For earlier versions of Windows, such as Windows XP and earlier, the connscan plugin performs the same function as the netscan plugin. The connscan plugin finds the _TCPT_OBJECT and is able to find both existing and exited connections. This provides responders with data concerning connections in relation to processes that were running. To determine the network connections, run the following command against the Cridex image:
dfir@Desktop-SFARF6G~$ volatility -f cridex_laptop.mem -profile=WinXPSP2x86 connscan
The command produces the following output:

The output indicates that the PID of 1484, which is Explorer.exe, the parent process of Reader_sl.exe was communicating with two external IP addresses. A review of the threat intelligence resource VirusTotal indicated that the IP address 41.168.5.140 was associated with several URLs that were communicating with malicious executables. The following image shows the various malicious files, their detections, and the filenames associated with the IP address 41.168.5.140:
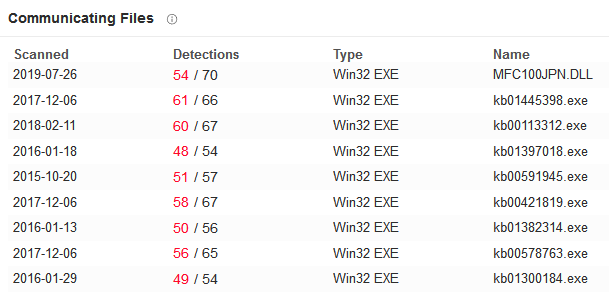
Taking the data that was derived from the process analysis in conjunction with the IP address taken from the network connections, there is enough reason to believe one, or both, of the Explorer.exe and Reader_sl.exe processes are associated with malicious code. In the next section, Reader_sl.exe will be extracted along with its associated DLL files for analysis.