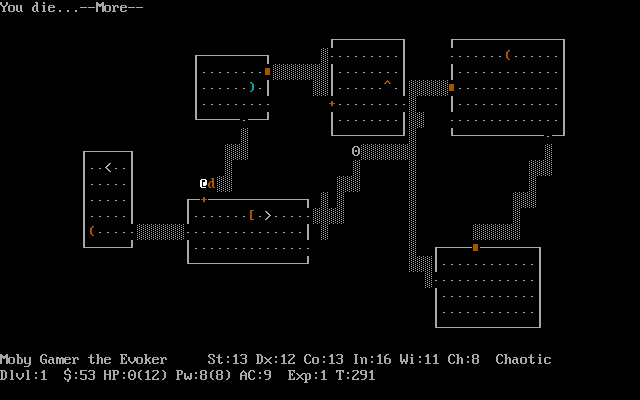
NetHack closely resembles Rogue and Hack, albeit with more color and deeper game systems. (Image: Mobygames.)
Hack + 1
Mathematisch Centrum was founded in the 1940s as Amsterdam's premiere destination for research in the fields of mathematics and computer science. During the 1980s, doctoral students, scientists, and postdocs scrambled to claim computer terminals so they could carry out their work in biology, cryptology, economics, information technology, and energy.
"During the daytime, there was a shortage of terminals, so game-playing was not done," explained Andries Brouwer, a mathematician and computer programmer in the department of mathematics at Mathematisch Centrum, known today as Centrum Wiskunde & Informatica (CWI).1 When the sun went down and the labs cleared out, however, Brouwer moonlighted as the facility's resident game master. "The game master installed games, made sure they worked, and made sure the login that gave access to them was suitably restricted in time and capabilities."
According to Brouwer, CWI was one of the first facilities in Europe to receive Internet access. In 1984, while spelunking through the archives of businesses and universities that had gone online, he dug up the Lincoln-Sudbury tape submitted to the USENIX conference two years earlier. Sifting through its contents, he uncovered the Hack game made by the computer gang at Lincoln-Sudbury High.
Brouwer got hooked on the game and made sure it was installed on CWI's minicomputers, enabling other researchers to indulge in their proclivity for delving through dungeons. While his peers fought monsters and sought out artifacts, Brouwer observed their efforts with scholarly interest. "Hack was a topic [of conversation] near the coffee machine, and I also watched my brother play."
More interested in modifying the code than questing for loot, Brouwer listened carefully when players opined suggestions for new features. Being able to fight alongside pets was a popular request, so Brouwer added a few four-legged critters to the code. Fenlason had included fifty-two monsters in Hack, doubling Rogue's bestiary. Brouwer added even more. Every addition broadened the options at the player's disposal.
"Hack became a challenge of a different type. Since there are many different things one might do, one almost always has the possibility to overcome a [challenge]. Just after one dies, one goes 'I should have...' and immediately starts the next game."
Traffic Jam
Brouwer eyed Usenet as the perfect distributor for his revised Hack game. Formed in 1980, Usenet functioned like a virtual bulletin board: users could post messages and files in various categories, called newsgroups, and other users could respond, forming chains of conversations and data. Unlike forums and bulletin board systems (BBS), which came several years later, Usenet did not utilize a central server to store and pass messages between computers. Instead, individual users managed newsgroups. As newsgroups made contact with other computers, they exchanged information, such as copying a message or file. Most newsgroups catered to a specific group of users. Fans of Rogue congregated at net.games.rogue to talk about and download the game, while net.games was a broader newsgroup dedicated to discussion about all sorts of games.
On December 17th, 1984, Brouwer uploaded Hack 1.0 to the net.sources newsgroup, marking the game's first public release.2 Stability was shaky on early Usenet connections, so Brouwer uploaded Hack 1.0 in fifteen separate files for easier downloading. Over the following month, Hack 1.0 spread from news server to news server as more players caught wind of it.
Few, if any of the players who partook in Hack 1.0 were casual users. The Internet was still in its infancy, and years from being made widely available by providers such as America OnLine and CompuServe, who would bring Internet to millions of families around the world. In the early 1980s, anyone with Usenet access was a scientist, military personnel, a hacker, or a knowledgeable student connecting from a university lab.
Consequently, Hack 1.0's rapid spurt in popularity was driven by individuals with a keen interest in studying and sharing software, and who had a working knowledge of the UNIX operating system and software designed for it. "Hack was very accessible," Brouwer recalled. "Everybody could sit down and play. The movement commands ['h' for left, 'j' for down, 'k' for up, and 'l' for right] were identical to the cursor movement commands in the text editor, vi. Pressing '?' would give instructions."
As word of Hack's breadth of gameplay spread across Usenet, more users stormed newsgroups in search of the game. Computers responsible for holding news posts and files buckled under the weight. In mid-January 1985, Gene Spafford, an avid Usenet explorer and professor of computer science at Purdue University, took the necessary steps to divert all Hack 1.0-related discussion and downloads to a central location.
From: spaf@gatech.UUCP (Gene Spafford)
Newsgroups: net.news.group,net.games,net.games.rogue,
net.games.hack
Subject: net.games.hack is created
Date: Thu, 17-Jan-85 12:43:33 EST
Date-Received: Fri, 18-Jan-85 10:15:10 EST
There has been an incredible amount of traffic generated by users (and abusers) of the "hack" game recently posted to the net. I have just created the newsgroup "net.games.hack" for that traffic. Please stop posting articles about "hack" to "net.games" and "net.games.rogue" and use this new group instead.
We now resume the disaster, already in progress.3
Brouwer did his best to feed the growing need for more Hack, rolling out new updates to the net.games.hack newsgroup. Version 1.0.3, released in July 1985, was three times as large as the previous version and included assorted new features such as the dog pet, shops randomly scattered throughout dungeons, and new monsters such as the long worm, represented on-screen by W~~~~. The long worm was one of many additions that required players to think strategically rather than simply confront monsters head on. Attacking the long worm's middle split it in half, creating two foes. To kill the creature without multiplying it, players had to dart around and attack its tail while avoiding its gnashing teeth. Other tactical considerations implemented by Brouwer included having to leave items behind when the player's backpack reached full capacity, and leaving space in the pack for gems and gold which increased the player's high score upon inevitable death. Players also had to forage for food to ward off starvation, which set in quicker as they grew stronger. [SQ1]
The 1.0.3 update boosted character diversity as well. Players could choose a class, such as the caveman (or cavewoman), and venture into new environments such as swamps, vaults, and Hell, the location of the Amulet of Yendor, which had made the jump from Rogue as the ultimate prize in Hack. Of course, players could not simply follow the linear path down to Hell, grab the Amulet, and celebrate. Adventurers who entered Hell without covering themselves from head to toe in fire-resistant gear were instantly burned to a crisp.
Curator
Brouwer moved on to other interests after releasing Hack 1.0.3. Like Jay Fenlason before him, Brower uploaded his source code, a torch passed on to anyone interested in carrying it. Another hacker, Don G. Kneller, stepped up. Kneller had gleaned hours of enjoyment playing the game on UNIX and decided to port Hack to Microsoft's MS-DOS operating system for PC. Carrying over the copyright license still intact from Jay Fenlason's upload of the game years before, Kneller called his version PC HACK 1.01e. He went on to release four more versions, each adding support for hardware such as the DEC Rainbow microcomputer. A developer by the name of R. Black downloaded PC HACK 3.51 and rewrote it in Lattice C, a permutation of the C language. Black then got the game up and running on the Atari ST, leading to the advent of ST Hack 1.03.6
Yet another hacker, Mike Stephenson, saw the merit in spreading the joy of Hack to as many hardware platforms as possible. "I discovered Hack back in the '80s when I was working as an analyst at a computer hardware supplier and actually had free time on my hands. It was also just about the time I was discovering a variety of UNIX OS variants, [namely] AT&T and BSD, which were in a religious war at the time."7
Stephenson enjoyed the game but, like Brouwer, saw plenty of room for improvement. Using the 1.0.3 codebase as a foundation, he wrote patches that fixed bugs and added new features here and there. Other hackers were equally invested in growing the game. Izchak Miller, a philosophy professor who had lectured at Stanford and MIT, was teaching at University of Pennsylvania when he met Stephenson online in 1986. Janet Walz, programmer and avid Hack fan, was another early contributor. The three met over email and decided to collaborate on the code.
As the team grew, they began referring to themselves as the DevTeam. "I'm not sure when we started calling ourselves that, but I think it happened after we had reached a critical mass in the core of the team and had released at least one or two versions as a team," Stephenson recalled.
At first, the DevTeam focused on squelching bugs. It did not take long for Stephenson's team of hackers to penetrate Hack's surface and make major alterations to its DNA. "Eventually, the game had branched off from the original by a significant amount. Also, by that time, the core of the DevTeam had formed, and someone—I can't remember who, precisely—-suggested that we rename the variant that we'd created. I suggested the NetHack name [as a portmanteau of] 'UseNet' and 'Hack.'"
Released in July 1987, NetHack 1.3d was the first public release to distinguish NetHack as a separate entity from, rather than an update to, Hack. New features included weapons such as Excalibur, King Arthur Pendragon's legendary sword. Character classes derived from Dungeons & Dragons mainstays such as the fighter, elf, priest, and wizard were joined by the ninja, archeologist, samurai, and tourist, presenting unique alternatives for players who had grown weary of stereotypical fantasy fare. The tourist started out with lots of gold, a credit card, maps, and a camera able to be used offensively against monsters.
Although the DevTeam packed even more features into NetHack 1.4f, one convention of Hack remained constant. Players fought their way down from one floor to the next. The first twenty-five floors were standard dungeons consisting of rooms, usually rectangular in shape, chained together by hallways. Deeper down, the corridors narrowed and snarled, forming mazes. The ultimate goal remained to enter Hell and claim the Amulet of Yendor, which was in the clutches of a wizard camped out in the center of a fiery maze.
Four months later, the DevTeam rolled out another update, version 2.2a. New features included Medusa, the voluptuous she-serpent from Greek mythology able to turn adventurers to stone with a glance, and represented in NetHack's dungeons by the number 8. Twenty more dungeon levels were added, increasing the total to sixty, but advancement to Hell remained linear.
Teamwork
In April 1988, the DevTeam patched NetHack to version 2.3e. The update introduced new monsters such as the giant eel and the Three Stooges of slapstick-comedy fame, appearing as @ symbols labeled Larry, Curly, or Moe, and as likely to smack each other as they were the player. New effects and implements were added. Eating the corpse of a slain quantum mechanics monster caused players to teleport around the dungeon at random. Magic wands could detect secret doors, spin monsters out of thin air, or polymorph them into a different species or object. "Special rooms" held treasure and dangerous enemies. One special room was the barracks, a large space filled with soldiers who stood a chance of being asleep, giving players a small window of time in which to ransack the place without rousing them.
Although NetHack 2.3e was the biggest version of the game yet, the adventure still boiled down to moving from Point A to Point Z. The DevTeam knew they needed more members to grow the game, and they did make the source code freely available on the NetHack newsgroup. However, they drew a fine line between users who downloaded the code and mucked around at home, and becoming an official member who made modifications that would be integrated into official releases. To join the ranks of the DevTeam, a programmer had to be passionate about ushering in change. Jean-Christophe Collet's desire to innovate fit the bill.
Like his predecessors, Collet gravitated to computer games after playing early adventures like Zork and Wizardry. In college, he studied UNIX and C programming, which led him to a vast repository of games. "I got access to Usenet and discovered a whole bunch of games in source [code] form; the term open-source wasn't coined yet. Compiling them was rarely easy unless you had access to the same variant of UNIX that the developers of the game were using, but with patience and hard work, you could do it. It was also a great way to learn some of the tools and languages of the time."
Naturally, Collet found his way to NetHack newsgroups, where Stephenson and the DevTeam made source code freely available. "The Hack/NetHack source code was the way the games were initially released, which meant anybody could theoretically get them and port them to their computer—unlike Rogue, which required you to run [the game] on your institution's BSD VAX 11/780," explained a DevTeam member who asked for anonymity.
After uploading several rounds of patches, Collet caught Stephenson's attention and received an invitation to join the DevTeam. Collet signed on, and his name was added to the mailing list of developers who received every new snippet of code to test prior to public release. Collet's involvement in NetHack's development almost landed him in hot water at work. "The company I was working for was paying for our Usenet access—not Internet; that was extremely rare in France back then—by the byte, so to speak. So when I joined the team, my mailbox started filling with huge chunks of code and patches, to the point that my boss pointed out to me that for that first month, my email traffic alone was nearly three-quarters of the bill."
Worried that his situation might bar him from contributing, Collet explained the problem to Stephenson and the others. His teammates quickly concocted a workaround to accommodate him. Normally, each member of the DevTeam submitted patches through email. A proxy collected the patches and applied them to the main codebase. Due to his situation, Collet was given permission to code in relative isolation and send patches to another DevTeam member, who was in charge of making sure Collet's fixes stayed in tune with the collective. Every now and then, he received floppy disks via postal mail that contained code from the rest of the DevTeam, giving him the opportunity to follow their work.
Over the first several months of group development, DevTeam members filtered ideas through Stephenson. As time went on, he encouraged them to use each other as sounding boards, and to act unilaterally in most circumstances. "Little changes and bug fixes could just be put in unless somebody objected; larger ones should be discussed first," explained the anonymous developer. "Some things got voted on; some coalesced into The Right Thing; some were dropped when a strong objection [was raised] or several mild ones couldn't be satisfied."
Simply put, the DevTeam members were too busy with day jobs, and scattered pell-mell around the globe, to convene regularly. "I don't recall any big change that was made in the game by a person and someone else coded it. If you had an idea, it was not going anywhere [unless] you were willing to do the coding," confirmed Paul Winner, another DevTeam member. "It is also the case that some people specialized in certain aspects of the game. You wouldn't make changes to those areas of the game without talking about it with the appropriate person first."9
One of the earliest contributors to NetHack was Eric S. Raymond, a pioneer in the growing movement to support the distribution of source code so that others could learn from and build on software. For his first contribution, submitted in 1985, Raymond layered on a veneer of graphics by drawing dungeons out of solid gray bars rather than plain ASCII text characters such as hyphens and pipes ('|').
For his next trick, Raymond added vibrancy to NetHack. As of version 2.3e, some monsters still appeared in monochrome, while others were doused in shades of color. The use of color not only spiced up the game, but gave observant players more information to work with. Several types of dragons existed, and each dragon's breath dealt damage of a different type depending on the creature's color. Red dragons breathed fire, while blue dragons dealt cold damage. Players could file away the differences between each type and equip themselves appropriately before each encounter.
"This was about five years before color bitmap displays were common, which didn't happen until the early 1990s. The sight of color in a terminal window was actually startling then, even if you knew it was theoretically possible," Raymond explained to me.10 Later, he added audio support, which manifested as beeps emitted from PC speakers.
Cult of Personality
While autonomy was the norm among the DevTeam, introducing a new character class required consensus. "I was a big fan of Star Wars, so I coded the Jedi class, adding things like light sabers, which required batteries to operate and you needed to replace them regularly," recalled Collet. "I had published the patch just before getting invited into the team, but it was deemed as a bit too far from the 'canon' [of NetHack]."
Designing character classes gave DevTeam members a chance to shine. Raymond had been the engineer behind NetHack 1.3d's tourist class, which offered an unorthodox play style compared to conventional fantasy archetypes like the fighter and wizard. Paul Winner modeled the barbarian after Conan, the popular fantasy character created by sword-and-sorcery fiction author Robert E. Howard. Winner researched the character extensively, going so far as to read all the Conan novels and take notes on the character's appearance and weaponry so that fans would recognize the similarities between the Cimmerian and their avatar's characteristics.
Winner pointed to the samurai class as his crowning achievement. "[Creating a realistic samurai] meant adding quite a number of new things to the game, which I tried very, very hard to make accurate. Even references to the dog's name come from a Japanese dog that waited at a subway station for years for his master to come home, but the master had died." [SQ2]
DevTeam members who created a class were also in charge of designing a special quest for their class. Players who chose the barbarian had to journey through dangerous encampments of foes and defeat Thoth-Amon, a spell caster and nemesis to Conan the Barbarian. Character quests featured dialogue between non-player characters (NPCs) and the player-character printed to the screen. "The vocabulary used in the quest was very meticulously [written] to use formal speech. The reception that it received was rewarding," Winner remembered.
"We all had different backgrounds, therefore our references were quite varied. In the end, that diversity is reflected in the game," Collet recalled.
Quests specific to certain character classes were only some of the surprises the DevTeam had in store for NetHack. Branching paths appeared in version 3.1.0, which Izchak Miller published to Usenet in 1993. One of the most popular paths materialized as a staircase that stood a chance of materializing between dungeon levels 34 and 42. Trekking up the stairs led audacious adventurers to Vlad's Tower, a set of levels based on the legend of Vlad the Impaler, the historic figure who became the basis for Dracula. Players had to defeat Vlad to acquire the Candelabrum of Invocation, an artifact required to ascend, the ritual of handing the Amulet of Yendor to a god and completing the game.
"Let's be very clear: NetHack is a collaborative effort. I don't think there is a single feature, file, or anything, that hasn't been worked on by multiple members of the team at some point in time," Collet stressed. "However, two contributions that I remember the most fondly are the special level compiler and Vlad's Tower. Creating the language and technology to script levels while remaining true to the randomly generated part of the game has been one of the most rewarding challenges I've faced as a developer and designer. [Vlad's Tower] was often mentioned, much to my later delight, as one of the most devious parts of the game."
Every new path added new strata of exploration and gameplay possibilities, a feat made even more impressive by the fact that NetHack's dungeons unraveled across a single screen. Confining level real estate to one screen kept the experience manageable for players, while adding dozens of branching paths—woven into the adventure via algorithms—breathed new life into each foray through the game.
"I believe Jay Fenlason's concept for Hack, which became NetHack, was just to build a better Rogue, and it never occurred to him to do otherwise," said Raymond. "Similarly, nobody in the NetHack group thought about the project as anything other than 'build a better Hack.' To everybody, this was Rogue with more features; why start from scratch when that concept worked so well?"
T.D.T.T.O.E.
Izchak Miller published version 3.0.0 of NetHack to the comp.sources.games newsgroup in July 1989. A moderator approved it shortly thereafter, marking the release as the first update credited to the DevTeam instead of a single contributor. Over the versions that followed, the gameplay became increasingly open-ended, enabling players to make their way through NetHack's crucibles in any way they saw fit. Players could discard items onto a single tile of the dungeon floor, creating a pile, and then cast polymorph to transform every item in the pile into a different item. When players who journeyed with a feline companion opened a can, their pet would instantly appear by their side, an addition made by Paul Winner as a reference to his cats' uncanny ability to hear treats being served from virtually anywhere in his house.
Perhaps the most popular example of NetHack's open-ended gameplay is the cockatrice, a monster able to turn players to stone by touching them. By wearing gloves, players can pick up a dead cockatrice and swing it like a club, petrifying any monster touched by the corpse.
The DevTeam's seemingly telepathic ability to predict every possible action gave rise to the acronym TDTTOE, The DevTeam Thinks of Everything. "The more options you have to manipulate the game environment, the more immersive and interesting the game is," asserted Raymond.
Another acronym, YASD, stands for Yet Another Stupid Death, referring to the countless ways in which NetHack's algorithms can bring quests to an abrupt and violent halt. Some deaths, such as standing in the path of a fire-breathing dragon, seem prosaic compared to others that stem from innocuous actions. If players fall down a set of stairs while carrying a cockatrice, the corpse may touch their body, petrifying them. Knights, who attack while on horseback, stand a chance of slipping while trying to mount their steed, breaking their necks.
Over the years, such deaths have become known throughout the NetHack community as "gotcha" moments, deaths that occur suddenly and seem completely out of the hands of players. Some players do not mind them, while others call foul. The majority of the DevTeam believes they are part and parcel of playing the game. "NetHack tries to be an approximation of a real life experience," Stephenson explained. "If you'd mounted a horse hundreds of times, you'd have patterned a 'mount' into your muscle memory and would execute it without really consciously thinking about it. Then, if something happened to go wrong—say, something slightly off with the horse's harness—oops! On your head you go. We do this via a random-number generation to try to simulate that sort of real-life set of risks."
"Players do have control over whether to mount the horse," pointed out DevTeam Member A. "Lots of things have both risk and reward, and if you find the risk too great, you can do something else instead."
YASDs have led some players to disparage the game, claiming one needs a detailed spoiler guide detailing the best equipment, the most efficient route down to the Amulet of Yendor, and which monsters to avoid at all costs, in order to win. Raymond believes the game has grown too arbitrary, the main reason he bowed out of contributing. "There was a natural tendency for the devs to see the game from the point of view of someone who played it constantly and obsessively; thus, over time, their notion of not making it 'too easy' gradually ratcheted up the difficulty level to the point where you couldn't really enjoy it casually anymore."
Thousands of fans, and more than a few members of the DevTeam, view the game differently. To them, NetHack is about the journey, not the destination—the same philosophy that guided Michael Toy and Glenn Wichman as they wrote early versions of Rogue. "You have to know a lot to win, but you don't have to know a lot to play, and we tried very hard to allow people to learn everything they need by playing—after initially reading the provided documentation. It took me years to win Rogue. I think I managed it one time. It was still fun without winning, and I believe NetHack is the same," explained an anonymous DevTeam member.
Paul Winner views death as a learning tool. If angry messages on Usenet excoriated a particular trap, monster, or scenario, or if the developers themselves hit a brick wall, they weighed the merit of complaints. "Things like starving to death and overeating are designed to make sure you learn to read the status [on the screen]. We didn't tell people they were feeling hungry in the beginning, so we did lighten up on some things, but in the end, you need to learn the game and gotcha moments almost always do that."
"Again, this has to do with balance," agreed Collet. "The game is turn-based, so you can take your time and consider your next move. Most of the stupid deaths when I was playing [occurred] because I was [not paying attention]: hitting the move or attack key in sequence without too much consideration. That being said, I'm not saying that all these individual decisions are perfectly balanced, but overall, it seems to work."
Like most roguelikes, NetHack is viewed by fans and developers as extremely difficult. Figuring out how to conquer difficult dungeon levels, most of which will likely never be repeated thanks to algorithms, is what attracted developers and players to the game in the first place. "Many games seem to exist to be beaten and then forgotten—once you know how to do things, you can just do it the same way again and win again, so there's no point [in replaying them]," explained the anonymous developer.
"The aim of [NetHack] was to be difficult in the same way that an old-school D&D dungeon crawl was difficult, creating a strong sense of challenge and accomplishment," according to Raymond, who added that, for as capricious as NetHack can be, "I don't know that any of the other roguelikes managed this better."
Pioneers
NetHack has grown far beyond its origins as a cult game enjoyed only by hackers and college kids with Usenet access. In January 2000, Salon editor Wagner James Au crowned NetHack the best game ever. 12 "No graphics, no sound, no razzle-dazzle—but NetHack is still one of the finest gaming experiences the computing world has to offer.
Indeed, many designers of big-budget role-playing games lifted game mechanics from NetHack and gave them a graphical coat of paint. Diablo, arguably the most popular example of the hack-and-slash-style RPG, was the brainchild of David Brevik, who whiled away his college years playing NetHack and other roguelikes.
For members of the DevTeam, NetHack is a ticket to immortality. In April 1994, Izchak Miller succumbed to cancer. He was only fifty-eight years old. Until the point when he grew too ill to continue, Miller, in addition to arbitrating code submissions and suggestions, had written the majority of the logic that controlled the shopkeepers players interacted with over the course of their adventures. The DevTeam memorialized him in version 3.2 by inserting a new character named Izchak, proprietor of a lighting shop where players can purchase candles and lanterns.13
Besides gaining notoriety as the architects behind one of the most addictive and intricate games ever made, the earliest DevTeam colleagues are pioneers. At the advent of computers and for many years following, there was no difference between hardware and software. Programmers and administrators performed tasks on mainframes by flipping switches and pulling knobs. When commercial computers became available, companies began writing proprietary software that consumers could use but were forbidden to modify.
In answer, hackers around the world began advocating open source software during the 1980s. Eric S. Raymond of the NetHack DevTeam is one of the leaders of the open source movement. Raymond authored "The Cathedral and the Bazaar," an essay later expanded into a book in which he espouses that open source software is technically superior to proprietary software.14 The more programmers able to evaluate code, Raymond argues, the faster bugs can be expunged and updates pushed out.
Stephenson believes that NetHack played a part in the open-source movement. "We pre-dated open-source [as a formalized movement], but I do think that the fact that we made a huge amount of source code available, without charge and under a public license—an early variant of the LGPL [Lesser General Public License]—helped to promote the idea of making software available for public use without cost. I think the other thing that really contributed to the concept of open-source is that NetHack has, and still does, accepted bug reports and feature ideas from anyone."
In December 2003, the DevTeam released version 3.4.3 of NetHack. The update marked the twenty-ninth public release of the game—and, as of this printing, the most recent release. Regardless of its long dormancy, NetHack is proof that compelling gameplay, not state-of-the-art graphics, stand the test of time.
"I am, to this day, incredibly proud of having been part of this adventure," Collet told me. "The fact that almost 30 years later I'm still answering questions about it, and that it is still seen as such a reference, never ceases to amaze me. The friends I made during that time are some of the most precious people in my life, and I'm so grateful that I was so incredibly lucky."