NetFlow is a feature that was first introduced by Cisco Systems in the 1990s. NetFlow collects specific data about packets as they enter or exit an interface of a router or switch. This data is then sent to a NetFlow Collector via a NetFlow Exporter, which is often made part of switches or routers. The NetFlow Collector then aggregates and stores the flow data for analysis. This data is often leveraged by network and systems administrators to troubleshoot bandwidth issues, identify network congestion, and to observe the flow of data.
A sample NetFlow output is included next. What is included with flow data can vary from network device manufacturers as there are several versions in the commercial market. The following screenshot shows some of the basic information that is captured as part of a NetFlow dataset:
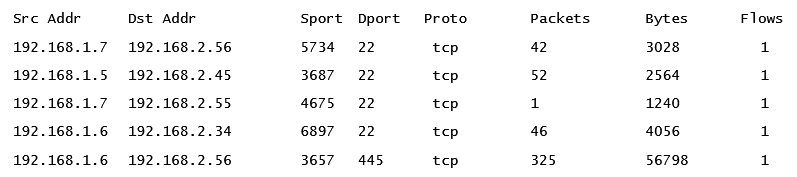
The following components of a NetFlow record are found in the preceding screenshot:
- Src Addr: This is the source address that has initiated the connection or is sending traffic.
- Dst Addr: The destination address for the connection.
- Sport: This is the source port for the source address.
- Dpost: This is the destination port. In terms of analyzing NetFlow as part of an incident investigation, this is one of the key data points to focus in on as this often tells responders the service the source address is connecting to.
- Proto: This is the protocol in use.
- Packets: The number of packets that are made as part of the flow.
- Bytes: The total number of bytes.
- Flows: Indicates how many flows have been recorded.
When examining the NetFlow data of the preceding example, there are two significant data points that may be important. The first is the number of SSH connections between devices. Secure Shell is a common way for systems to communicate with each other, but if this is outside the bounds of normal network behavior, it warrants a follow-up. In addition, connections via SMB (port 445) are commonly abused by adversaries to access other systems, deliver ransomware, or to access file shares. Even in this short example, it becomes very clear that responders gain a great deal of insight by just having visibility of the connections that occur on the internal network.
There are a wide variety of commercial tools that are in use to view NetFlow. The use of NetFlow data is also largely dependent on the organization. Configuring NetFlow is not something that can readily be accomplished during an incident without access to significant resources from both commercial providers and internal operations personnel. Regardless, responders that do have access to NetFlow would be well served to acquaint themselves with the technology, as it does provide a significant insight as to how data moves through the network.