Let's say we're working in an organization and we are provided with the credentials to access Nessus via the Metasploit terminal ONLY. In situations like these, it's always better to run some basic commands to understand what we can and cannot do. Let's have a look at these commands over the course of the following steps:
- The first command we can execute is nessus_server_properties in msfconsole. This command will give us the details regarding the scanner (Type, Version, UUID, and so on). Based on the type of scanner, we can set our scanning preferences, as shown here:

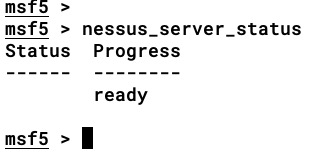
- The nessus_server_status command is used to confirm the status of the scanner so that we can determine whether it is ready. This is helpful in situations where the organization is using a cloud-based Nessus with distributed scanner agents. The output of the command is shown in the following screenshot:
- The nessus_admin command is used to check whether the authenticated user is an administrator, as shown here:

- The nessus_folder_list command is used to see the directories in Nessus that are available for us to use. Running the command will give us the output shown here:

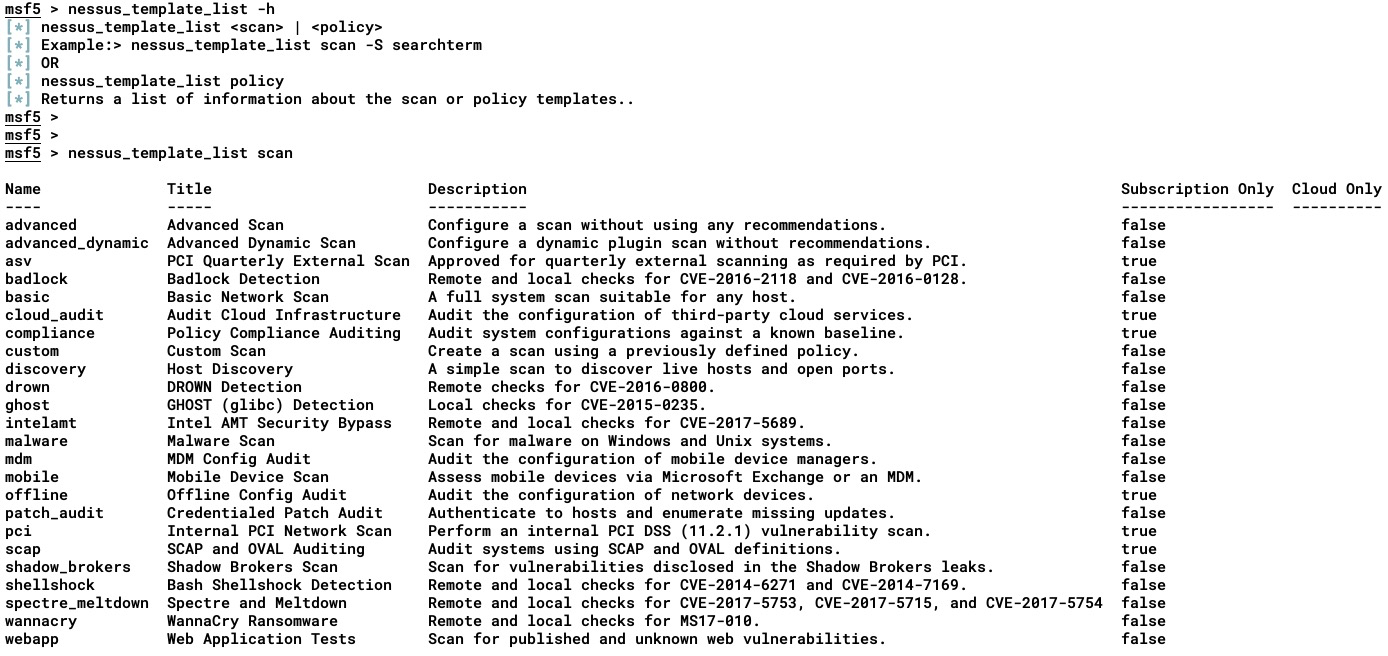
- The nessus_template_list command is used to list all of the templates available in Nessus. (Note: We can use the -h flag to see the help section for this command). The accessible templates have Subscription Only set to TRUE. To use all of the templates, we have to look for the subscription online. The output of the preceding command is shown in the following screenshot:
- To see a list of categories that are configured in Nessus, we execute the nessus_family_list command. Upon executing this command, we will see all of the available categories (Family Names) with their respective Family ID and number of plugins, as shown here:

- To list all of the plugins in a family, we can execute the nessus_plugin_list <family ID> command. This will show us all of the plugins that are available to use in Nessus, as shown in the following screenshot:

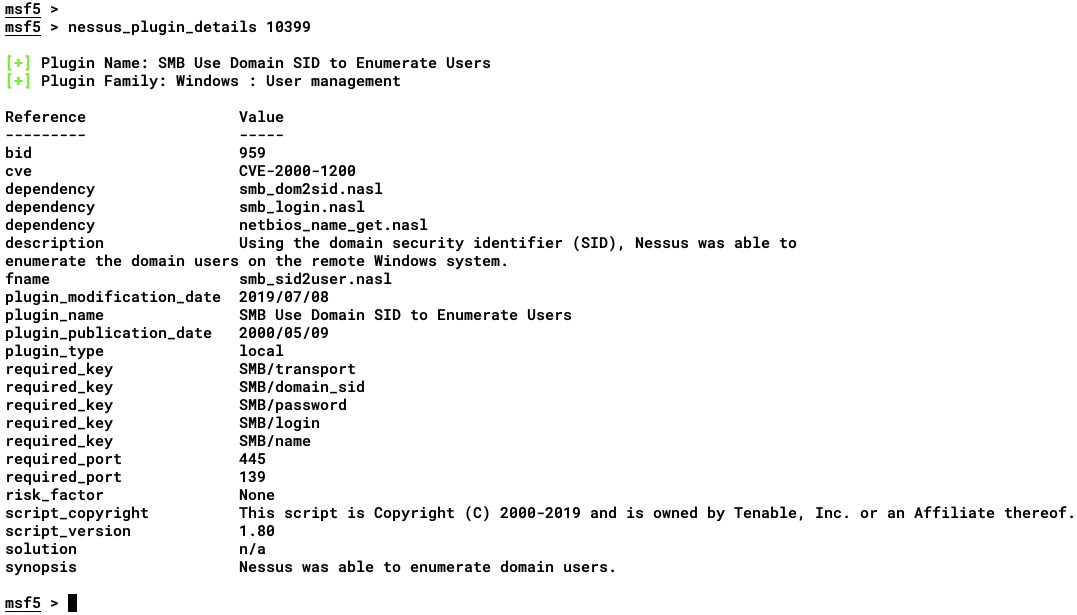
- To learn more about the plugin in detail, we can execute the nessus_plugin_details <plugin ID> command in msfconsole, as shown here:
- To list all of the available custom policies, we can execute the nessus_policy_list command. This will give us the policy UUID, which we'll be using to perform vulnerability scanning. These policies are used to perform custom scans. Policy UUIDs can be used to differentiate between the different scans performed using multiple policies, as shown here:

To begin scanning, we first need to patch the Metasploit Gem, which is responsible for communicating with the Nessus RESTful API (as the official patch is not yet released) for the errors we may face while running the scan. This is a workaround developed by @kost (https://github.com/kost). If not patched, Metasploit will throw an error, as shown in the following screenshot:
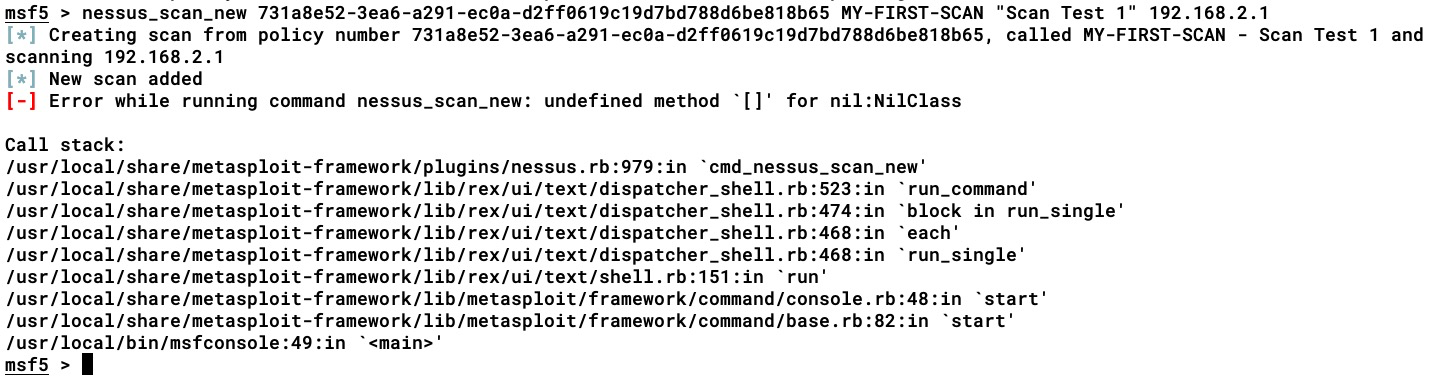
In the next section, we will look at patching the Metasploit library.