Now that we have learned about the different ways of detecting a Joomla-based target, we can perform reconnaissance using the Metasploit modules that are already provided with the Metasploit framework. The first module that we'll use is the joomla_version module. We can use the use auxiliary/scanner/http/joomla_version command, as shown:

After setting up all the information required by the module (in other words, RHOSTS and RPORT), we can execute the module using the run command, as shown:
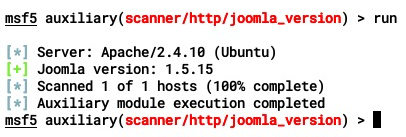
This module will return the Joomla version running on the target instance via the different methods that we covered in the Version detection section. In the next section, we'll learn how to enumerate Joomla plugins and modules using Metasploit.