Chapter 5
Understanding Digital Certificates
IN THIS CHAPTER
 Understanding certificates in Windows Server 2019
Understanding certificates in Windows Server 2019
 Examining certificate types in Active Directory Certificate Services
Examining certificate types in Active Directory Certificate Services
 Selecting the appropriate user certificate
Selecting the appropriate user certificate
 Choosing the right computer certificate
Choosing the right computer certificate
Everyone knows that certificates are a good thing. Far fewer people understand what a certificate is and how it works.
When you go to a website, you might check that the site is using HTTPS. But what does the HTTPS actually mean? Its short for HyperText Transfer Protocol over SSL (which stands for Secure Sockets Layer). A certificate is used to secure the communication channel.
In this chapter, I explain certificates in general and tell you what type of certificates can be issued with Active Directory Certificate Services (AD CS). The certificates I discuss in this chapter are definitely not an exhaustive list, but they are some of the more commonly used certificates.
Certificates in Windows Server 2019
Windows Server 2019 provides AD CS, which is the focus of the next chapter in this minibook. AD CS allows you to stand up your own public key infrastructure (PKI), which allows you to issue certificates for users and internal systems that are trusted.
You can still install certificates from third-party certificate authorities, like GoDaddy and DigiCert; in fact, this is a must if the certificate is securing a resource that people outside your organization will access. However, if a resource will only be accessed by people within your organization, then it’s a prime candidate for an internal certificate issued by your organization’s PKI. This saves you the expense of the external certificate as well.
Cryptography 101
Cryptography is used to secure data in transit and at rest. Cryptography uses mathematical algorithms to generate “keys,” which are used to encrypt data. A single key may be used that can encrypt and decrypt the data (see “Symmetric cryptography”), or you may have a private key and a public key, which are mathematically linked. One key encrypts and the other decrypts (see “Asymmetric cryptography”).
There are two types of cryptography: symmetric and asymmetric.
Symmetric cryptography
Symmetric cryptography is the ability to encrypt and decrypt with the same key. When you’re using a shared secret or a password, you can think of that as symmetric cryptography. Because it only uses one key, it’s faster, but it’s also less secure because an attacker would only need to find out what the key is to decrypt the data. You can see a diagram of how symmetric cryptography works in Figure 5-1.
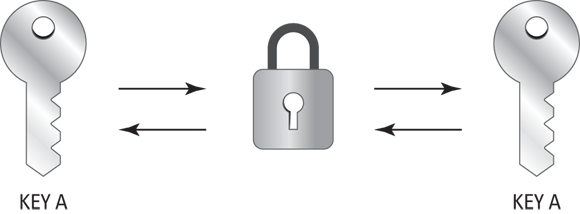
FIGURE 5-1: Symmetric cryptography uses one key to encrypt and decrypt data.
Some common symmetric ciphers include
- 3DES
- AES
- TwoFish
- BlowFish
- IDEA
Asymmetric cryptography
Asymmetric cryptography (or public key cryptography) is an encryption scheme where data is encrypted by one key and decrypted by another key. The keys are mathematically linked and will only work with each other. The private key is kept safe and offers non-repudiation (meaning that it can prove identity) because it isn’t distributed. The public key is given to others and is used to decrypt data that was encrypted by the private key. Asymmetric cryptography is what is used in public key infrastructure (PKI). A common example of asymmetric cryptography is when you use HTTPS. Say you go to your bank’s website. Your browser is presented with the public certificate, which it uses to encrypt and decrypt traffic with the bank’s web servers. Your bank’s web servers have the private key, which proves that the bank is who it says it is, and allows the bank to decrypt your traffic. You can see a diagram of how asymmetric cryptography works at a high level in Figure 5-2.
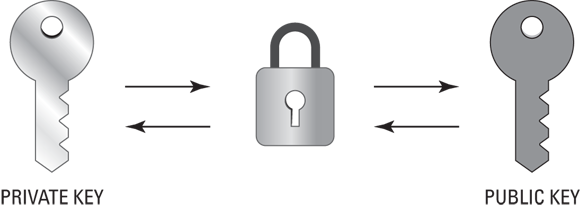
FIGURE 5-2: Asymmetric cryptography uses two mathematically linked keys to encrypt and decrypt data.
Certificates fall under asymmetric cryptography. When you need to create a certificate, you generate a private key, and then a certificate signing request (CSR), which is an encoded representation of your public key. The CSR is given to a certificate authority, internal or external, and the certificate is created from there. The private key never leaves your possession.
Common asymmetric ciphers include
- Diffie-Hellman
- DSS\DSA
- RSA
- ECDH
- ECDSA
Certificate-specific concepts
No introduction to certificates or cryptography would be complete without clearing up a few terms. If you understand these terms, then this chapter and the next will be a lot simpler:
- CRL: The Certificate Revocation List keeps track of certificates that have been revoked, which makes them no longer valid. By default, the base CRL is updated every seven days, and the delta CRL is updated once a day.
- OCSP: The Online Certificate Status Protocol gives near real-time revocation information on certificates. This is an improvement over using strictly CRLs because CRLs don’t update as frequently.
- FQDN: A Fully Qualified Domain Name is the hostname and domain name. For instance,
Server2.sometestorg.comwould be an FQDN. - CN: The common name on the certificate is typically going to be the same as the FQDN.
- SAN: Subject Alternative Names allow you to add more names to a certificate than just the common name. This is useful when you need to support short names and IP addresses, especially for development work. You can add whole other FQDNs as well, which makes these certificates very useful when you want to avoid wildcard certificates.
- Wildcard certificate: A certificate that is essentially valid for any host on your domain. A wildcard for
sometestorg.comwould be expressed as*.sometestorg.com. Wildcard certificates can be used to save money to secure multiple websites and/or servers.
Types of Certificates in Active Directory Certificate Services
There are many types of certificates in AD CS. The standard non-domain-joined server has a set of certificate templates out of the box, but a domain-joined Enterprise certificate authority (CA) has even more certificate templates to choose from.
In the following section, I discuss the more common types of user and computer certificates that you encounter, and what their uses are.
User certificates
User certificates are all about — you guessed it — the users. These certificates are typically used to establish the identity of a user. Here are some of the more common User certificate types that you may run into:
- User: This certificate template is used for the traditional authentication-style certificate. It’s most commonly used in two-factor authentication (2FA) solutions as the second factor of authentication, after username and password. This is especially popular with virtual private network (VPN) solutions. You can always look at the template on the issuing CA, and it will tell you what purposes it’s approved for. In Figure 5-3, you can see the template properties for the User template.
-
Code Signing: When you need to run internal PowerShell scripts or executables and you want to ensure that they haven’t been changed or altered in any way, you want a code signing certificate. The Code Signing certificate validates that the code has not been changed or altered in any way since it was last signed. If you want to run remote PowerShell scripts, this is a great way to ensure that only good, tested scripts are run from authorized users because you can set the permissions on who can enroll with the template, as well as the execution policy of PowerShell scripts in your environment.
 Encrypting File System (EFS) can be used to encrypt files or folders and can only be decrypted by the user who encrypted them or an authorized recovery agent (EFS Recovery Agent). Please note that this is different from BitLocker, which offers full disk encryption, not file/folder-level encryption.
Encrypting File System (EFS) can be used to encrypt files or folders and can only be decrypted by the user who encrypted them or an authorized recovery agent (EFS Recovery Agent). Please note that this is different from BitLocker, which offers full disk encryption, not file/folder-level encryption. - Basic EFS: If you’re using EFS, your systems will automatically request a Basic EFS certificate from one of your certificate authorities the first time one of your users tried to encrypt a file, assuming they don’t already have a User certificate already. The Basic EFS certificate is used for EFS operations exclusively.
- EFS Recovery Agent: This certificate template is also used in conjunction with EFS, but it’s used to decrypt data that has been encrypted by EFS. This may be due to someone leaving the company or having been terminated. It may even be an accidental deletion. With the EFS Recovery Agent certificate, the data can be decrypted. By default, all members of the Domain Admins and Enterprise Admins groups can enroll in this certificate.
-
Key Recovery Agent: The Key Recovery Agent certificate is used by an authorized administrator to decrypt private keys. It can be used to recover private keys assuming that the CA has been configured to archive and allow recovery of the private key that is associated with the public key it was given when a certificate was requested. This template should be used very sparingly because it gives the user with the certificate the ability to recover private keys and, by extension, the ability to decrypt the data encrypted by the certificates to which the private key belongs.
 It is considered a best practice by Microsoft to use separation of duties if you want to utilize the Key Recovery Agent template. The recommendation is to allow someone in the Certificate Manager role to retrieve the private key but not decrypt it, and to allow the Key Recovery Agent to decrypt the private key but not retrieve it. This provides better safeguards to organizational data because no one person can decrypt all data.
It is considered a best practice by Microsoft to use separation of duties if you want to utilize the Key Recovery Agent template. The recommendation is to allow someone in the Certificate Manager role to retrieve the private key but not decrypt it, and to allow the Key Recovery Agent to decrypt the private key but not retrieve it. This provides better safeguards to organizational data because no one person can decrypt all data.
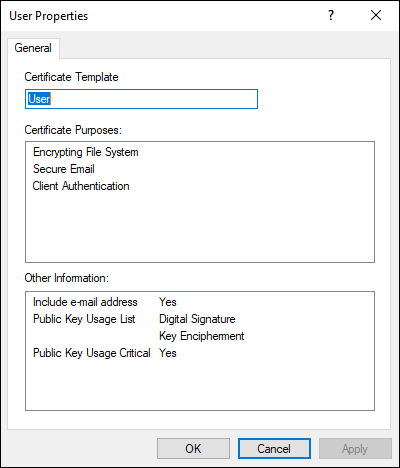
FIGURE 5-3: The User certificate template is good for EFS, secure email, and client authentication.
Computer
Computer certificates are similar to user certificates in that they’re verifying identity. The main difference is that they’re verifying the identity of a machine rather than the identity of a user. Here are some of the more common Computer certificate templates and their uses:
- Computer: The Computer template can be used for both workstations and servers. This is often used for VPNs to determine whether a system is authorized, but it can also be used for encryption. By default, the name of the system is pulled from Active Directory, though it can be made a manual process. You can always look at the template on the issuing CA and it will tell you what purposes it’s approved for. In Figure 5-4, you can see the template properties for the Computer template.
- Domain Controller: The Domain Controller template is good for both client and server authentication, as well as the use of smart card logon support. The biggest difference between it and the Computer template is that the Domain Controller template is designed to help facilitate secure replication between domain controllers. I always recommend making sure that your domain controllers have a certificate from this template because it allows them to support Lightweight Directory Access Protocol (LDAP) over SSL (LDAPS), which encrypts authentication traffic across the wire. By default, the name of the system is pulled from Active Directory, though it can be made a manual process.
- Web Server: The Web Server template is used for supporting HTTPS on internal websites. This template is typically one that you would want to set up to ask for the common name and any storage area networks (SANs) that you want to use so that users don’t get certificate untrusted messages. For internal certs, I often use the FQDN for the CN, and will add the short name and IP address as SANs.
- Subordinate Certification Authority: This is the template used by a root or issuing certificate authority to issue certificates to subordinate certificate authorities. This deals a little more with the hierarchy of certificate authorities, which is covered in the next chapter. Simply put, this template is used on any system that sits in the certificate issuing chain between the root CA and the end user or system’s certificate. It’s one of the few certificate templates that does not have an intended purpose added into the description of the template. In fact, if you look at its intended purpose, it simply says, “All.”
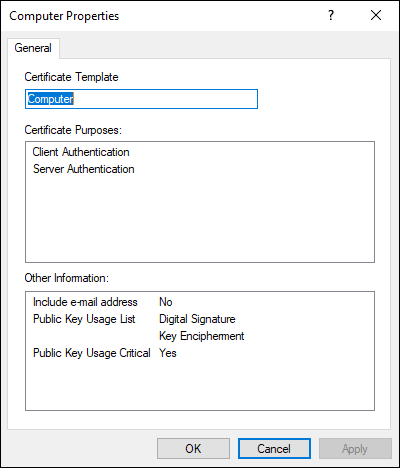
FIGURE 5-4: The Computer template provides client and server authentication.