In memory corruption vulnerabilities such as buffer overflows and format strings, if memory defenses such as Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are in place, code reuse techniques such as Return-to-libc (ret2libc) and Return-Oriented Programming (ROP) can be used to bypass those defenses. Code reuse techniques are also viable in the case of PHP-based web applications, which use the concept of objects. One code reuse technique that can utilize the properties of the object for exploitation is Property-Oriented Programming (POP).
A POP chain is an exploitation approach for object injection vulnerabilities in web applications that exploit the ability to arbitrarily modify the properties of an object that is injected into a given web application. The data and control flow of the victim application can then be manipulated accordingly.
To create a POP chain, the serialized payload uses the HandlerStack class of GuzzleHttp:
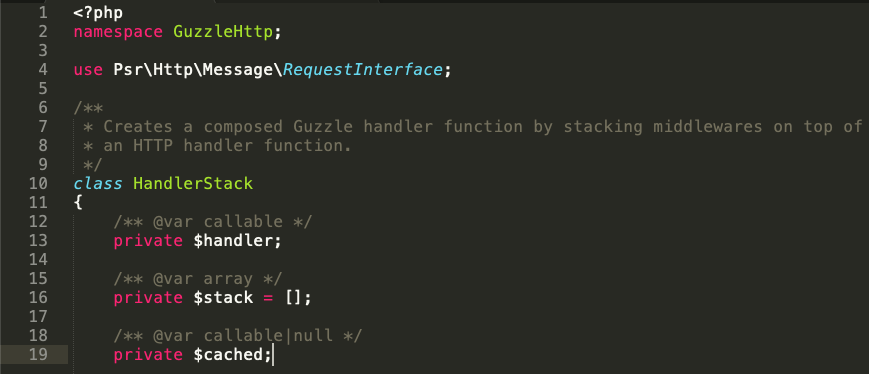
We'll pass our command to the handler method, and the dangerous function to the stack[] method, as shown in the following screenshot:
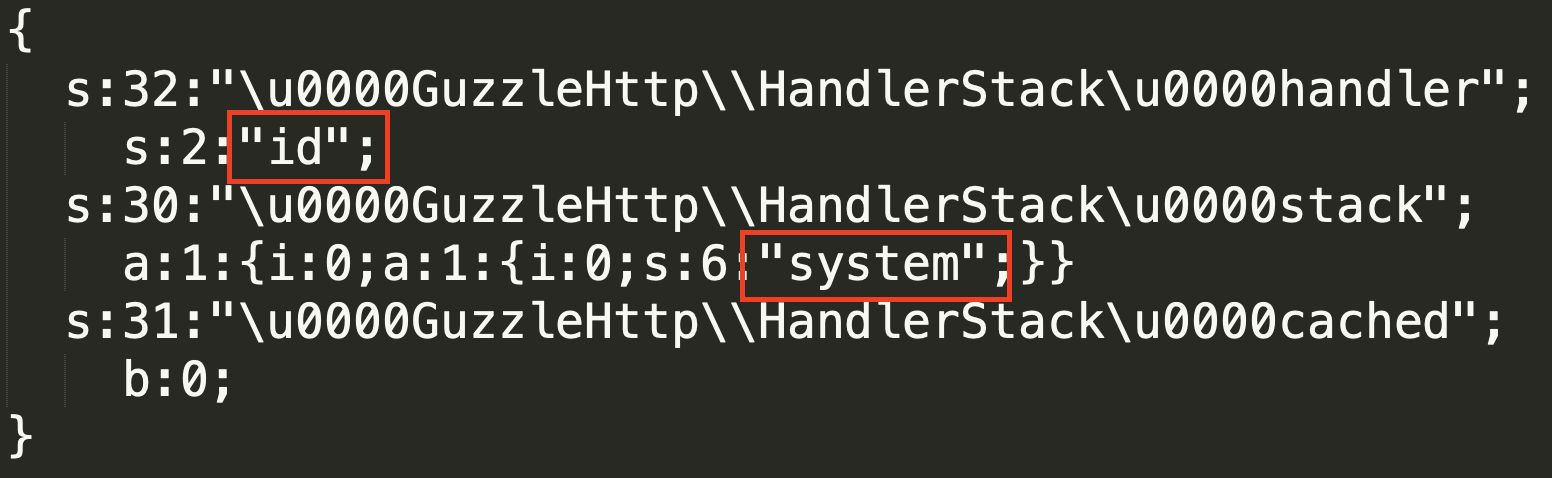
Once the destructor is called (the calling is done automatically at the time of object destruction), the properties of the _fn_close method are passed to call_user_func(), and system(id) is executed:
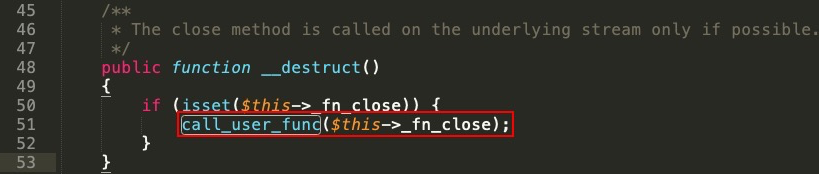
Next, we will deserialize the payload.