In Burp Suite, the different attack types help us with this kind of test case. To fuzz through two wordlists simultaneously, we'll be using the cluster bomb attack type in Intruder:
- To begin with, let's set the Attack type to Cluster bomb and set the payload marker as /?§§=§§ (as shown in the following screenshot):

- As we'll be using two payload sets in this case, let's set our first Payload set (parameter name) and change the Payload type to Simple list:
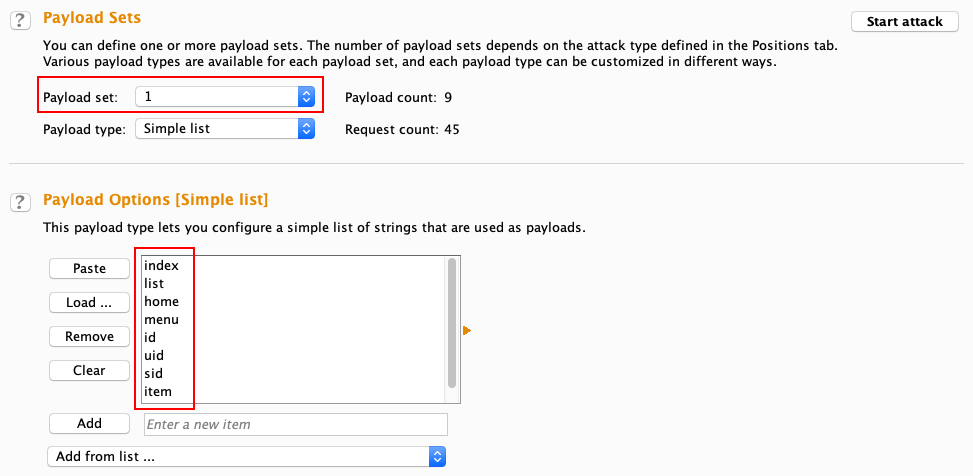
- Now that our first payload set is configured, let's configure our second payload set (parameter value). After setting Payload set to 2, let's change Payload type to Numbers. As the parameter value is in the integer format (in this case), let's set the range from 1 to 5 and set Step to 1:

- Our Intruder is now configured for fuzzing through multiple payload sets. Let's begin the fuzz testing by clicking on the Start attack button (as we can see in the preceding screenshot). We will then see the following screen:
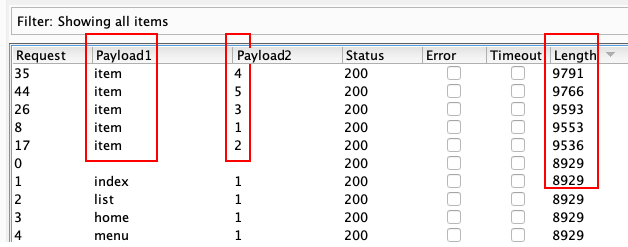
Success!
As we can see from the preceding screenshot, Intruder was able to find an item parameter name with some parameter values. How can we differentiate between the found parameter name and values from other entries in the wordlist? By observing the response length.
Let's try to fuzz three fuzz vectors using Wfuzz (directories, files, and file extensions). This would definitely take a lot of time as it combines different payload sets simultaneously. To fuzz the directories, filenames, and file extensions, we can execute the following command:
wfuzz -c --hc=404 -z file,SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt -z file,wfuzz/wordlist/general/common.txt -z list,php-txt http://192.168.2.19/FUZZ/FUZ2Z.FUZ3Z
The following screenshot shows the output of the preceding command:

The result can be filtered based on the number of characters (--hh), words (--hw), or lines (--hl):

Now that we have some idea of how to fuzz HTTP request URIs, let's understand how we can fuzz HTTP headers.