Ahlia University, Bahrain
A Review
This chapter is an introductory chapter that attempts to highlight the concept of computational intelligence and its application in the field of computing security; it starts with a brief description of the underlying principles of artificial intelligence and discusses the role of computational intelligence in overcoming conventional artificial intelligence limitations. The chapter then briefly introduces various tools or components of computational intelligence such as neural networks, evolutionary computing, swarm intelligence, artificial immune systems, and fuzzy systems. The application of each component in the field of computing security is highlighted.
The aim of artificial intelligence (AI) is to simulate human intelligence on machines so that they can act and think like humans. AI is regarded as a wide field of knowledge that involves reasoning, machine learning, planning, intelligent search and building perception. Reasoning aims to reach a predetermined objective of a problem using a set of facts supplied and a predefined base of information or what we call a knowledge base. The knowledge base consists of a compilation of IF-THEN rules or a conceptual graphic structure reflecting the knowledge of the professional in a specialized field. On the other hand, learning can be described as a process of encoding the situation-action pairs at memory so that the memory can remember the correct action. The learning process is carried out on machines either by training the machine with established situation-action pairs or by enabling the machine to adjust the parameters of the specified learning rule in a trial sense. Whereas preparation is about the sequence of steps to solve a problem. To be more precise, provided a knowledge base and a set of facts, preparation calls for the sequencing of the rule firing phase, so that there is at least one such target lading sequence.
Therefore, AI's main goals are to develop methods and systems for solving problems that are normally solved by human intellectual activity, such as image recognition, language and speech processing, preparation and forecasting, thereby enhancing computer information systems; and to develop models that simulate living organisms and, in general, the human brain, thereby improving our understanding. There is a large AI literature (Jain and Lazzerini, 199), (Jain, 1999) and (Mitchell, 1997) that covers various techniques of representation of information, reasoning (Shapiro, 2010) and (Rashmi & Neha, 2017)., machine learning (Shai & Shai, 2014) and (Yu-Wei, 2015), image and language understanding (Mishra, 2018) and (Rastgarpour & Shanbehzadeh, 2011), planning, smart search and realization of knowledge. A detailed discussion on these issues goes beyond this chapter's reach.
It is clearly reported by a number of researchers that AI was incompetent to meet the growing demand for search, optimization and machine learning in information systems with broad biological and commercial databases and factory automation for the steel, aerospace, energy and pharmaceutical industries claims Konar (2005). These pitfalls of traditional AI can be summarised as follows:
The shortcoming of this classical AI has opened up new opportunities for non-classical models in different intelligent based applications. Such computational analytical tools and techniques have led to a new field called computational intelligence.
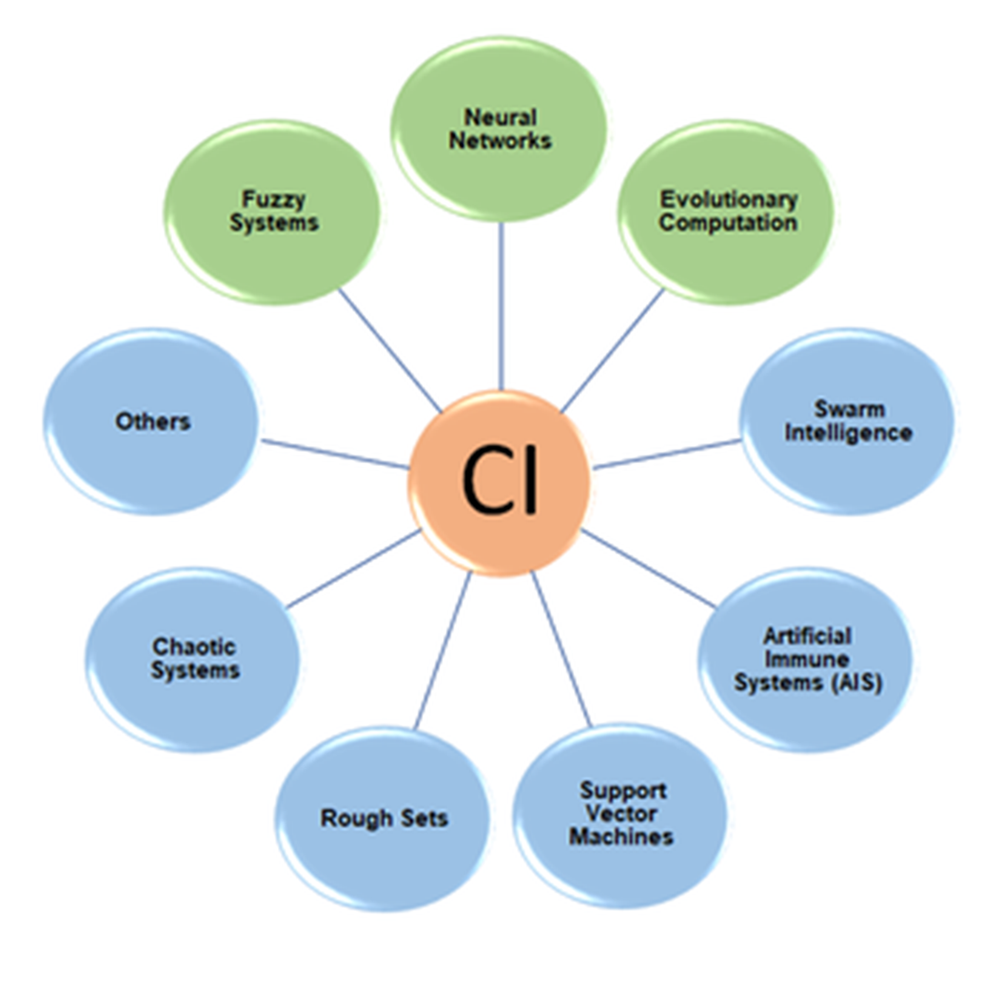
Computational Intelligence (CI) is a set of computational models and techniques that incorporate components of learning, adjustment, or potentially heuristic advancement. It is utilized to help study issues that are hard to unravel utilizing regular computational calculations and algorithms. The three main pillars of CI are neural networks, evolutionary computing, and fuzzy systems. In recent years, the scope of computational intelligence technologies has been applied to emerging areas such as swarm intelligence, artificial immune systems (AIS), supporting vector machines, rough collections or sets, chaotic structures or systems, and others. Figure 1 illustrates the main pillars for CI.
| Figure 1. Computational intelligence pillars |
|---|
 |
This chapter is and interlocutory chapter to describe CI techniques and models. It starts with a number of CI definitions to build the foundation for this emerging paradigm. Different pillars and new emerging components of CI such as neural networks, evolutionary computing, fuzzy systems, swarm intelligence and artificial immune systems (AIS) will be tackled in the remaining sections of this chapter.
COMPUTATIONAL INTELLIGENCE DEFINED
To have a better understanding of computational Intelligence and its scope as a new field of research and study, we begin looking at different definition of CI.
The term computational intelligence if first coined in 1983 as reported by Bezdek when explained his personal email communication about the IJCI journal with Nick Cercone (Bezdek, 1994) “Back in 1983 my colleague Gordon McCalla and I were the executives for the Canadian Society for Computational Studies of Intelligence (CSCSI), ….. We decided that Computational Intelligence was a more fitting term than Artificial Intelligence after much debate; it seemed to describe our field more accurately.”
James Bezdek (Bezdek, 1994) who is the father of fuzzy pattern recognition theory, defined CI system in his article “What is Computational Intelligence?”
A system is computational intelligent when it: deals with only numerical data, has pattern recognition, does not use knowledge in the AI sense; and additionally when it begin to exhibit computational adaptivity, computational fault tolerance, speed approaching human-like turnaround and error rates that approximate human performance
Eberhart and Shi (Eberhar & Shi, 2007) in their book “Computational Intelligence: Concepts to Implementations” defined computational intelligence as:
Computing Intelligence is a methodology involving computing that provides a system with an ability to learn and/or to deal with new situations, such as that the system is perceived to possess one or more attributes of reason, such as generalization, discovery, association, and abstraction.
Kahraman and his group defined computational intelligence as (Kahraman et al., 2010):
CI can be broadly defined as the ability of a machine to react to an environment in new ways, making useful decisions in light of current and previous information.
One of the most concise and comprehensive definition of computation intelligence is provided by IEEE Computational Intelligence Society as follows (IEEE CIS, 2019):
Computational Intelligence (CI) is the theory, design, application and development of biologically and linguistically motivated computational paradigms. Traditionally the three main pillars of CI have been Neural Networks, Fuzzy Systems and Evolutionary Computation.
Having presented the basic definitions of CI, next this chapter will review the theory and technology foundations of computational intelligence tools and component methodologies.
The concept of the neural network, more accurately referred to as the 'Artificial' Neural Network (ANN), was given by the inventor of one of the first neuro-computers, Robert Hecht-Nielsen (Hecht-Nielsen, 1987). The neural network is defined as:
...a computing system made up of a number of simple, highly interconnected processing elements, which process information by their dynamic state response to external inputs.
Neural Networks suggests machines that are something like brains and it can be viewed as an interconnected assembly of basic processing components, units or nodes, the design of which is loosely based on an animal neuron. The processing power of the network shall be stored in the inter-unit relation strengths or weights obtained by the method of adaptation to, or learning from, a set of training patterns. Just as the brain uses a network of interconnected cells called neurons to create a massive parallel processor, ANN uses a network of artificial neurons or nodes to solve learning difficulties.
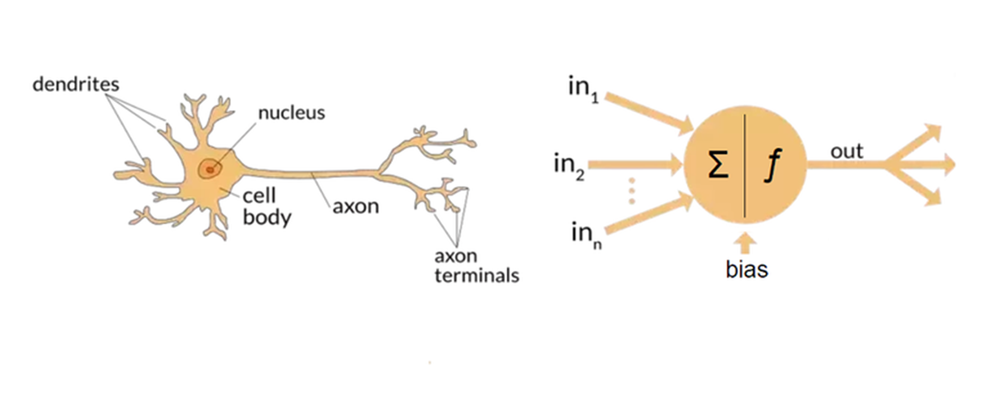
The human brain is made up of about 100 billion nerve or neurons which are connected with approximately 1015 interneuron connections mediated by electrochemical junctions called synapses, allowing a complicated network with a capability of representing a large amount of knowledge. Every neuron usually receives several thousands of contacts from other neurons and is therefore continuously receiving a multitude of incoming signals that eventually reach the cell body. Figure 2 illustrates biological neuron (left) and an ANN mathematical model (right).
| Figure 2: Biological neuron (left) and a common ANN mathematical model (right) |
|---|
 |
Neural networks are mainly applied to perform statistical analysis and data modelling (Hsieh & Tang, 1998), where their function is viewed as an alternative to traditional nonlinear regression or cluster analysis techniques. As a consequence, they are usually used in problems that may arise in terms of classification or forecasting. Examples here might include image and speech recognition, textual character recognition, and areas of human experience such as medical diagnostics, oil geological surveys, and financial market forecasting indicators.
Neural Networks Security Applications: Securing digital assets and intellectual property is becoming a concern for organizations. Recent studies have identified internal hacking as the primary cause of data loss in the corporate sector. Organizations are working hard to take appropriate measures to protect their data from destruction or leakage. Many researches work in the field of intrusion detection systems utilizes neural network power to design, implement and enhance security monitoring system. The following paragraphs describe some of the research work in this field.
Parveen’s article (Parveen, 2017) “Neural Networks in Cyber Security” is a good example for utilizing neural network in designing an intrusion detection system to protect a network from external cyber threats. This research work starts by describing the challenges faced by IT leaders with respect to Internet Security now a days. These threats are related to how to protect organizations, customers, citizens and data, while upsetting attacks from cyber criminals. As a result of these threats, the author proposes an Intrusion Detection System (IDS) to protect the network from cyber criminals and cyber threats by employing neural networks to detect and classify network activity based on minimal, incomplete and non-linear network security data sources. The article concludes that by combining advanced techniques such as Artificial Intelligence and Neural Networks can play a significant role in achieving one of highest detection rates in the industry of cyber security.
Igor and his team in their article (Igor et al., 2013) “Application of Neural Networks in Computer Security”, focused on ensuring data communication system control that neural network technologies in connection with traditional methods used in expert systems. They proposed a solution which specifies an innovative method to identifying data elements in transmission networks, addresses the transformation of their parameters for neural network input and determines the type and design of an effective neural network. Igor and his team began by analysing the security of communication of control systems and then analysed the possible use of neural networks by validating the data transfer and selected an appropriate type of neural network. As a result, they developed a practical security system design and implemented the communication network security model system using appropriate tools. Finally, this research work suggests using a much broader neural network for future development that would be able to separate incoming packets into more groups. The research can also be used to expand the model with other neural networks to look for other anomalies in the data stream.
Evolutionary Computing (EC) is a computer science research area. It is, as the name suggests, a special computing flavour that draws inspiration from the natural evolution process (Eiben and Smith, 2015). It is claimed by Fogel that the notion of applying Darwinian concepts to automatic problem-solving dates to the 1940s, long before the software revolution (Fogel,1998). Eiben and Smith claimed that Turing proposed “genetic or evolutionary search” as early as 1948, and Bremermann carried out computer experiments on “optimization through evolution and recombination” as early as 1962. Three different basic concept implementations were developed in different places during the 1960s (Eiben and Smith, 2015). Fogel, Owens, and Walsh (Fogel et al., 1966) implemented evolutionary programming in the United States, while Holland named his method a genetic algorithm (Holland, 1973) and in Germany, production techniques were discovered by Schwefel (Schwefel, 1995).
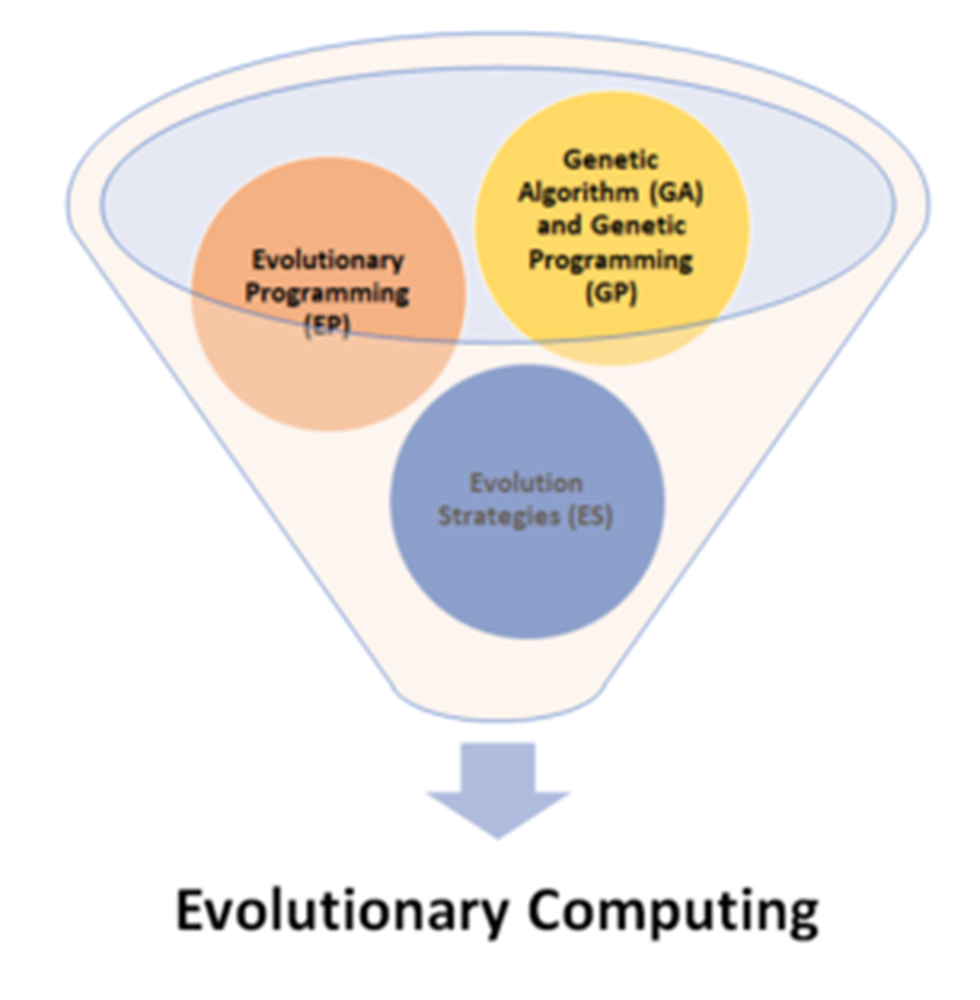
Eiben and Schoenauer (Eiben& Schoenauer, 2002) in their article “Evolutionary computing” showed that Evolutionary Computing consists of constructing, implementing and learning algorithms based on Darwin's natural selection principles. Oduguwa and his research team claimed that: Genetic algorithms (GA), evolutionary programming (EP), evolutionary strategies (ES) and genetic programming (GP) are the core Evolutionary Computing methodologies (Oduguwa et al., 2004). Figure 3 illustrates this concept.
| Figure 3. Components of evolutionary computing |
|---|
 |
Evolutionary Computing and Security Applications: Evolutionary computation (genetic algorithms and genetic programming), are becoming increasingly present in the area of computer security, both in the area of network host security and in the very challenging area of cryptology. The computer security community is increasingly interested in evolutionary computing techniques as a result of successes implementations, but there are still a range of open issues to be addressed in the field. One of these open issues is describe by Cesar (Cesar, 2004) in the field of cryptanalysis is how to define fitness functions for the various heuristic methods (say genetic algorithms, simulated annealing, etc.) which avoid the problem of the landscape of deceptive fitness. The following paragraphs describe some of the research work in employing evolutionary computing in solving security issues.
Amro and his research group (Amro et al., 2012) in their work “Evolutionary Computation in Computer Security and Forensics: An Overview claimed that evolutionary computation is an appropriate technique to find an optimal solution to a problem and evolutionary computing can provide an effective way to solve those related to computer security and forensics among these problems. Their work looked at the methods provided by evolutionary computation to find an optimal solution to a problem and it explored evolutionary computing can be applied in various computer security and forensics scenarios. In summary Amro et al., research work shows how Evolutionary computation (EC) is inspired by the natural evolution process and expresses its rules in algorithms that can be used to search for the most suitable solutions to solve a problem. Evolutionary computation thus mimics natural evolution, but on a computer, through a series or sequence of optimization algorithms that typically rely on a set of rules and the optimization process improves the quality of solutions iteratively until a better one is reached. As result, evolutionary computation does not derive its ideas from human intelligence, but rather from the transition of species from one generation to the next.
Lugo, in his work “Coevolutionary Genetic Algorithms for Proactive Computer Network Defences” (Lugo, 2017) investigates the use of coevolutionary genetic algorithms as tools to build proactive defences in the computer network and implemented rIPCA, a new coevolutionary algorithm based on speed and performance. This research work refers to the threat of disruption posed by adaptive attackers in computer networks and the aim was to strengthen network defences by modelling the actions of adaptive attackers and anticipating threats so it can protect against them proactively. o counter this, we are launching RIVALS, a new cybersecurity project designed by using coevolutionary algorithms to better defend against adaptive agents. As a contribution, this research work described the current suite of coevolutionary algorithms built by RIVALS and how they explore archiving to sustain progressive discovery. The proposed model in this work enables us to investigate a network's connectivity under an adversarial risk model. The work then conducted a generic coevolutionary test (Compare-on - one) and RIVALS simulations on 3 different network topologies to evaluate the efficacy of the package and the experiments showed that current algorithms either compromise the speed of execution or give up maintaining consistent results.
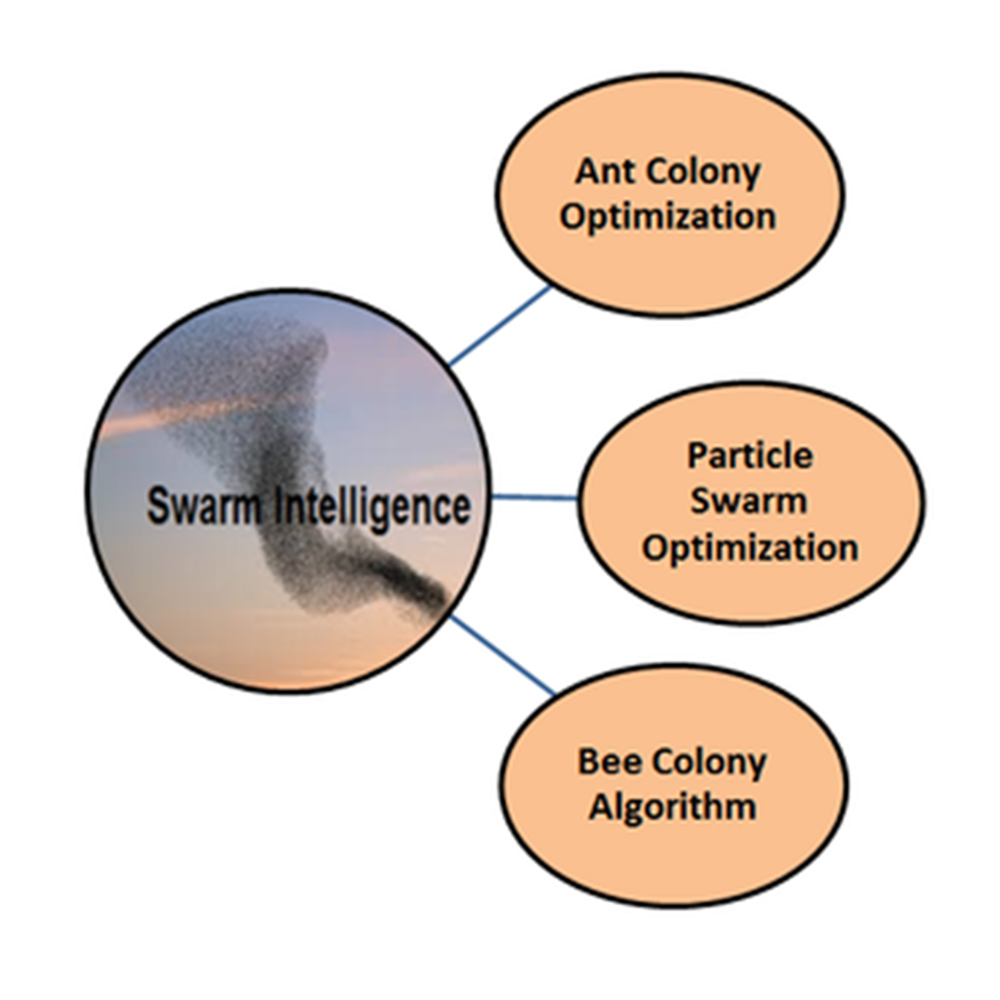
A swarm can be viewed as a relatively large group of homogeneous, simple agents that communicate locally with each other and their environment, without central control to allow an interesting global behaviour. Biologists and natural scientists researched social insect behaviours because of the incredible efficiency of these natural swarm systems. Ahmad and Glasgow reported that in the late 1980s, computer scientists proposed to the field of artificial intelligence the scientific insights of these natural swarm systems (Ahmed and Glasgow, 2012). Beni and Wang first introduced the term “Swarm Intelligence” as a set of algorithms for controlling robotic swarm in the global optimization framework (Beni and Wang, 1989). Dorigo introduced Ant Colony Optimization in 1992 as a novel meta-heuristic inspired by nature to solve difficult combinatorial optimization problems (Dorigo, 1992). In 1995, Kennedy and Eberhar introduced Particle Swarm Optimization and it was first intended to simulate the social behaviour of the bird flocking (Kennedy and Eberhart, 1995). It is reported by Beni and Wang that by the late 1990s, both Ant Colony Optimization and Particle Swarm Optimization are considered to be the most successful swarm intelligence algorithms started to go beyond pure scientific interest and enter the domain of applications in the real world. In 2005, Karabago proposed the Artificial Bee Colony Algorithm as a new member of the swarm intelligence algorithms family (Karabago, 2005). Figure 4 illustrates Swarm Intelligence Algorithms.
| Figure 4. Swarm intelligence algorithms |
|---|
 |
Swarm Intelligence and Security Application: Swarm-based algorithms have recently emerged as a family of population-based, nature-inspired algorithms capable of producing low-cost, rapid and robust solutions to several complex problems such as Intrusion Detections (ID). When an intrusion occurs, the security of a computer system or network is compromised. An intrusion can be characterized as any set of actions that attempt to compromise a resource's credibility, privacy or availability. Techniques such as firewalls, access control and authentication for intrusion prevention have failed to fully secure networks and systems against rising attacks and malware. Therefore, Intrusion Detection System has become a key component of the security infrastructure to detect and monitor these threats. As these Intrusion Detection Systems must have a high Detection Rate of Attack, at the same time having a low False Alarm Rate, building such a system is a challenging task. A promising solution for such a problem was swarm intelligence techniques and it is utilized by many researchers for improving the performance of Intrusion Detection Model. The following paragraphs describe some of the research work in employing swarm intelligence algorithms in solving security issues.
Amudha and Abdulrauf in their article (Amudha and Abdulrauf, 2012) “A Study on Swarm Intelligence Techniques in Intrusion Detection” provided an overview of the research progress in swarm intelligence techniques to assist tackling the problem of intrusion detection. The review mainly aimed to use the capabilities of swarm intelligence techniques for improving the performance of intrusion detection model. This work started by reviewing the theory behind Intrusion Detection with an emphasis on the needs for a technique such as Swarm Intelligence Algorithms Model as an aid in solving network intrusion issues. This research work identified two most common performance evaluation metrics in designing Intrusion Detection Systems to be Detection Rate (DR), which is defined as the ratio of the number of correctly detected attacks to the total number of attacks, and False Alarm Rate (FAR), or False Positive Rate (FPR), which is the ratio of the number of normal connections misclassified as attacks to the total number of normal connections. Different swarm intelligence techniques used by researchers in evaluating intrusion detection template quality were examined in this research work and as a conclusion from the empirical study carried out, this work found that its application to the field of intrusion detection, which is still to be explored, is constrained.
Jeswani and Kale in their article (Jeswani & Kale, 2015) “The Particle Swarm Optimization Based Linear Cryptanalysis of Advanced Encryption Standard Algorithm” applied the swarm Optimization technique in enhancing network security. Cryptography algorithms are the main component and the key factor in data storage and uninterrupted network transmission protection mechanisms and the data security depends purely on the cryptography algorithm and therefore the cryptography keys must be handled in an appropriate manner. Therefore, mechanisms of security are established when a security threat is identified. This research work describes the implementation of computational intelligence-based approach for the known cryptanalysis of the Advanced Encryption Standard (AES) algorithm is to define the security risk associated with the AES algorithm. The Authors of this research work utilized the Particle Swarm Optimization (PSO) based cryptanalysis which is used much now a days because of its fast convergence rate, they implemented a PSO-oriented cryptanalysis technique to crack the key used in advance by the standard encryption algorithm. Jeswani and Kale claimed that this technique is known as a text-only cipher attack for an AES encryption system, where the key is deduced in a minimum search space as opposed to the Brute Force Attack. In general, this research work it applied a new method for Advanced Encryption Standards (AES) Algorithm Linear Cryptanalysis using Particle Swarm Optimization. The fitness function used in this approach ensures that the solution is efficient, and this technique successfully identifies the Cryptographic key bits using cipher text attack only to ensure minimal search space allowing less overhead and time-efficient solution. As a conclusion this research work demonstrated how PSO is applied to the AES allowing the key length 128 bits where 76 bits are identified, and the percentage of result obtained is 59.37 and the elapsed time is 17.3 sec. Thus, the use of Particle Swarm Optimization has led to the good reduction factor in Linear Cryptanalysis.
An Artificial Immune System (AIS) is a system that uses some of the biological immune system technology to construct algorithms or technologies that tackle systemic objectives, and this may include the computational and computer simulation of immune systems, or the integration into algorithms of certain concepts related to immunology. Reviewing literature suggested four main AIS algorithms were based on the development of various AIS applications. Daudi classifies these four AIS algorithms as: Negative Selection Based Algorithms, Clonal Selection Based Algorithms, Artificial Immune Networks (AINs) and Danger Theory and Dendritic Cell Algorithms (Daudi, 2015). Figure 5 describes the major AIS algorithms. The following paragraphs will briefly highlight on each AIS algorithm.
Negative Selection Based Algorithm: Inspired by the selection processes that occur in the thymus during cell maturation. Delona’s research team reported that negative selection refers to the recognition and elimination (apoptosis) of self-reacting cells, which are T cells that can pick and invade tissues of their own (Delona et al., 2017). This algorithm is used for problem domains of classification and pattern recognition. For example, the algorithm prepares a collection of exemplary pattern detectors trained on ordinary (non-anomalous) patterns that model and detect unseen or anomalous patterns in the case of an anomaly detection domain. Delona also reported that the NSA was motivated by the negative process of selection in the natural immune system. In thymus, if a T-cell detects any self-cell, it is removed, and immune functionality is then performed in a process of T-cell maturation.
Clonal Selection Based Algorithms: The theory of clonal selection in an immune system is used to explain the adaptive immune system's basic response to an antigenic stimulus. Burnet described the theory of Clonal Selection Based Algorithm as an idea that relies on the concept of proliferating only cells capable of recognizing an antigen (Burnet, 1959).
| Figure 5. Artificial immune systems (AIS) |
|---|
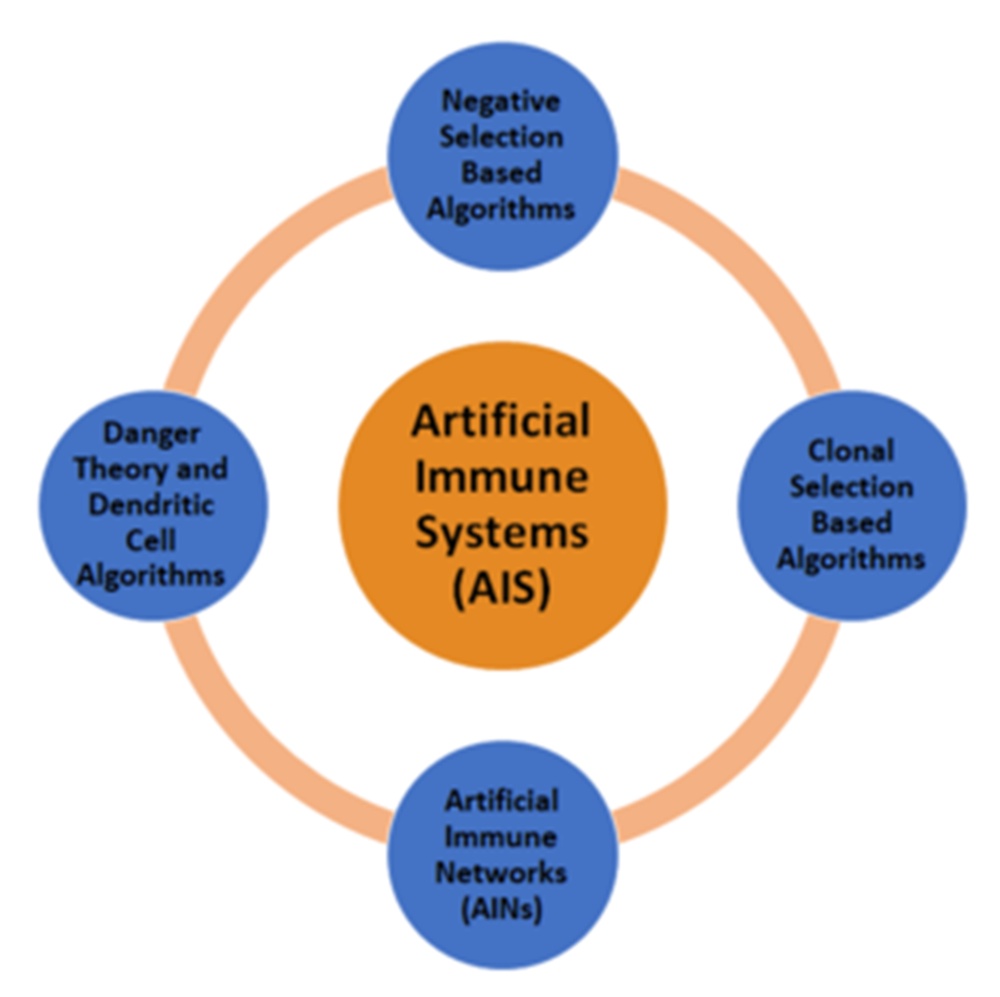 |
Artificial Immune Networks: A successful implementation models of Artificial Immune Systems are Artificial Immune Networks. Framer’s research team proposed their immune network model (Farmer et al., 1986) which became the fundamental for various Artificial Immune Systems algorithm and hence based on this the first immune network algorithm was proposed by Ishida (Ishida, 1990). Subsequently, The Artificial Immune Network algorithm sets the foundation and the extension for optimization problems known as the Optimization Artificial Immune Network algorithm. The algorithm of the Artificial Immune Network is inspired by the theory of the immune system acquired. The principle of clonal immunity selection accounts for the immune system's adaptive actions, including the ongoing selection and proliferation of cells choosing potentially harmful (and usually foreign) material in the body. A clonal selection theory's problem is that it presumes that the reactive cell repertoire stays idle when there is no pathogen to respond to. Jerne suggested an Immune Network Theory (Idiotypic Networks) in which immune cells do not rest in the absence of pathogen but identify and respond to each other's antibodies and immune cells.
Artificial Immune Systems Security Applications: Organizations should defend their networks from interference and attacks on computer from unintended or unauthorized access, change, or destruction and these securities should detect anomalous patterns by taking advantage of recognized signatures when tracking normal computer programs and abnormality network use. Computer security is facing huge challenges with network development. Until causing widespread harm, such as virus attacks and Intrusion Detection have become an indispensable element for detecting unusual behaviours to solve this problem. Computer science has a great tradition of learning nature’s good ideas. The brain has inspired the model of the neural network, the basis of many attempts to develop artificial intelligence. The application of theoretical immunology and immune functions to solve security issues slowly became a research field based on applying Artificial Immune Systems (AIS) techniques to aids in solving these security issues. Researchers made significant contributions to AIS production. Many AISs have been developed for a wide range of applications, such as fraud detection, optimization, machine learning, robotics, and computer security. The following paragraphs describe some of the research work in employing Artificial Immune Systems algorithms in solving security issues.
Harmer’s research team in their article (Harmer et al., 2002) “An Artificial Immune System Architecture for Computer Security Applications” describe how the task of detecting and classifying new viral stains and intrusion patterns could overwhelm existing antivirus and network intrusion detection (ID) solutions. Within a hierarchical layered architecture, a self-adaptive decentralized agent-based immune system based on biological strategies is proposed by Harmer’s team. An interactive software system is designed, implemented and tested in Java. The findings validate the use of a biological-system distributed-agent approach to computer-safe virus elimination and ID problems. The experimental implementation of this research work is based on the prototypes and it provides an effective solution for detecting, recognizing and removing malicious code and bad packets. The efficacy level of this implementation can be adjusted by selecting the number of antibodies, the length of the antibody, and the threshold for detection. These must be selected on the basis of known self-content and with an understanding of their ramifications on negative selection time, scanning time, and coverage of non-self-space.
Yang’s research group in their research work (Yang et al., 2014) “A Survey of Artificial Immune System Based Intrusion Detection” reported that there is a lot of literature about Intrusion Detection Systems, their study only surveys the approaches based on Artificial Immune System (AIS) and the use of AIS in ID is an attractive term in today's techniques. Yang’s research work discussese AIS-based ID approaches from a new perspective; a model for AIS-based ID Systems (IDSs) development is also proposed and based on three core aspects, this model is evaluated and discussed: antibody / antigen encoding, generation algorithm and mode of evolution. This research work collates into the proposed system the widely used algorithms, their implementation features, and the design of IDSs. Finally, it also highlights some of the future challenges in this field.
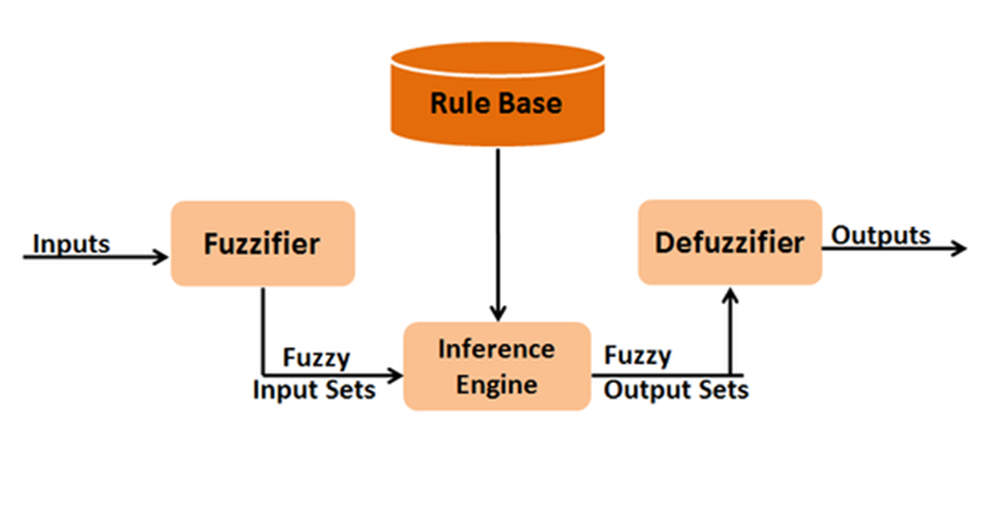
Zadeh introduced fuzzy sets as a way of representing and manipulating information that was not reliable but rather confusing (Zadeh, 1965). The main inspiration behind the introduction of the theory of fuzzy sets was the need to model phenomena of the real world, which are inherently vague and ambiguous. Utilizing the imprecise terms of natural language, human knowledge about complex issues can be successfully represented through implementing fuzzy sets theories and fuzzy logic which can offer formal methods for numerical representation and efficient data processing. Fuzzy Logic FL is a reasoning system which is like human reasoning. FL's approach imitates the way human decision-making includes all intermediate possibilities between YES and NO virtual values. The standard logic blocks a machine can understand takes correct input and generates a definite output such as TRUE or FALSE that is like the YES or NO of humans. Mendel defined a fuzzy logic system (FLS) as the non-linear mapping of a set of input data to a scalar output (Mendel, 1995). A FLS consists of four main parts: fuzzifier, rule base, engine of inference, and defuzzier. Figure 6 shows these elements and the overall structure of an FLS.
| Figure 6. Components of fuzzy logic system |
|---|
 |
Fuzzy logic has always been one of the key areas of research in the field of informatics, as it helps to cope with vagueness and ambiguity in the real world. A variant of fuzzy logic systems has gained enormous popularity for research purposes in recent years, Type-2 Fuzzy Logic. An overview of the study trends of Type-2 Fuzzy logic is given in this paper.
Fuzzy Systems Security Applications: The value of protecting computer systems and networks from attack cannot be underestimated due to the growing reliance of corporations and government agencies on their systems and networks. A single malicious invasion of a computer network can cause an organization a lot of damage. Therefore, computer security tackles the protection of information and property from misuse by unauthorized people. Digital forensics offers strategies for storing, gathering, validating, recognizing, evaluating, describing, recording and presenting digital evidence from digital sources to recreate criminal activity or breach policy. Fuzzy logic can be used properly to help address issues related to computer security and computer forensics. The following paragraphs describe some of the research work in employing fuzzy logic systems in solving security issues.
Javed and Pandey in their article “Advance Cyber Security System using fuzzy logic” (Javed & Pandey, 2014)reported that increasingly, critical infrastructure sites and software facilities rely on integrated physical and cyber-based real-time control systems and the existence of these omnipresent and sometimes unrestrained communications interconnections results in a growing cyber security risk. Cyber security is not a single issue, but a group of very different issues involving different sets of threats. On the other hand, an advanced cyber security system using fuzzy logic is a system consisting of a depository of rules and a mechanism to access and execute the rules. Javed and Pandey tried to use fuzzy logic in their work to develop an integrated cyber security platform and their study suggested a cyber security program using fuzzy logic that alerts system administrators about cyber threats anticipated. The also assumed that the system works well if the cyber threat scenario is applied. The model developed was not intended to protect a system but to warn the system administrator of expected threats. When tested the developed system showed its superiority in the areas of development flexibility and fast response for cyber threats.
Al-Ali and AlMogren in their research work (Al-Ali & AlMogren, 2017) “Fuzzy logic methodology for cyber security risk mitigation approach” described the impacts of criminal activity based on the nature of the crime, the victim, and the context of cybercrime impacts (whether short-term or long-term. They showed how the Kingdom of Saudi Arabia faces various cyber threats, including malware, spam and phishing email attacks. While recent findings highlight the poor state of the information security system in Saudi Arabia, it is within the current premise that a special cyber security risk assessment should be established claimed Al-Ali and AlMogren and using the concept of Fuzzy Logic (FL), they proposed a Fuzzy Inference System (FIS) to generate risk mitigation and attempt to solve these problems for proposed entities. The researchers in this work reported that technological advancement and its association with digital wellness can be described as a two-edged metaphoric sword, one providing new insight into the vulnerabilities of the global cyber network, and another seeking a way to rectify the possibilities of successive cyber-attacks and there are numerous attempts, both at local and global level, to counter cybercrime and reduce the risk of cyber-attacks in both the private and public spheres. As a result of this conceptualization of the hiring of additional cyber security experts is unavoidable as the main strategy for eliminating cyber vulnerabilities from the top three security threats. Applying Fuzzy logic, however, may give organizations a vision abroad to quantify risk and evaluate risk factors, and may end up assessing the most important security steps.
Achieving the full potential of Computational Intelligence technologies and models poses research challenges that involve a radical transformation of the CI research market, driven by significant and sustained investment in different applications especially in the field of computing security and cyber security. These are the key findings of a recent study conducted by researchers in the field.
When we understand that intelligence is not limited to a single brain, we may expect a more promising future; it also exists in communities such as insect colonies, organisations and human societies markets, to name a few. In all these instances, large numbers of agents able to perform specific tasks that can be viewed as computations participate in collective behaviour that effectively solves a number of problems that exceed a single individual's ability to solve. And they do so often without global controls, while sharing incomplete and sometimes delayed data.
Many of the features that underlie distributed intelligence can be found in our planet's computer networks. Processes are produced or “made” within these systems, migrate across networks and spawn other processes on remote computers. And as they do, we solve complex problems - think about what it takes to make a movie on your computer - when vying for assets like bandwidth and CPU that are threatened by other system.
Ironically, we understand distributed intelligence quality, both natural and artificial, much better than individual minds ' functions. This is partly due to the ease with which the interactions between individuals and programs can be observed and measured when navigating complex information spaces. Compare this with the complexity of studying comprehensive cognitive processes in the human brain. And we know from this wide range of knowledge that while the overall performance of a distributed system is determined by the ability of many agents to exchange partial results that are not always optimal, success is determined by the few who make the most progress per unit time.
This chapter analysed several computational intelligence algorithms based on computing security and cyber security problems applications. Considering the rapidly changing and increasingly complex nature of global security, we continue to see a remarkable interest in novel, flexible and resilient strategies in computing security, cyber security and network security environments that can cope with the challenging issues that arise in this area. Such problems arise not only because of the vast amount of data collected by a multitude of sensing and tracking modalities, but also because of the advent of creative groups of decentralized, mass-scale communication protocols and networking structures, and the advancement in Computational Intelligence techniques such as Neural Networks, Evolutionary Computing, Swarm Intelligence, Artificial Immune Systems and Fuzzy Systems.
Inspired by imitative aspects of living systems, CI systems common feature is that data is processed by symbolic knowledge representation. CI systems are capable of reconstructing behaviours found in learning sequences, creating inference rules, and generalizing information in circumstances where assumptions are expected to be made or predicted categorized based on categories previously observed. The CI literature contains research articles and research works that show promising potential practical applications in the field of computing security.
Ahmed, H., & Glasgow, J. (2012). Swarm Intelligence: Concepts, Models and Applications. Technical Report 585. School of Computing. Queen's University Kingston, Ontario, Canada.
Al-Ali, M., & AlMogren, A., (2017). Fuzzy logic methodology for cyber security risk mitigation approach. Journal of Networking Technology, 8(3).
Amro, S., Elizondo, D., Solanas, A., & Martinez-Balleste, A. (2012). Evolutionary Computation in Computer Security and Forensics: An Overview. In Computational Intelligence for Privacy and Security, SCI 394, (pp. 25–34). Springer-Verlag Berlin Heidelberg.
Amudha, P., & Abdulrauf, H. (2012). A Study on Swarm Intelligence Techniques in Intrusion Detection. IJCA .
Beni, G., & Wang, J. (1989). Swarm intelligence in cellular robotic systems. NATO.
Bezdek, J. (1994). What is Computational Intelligence? Computational Intelligence Imitating Life. IEEE Press.
Burnet, F. M. (1959). The clonal selection theory of acquired immunity . Cambridge University Press.
Cesar, J. (2004). Evolutionary Computation in Computer Security and Cryptography. New Generation Computing , 23, 193–199.
Daudi, J. (2015). An Overview of Application of Artificial Immune System in Swarm Robotic Systems. Automation . Control and Intelligent Systems , 3(2), 11–18. doi:10.11648/j.acis.20150302.11
Delona, C., J., Haripriya, P., V., & Anju, J., S. (2017). Negative Selection Algorithm: A Survey. International Journal of Science, Engineering and Technology Research, 6(4).
Dorigo, M. (1992). Optimization, learning and natural algorithms (Ph.D. Thesis). Dipartimento diElettronica, Politecnico di Milano, Italy.
Eberhart, R., & Shi, Y. (2007). Computational Intelligence: Concepts to Implementations . Elsevier. doi:10.1016/B978-155860759-0/50002-0
Eiben, A. E., & Schoenauer, M. (2002). Evolutionary computing. Information Processing Letters , 82(1), 1–6. doi:10.1016/S0020-0190(02)00204-1
Eiben, A. E., & Smith, J. E. (2015). Introduction to Evolutionary Computing (2nd ed.). Springer-Verlag Berlin Heidelberg. doi:10.1007/978-3-662-44874-8
Farmer, J. D., Packard, N. H., & Perelson, A. S. (1986). The immune system, adaptation, and machine learning . Physica , 22, 187–204.
Fogel, B. (Ed.). (1998). Evolutionary Computation: The Fossil Record . Piscataway, NJ: IEEE Press. doi:10.1109/9780470544600
Fogel, L., Owens, A., & Walsh, M. (1966). Artificial Intelligence through Simulated Evolution . Chichester, UK: Wiley.
Harmer, P., Williams, P., Gunsch, G., & Lamont, G. (2002). An Artificial Immune System Architecture for Computer Security Applications. Transactions on Evolutionary Computation, 6(6).
Hecht-Nielsen, R. (1987). Kolmogorov’s Mapping Neural Network Existence Theorem . Hecht-Nielsen Neurocomputer Corporation.
Holland, J. (1973). Genetic algorithms and the optimal allocation of trials. SIAM Journal on Computing , 2, 88–105.
Hsieh, W., & Tang, B. (1998). Applying Neural Network Models to Prediction and Data Analysis in Meteorology and Oceanography. Bulletin of the American Meteorological Society , 79(9), 1855–1870.
IEEE CIS. (2019). What is Computational Intelligence? Retrieved from: https://cis.ieee.org/about/what-is-ci
IgorH.BohuslavaJ.MartinJ.MartinN. (2013). Application of Neural Networks in Computer Security. In 24th DAAAM International Symposium on Intelligent Manufacturing and Automation. Elsevier Ltd.
IshidaY. (1990). Fully distributed diagnosis by PDP learning algorithm: towards immune network PDP model. IEEE International Joint Conference on Neural Networks. 10.1109/IJCNN.1990.137663
Jain, C. (Ed.). (1999). Intelligent Biometric Techniques in Fingerprint and Face Recognition . Boca Raton, FL: CRC Press.
Jain, C., & Lazzerini, B. (Eds.). (1999). Knowledge-Based Intelligent Techniques in Character Recognition . Boca Raton, FL: CRC Press.
Javed, A., & Pandey, M. K., (2014). Advance Cyber Security System using fuzzy logic. Journal of Management and IT, 10(1).
Jeswani, D., & Kale, S. (2015). The Particle Swarm Optimization Based Linear Cryptanalysis of Advanced Encryption Standard Algorithm. International Journal on Recent and Innovation Trends in Computing and Communication , 3(4).
Kahraman, C., Ihsan Kaya, I., & Didem, C. (2010). Computational Intelligence: Past, Today, and Future . In Ruan , D.(Ed.), Computational Intelligence in Complex Decision Systems . doi:10.2991/978-94-91216-29-9_1
Karaboga, D. (2005). An Idea Based On Honey Bee Swarm for Numerical Optimization . Academic Press.
KennedyJ.EberhartR. (1995). Particle Swarm Optimization. Proceedings of IEEE International Conference on Neural Networks, 1942–1948.
Konar, A. (2005). Computational Intelligence-Principles, techniques and Applications . Springer-Verlag Berlin.
Lugo, A. (2017). Coevolutionary Genetic Algorithms for Proactive Computer Network Defences (Master’s thesis). MIT.
Mendel, J. (1995). Fuzzy logic systems for engineering: A tutorial. Proceedings of the IEEE , 83(3), 345–377. doi:10.1109/5.364485
Mishra, S. (Ed.). (2018). Artificial Intelligence and Natural Language Processing . Newcastle upon Tyne, UK: Cambridge Scholars Publishing.
Mitchell, M. (1997). Machine Learning . New York: McGraw-Hill.
Oduguwa, V., Tiwari, A., & Roy, R. (2004). Evolutionary computing in manufacturing industry: An overview of recent applications. Applied Soft Computing , 5(3), 281–299. doi:10.1016/j.asoc.2004.08.003
Parveen J., R., (2017). Neural Networks in Cyber Security. International Research Journal of Computer Science, 9(4).
Rashmi, S., & Neha, S. (2017). Knowledge Representation in Artificial Intelligence using Domain Knowledge and Reasoning Mechanism. International Journal of Scientific Engineering and Research , 5(3), 17–20.
Rastgarpour, M., & Shanbehzadeh, J. (2011). Application of AI Techniques in Medical Image Segmentation and Novel Categorization of Available Methods and Tools. Proceeding of the International Multi Conference of Engineers and Computer Scientists.
Schwefel, H. (1995). Evolution and Optimum Seeking . New York: Wiley.
Shai, S., & Shai, B. (2014). Understanding Machine Learning: From Theory to Algorithms . New York: Cambridge University Press.
Shapiro, S. (2010). Knowledge Representation and Reasoning Logics for Artificial Intelligence. University at Buffalo, The State University of New York Buffalo.
Sonakshi V., Amita, J., Devendra, T., & Oscar, C. (2018). An Analytical Insight to Investigate the Research Patterns in the Realm of Type-2 Fuzzy Logic. Journal of Automation, Mobile Robotics & Intelligent Systems, 12(2).
Yang, H., Li, T., Hu, X., Wang, F., & Zou, Y. (2014). A Survey of Artificial Immune System Based Intrusion Detection. The Scientific World Journal. doi:10.1155/2014/156790
Yu-Wei, C. (2015). Machine Learning with R Cookbook . Birmingham, UK: Packt Publishing Ltd.
Zadeh, L. A. (1965). Fuzzy Sets. Information and Control , 8(3), 338–353. doi:10.1016/S0019-9958(65)90241-X