In this phase, information related to the target is gathered using a crawler, proxies, and any other sources. The data is then saved in the MSF database for further use. The data can be fetched using any third-party tool, such as Burp Suite or Acunetix. The data can be imported into MSF using the db_import command as MSF supports many third-party tools. Let's look at an example of how a Burp scan can be imported into Metasploit.
The following screenshot shows the output of the db_import command:

The following are the steps to export the Burp Suite data and import it into Metasploit:
- Open up a previously completed scan of a domain name. It could be either active or passive. In our case, we will use an example of a passive scan of prod.packtpub.com. The Issues tab in the following screenshot shows various issues discovered by Burp:

- We will then select the issues we want to transfer to Metasploit and right-click. Then, we choose the Report selected issues option, as shown here:

- A new window will open that asks us to choose the format for the report. We choose XML and click Next:

- In the next step, we can specify the details we want in our report and click Next:

- Then we choose whether we want to include requests and responses for our selected issues from the scanner. We choose both of them and click Next:

- Next, it will ask us to select all the issues we want to export. We choose the ones we need and click Next:

- In the final step, we choose the destination path and filename and click Next:

- The report will now be exported and we can close the window once the export is complete:

- To import the Burp Suite report into Metasploit, we can simply use the following command:
db_import test.xml
The following screenshot shows the output of the preceding command:

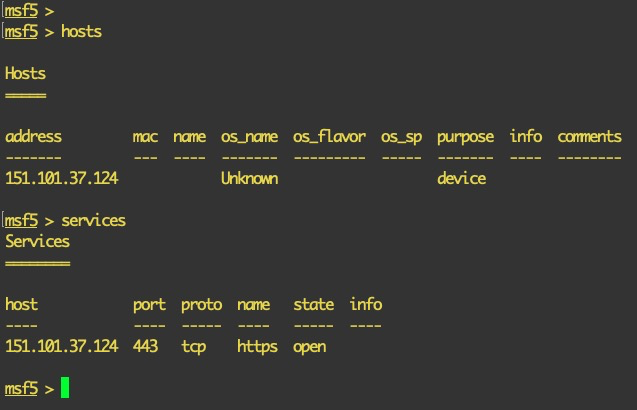
- Once the import is complete, we can view all the hosts in the report by using the hosts command, as shown here:
- To see the vulnerabilities imported from the Burp Suite scanner, we can use the vulns command, as shown in the following screenshot:

As the information is now imported into Metasploit, WMAP will automatically detect and load the same information too, which means the hosts in Metasploit will now automatically be added as sites in the WMAP module.