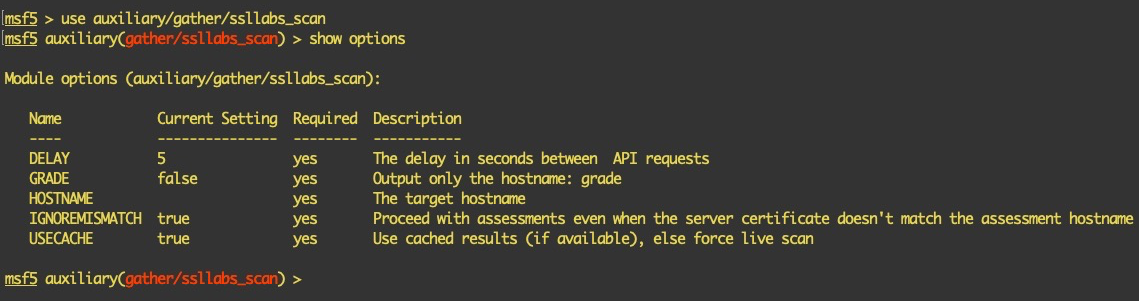
- We now edit the source code of this module so that we can add the necessary library and methods that can be used in the scan:

- We add the following line below the MetasploitModule class:
include Msf::Auxiliary::WmapScanSSL
The aforementioned WMAP library provides methods for WMAP SSL scanner modules that are included in the scan. This can be seen in the following screenshot:

Just adding the library won't suffice; running the module with just the library added will result in an error:

The reason is this is the HOSTNAME datastore, which is the ssllabs_scan module option, and it is not picked up by the WMAP plugin at all. The plugin only has the following methods defined (refer to the metasploit-framework/lib/msf/core/auxiliary/wmapmodule.rb file):
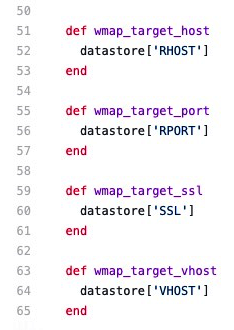
In this case, we need to find a way for WMAP to identify the HOSTNAME datastore for the ssllabs_scan module. There could be many workarounds, but we'll use this one as it's convenient for us:

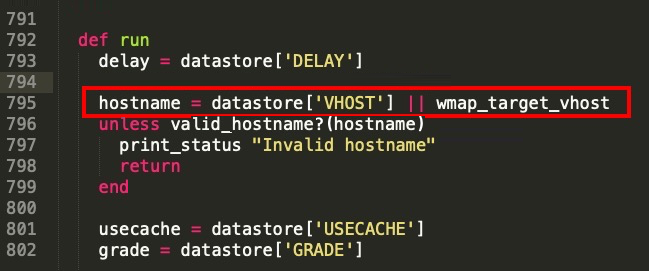
- We change the datastore to be used from datastore['HOSTNAME'] to datastore['VHOST']:
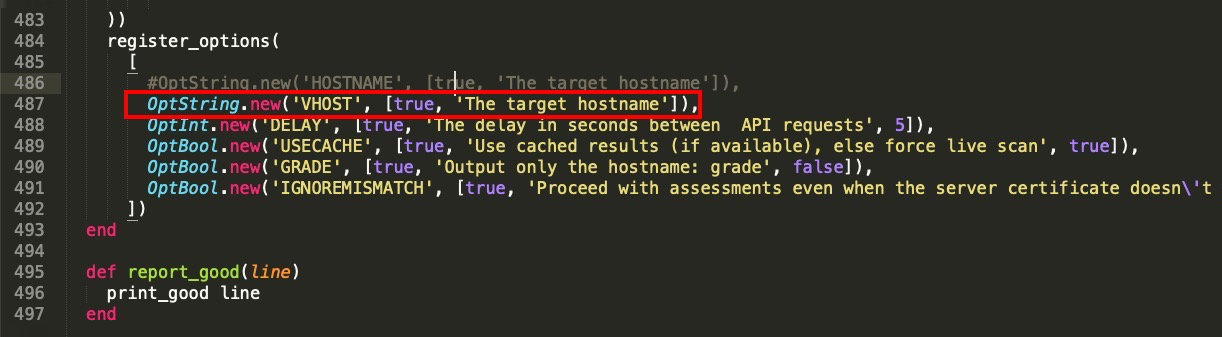
The variable that was storing the data from the HOSTNAME datastore will save the data from the VHOST datastore. At the same time, WMAP will recognize the VHOST datastore through the wmap_target_vhost() method:
- Now we save the code and go back to our Metasploit console and reload the module by typing reload:
We also reload the WMAP modules using the following command:
wmap_modules -r
The following screenshot shows the output of the preceding command:
- Let's list the modules now:

The module is loaded!
The following are the types of mixins that can be used in any module:
|
Mixins |
Description |
| WmapScanSSL | Runs the scan against the SSL service once |
| WmapScanServer | Runs the scan against a web service once |
| WmapScanDir | Runs the scan for every directory found in the target |
| WmapScanFile | Runs the scan for every file found in the target |
| WmapScanUniqueQuery | Runs the scan for every unique query found in each request of the target |
| WmapScanQuery | Runs the scan for every query found in each request of the target |
| WmapScanGeneric | Modules to be run after the completion of the scan (passive analysis) |
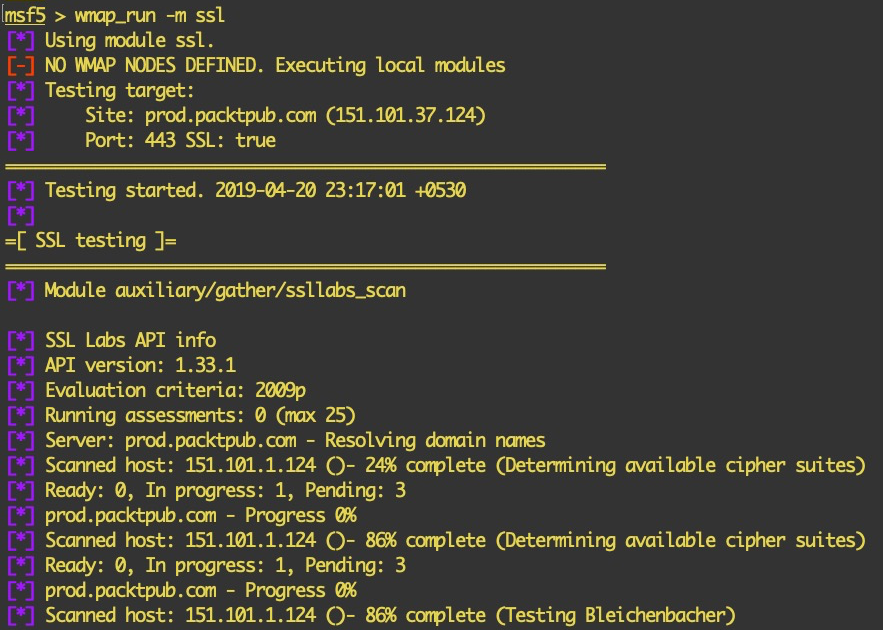
- Update the WMAP module in action:
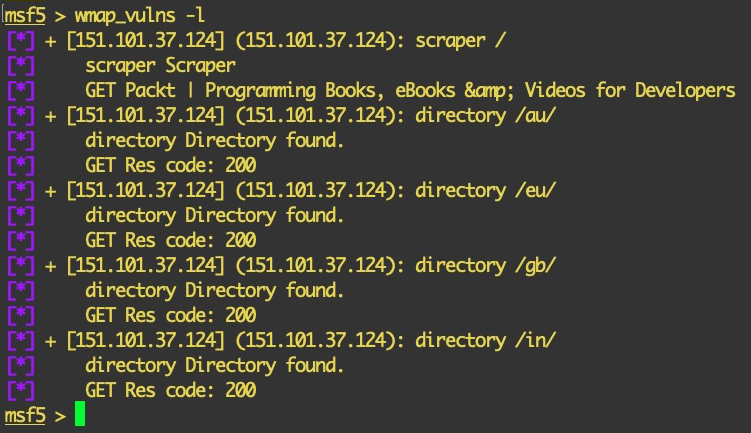
The vulnerabilities found by the modules are saved in the database, which can be viewed by executing the wmap_vulns -l command:
In the next section, we will look at the distributed scanning feature of WMAP.