The enum_dns module in Metasploit is a bit outdated (we can check the TLD wordlist for updates). So, let's customize the module to meet our needs. The idea is to provide enum_dns with the Top Level Domain (TLD) wordlist and the entries will be parsed and checked to query a record. Looking at the source code of the auxiliary, we can see that the TLDs it looks for do not have the new TLDs that were launched recently:

This can be seen in line 302, in the modules/auxiliary/gather/enum.dns.rb file, which can also be accessed online by visiting the following link:
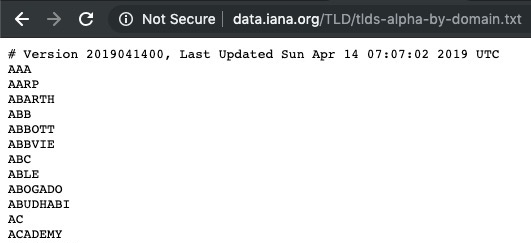
From the preceding source code, we can see that the TLDs are stored in the tlds[] array. Let's edit the code to update the TLDs by performing the following steps . The updated TLD list can be found from the Internet Assigned Numbers Authority (IANA) website: http://data.iana.org/TLD/tlds-alpha-by-domain.txt:
- Download the TLD file from the preceding URL and remove the first line, starting with #:
- Make a backup of the enum_dns.rb file using the following command before modifying the Metasploit module:
cp /usr/local/share/metasploit-framework/modules/auxiliary/gather/enum_dns.rb enum_db.rb.bak
Note that the Metasploit framework is installed in the /usr/local/share directory. In our case, we have named the file enum_dns.rb.bak.
- Now, open the enum_dns.rb file in any text editor of your choosing and go to line 29:

- Let's add another register entry to the code so that we can provide our TLD wordlist to the Metasploit module:

In this module, the TLD enumeration is disabled by default. As we can see from the preceding screenshot, the ENUM_TLD option will perform a TLD expansion by replacing the TLD with the IANA TLD list (old list) when set to TRUE.
- Let's search for the ENUM_TLD string to look for function(), which will be called when the TLD enumeration option is enabled.
As we can see from the following screenshot, the get_tld() function will be called if ENUM_TLD is set to TRUE:
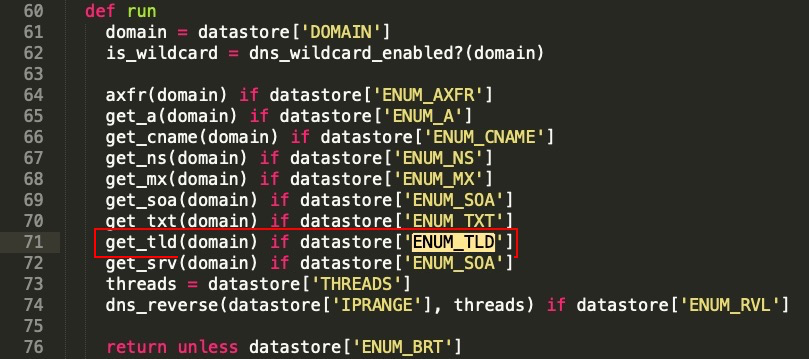
- Let's now look into the get_tld() function:

- Let's now add a code section that will load the latest TLD wordlist and save it in the tlds[] array. Note that we have emptied the TLD array from the preceding screenshot:

What did we do here? The following table explains the functions and code structures used in the previous screenshot:
|
Code |
Description |
|
tlds = [] |
This declares an array. |
|
tld_file = datastore['TLD_WORDLIST'] |
This saves the wordlist filename (with location) in the tld_file variable. |
|
File.readlines(tld_file).each do |tld_file_loop| |
This reads the TLD wordlist line by line. |
|
tlds << tld_file_loop.strip |
This strips off the \n from each line and saves it in the tlds[] array. |
- Now, save the file and execute the reload command in msfconsole to reload the modules in the framework:

- Let's use the customized enum_dns module now and execute show options:
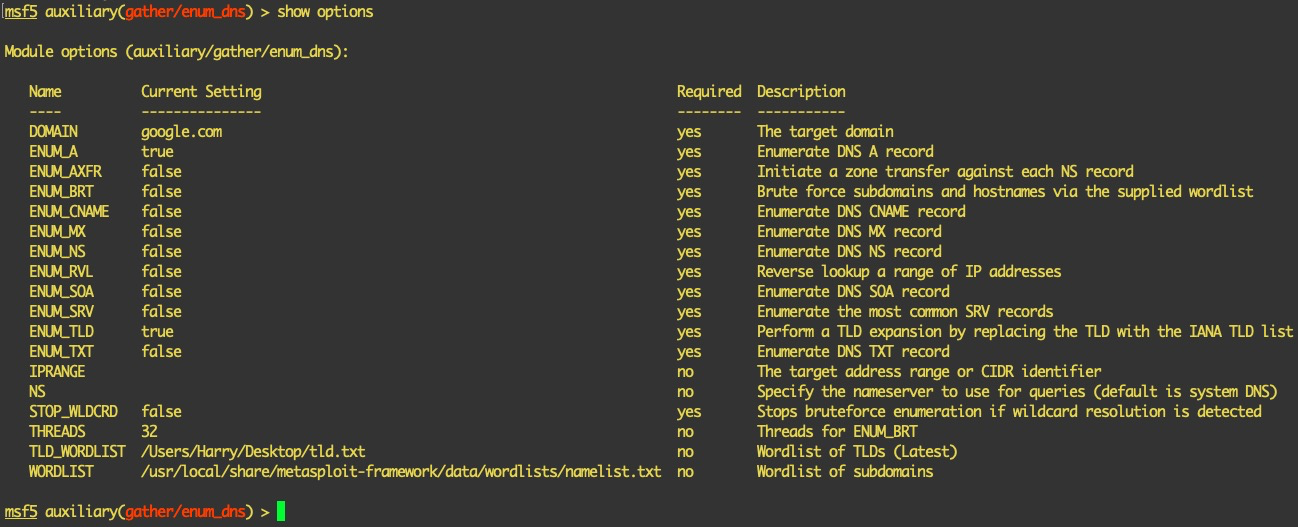
As we can see in the preceding screenshot, we have set the domain to google.com to find TLDs for Google. We have also set the TLD_WORDLIST option to our updated TLD wordlist. Let's execute it:

Bingo! The updated Metasploit module now shows us the TLDs, which are provided to the module itself. Let's now move on to the next section where we will be enumerating files and directories using Metasploit.