There's no Metasploit module that can perform a vulnerability scan on Drupal. As such, we need to use a third-party tool, such as droopescan, to help us find vulnerabilities in Drupal. droopescan can be downloaded from https://github.com/droope/droopescan:
- Let's clone the Git repository of droopescan for installation using the following command:
git clone https://github.com/droope/droopescan
The following screenshot shows the output of the preceding command:
- Before running droopescan, we still need to install the necessary Python modules, which can be done using the following command:
pip install -r requirements.txt
- Once all the packages are installed on the system, we can test the installation by executing droopescan using the following command:
./droopescan
- If there's an error while executing droopescan, we can execute it using the following command as well:
python droopescan
- Following the installation of droopescan, we can execute the following command to run a vulnerability scan on Drupal:
./droopescan scan drupal -u <URL>
The following screenshot shows the output of the preceding command:
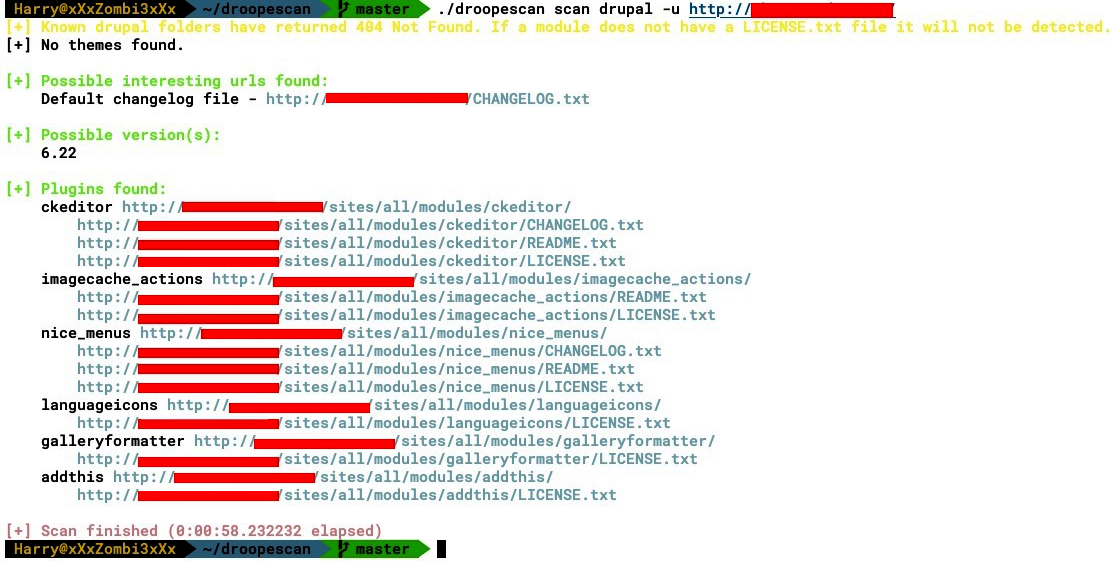
droopescan is a plugin-based scanner that identifies vulnerabilities in several CMSes, but mainly Drupal. droopescan uses a pre-built word list, and the detection of modules, themes, and plugins is done by brute force. So, this all depends on how good our word list is. We can find other Drupal-based vulnerability scanners as well, which can be used to identify vulnerabilities in Drupal. The only difference is the language they are written in (for efficiency) and the word list they use.
When we have found vulnerabilities in the Drupal CMS, we can move on to finding public exploits for them. One of the most famous vulnerabilities is Drupalgeddon. In the next section, we will cover the Drupalgeddon2 vulnerability and learn how it is exploited.