Enumerating files and directories is one of the most important steps during a pentest activity. A small misconfiguration on the server's end can lead us to the following files:
- Hidden files
- Backup files
- Config files
- Duplicate files
- Files containing juicy information, such as credentials files, password backup, error logs, access logs, and debug trace
Information contained in such files can help us to plan further attacks on an organization.
The following are a few auxiliaries that are available in the Metasploit framework that can help us to gather information:
- dir_scanner
- brute_dirs
- prev_dir_same_name_file
- dir_listing
- copy_of_file
- Backup_file
Here are some examples of the aforementioned auxiliaries:
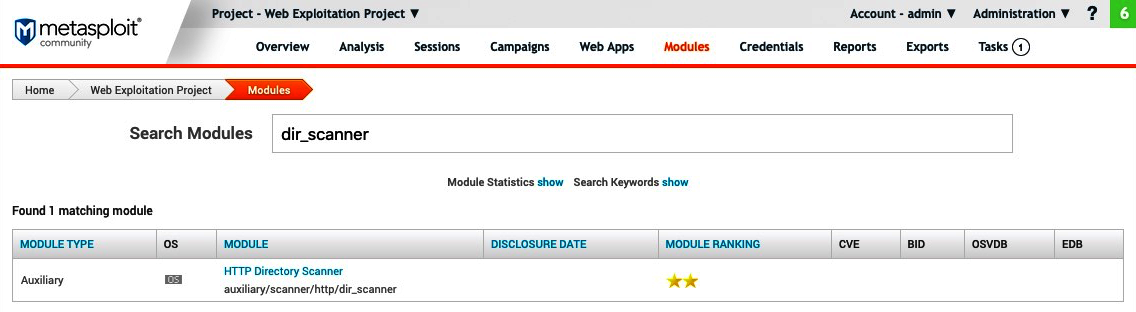
- We can look for a directory listing, as well as hidden directories, using the HTTP Directory Scanner module. We can use the dir_scanner keyword to find the module, as shown in the following screenshot:
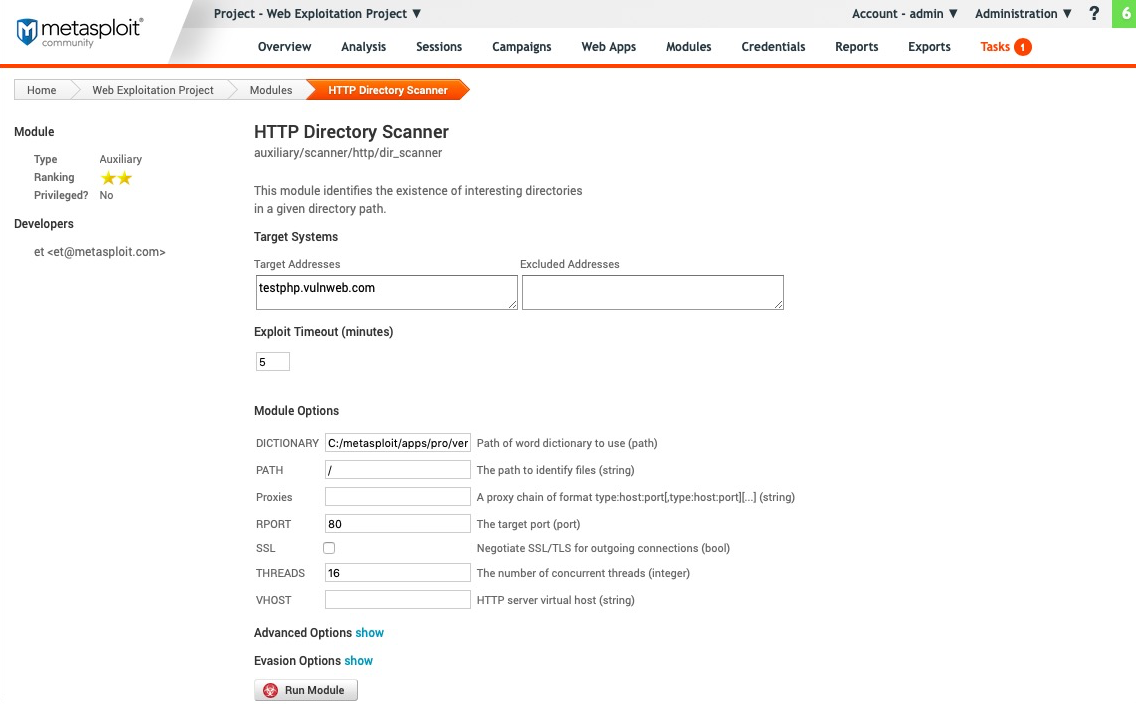
- Clicking on the module name will take us to the options page, where we can specify the target IP/domain name and port number, as shown in the following screenshot:
- Clicking on the Run Module will create a new task and we can see the output in the task window:
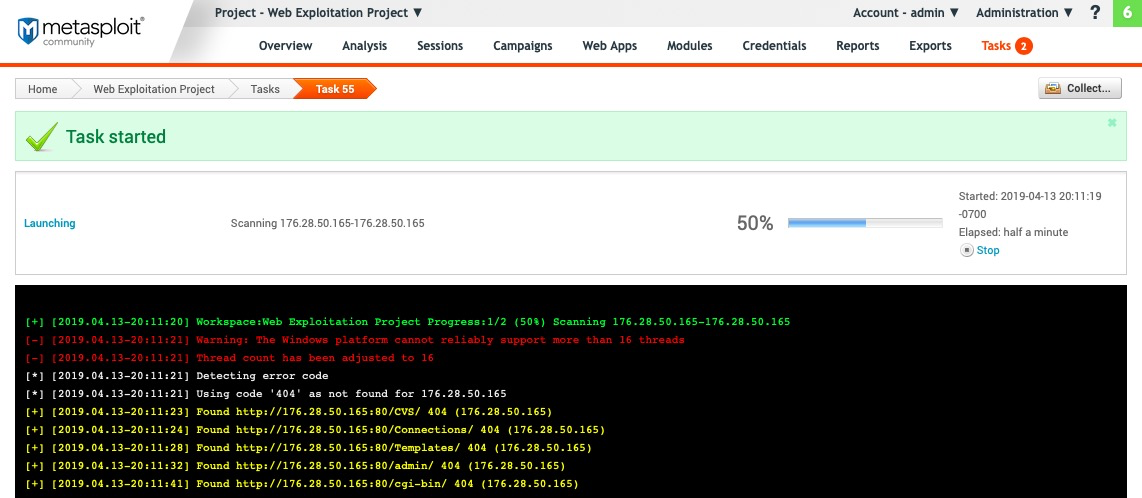
The preceding screenshot shows the different directories discovered by the script.
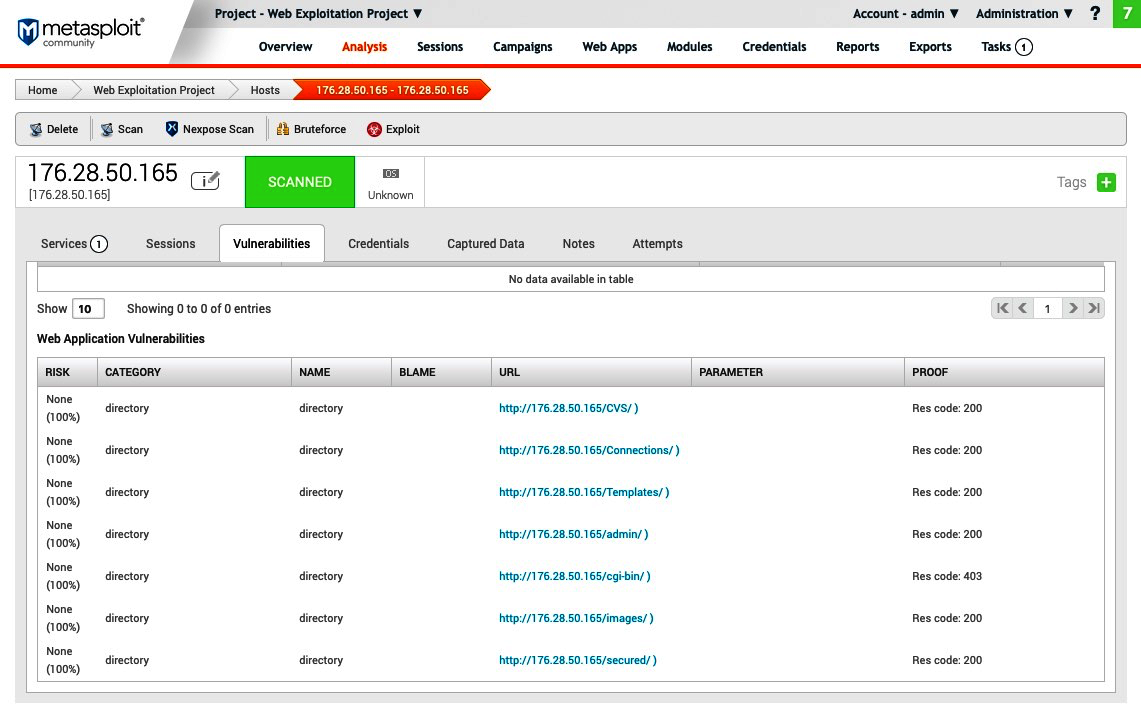
- We can also view the directory list once the scan is complete in the Hosts tab:

- We go to the Analysis tab and choose the host on which we performed the scan.
- Clicking on the Vulnerabilities tab will show us a list of all the directories found by the auxiliaries, as shown in the following screenshot. Similarly, we can use other modules listed at the beginning of this section to perform further enumeration:
In the next section, we will be learning about crawling and scraping using web auxiliaries.