Chapter 2/ Overview of Anti-Forensics

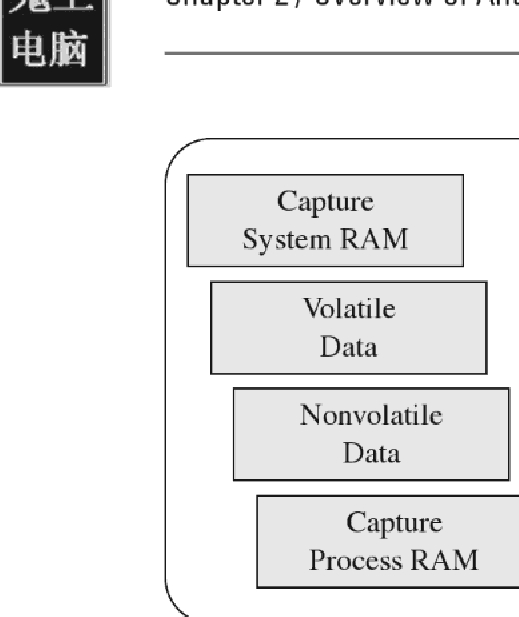
Once he has captured a memory image of the entire system, the investigator
will collect volatile data and then nonvolatile data. Volatile data is informa¬
tion that would be irrevocably lost if the machine suddenly lost power (e.g.,
the list of running processes, network connections, logon sessions, etc.),
Nonvolatile data is persistent, which is to say that we could acquire it from
a forensic duplication of the machine's hard drive. The difference is that the
format in which the information is conveyed is easier to read when requested
from a running machine.
As part of the live response process, some investigators will also scan a
suspected machine from a remote computer to see which ports are active.
Discrepancies that appear between the data collected locally and the port scan
may indicate the presence of an intruder.