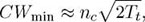
In the highly dynamic vehicular environment, congestion control is essential, especially with regard to safety messages. Although a dedicated spectrum has been allocated for vehicular communications, the European 30 MHz Intelligent Transportation System (ITS) band (with a possible extension to 50 MHz) or the US 75 MHz Direct Short Range Communication (DSRC) band still represent a scarce resource and need efficient mechanisms in order to be optimally used under high vehicular density. In both Europe and the US, the allocated spectrum has been divided into 10 MHz channels. From these channels, one is known as the control channel (CCH) and it is used solely by road safety applications. The rest of the channels, called service channels (SCH), can be used by both safety and non-safety applications.
The number of proposed vehicular safety applications that could use direct vehicle to vehicle (V2V) communication is impressive [PAP 09]. However, at a close inspection, it can be noted that all these applications practically use the same information, coming from onboard sensors of neighboring vehicles: speed, acceleration, steering angle and location.
Considering this, the standardization bodies decided to add a supplementary layer between the applications and the transport protocol. The role of this layer, called message sublayer in the IEEE Wireless Access in Vehicular Environments (WAVE) architecture and facilities layer in the ETSI ITS terminology, is to keep an accurate image of the surrounding environment inside every vehicle and to provide applications with the desired information.
The facilities layer only needs two types of messages in order to achieve these objectives, called (in the ETSI ITS architecture) cooperative awareness message (CAM) and decentralized environmental notification message (DENM). CAMs are regular beacons, transmitted by every vehicle with a predetermined frequency, and containing details about the vehicle that might be relevant to its neighbors from a safety point of view. In addition, if a vehicle detects a potential hazard (e.g. a sudden brake) and considers that this information needs to be quickly disseminated to the other traffic participants, it transmits a DENM.
However, regardless of the scenario and message type, these safety messages are always transmitted in broadcast mode at the medium access control (MAC) layer. Even in the case when the transmitted information targets a certain geographical area (e.g. an electronic brake alarm is only of interest to vehicles traveling in the same direction as the transmitter and situated behind it), the message is still broadcast and the filtering happens at the facilities layer, as described by the ETSI framework [EUR 10].
The broadcast nature of the CCH in vehicular ad hoc networks (VANET) is an essential property that distinguishes it from other IEEE 802.11-based networks. As a matter of fact, the numerous studies on the distributed coordination function (DCF) implementing MAC mechanisms in IEEE 802.11 usually focus on unicast traffic, and broadcast messages are only considered for control purposes. Oliveira et al. [OLI 09] quantify the influence of broadcast traffic on the performance of IEEE 802.11 networks, and they find out that the effect of broadcast messages becomes significant when the proportion of broadcast traffic is higher than 50%. In this scenario, the behavior of the network largely deviates from what is predicted by classic DCF models. However, the authors consider this situation quite unreal and they do not investigate the issue further.
Another important characteristic of safety messages comes from the limited lifetime of CAMs. As these beacons are produced periodically by the facilities layer, there is a certain probability that they can expire before the MAC layer has the opportunity to transmit them. When a CAM is waiting for the IEEE 802.11 back-off timer to expire, and the next beacon also arrives in the transmission queue, the first message has to be dropped, as its transmission would only disseminate outdated information to its neighbors. This property, rarely taken into consideration in VANET studies, has a significant effect on the optimal value of different MAC layer parameters.
The IEEE 802.11p amendment [THE 10] is the preferred MAC technology in both the IEEE WAVE and the ETSI ITS architectures. IEEE 802.11p radios can communicate at a distance of 1 km. In a simple scenario, with a two-lane road in both directions and an average inter-vehicular distance of 50 m (a medium density highway), the number of one-hop neighbors reaches 160 vehicles. This is clearly a more challenging environment than the classic Wireless Local Area Network (WLAN), with a central access point and no more than 10–20 nodes. The MAC layer protocol, therefore, needs solutions for this congested environment to achieve scalability.
Congestion control mechanisms received a lot of attention from the VANET research community and the most relevant studies in this area are summarized later. The standardization bodies also recognized the importance of a decentralized congestion control framework for V2V safety communications, and ETSI published a series of technical specifications in this area in July 2011 [EUR 11]. In the US, the Society of Automotive Engineers (SAE) is also developing a standard with similar objectives, SAE J2945.1, currently in a draft phase. SAE J2945.1 is expected to be integrated into the WAVE architecture as a complement for the different IEEE standards.
In this chapter, five different approaches for MAC layer congestion control are discussed. In section 1.2, beaconing frequency adaptation is presented that reduces the number of transmitted safety messages in a dense network, speculating the relationship between high density and reduced speed in vehicular traffic. In section 1.3, increased data rates can be achieved by using more complex modulations and result in a lower occupancy of the CCH. Other proposals form the object of section 1.4, which are based on the fact that transmission power control has an important impact on the number of hidden nodes, and can increase the spatial reuse and hence the channel capacity, in a congested network. In section 1.5, the fourth element, the minimum contention window (CWmin), is analyzed, a parameter with a major importance for collision probability in an IEEE 802.11 network. Finally, the role of the physical carrier sense in congestion control is highlighted in section 1.6.
The most obvious solution for controlling the channel load in a congested environment is to reduce the number of transmitted messages. This can be achieved in a straightforward manner in vehicular networks by adapting the frequency of the safety beaconing. However, such an adaptive mechanism should be designed carefully because sending less messages can easily have the effect of damaging the performance of safety applications instead of improving it.
In this context, Fukui et al. [FUK 02] proposed transmitting a CAM every time the vehicle travels a certain distance instead of using a regular time interval. According to a fundamental relationship from traffic theory, the mean speed decreases when the vehicular density increases, thus the consequence of this approach would be that nodes would reduce the beaconing frequency in a dense network where they would travel at low speeds. However, a basic example for which this solution fails is that of a vehicle waiting to make a left turn in normal traffic. Because the vehicle would need to stop, the adaptive mechanism would practically turn off the beaconing transmission, making an application like the left turn assistant practically unusable. Therefore, as stationary vehicles or low speeds are not always the consequences of high vehicular densities, such an approach cannot be efficiently used in a real scenario.
As a part of the California PATH program, Rezaei et al. [REZ 07] take a more complex approach, where vehicles run an estimator to calculate the position of each one-hop neighbor based on the already received messages. The same estimator is used by the node to predict its own position, as it would be calculated by its neighbors. When the difference between the prediction and the actual location becomes larger than a predefined threshold, the node transmits a safety beacon. The problem with this solution is that it is efficient in the predictable free-flow traffic, but not in a congested scenario where the acceleration is highly variable. Moreover, this self-estimator approach does not take into account that the error at some of the neighbors might be considerably different because some of the transmitted beacons could be lost. To solve this problem, Huang et al. [HUA 10] further develop this idea using the packet error ratio (PER) measured by a node to predict the losses encountered by its neighbors. Still, measuring a PER in a vehicular network without being able to detect collisions or use feedback from the receivers is not a straightforward task.
Seo et al. [SEO 10] make an analogy between the safety beaconing and the coupon collector problem. The mechanism they design relies upon nodes piggybacking acknowledgments (ACKs) for the received beacons in their own safety message. Every received ACK would further delay the transmission of the next CAM, reducing the beaconing frequency. However, the introduced overhead would be significant, especially in a dense network (a 4 byte ACK for 50 one-hop neighbors would result in 200 extra bytes for every safety message). It is also unclear if this approach would be compatible with a security framework based on changing pseudonyms, like the approach currently proposed by the ETSI ITS architecture [PAP 08], because the ACK would need to include the identifier of the sender and most probably a sequence number for the acknowledged message.
Adaptive Traffic Beacon (ATB) is a solution/mechanism/ approach proposed by Sommer et al. [SOM 11], where the beaconing frequency is calculated based on two metrics: the channel quality and the message utility. The idea is to transmit only the most important messages in a congested network, reducing the offered load. Nevertheless, the channel quality is very sensitive to the number of collisions, which implies that the nodes are somehow supposed to detect such events, clearly a difficult task in a broadcast environment [STA 12]. Moreover, while different utility factors could help differentiate between CAMs and DENs, safety beacons would be difficult to prioritise, as they belong to the same message class. Finally, ATB increases the beaconing period to a mean of 3.6 s, clearly a value that does not comply with the delay requirements of most safety applications, which vary between 100 ms and 500 ms [PAP 09].
For more details on adaptive beaconing solutions, the reader is referred to the very comprehensive review paper by Schmidt et al. [SCH 10]. To conclude, while reducing the beaconing frequency is a powerful tool in congestion control, the consequences of this adjustment on every safety application should be taken into account. However, road safety applications will most likely not be standardized, and addressing the constraints imposed by proprietary solutions is a difficult task.
The standards from the IEEE 802.11 family provide multi-rate capability at the physical layer, but without specifying a particular approach for data rate adaptation. In wireless communications, a more complex modulation results in a higher data rate, but it also requires a higher signal-to-noise ratio (SNR) at the receiver in order to be correctly decoded. In the continuous fight for increased bandwidth, the search for an efficient data rate control solution in the very lucrative WLAN industry stimulated the research in this area, and two main classes of mechanisms have been designed.
The solutions in the first class are based on their choice for a certain modulation and coding rate on the success or failure of previously sent messages. For example, the Robust Rate Adaptation Algorithm (RRAA), proposed by Wong et al. [WON 06], calculates the frame loss ratio in a short time window and compares this value with two predefined thresholds. Too many losses determine a reduction in data rate, while a high percentage of successful transmissions results in the choice of a more complex modulation. The second type of mechanisms are based on feedback from the receiver regarding signal quality. A representative example in this class is receiver-based auto rate (RBAR), described by Holland et al. [HOL 01]. RBAR relies upon the idea of receivers measuring the channel quality by analyzing the Request To Send (RTS) message and calculating the highest achievable data rate based on the channel conditions. This information reaches the transmitter through the Clear To Send (CTS) message and the best modulation is set for the data frame.
The applicability of mechanisms from the two classes discussed above in a unicast vehicular network is studied experimentally by Camp and Knightly [CAM 08]. They show that, because of the highly variable vehicular channel, decisions based on historical data are not accurate in this environment, while the SNR-based mechanisms need to be trained in the target geographical region in order to cope with the short coherence time (around 300 μs when other vehicles are also present on the road).
In broadcast safety communications, solutions using feedback from the receivers are clearly unsuitable, therefore the data rate adaptation mechanisms proposed for vehicular safety messages follow the classic path of algorithms based on historical data. Mertens et al. [MER 08] use RRAA in their simulation study, showing a significant improvement in performance when compared with regular IEEE 802.11p. Nevertheless, they do not address the problem of computing the frame loss ratio in a VANET. A more innovative approach is proposed by Ruffini and Reumerman [RUF 05], building on the correctly received CAMs to create a map of the average path loss at different receivers and use this map to estimate the highest data rate that could be successfully used.
However, the data rate adaptation problem is not exactly equivalent in WLAN and in safety vehicular networks. In the first case, the goal is to maximize throughput by choosing the corresponding modulation. While the problem is, of course, difficult to solve, the existence of a solution cannot be questioned. In a VANET, the goal, as described in the different congestion control architectures, is to reduce the transmission time of a message when the vehicular density increases to give more stations the chance to access the channel during a beacon period. The choice of the modulation is not dictated in this case by the quality of the channel, but by the number of one-hop neighbors, and there is currently no proof that the assignment of a data rate based solely on the local node density could increase the beaconing reception ratio. Moreover, an experimental study led by General Motors R&D and presented by Bai et al. [BAI 10] argues that using Quadrature Phase-Shift Keying (QPSK) and a data rate of 6 Mb/s) is the only reasonable choice for V2V communications. In their tests, only two communicating vehicles have been used, ignoring therefore the impact of message collision or interference. Even in these idealistic conditions, any modulation resulting in a higher data rate drastically reduces the reception probability, even at small distances from the transmitter (less than 50% received beacons at 50 m using 18 Mb/s). Furthermore, even the more robust 3 Mb/s Binary Phase-Shift Keying (BPSK) modulation shows lower performance, because, in this case, the transmission time is larger than the coherence time (found to be around 300 μs, just like in [CAM 08]).
Considering these results, data rate adaptation mechanisms need to be better evaluated, especially using real hardware during field tests, before a decision relative to their usefulness in VANET congestion control can be taken.
Transmission power control is one of the most studied topics in the area of VANET congestion control. However, most of the proposed mechanisms are just variants of solutions previously proposed in a mobile ad hoc network (MANET) context, where the objective of adjusting the transmission power is to minimize energy consumption while keeping a connected network. For example, Chigan and Li [CHI 07] use a directional antenna approach originally designed for topology control in MANETs to obtain the minimal power needed to transmit messages only to the closest vehicle on each direction. Similarly, Yoon and Kim [YOO 11] adapt transmission power with the objective of keeping a constant number of one-hop neighbors.
Nevertheless, these solutions are not appropriate for a safety VANET, where messages need to cover a minimal distance, not a certain number of neighbors. With these requirements in mind, Guan et al. [GUA 07] define a target range for safety messages. When a node receives a message, it calculates the distance from the sender and verifies if it is positioned inside the target range. Vehicles receiving a beacon despite being outside the target range include the identifier of the transmitter in a special feedback field in their own beacon. Using the information in this field, a station can calculate how many nodes outside the target range were reached by its transmission and the goal of the power control mechanism is to keep this number between certain limits.
Another proposal using special feedback piggybacked in the CAMs is the distributed fair power adjustment for vehicular environments (D-FPAV) strategy described by Torrent-Moreno et al. [TOR 09]. D-FPAV defines a maximum beaconing load (MBL) that can be accommodated by the CCH while still having spare bandwidth in the eventuality of a special notification. A distributed algorithm ensures an optimal power level assignment, where vehicles use the maximal possible power that still respects the MBL constraint. However, this optimality is achieved only when the power levels used by all the two-hop neighbors are known.
Because the overhead introduced by D-FPAV is significant, especially under high node density when saving bandwidth is the most important, Mittag el al. [MIT 08] designed segment-based power adjustment for vehicular environments (SPAV). SPAV on the one hand does not achieve an optimal assignment like D-FPAV, but on the other hand it does not require full knowledge about the power levels used by different neighbors, but only an estimate of the local density that can be obtained in a much more inexpensive manner.
The local node density (estimated, for example, from the received beacons) is also used in the computation of the transmission power by Rawat et al. [RAW 09], but in this case the transmission range is calculated using results from traffic flow theory. Artimy [ART 07] manages to entirely eliminate the overhead for transmission power control, using only data from the onboard speedometer to estimate the local density, again using fundamental relationships from traffic flow theory.
While calculating local density based on the CAMs received from the other vehicles is considered a natural property of the safety beaconing, this task might be complicated by the use of changing pseudonyms. Huang et al. [HUA 10] propose a solution that can cope with the VANET security requirements. In their framework, a node simply measures the channel occupancy from the information provided by the clear channel assignment (CCA) function. If the percentage of time the medium is sensed as busy in the last beaconing period is under a certain threshold Umin, the node uses the highest power level, otherwise a linear mapping between the channel occupancy and transmission power is used.
Because of its excellent properties and its feasibility using existing hardware, transmission power control is considered as a central mechanism for congestion control in VANETs and it has been included in the ETSI ITS decentralized congestion control framework [EUR 11].
The minimum contention window (CWmin) is one of the most important parameters of the IEEE 802.11 MAC layer. CWmin represents the initial value of the CW, the superior limit of the interval from which the back-off mechanism draws the number of idle slots the station has to wait before attempting a transmission. For unicast communication, the value of CW is doubled every time an expected ACK message is not received within a predefined delay and it is reset to CWmin for every acknowledged reception, leading to the so-called binary exponential back-off (BEB) mechanism.
Even before the release of the first version of the IEEE 802.11 standard, Bianchi et al. [BIA 96] showed that the optimal value for CWmin depends on the number of contending stations. More exactly, their analysis shows that, in a saturated WLAN, the throughput is maximized when:
where nc is the number of nodes in the network and Tt is the time needed to transmit the message (acknowledgment included). Building on these results, Cali et al. [CAL 00] determined that the protocol’s performance peaks when the time the channel is idle due to the back-off mechanism equals the time the channel is occupied by collisions (Tidle = Tcol).
Despite this well-known property, the IEEE 802.11 standard does not include any mechanism for the adjustment of CWmin when the number of contending stations grows. The main reason for this was that the protocol was designed for WLANs, with a central access point and a limited number of client stations (usually no more than 20) in mind. A second argument came from the use of the RTS/CTS handshake. In this case, collisions are limited to the short RTS and CTS messages, and therefore the time the channel is busy due to collisions is decreased. This implies that, for an optimal functioning, Tidle also needs to be reduced, which requires a lower CW. Moreover, with the massive success of multimedia services, and with the introduction of the IEEE 802.11e standard, the minimum CW has been reduced even more, in order to minimize the delay experienced by sensitive video and voice applications. The idea, in this case, was that most users, especially residential users, connect only a reduced number of devices to their access points, and generally use only one or two of them simultaneously. A reduced CW improves the MAC layer performance in this case, while the BEB mechanism is there as a back up for the cases when the number of contending stations increases.
An impressive number of modified back-off mechanisms have been designed in different WLAN scenarios, and Razafindralambo and Valois [RAZ 06] compare the performance of the most significant of these proposals. Most of the solutions considered in this unicast context still require a fixed value for CWmin and only modify the back-off mechanism. For example, Wang et al. [WAN 04] argue that when a transmission succeeds after a number of failures it is not correct to reset the CW to its minimal value, because the congestion will continue to exist on the channel. They propose a slower decrease of CW, and only after several acknowledged transmissions in a row. However, Medepalli and Tobagi [MED 06] proved analytically that the impact of CWmin on the throughput of a network is much more significant than the influence of the back-off mechanism.
For more than a decade, all the IEEE 802.11 enhancements related to CWmin adaptation in MANETs belonged to one of the two categories. The methods in the first class (e.g. [KIM 05]) estimate the number of contending stations in the two-hop neighborhood and use equation [1.1] or some variants to calculate the optimal CW. The second type of mechanisms consider the overhead introduced by the local density estimation as prohibitive, and the amount of time the channel is sensed as idle and the number of collisions are measured instead. The CW is adjusted, in this case, in order to keep the equality Tidle = Tcol valid: when there are too many collisions on the channel, the back-off time (and with it the idle time) is increased, while when the channel is idle for long time durations, the CW is reduced. A notable example from this second class is IdleSense, proposed by Heusse et al. [HEU 05].
Nevertheless, in 2008, Jiang and Walrand [JIA 10] took a completely different approach concerning the back-off mechanism in carrier sense multiple access (CSMA) networks, proposing optimal CSMA (oCSMA). The idea behind this new protocol is to adapt the CW of a node as a function of its queue length. In oCSMA, a node begins with an initial value for contention aggressiveness (which can be easily translated into a certain CWmin) and, when the number of messages in a link queue increases, the transmitter becomes more aggressive in the competition for channel access. Despite having very low complexity and requiring only local information, oCSMA has been proven to achieve throughput optimality under both continuous-time and discrete-time back-off duration [KIM 11], and was implemented using off-the-shelf IEEE 802.11 hardware [NAR 11].
With all these interesting studies coming from related research fields, we might believe that it should be rather straightforward to study and understand the impact of the CW in V2V communications. However, the particularities of the vehicular network translate once again into unique properties that modify the problem entirely. In a VANET, the node density is highly variable and a station can go, within a few minutes, from a vary sparse environment to several hundred contending neighbors. In addition to the fact that the RTS/CTS handshake cannot be implemented and the BEB mechanism is deactivated by the lack of ACK messages, none of the properties that allowed the use of a small CW in IEEE 802.11 WLANs hold in this scenario.
An adaptive mechanism is therefore needed, but a rapid analysis of the compatibility between the solutions described above and the safety VANET shows that the design of this mechanism is not exactly a simple formality. The Bianchi relationship is true for a unicast saturated one-hop WLAN cell, while a safety vehicular network is neither saturated nor fully connected. In addition, collisions remain difficult to detect in V2V communication, therefore IdleSense and other similar approaches cannot be directly transposed in a vehicular environment. Finally, because expired beacons are dropped, the MAC layer always has at most one safety message to transmit [STA 12], and the queue length cannot determine the CW as proposed in oCSMA. Moreover, the goal of all these mechanisms is to maximize throughput, an objective that is not shared by a safety vehicular network.
The few proposals for CW adaptation issued from the VANET research community failed to consider these important differences. Rawat et al. [RAW 09] propose a heuristic based on the number of detected collisions, where the CW is increased if the number of collided messages is higher than a predefined threshold. However, the threshold does not depend on the local node density and the technique used for collision detection is not described. The same critique applies to Mertens et al. [MER 08], who, in a first phase, estimate the local node density and directly use this result in equation [1.1]. Then, they further refine the value of the CW by increasing CWmin when the percentage of lost beacons becomes higher than a target PER. Balon and Guo [BAL 06] address this issue of measuring the percentage of lost beacons by using the sequence numbers inside the safety messages, which might not be compatible with a privacy framework based on pseudonyms.
In a similar manner, Wang et al. [WAN 08] design a heuristic relying upon the channel busy time measured by the CCA function during a predefined time period. In their solution, if the channel busy time increases between two consecutive measures, the CW grows linearly with the observed difference. In the opposite case, CW is reduced, also using a linear relationship. Although the efficiency of this mechanism depends on the initial value of the CW, the authors do not provide any guidelines for the choice of this parameter.
Meanwhile, Jang and Feng [JAN 10] establish a relationship between the number of contending stations and the optimal back-off time in a vehicular network, but their study is focused on unicast communication using RTS and CTS control messages. Finally, Alapati et al. [ALA 10] try to maximize throughput using a type of probing mechanism, where the node tests different values for CWmin until an optimum is reached. The problem comes from the fact that this optimum depends on the local density that might vary faster than the convergence speed of the algorithm.
On the basis of these observations, five different mechanisms for CW control in a vehicular environment have been adapted from solutions proposed in the research literature, but not necessarily related to CWmin adjustment. The properties and feasibility of these mechanisms are characterized below, followed by the results of a simulation study using the Java in simulation time/scalable wireless ad hoc network simulator (JiST/SWANS) framework [JAV] and the street random waypoint (STRAW) mobility model [CHO 05].
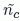 , determined this way, cannot be directly applied in Bianchi’s equation, even though Tt would be very easy to calculate for fixed-size CAMs. In this case, not only does the VANET not correspond to the original assumptions of a full connected saturated network, but also the accuracy of the estimation
, determined this way, cannot be directly applied in Bianchi’s equation, even though Tt would be very easy to calculate for fixed-size CAMs. In this case, not only does the VANET not correspond to the original assumptions of a full connected saturated network, but also the accuracy of the estimation 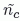 depends on the beaconing reception ration.
depends on the beaconing reception ration.Therefore, instead of using equation [1.1] directly, the first studied mechanism keeps this linear dependency, but uses a more general formula to calculate the CW:
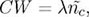
where λ is a parameter depending on the size of the beacon, and whose optimal value was explored through simulation.
This solution would be relatively simple to implement because the addresses of the neighbors will be stored anyway for routing purposes, therefore a simple counter is needed. Nevertheless, repeatedly changing the pseudonyms of a node for privacy purposes could have a non-negligible impact on the performance of this solution (and also on the routing protocol).
The main advantage of this mechanism is that it tries to directly optimize the percentage of delivered beacons. However, the coexistence of a solution based on sequence numbers and a security protocol using changing pseudonyms appears to be extremely difficult. When a vehicle would change its identifiers, it would also need to reset its sequence counter and, therefore, tracking the lost beacons at the receiver level would become an important problem.
As in the previous algorithm, CW(0) = CWdef and a new value is computed every Tupdate seconds:

where α > 1 is a parameter whose value was explored through simulation.
The simple idea behind this solution is that if there are too many colliding messages, the CW should be increased, while CW should be decremented when the channel is idle for an important amount of time. This proposal presents the same advantages and drawbacks as the previous proposal. A supplementary implementation problem could come from the fact that the station requires the capacity to measure Tidle, a feature that is not currently available in all IEEE 802.11 devices.
The following algorithm is inspired by the approach taken in [ART 07] for transmission power control, where the vehicular density is estimated based on the time the car stops in traffic. Therefore, the vehicle needs to measure the stop time (Tstop) in the last Tupdate time window. If Tstop = 0, the traffic is in a free-flow state and the CW is set to CWmin. If Tstop = Tupdate, the vehicle is considered to be a part of a traffic jam and CW = CWmax. For intermediate values, the following formula is used:
The mechanism could be implemented without any additional hardware, as the stop time can already be calculated using data from the speedometer. The problem could lie in the fact that a vehicle might stop for several other reasons than a traffic jam, especially in an urban scenario.

where Dl = |jerk|/speed, and Dmax is the predefined upper threshold.
Although this approach uses more information than the previous approach, it still lacks the ability to handle, without any delay, some situations common to city traffic, which result in a low speed without necessarily implying a high vehicular density (e.g. left-turn and stop sign). Moreover, jerk is not currently measured on a regular basis in vehicles.
The behavior of these five mechanisms has been compared with the original IEEE 802.11p under medium and high vehicular density, with a traffic volume varying between 40 vehicles/km and 80 vehicles/km. In a first phase, simulations were run in order for each of the above algorithms to be optimized with regard to the different parameters that have an impact on their performance. The tested values and those that achieved the best performance for each parameter are shown in Table 1.1. In the case of IEEE 802.11p, a value of 7 has been used for CWmin. This is equivalent to the value mentioned in the standard for the access category with the second highest priority [THE 10].
Table 1.1. Optimal values for the different parameters of the algorithms
| parameter | Tested values | Optimal value |
| Tupdate | 1 s, 5 s, 10 s, 20 s | 5s |
| λ | 0.25, 0.5, 1, 2 | 0.5 |
| PERmin/PERmax | 5%/10%, 10%/15%, 15%/20% | 5%/10% |
| α | 1, 1.1, 1.2, 1.3, 1.4 | 1.1 |
| dcol | 100 m, 150 m, 200 m, 250 m | 200 m |
| CWmax | 40, 50, 60 | 50 |
| Dmax | 2, 2.5, 3, 3.5 | 3 |
The metric used for this optimization and for the comparison was the beaconing reception probability at a distance of less than 200 m from the source vehicle. This metric is considered to be particularly suitable because it includes in a single value both the probability of collision and the probability of an expired beacon. Moreover, because a beacon that cannot be sent with the required time delay expires, all the received messages respect the imposed time constraints and therefore the analysis of the average delay becomes less important.
The beaconing reception probabilities for the studied solutions can be observed in Figure 1.1. To better understand the behavior of each mechanism, Figure 1.2 shows the average CW as a function of vehicular density.
Figure 1.1. Beaconing reception probability (including expired beacons) using IEEE 802.11p and the five mechanisms described in this chapter for different vehicular densities (the 95% confidence interval is also shown)
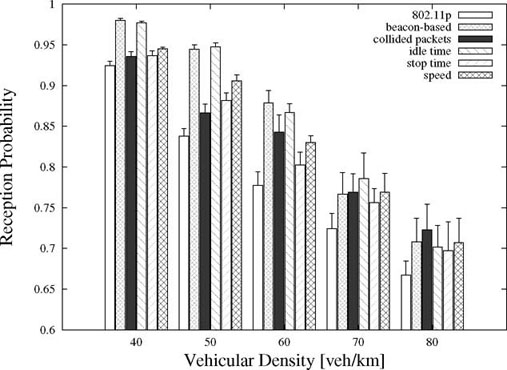
The first thing that can be noted from the data is that all the five solutions show better performance than the basic mechanism, with a difference that can reach more than 10%. Estimating the number of neighbors using the received beacons gives the best results for a vehicular density under 60 cars/km. The idle time approach also gives similar results, showing that the estimation used for Tcol is quite accurate. However, even though the beacon-based and idle time algorithms show similar results for the CAM reception probability, they achieve this through different means, as it can be seen from the dissimilar average values of the CW. As expected, the beacon-based approach shows a linear increase of CW with the number of vehicles. Therefore, under high density, the nodes back-off for an important amount of time, which leads to an increased number of expired beacons. Moreover, when using the idle time mechanism, the CW converges to an average value of only 36. In this case, the majority of lost messages are due to collisions and the number of expired CAMs is much lower.
An interesting result is obtained when adjusting CW based on the number of lost packets. When the PER is below PERmax (10% in this case), the algorithm almost always uses the default value for CW (CWaverage = 7.5) and its results are similar with those of the basic IEEE 802.11p. However, when the vehicular density increases and more beacons start colliding, the mechanism starts increasing the CW and its performance drastically improves, showing the best results for a density of 80 vehicles/lane/km. Using a lower value for PERmax increases the efficiency of this solution in low density, it also highly degrades its performance when the number of vehicles becomes more important, indicating that dynamic thresholds would be an interesting approach in this case.
The two solutions inspired from traffic-flow theory also perform better than IEEE 802.11p. However, for the lower values of the vehicular density, their results are not as good as those of the beacon-based or idle sense mechanisms. This is because, in these traffic conditions, vehicles are usually in a free-flow state and they rarely stop or modify their speed in order to increase their CW. Nevertheless, when the number of cars increases, the mobility pattern is also altered and the two algorithms show similar results with the other strategies. It is also important to note that the approach based on cars’ speed and jerk always achieves a better reception probability than the approach based on stop time, because it uses a more detailed relationship between car movement and density. Moreover, a very significant property of these two mechanisms is that they can be used together with security solutions based on pseudonyms.
Figure 1.2. Average contention window (CW) as a function of vehicular density for the analyzed mechanisms
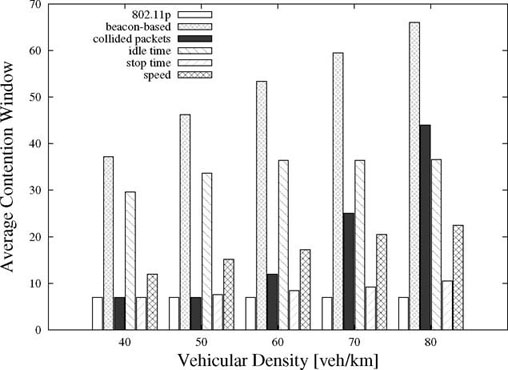
This comparative study shows the importance that the CW has on the MAC layer performance and argues against the use of a small back-off interval in the case of vehicular safety messages, where reliability is an essential parameter and collisions need to be avoided as much as possible.
The physical carrier sense mechanism is the core of any CSMA-based channel access technique, including the protocols from the IEEE 802.11 family. The concept is well-known and it is used in both wired and wireless networks: before a transmission, a node has to first sense the channel to make sure that it is not already occupied by another station.
The carrier sense method described in the IEEE 802.11 standard is based on two functions: Clear Channel Assignment (CCA) and Network Allocation Vector (NAV). NAV is also known as virtual carrier sense and is a MAC layer mechanism that uses special control messages – RTS and CTS – in order to reserve the medium for data transmission. CCA is a function of the Physical Layer Convergence Procedure (PLCP) layer and is in charge of physical carrier sensing.
In the case of the Orthogonal Frequency Division Multiplexing (OFDM) physical layer, CCA uses two mechanisms to assess the state of the channel: header detection and energy detection. The PLCP header, shown in Figure 1.3, is always sent using the most robust combination of modulation and coding rate. It contains information on the data rate used for the rest of the message and a LENGTH field indicating the number of bytes to be transmitted. A node capable of decoding the PLCP header calculates the time duration for which the channel will be occupied by this transmission and declares the channel busy for this entire duration, even if the reception of the rest of the message fails. If no PLCP header is detected, the CCA function measures the energy level present on the channel and compares it with a predefined value, called energy detection threshold (EDt). If the perceived energy level is larger than EDt, CCA declares the channel busy and denies any MAC layer transmission. To give a numerical example, in the IEEE 802.11p OFDM PHY, the receiver must have the capacity to detect any PLCP header arriving with a power level over −85 dBm and, if the PLCP header is missed, an EDt of −65 dBm is used.
Figure 1.3. Physical Layer Convergence Procedure (PLCP) header format

Despite the fact that the physical carrier sensing lays the foundation of an entire category of channel access methods, its impact on the MAC layer performance has received only little attention, at least compared with the recognition received by other parameters, such as transmission power or data rate.
One of the first studies that focused on physical carrier sensing in multi-hop networks was proposed by Zhu et al. [ZHU 04], who calculate the optimal carrier sense range for different networks with regular topologies. Their results demonstrate a relationship between the sensing threshold and the signal-to-interference ratio needed to decode the message. Soon afterwards, Yang and Vaidya [YAN 05] pointed out that the value of this optimal carrier sense threshold is higher if the PLCP header is transmitted using the minimum data rate considered. An essential finding came from Kim et al. [KIM 08], who discovered that the capacity of a multi-hop wireless network depends only on the ratio between transmission power and carrier sense threshold. In a follow-up of this study, Yang et al. [YAN 07] propose a mechanism for topology control through joint transmission power and carrier sense adaptation.
Nevertheless, all these studies have been conducted under the assumption of a pairwise interference model, unrealistic for safety V2V communications. Recently, Fu et al. [FU 10] calculated a safe carrier-sensing range that guarantees interference-safe transmissions under the cumulative interference model. The authors also propose a new mechanism, Incremental-Power Carrier-Sensing (IPCS), where the CCA is based on the history of the sensed power level and the medium is declared idle if a sufficient drop in the energy level is detected on the channel. Finally, following an experimental study with an indoor IEEE 802.11 testbed, Brodsky and Morris [BRO 09] conclude that a fixed carrier sense threshold is sufficient in short range networks (under 100 m wide), but it highly degrades MAC layer performance in long range networks, category that clearly includes VANETs.
In a similar case with the other congestion control mechanism, all these ideas are focused on maximizing throughput in wireless networks that do not exhibit the same properties as a safety VANET. The only existing results in the case of a vehicular network come from Schmidt et al. [SCH 10], who consider that in the case of safety communications the receivers should be more sensitive, using a lower carrier sense threshold that would allow them to detect transmissions even from vehicles situated far away. However, this assumption is not supported by any theoretical argument. An increased sensitivity would result in a higher carrier sense range, and therefore in more contending neighbors. The nodes would sense the channel as busy for a longer period and simultaneous transmissions would also be more probable. The remainder of this section is dedicated to a series of simulation results demonstrating the impact of the physical carrier sense threshold on the CAM reception ratio.
This simulation study measures the beaconing reception ratio for three different mean vehicular densities (25 veh/lane/km, 35 veh/lane/km and 45 veh/lane/km) while varying the carrier sense threshold (CSt) between −95 dBm and −55 dBm. The noise level assumed for these simulations peaks at −98 dBm, and an SNR ratio of at least 3dB is necessary for decoding the PLCP header, hence the minimal value of −95 dBm for CSt. This noise level can be considered relatively high, and the VANET physical channel is indeed very noisy, as it has been confirmed by experimental studies (e.g. [BAI 10]).
In Figure 1.4 the results obtained for a vehicular density of 35 veh/lane/km and three different carrier sense thresholds (−95 dBm, −79 dBm and −71 dBm) are shown. As expected, in all the cases the beaconing reception probability decreases with the distance from the sender. However, comparing what happens when CSt is modified from −95 dBm to −79 dBm, it can be observed that the reception ratio increases at a distance of less than 200 m from the sender and decreases beyond this distance.
This behavior can be explained by understanding that a collision can be the consequence of a simultaneous transmission (beginning exactly in the same slot) with a station from the carrier sense range, or the result of a concurrent transmission (the messages superpose on at least a slot) with a hidden node. A higher CSt reduces the number of sensed vehicles, and therefore the probability to consider the medium as busy. This allows more transmission opportunities for every node and reduces the number of simultaneous transmissions. However, on the negative side, because the carrier sense range is reduced, the degree of spatial reuse is increased and therefore concurrent transmission can occur from closer vehicles. This has little effect in the immediate neighborhood due to the capture effect, but produces collisions at higher distances.
Figure 1.4. Beaconing reception probability as a function of the distance from the sender for several carrier sense thresholds. The mean vehicular density in this case is 35 veh/lane/km. The 95% confidence interval has about the same size as the symbols and has not been included for visibility purposes
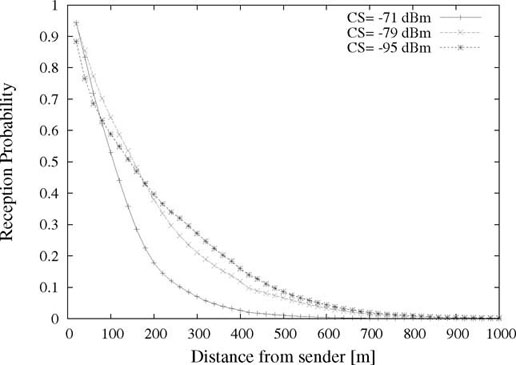
This phenomenon is exacerbated by further increasing CSt (from a value of −79 dBm to −71 dBm in Figure 1.4). As the physical carrier sense covers less and less space, the interferer gets closer to the sender and the Signal to Interference Ratio (SIR) increases, reducing the beaconing reception probability even for closely situated vehicles.
To better understand the influence of the carrier sense threshold on the reception of safety messages, the beaconing reception ratio at 50 m from the transmitter as a function of CSt for different vehicular densities is shown in Figure 1.5. It can be noted that the number of received beacons slowly increases with CSt, it reaches an optimal point and then drops quite sharply.
Figure 1.5. Beaconing reception probability as a function of the carrier sense threshold for different vehicular densities at a distance of 50 m from the sender. The 95% confidence intervals are also shown
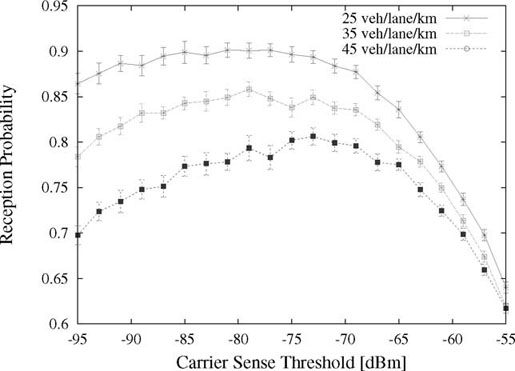
Two other important observations need to be made at this point, challenging the current view of using the minimum receiver sensitivity as a carrier sense threshold [SCH 10] and arguing in favor of a more elaborate solution. First, the difference between the peak value of the reception probability and the one obtained using the lowest possible value for CSt (−95 dBm in this case) can be significant, reaching almost 10% in the scenario with the highest density. Second, the optimal carrier sense threshold varies with the vehicular density, increasing when the number of neighbors becomes larger. This confirms the ideas formulated earlier in this chapter and shows the necessity of an adaptive mechanism for physical carrier sense control.
In this chapter, different techniques for congestion control in vehicular ad hoc networks have been described. These mechanisms can be divided into two classes: protocol agnostic solutions, which could work with any MAC protocol, and IEEE 802.11 dedicated solutions, designed specifically for the protocols in this family.
The chapter begins with a discussion on generic mechanisms, such as adaptive beaconing frequency, data rate control or transmission power adjustment. The most significant studies in each category are presented and the feasibility of these ideas is commented.
However, the focus of the chapter is on two parameters with a central role in IEEE 802.11, namely the CW of the back-off mechanism and the carrier sense threshold. Adaptive mechanisms for both of these parameters are presented and their performance is compared with the current version of the IEEE 802.11p standard. The improvement brought by choosing the correct value for these parameters is an important argument supporting the design of efficient mechanisms and their integration in the IEEE 802.11p protocol.
[ALA 10] ALAPATI J., PANDYA B., MERCHANT S., et al., “Back-off and retransmission strategies for throughput enhancement of broadcast transmissions in 802.11p”, Proceedings of the 21st IEEE Intelligent Vehicles Symposium (IV 2010), San Diego, pp. 700–705, June 2010.
[ART 07] ARTIMY M., “Local density estimation and dynamic transmission-range assignment in vehicular ad hoc networks”, IEEE Transactions on Intelligent Transportation Systems, vol. 8, no. 3, pp. 400–412, 2007.
[BAI 10] BAI F., STANCIL D., KRISHNAN H., “Toward understanding characteristics of dedicated short range communications (DSRC) from a perspective of vehicular network engineers”, Proceedings of the 16th ACM Annual International Conference on Mobile Computing and Networking (MOBICOM 2010), Chicago, pp. 329–340, September 2010.
[BAL 06] BALON N., GUO J., “Increasing broadcast reliability in vehicular ad hoc networks”, Proceedings of the 3rd ACM International Workshop on Vehicular Ad Hoc Networks (VANET 2006), Los Angeles, pp. 104–105, 2006.
[BIA 96] BIANCHI G., FRATTA L., OLIVERI M., “Performance evaluation and enhancement of the CSMA/CA MAC protocol for 802.11 wireless LANs”, Proceedings of the 7th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC 1996), Taipei, Taiwan, pp. 392–396, October 1996.
[BRO 09] BRODSKY M., MORRIS R., “In defense of wireless carrier sense”, Proceedings of the ACM SIGCOMM Conference on Data Communication (SIGCOMM 2009), Barcelona, Spain, pp. 147–158, August 2009.
[CAL 00] CALI F., CONTI M., GREGORI E., “Dynamic tuning of the IEEE 802.11 protocol to achieve a theoretical throughput limit”, IEEE/ACM Transactions on Networking, vol. 8, no. 6, pp. 785–799, 2000.
[CAM 08] CAMP J., KNIGHTLY E., “Modulation rate adaptation in urban and vehicular environments: cross-layer implementation and experimental evaluation”, Proceedings of the 14th ACM Annual International Conference on Mobile Computing and Networking (MOBICOM 2008), San Francisco, pp. 315–326, September 2008.
[CHI 07] CHIGAN C., LI J., “A delay-bounded dynamic interactive power control algorithm for VANETs”, Proceedings of the 42nd IEEE International Conference on Communications (ICC 2007), Glasgow, pp. 5849–5855, June 2007.
[CHO 05] CHOFFNES D., BUSTAMANTE E., “An integrated mobility and traffic model for vehicular wireless networks”, Proceedings of the 2nd ACM International Workshop on Vehicular Ad Hoc Networks (VANET 2005), Cologne, pp. 69–78, September 2005.
[EUR 10] EUROPEAN TELECOMMUNICATIONS STANDARDS INSTITUTE (ETSI), Intelligent Transport Systems (ITS) – vehicular communications – basic set of applications – part 1: functional requirements, ETSI TS 102 637-1 v1.1.1, September 2010.
[EUR 11] EUROPEAN TELECOMMUNICATIONS STANDARDS INSTITUTE (ETSI), ETSI TS 102 687 v1.1.1 – Intelligent Transport Systems (ITS) – decentralized congestion control mechanisms for intelligent transport systems operating in the 5 GHz range – access layer part, July 2011.
[FU 10] FU L., LIEW S., HUANG J., “Effective carrier sensing in CSMA networks under cumulative interference”, Proceedings of the 29th IEEE Annual International Conference on Computer Communications (INFOCOM 2010), San Diego, pp. 1–9, March 2010.
[FUK 02] FUKUI R., KOIKE H., OKADA H., “Dynamic Integrated Transmission Control (DITRAC) over Inter-Vehicle Communications in ITS”, Proceedings of the IEEE 55th Vehicular Technology Conference (VTC Spring 2002), Birmingham, pp. 483–487, May 2002.
[GUA 07] GUAN X., SENGUPTA R., KRISHNAN H., et al., “A feedback-based power control algorithm design for VANET”, Proceedings of the 1st IEEE Workshop on Mobile Networks for Vehicular Environments (MOVE 2007), Anchorage, pp. 67–72, May 2007.
[HEU 05] HEUSSE M., ROUSSEAU F., GUILLIER R., et al., “Idle sense: an optimal access method for high throughput and fairness in rate diverse wireless LANs”, Proceedings of the ACM SIGCOMM Conference on Data Communication (SIGCOMM 2005), Philadelphia, pp. 121–132, August 2005.
[HOL 01] HOLLAND G., VAIDYA N., BAHL P., “A rate-adaptive Mac protocol for multi-hop wireless networks”, Proceedings of the 7th Annual International Conference on Mobile Computing and Networking (MOBICOM 2001), Rome, Italy, pp. 236–251, July 2001.
[HUA 10] HUANG C., FALLAH Y., SENGUPTA R., et al., “Adaptive intervehicle communication control for cooperative safety systems”, IEEE Network, vol. 24, no. 1, pp. 6–13, 2010.
[JAN 10] JANG H.-C., FENG W.-C., “Network status detection-based dynamic adaptation of contention window in IEEE 802.11p”, Proceedings of the IEEE 71st Vehicular Technology Conference (VTC Spring 2010), Taipei, Taiwan, pp. 1–5, 2010.
[JAV] JAVA IN SIMULATION TIME FRAMEWORK (JiST), “The Scalable Wireless Ad hoc Network Simulator (SWANS)”, http://jist.ece.cornell.edu/.
[JIA 10] JIANG L., WALRAND J., “A distributed CSMA algorithm for throughput and utility maximization in wireless networks”, IEEE/ACM Transactions on Networking, vol. 18, no. 3, pp. 960–972, 2010.
[KIM 05] KIM M.-S., KWON D.-H., SUH Y.-J., “Adaptive window mechanism for the IEEE 802.11 MAC in wireless ad hoc networks”, Proceedings of the 19th International Conference on Information Networking (ICOIN 2005), Jeju, South Korea, pp. 31–40, February 2005.
[KIM 08] KIM T.-S., LIM H., HOU J., “Understanding and improving the spatial reuse in multihop wireless networks”, IEEE Transactions on Mobile Computing, vol. 7, no. 10, pp. 1200–1212, 2008.
[KIM 11] KIM T., NI J., SRIKANT R., et al., “On the achievable throughput of CSMA under imperfect carrier sensing”, Proceedings of the 30th IEEE Annual International Conference on Computer Communications (INFOCOM 2011), Shanghai, China, pp. 1674–1682, April 2011.
[MED 06] MEDEPALLI K., TOBAGI F., “Towards performance modeling of IEEE 802.11 based wireless networks: a unified framework and its applications”, Proceedings of the 25th IEEE Annual International Conference on Computer Communications (INFOCOM 2006), Barcelona, Spain, pp. 1–12, April 2006.
[MER 08] MERTENS Y., WELLENS M., MAHONEN P., “Simulation-based performance evaluation of enhanced broadcast schemes for IEEE 802.11-based vehicular networks”, Proceedings of the IEEE 67th Vehicular Technology Conference (VTC Spring 2008), Singapore, pp. 3042–3046, May 2008.
[MIT 08] MITTAG J., SCHMIDT-EISENLOHR F., KILLAT M., et al., “Analysis and design of effective and low-overhead transmission power control for VANETs”, Proceedings of the 5th ACM International Workshop on Vehicular Inter-Networking (VANET 2008), San Francisco, pp. 39–48, September 2008.
[NAR 11] NARDELLI B., LEE J., LEE K., et al., “Experimental evaluation of optimal CSMA”, Proceedings of the 30th IEEE Annual International Conference on Computer Communications (INFOCOM 2011), Shanghai, pp. 1188–1196, April 2011.
[OLI 09] OLIVEIRA R., BERNARDO L., PINTO P., “The influence of broadcast traffic on IEEE 802.11 DCF networks”, Computer Communications, vol. 32, no. 2, pp. 439–452, 2009.
[PAP 08] PAPADIMITRATOS P., BUTTYAN L., HOLCZER T., et al., “Secure vehicular communication systems: design and architecture”, IEEE Communications Magazine, vol. 46, no. 11, pp. 100–109, 2008.
[PAP 09] PAPADIMITRATOS P., DE LA FORTELLE A., EVENSSEN K., et al., “Vehicular communication systems: enabling technologies, applications, and future outlook on intelligent transportation”, IEEE Communications Magazine, vol. 47, no. 11, pp. 84–95, November 2009.
[RAW 09] RAWAT D., YAN G., POPESCU D., et al., “Dynamic adaptation of joint transmission power and contention window in VANET”, Proceedings of the IEEE 70th Vehicular Technology Conference (VTC Fall 2009), Anchorage, pp. 1–5, September 2009.
[RAZ 06] RAZAFINDRALAMBO T., VALOIS F., “Performance evaluation of backoff algorithms in 802.11 ad hoc networks”, Proceedings of the 3rd ACM International Workshop on Performance Evaluation of Wireless Ad Hoc, Sensor and Ubiquitous Networks (PE-WASUN 2006), Malaga, Spain, pp. 82–89, October 2006.
[REZ 07] REZAEI S., SENGUPTA R., KRISHNAN H., “Reducing the communication required by DSRC-based vehicle safety systems”, Proceedings of the IEEE 10th International Conference on Intelligent Transportation Systems (ITSC 2007), Seattle, pp. 361–366, October 2007.
[RUF 05] RUFFINI M., REUMERMAN H.-J., “Power-rate adaptation in high-mobility distributed ad hoc wireless networks”, Proceedings of the IEEE 61st Vehicular Technology Conference (VTC Spring 2005), Stockholm, pp. 2299–2303, May 2005.
[SCH 10] SCHMIDT R., LEINMULLER T., SCHOCH E., et al., “Exploration of adaptive beaconing for efficient intervehicle safety communication”, IEEE Network, vol. 24, no. 1, pp. 14–19, 2010.
[SCH 10] SCHMIDT R., LEINMULLER T., BODDEKER B., et al., “Adapting the wireless carrier sensing for VANETs”, Proceedings of the 7th International Workshop on Intelligent Transportation (WIT 2010), Hamburg, Germany, pp. 1–6, March 2010.
[SEO 10] SEO H., YUN S., KIM H., “Solving the coupon collector’s problem for the safety beaconing in the IEEE 802.11p WAVE”, Proceedings of the IEEE 72nd Vehicular Technology Conference (VTC Fall 2010), Ottawa, pp. 1–6, September 2010.
[SHI 09] SHIRANI R., HENDESSI F., GULLIVER A., “Store-carry-forward message dissemination in vehicular ad hoc networks with local density estimation”, Proceedings of the 70th IEEE Vehicular Technology Conference (VTC Fall 2009), Anchorage, pp. 1–6, September 2009.
[SOM 11] SOMMER C., TONGUZ O., DRESSLER F., “Traffic information systems: efficient message dissemination via adaptive beaconing”, IEEE Communications Magazine, vol. 49, no. 5, pp. 173–179, 2011.
[STA 12] STANICA R., CHAPUT E., BEYLOT A.-L., “Properties of the MAC layer in safety vehicular ad hoc networks”, IEEE Communications Magazine, vol. 50, no. 11, pp. 1–6, 2012.
[THE 10] THE INSTITUTE OF ELECTRICAL AND ELECTRONICS ENGINEERS, IEEE standard for information technology – telecommunications and information exchange between systems – local and metropolitan area networks – specific requirements. Part 11: wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications – amendment 6: wireless access in vehicular environments, July 2010.
[TOR 09] TORRENT-MORENO M., MITTAG J., SANTI P., et al., “Vehicle-to-vehicle communication: fair transmit power control for safety-critical information”, IEEE Transactions on Vehicular Technology, vol. 58, no. 7, pp. 3684–3703, 2009.
[WAN 04] WANG C., LI B., LI L., “A new collision resolution mechanism to enhance the performance of IEEE 802.11 DCF”, IEEE Transactions on Vehicular Technology, vol. 53, no. 4, pp. 1235–1246, 2004.
[WAN 08] WANG Y., AHMED A., KRISHNAMACHARI B., et al., “IEEE 802.11p performance evaluation and protocol enhancement”, Proceedings of the 4th IEEE International Conference on Vehicular Electronics and Safety (ICVES 2008), Columbus, pp. 317–322, September 2008.
[WON 06] WONG S., YANG H., LU S., et al., “Robust rate adaptation for 802.11 wireless networks”, Proceedings of the 12th Annual International Conference on Mobile Computing and Networking (MOBICOM 2006), Los Angeles, pp. 146–157, September 2006.
[YAN 05] YANG X., VAIDYA N., “On physical carrier sensing in wireless ad hoc networks”, Proceedings of the 24th IEEE Annual International Conference on Computer Communications (INFOCOM 2005), Miami, pp. 2525–2535, March 2005.
[YAN 07] YANG Y., HOU J., KUNG L., “Modeling the effect of transmit power and physical carrier sense in multi-hop wireless networks”, Proceedings of the IEEE 26th Annual International Conference on Computer Communications (INFOCOM 2007), Anchorage, pp. 2331–2335, May 2007.
[YOO 11] YOON Y., KIM H., “Resolving distributed power control anomaly in IEEE 802.11p WAVE”, IEICE Transactions on Communications, vol. E94-B, no. 1, pp. 290–290, 2011.
[ZHU 04] ZHU J., GUO X., YANG L., et al., “Leveraging spatial reuse in 802.11 mesh networks with enhanced physical carrier sensing”, Proceedings of the 39th IEEE International Conference on Communications (ICC 2004), Paris, France, pp. 4004–4011, June 2004.