This method is used when we don't have access to REST APIs, which are responsible for importing the result directly into the DB. The simple workaround is as follows:
- First, export the Nessus result in a file, download the file, and then import the same file using the db_import command.
- To export the result, use the nessus_scan_export <scan ID> <export format> command. (The available export formats are Nessus, HTML, PDF, CSV, or DB). A file ID will be allotted during the process.
- Once the export is ready, execute the nessus_scan_report_download <scan ID> <file ID> command:

As we can see in the preceding screenshot, we have exported the results into Nessus format and downloaded the file.
- Now, import the same file using the db_import command.
- Next, let's execute the vulns command to confirm whether the Nessus results have been successfully imported into the DB:

- We can also confirm whether the preceding method has worked by executing the hosts and services commands, as shown here:
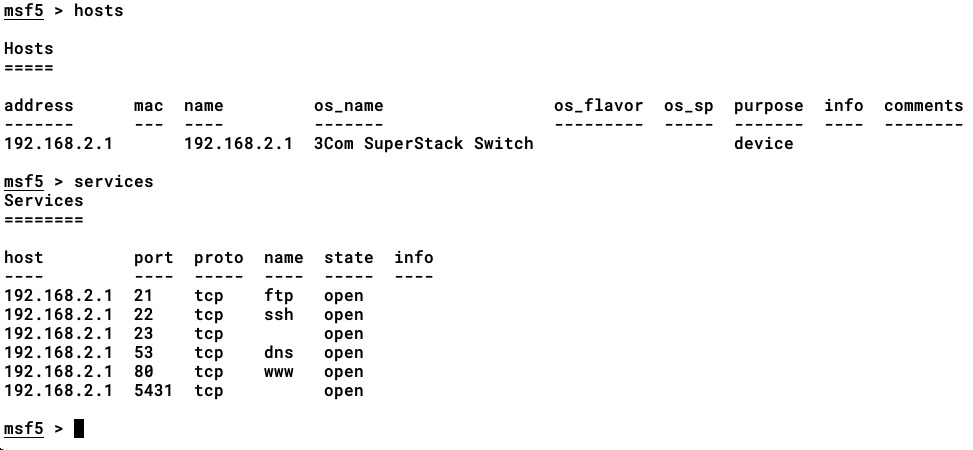
If used properly, we can manage VA projects quite efficiently with the click of a button (of course, by also including the custom Metasploit scripts for managing projects and automation).