Looking at the source code of class.rest-api.php, we can see that the user input is passed as a get parameter named fields into the explode function. The explode function is used to split a string by a specified string into pieces:
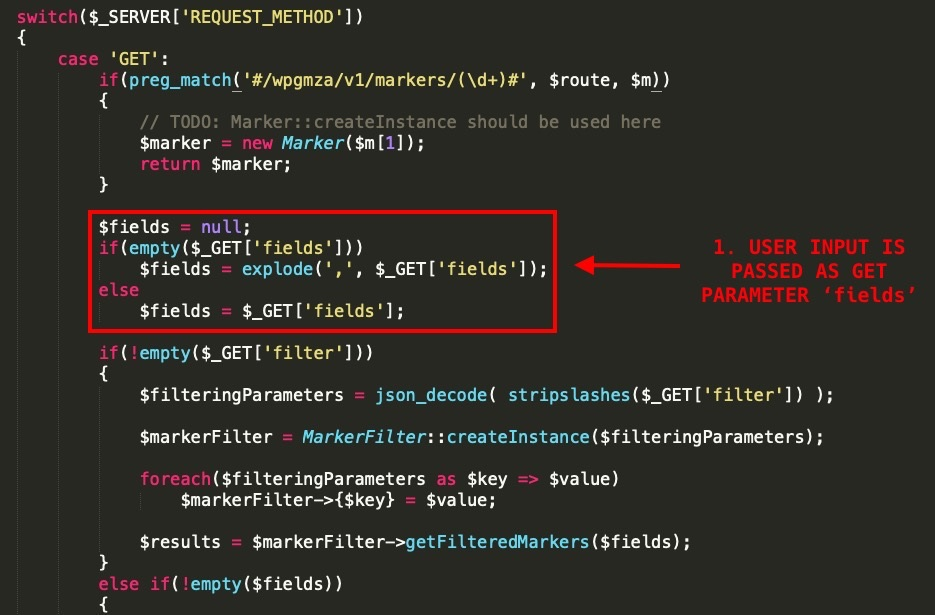
Then, the input is stored in the $imploded variable, combined back using implode(), and passed directly into the SELECT query, as shown in the screenshot here:

The $imploded variable is the injection point here. This vulnerability can be exploited by using the Metasploit module as well.