Metasploit does not yet have an inbuilt module for Joomla's specific vulnerability assessment. This gives us two options; either make a wrapper or plugin for Joomla ourselves, as we did for WordPress in the previous chapter, or use different tools that are already available online, such as JoomScan or JoomlaVS. In this section, we will look at a great tool that can be used to perform a vulnerability assessment of Joomla.
The following description is included on the official Joomla GitHub wiki page:
JoomlaVS can be downloaded from: https://github.com/rastating/joomlavs.
The tool can be run by executing the following command:
./joomlavs.rb
Running the tool without any arguments will print the help section, as in the following screenshot. The tool supports different scan types, such as scanning just the modules, templates, or components:

To perform a scan on a URL for all extensions, we can use the following command:
./joomlavs.rb --url http://<domain here>/ -a
The tool will start running and the details of everything it discovered will be printed on the screen, as shown:
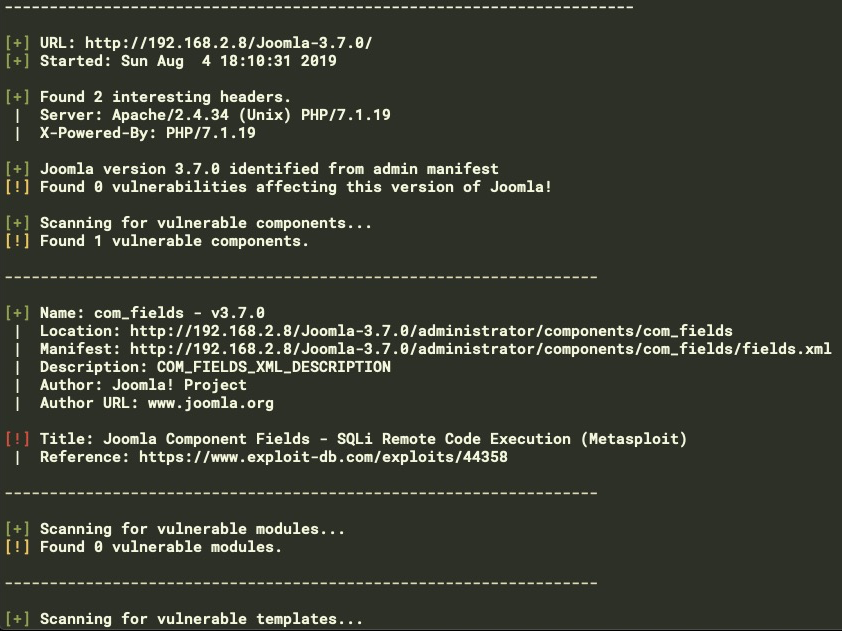
Once we have our information about the available exploits, plugins, and version numbers, we can proceed to the exploitation process.