Social Media Trustworthiness in Gulf Cooperation Countries
Given the current widespread popularity of social media, such as Twitter, Instagram, Snapchat, and many other applications, understanding users’ attitudes and usage behavior of social media applications becomes a necessity in order to develop future placements of such technologies and increase the level of trust among the users. Therefore, the aim of this chapter is to shed light on the impact of trustworthiness of social media on the intention to use it. Data is gathered through a quantitative method, in which a questionnaire is used as a primary data. A convenient sampling is applied, in which the most easily accessible managers and employees in Ministry of Interior in Bahrain are chosen. The results demonstrate that there is a significant positive relationship between trustworthiness and intention to use social media. The study recommends future works to study the impact of security awareness on the usage of social media in public sector in Bahrain.
The current trend of technology in the digital age extends the reach of communication media to all domains of social life in a network that is both global and local, generic and customized, and in a dynamic pattern. It is been argued that the Middle Eastern, in general, and the Countries Gulf Cooperation Countries (GCC), in particular, have heavy investments in their ICT infrastructure in order to develop Internet access through broadband along with 3G, 4G and 5G network services (Alqudsi-ghabra et al., 2011). In fact, the GCC economies in general has been leading the Middle East and North Africa (MENA) region’s economic growth during 2018 and 2019 through large-scale infrastructure investment such as the Expo 2020 in the UAE (Selman & Faiq, 2018). They stated that the technology in the GCC has evolved from a highly fragmented market to an ecosystem of a wide variety of product and services.
The adoption of advanced technologies have been rapidly accelerated. In this regard, Chami (2019) recently declared that FinTech and blockchain have affected nearly all the industries located in the GCC and at different paces. In general, FinTech is playing a vital role in the future of financial services in both public and private sectors in the GCC and the UAE itself is embracing the potential of blockchain technology across industries through targeting to have all government documents on the blockchain by 2020 (Chami, 2019).
The telecommunication sector is a significant engine for economic growth, diversification and social cohesion in Bahrain. It is used to provide leading-edge services and respond to both consumers’ and businesses’ needs. It is crucial for improving productivity and enhancing the growth of new sectors such as energetic digital services sector. Therefore, a strong telecommunications platform as a part of a dynamic Information and Communications Technology (ICT) ecosystem will enable the government and citizens to achieve a range of enhancement in health care, education and communication with governmental bodies (TRA Annual Report, 2017).
Web 2.0 technology is found to provide an easy access to information, improve communication, ensure convenience in health, education, and other sectors, and it enhance both the efficiency and the productivity. However, internet users still hesitate to fully trust these social networks. Given the nature of social media platforms and the large number of users disseminating information, inaccurate or false information is considered as an inherent problem (Lindsay, 2011). It has been found that such mistaken and untruthful information has been spread through social media during disasters such as the Arab spring.
Previous literatures have identified social media as a significant vehicle in promoting social networking and connections in all fields. However, still there is a lack of addressing the impact of such connections in order to create trust in these fields. Therefore, this research aims to study the impact of trustworthiness of social media on the intention to use it among employees in the Ministry of Interior in Kingdom of Bahrain.
This chapter is organized as follows. First, the Web 2.0 technologies and social media evolution are highlighted. Then, a literature review on technology acceptance frameworks is outlined. In this context, a framework for users’ trust is built to study the impact of trustworthiness of social media on the intention to use it among users. Finally, the case of Ministry of Interior in the Kingdom of Bahrain is discussed to link the conceptual framework developed in the preceding sections to practice. Conclusions and recommendations follow.
BACKGROUND – WEB 2.0 TECHNOLOGY AND SOCIAL MEDIA EVOLUTION
The term “Web 2.0” was officially coined in 2004 by Dale Dougherty (Tim, 2005). Web 2.0 is seen as a consequences of a more fully implemented Web. Whereas, Web is generally a set of technologies,
Web 2.0 is the attempt to conceptualize the significance of such set of outcomes that are enabled by Web technologies (Anderson, 2007). There are a number of Web-based services and applications that demonstrate the foundations of the Web 2.0 concept, including; blogs, wikis, multimedia sharing services, content syndication, podcasting and content tagging services (Anderson, 2007). One of the Web 2.0 characteristics is social participation, in which it provides users with the tools that allow them to engage in different activities such as Facebook, Twitter, and many other blogs (Merchant, 2009). It is apparent that Web 2.0 technologies enhance the experiences of various users. In this regard, Bugawa (2016) explained how the usage of Web 2.0 technologies could result in more interactive technologies among users.
The scale of Web impact has a vital role on the way the architectures of a given Web-based system are designed, especially for new technologies that are developed on the basis of Web 2.0 ideas (Anderson, 2007). The rise of social network sites is considered as a new socio-technical revolution, ranging from personal interaction to business, to culture, to social movements, to politics and so on. In fact, it can be noticed that currently the most important usage of the internet is the social networking. Social media has become the selected platform for different activities including; personal friendships, marketing, e-commerce, education, and entertainment (Manuel, 2013).
Users are experiencing new learning opportunities via social interaction (Merchant, 2009). Although the Middle East constitutes 3.2% of the worldwide internet users only, it has registered a remarkable growth in the internet usage 5,183% in the past 20 years compared with the rest of the world 1,114% (World Internet Usage Statistics News, 2010). As a result, this has attracted various online companies to conduct business in the Middle East and allowed many existing sectors such as education, health, airline and government to move their operations online (Aloul, 2010). Yet, the last few years have witnessed an increased number of cybercrime incidents (Aloul, 2010). Usage of advanced secure technologies in many organizations is forcing hackers to break into organizations with new and unusual technologies by targeting the weakest link (i.e., uneducated computer users) (Aloul, 2010). These technological changes have provided new ways of using the web that enhance users’ behavior (Bugawa, 2016). There are various theories that explain users’ behavior with respect to any given new technology. For instance, the Theory of Reasoned Action (TRA) proposed by Fishbein and Ajzen (1975) is generated from the field of social psychology that explains users’ behavior through their intentions. This theory is then adopted by Davis (1986, 1989) who proposed the Technology Acceptance Model (TAM). Since then, TAM has been revised in various studies in order to fit a certain context of technology being examined, and the most recent one is by Rauniar, et al. (2014) who proposed a revised model of TAM to study the usage behavior of social media applications.
Greenwell (2011) reported five eras of information systems attacks. The first era, attacks were characterized as being primarily small scale and mostly harmless. The second era, attacks were characterized by their large scale and their different motivation for hacking. The third era witnessed the introduction of laws to protect information security. The forth era, hackers began targeting large corporations to obtain money and finally the fifth era hackers become motivated by politics.
Based on a survey distributed to both students and staff in the University of Bahrain, it was found that the majority of social media users had been exposed to the security threat of website failure, maintenance error, spamming, while few had dealt with unauthorized access to their account and data, faced malware and had their identities stolen (Zolait et al., 2014). In terms of user accountability, it was found that the majority of social media users believe that they should be responsible for protecting their own information and only few believed that it is the government’s responsibility (Zolait et al., 2014).
In general, Gikas & Grant (2013) stated that Web 2.0 technologies are sometimes referred to as social media. Researchers are continuously intrigued by social media affordances and reach, supporting a wide range of interests and practices (Boyd & Ellison, 2008). Social network sites (SNSs) or social media in general is defined as web-based services that allow individuals to construct a public or semi-public profile within bounded system, articulate a list of other users with whom they share a connection, and view and traverse their list of connections and those made by others within the system (Boyd & Ellison, 2008). Lately, it is been observed that social media’s popularity and the number of active participants are growing simultaneously (Bugawa, 2016).
The following section outlines conceptual frameworks for technology acceptance along with factors affecting users’ attitude and usage behavior of a given technology.
The Problem of the Study
Theoretically, studies and research need to be re-evaluated to give a proper context and understanding of the widespread popularity of social media among its users. In this regard, Rauniar, et al. (2014) examined individual adoption behavior of Facebook as one of the popular social networking sites through revising TAM model and the results demonstrated that the revised model supported all the hypotheses of social media usage behavior. Since they focused only on Facebook, they claimed that future studies can include data analysis from other social media (Rauniar, et al., 2014).
Also Ghannam (2011) stated that there is an awakening of free expression in the Arab world which has helped break down the power of state in controlling media and information. The rise of an independent vibrant social media and citizen engagement on the internet is being increased, and is expected to attract 100 million Arab. Moreover, AL-Adawi, Yousafzai & Pallister (2005), claimed that trust can also influence behavioral intentions and attitude. Thus, it is important to detect what is arguably the most dramatic and unprecedented improvement in trustworthiness and access to information in order to peruse the Arab blogs, online videos, and other digital platforms (Ghannam, 2011).
Therefore, this study aims to address this knowledge gap in literature, in order to explain the users’ behavior along with their trust of social media among employees in the Ministry of Interior in Kingdom of Bahrain through building on the revised TAM model by (Rauniar, et al., 2014).
CONCEPTUAL FRAMEWORKS FOR TECHNOLOGY ACCEPTANCE
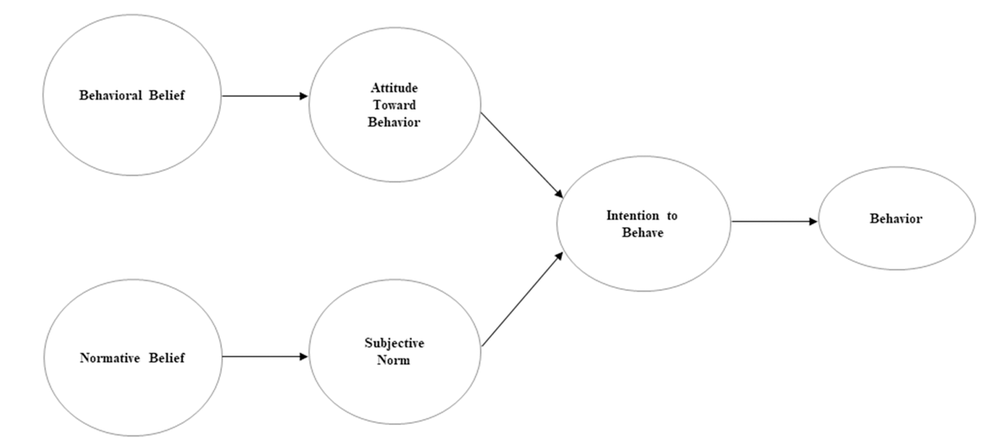
Social media’s widespread popularity is due to its acceptance and usage in the personal, social, and professional life of individual users (Rauniar, et al., 2014). Technology Acceptance Model (TAM) as proposed by Davis (1986, 1989) is one of the widely accepted theory on the actual usage behavior of a new technology, and it is derived from a popular theory called Theory of Reasoned Action (TRA) proposed earlier by Fishbein and Ajzen (1975) from the field of determinants of social psychology that explains a person’s behavior through his/ her intentions. Specifically, TRA was theorized to explain general human behavior, while TAM was theorized to explain technology usage behavior (Davis. et al., 1989). Figure 1 and 2 below illustrate the TRA and TAM models respectively.
| Figure 1. |
|---|
 |
| Figure 2. |
|---|
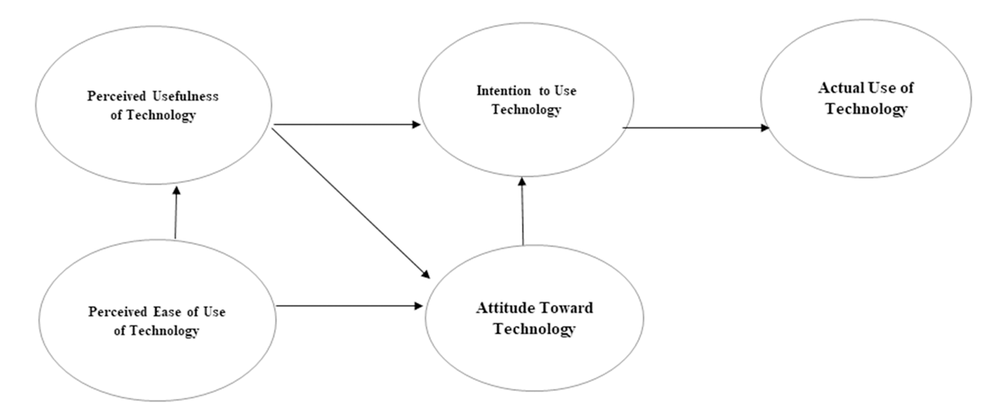 |
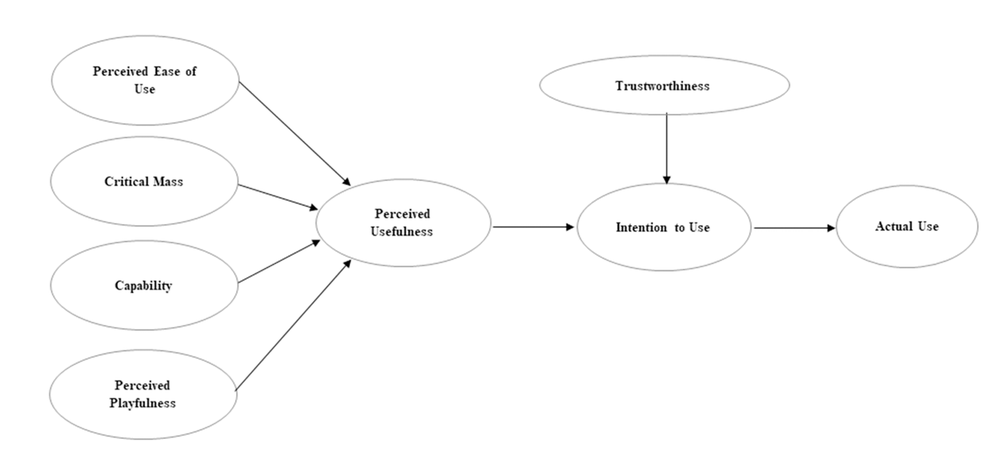
It is apparent that TAM breaks down the TRA’s attitude construct into two constructs; perceived usefulness (PU) and perceived ease of use (EU) in order to explain technology usage behavior (Rauniar, et al., 2014). TAM has been revised in various studies in order to fit a certain context of technology being examined (Rauniar, et al., 2014) and one of the well-revised model of TAM is the inclusion of trustworthiness construct in predicting the usage behavior of a new technology by its users (Venktatesh & Davis, 2000), as shown in Figure 3.
| Figure 3. |
|---|
 |
Research Framework
In this research, we built on the revised TAM model to study the impact of trustworthiness of social media on the intention to use it among employees in the Ministry of Interior in Bahrain, as it is shown in Figure 4 and this framework will be elaborated more upon in the text.
| Figure 4. |
|---|
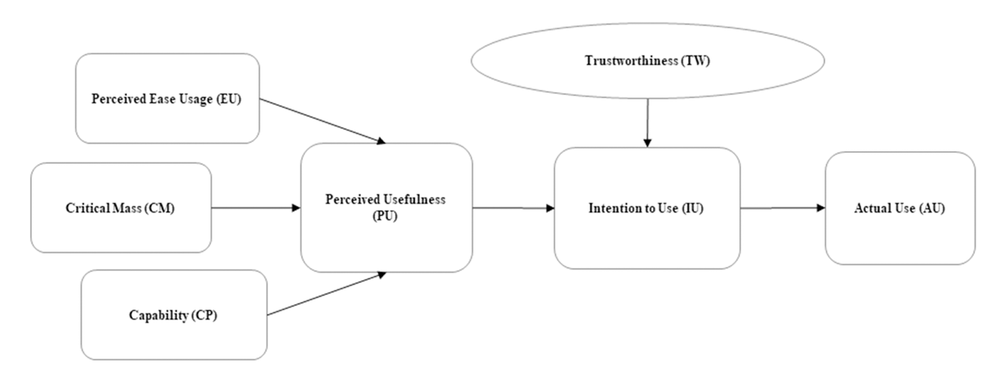 |
Table 1 summarizes the conceptual definition of each variable of this research as mentioned in the literature.
Table 1. Conceptual definitions of variables
| Variable | Conceptual Definition | Source |
|---|---|---|
| Perceived Usefulness (PU) | The degree to which a person believes that using a particular system would enhance his/ her performance | Venktatesh & Davis (2000) |
| Perceived Ease Usage (EU) | The degree to which a person believes that using a particular system would be free of effort | |
| Critical Mass (CM) |
The extent of the membership of people that matters most in a user’s social media network | Cameron & Webster (2005) |
| Capability (CP) |
Exchanges of diverse and rich media and the availability of applications enabling high levels of interactivity at social media | Daft & Lengel (1986) |
| Intention to Use (IU) |
The voluntary and cognitive representation of the user’s readiness to actually use the social media and it is determined by the user’s perceived benefits from social media | Rauniar, et al. (2014) |
| Actual Use (AU) |
The frequency of social media used by the user | |
| Trustworthiness (TW) | The extent to which a user is confident of the implicit contracts with the social media and other users and the user’s confidence towards the websites concerning freedom from risk of danger or doubt during the e-service process |
Perceived Ease Usage (EU) of Social Media
Venktatesh & Davis (2000) defined perceived ease usage as the degree to which a person believes that using a particular system would be free of effort.
It is been pointed out that the use of both Facebook and LinkedIn by adults has grown by 88% between 2009 and 2010 (Madden, 2010). This increasing diversity of users signing up with the social media is due to its relatively easy usage (Rauniar, et al., 2014). The concept of ease usage implies that users of social media will intend to use a given application that requires the least average effort, and they will be more appreciative of the minimum effort required to learn any specific feature such as uploading and sharing video or networking with their friends (Rauniar, et al., 2014).
The importance of perceived ease of use signifies the degree to which an innovation is perceived not to be difficult to, understand, learn, and use (Roger, 1962; Zeithmal, et al., 2002). It is clear that an easy to use application or site could enhance the user’s experience. Thus, based on TAM, the following hypothesis is proposed:
Hypothesis One: There is a significant relationship between perceived easy usage and perceived usefulness of social media.
Critical Mass (CM) of Social media
Cameron & Webster (2005) defined critical mass as the extent of the membership of people that matters most in a user’s social media network.
TAM has become very popular due to its simplicity (i.e., parsimony), verifiability, and ability to predict acceptance and usage of new technologies in various fields (i.e., generalizability) (Lee. et al., 2003; Hoof et al., 2005). However, TAM assumed that information systems are used only inside organizations for workers’ efficiency improvements and excluded the fact that information systems could also be used outside by individual users. Moreover, TAM theory does not explain the roles of other users in prompting an individual’s usage behavior and attitude toward social media (Rauniar, et al., 2014).
From a psychological perspective, social impact is rooted from the assumption that a person’s behavior is heavily influenced by the behavior of others (Rauniar, et al., 2014). Explicitly, the mass users networking in social media are considered as a critical component to explain the social media usage behavior (i.e. Critical Mass CM), and thus the following hypothesis is proposed:
Hypothesis Two: There is a significant relationship between critical mass and perceived usefulness of social media.
Capability (CP) of Social media
Daft & Lengel (1986) defined capability as exchanges of diverse and rich media and the availability of applications enabling high levels of interactivity at social media.
Various tools and applications are provided through social media which could boost the services provided to the users while they share and exchange information (Rauniar, et al., 2014). For instance, Snapchat allows users to communicate one-to-one with their followers, tell their stories in a unique way, save and share these stories on other platforms and they can view their story up to 24 hours before it is automatically deleted. Although it started just around 8 years ago in 2011, Snapchat is accessed by 150 million daily, and US advertisers spent around $50 million in 2015 (Meeker, 2014).
It is been argued that the vast growing usages of social media can also be attributed to the availability and effectiveness of tools and features in order to meet users’ needs (i.e. Capability CP) (Rauniar, et al., 2014). Therefore, the following hypothesis is proposed:
Hypothesis Three: There is a significant relationship between capability and perceived usefulness of social media.
Perceived Usefulness (PU), Intention to Use (IU) and Actual Use (AU) of Social media
Venktatesh & Davis (2000) defined perceived usefulness as the degree to which a person believes that using a particular system would enhance his/ her performance. While Rauniar, et al. (2014) defined the intention to use as the intended and cognitive representation of the user’s readiness to actually use the social media and it is determined by the user’s perceived benefits from social media and the actual use as the frequency of social media used by the user.
Based on TAM, it is been assumed that attitudes about perceived usefulness could determine users’ intention to use social media and accordingly their actual use (Davis, 1989; Venktatesh & Davis, 2000). Moreover, they argued that based on TRA, behaviors of social media users’ is determined by their intentions and in turn, these intentions are a function of their perceived benefits from social media (i.e., Perceived Usefulness PU). In fact, there is extensive empirical evidence that has examined the belief-intention-behavior causality in the context of usage of various technologies (Davis et al., 1989; Davis, 1989 & Igbaria et al., 1996).
Social media intentions are the perceptive representation of a user’s readiness in order to actually use the social media, and it is considered as the immediate antecedent of social media usage in TAM (Rauniar, et al., 2014). In this regard, TRA also recommends that the more favorable the attitude toward a behavior, the stronger the person’s intention to perform such behavior. Thus the following hypotheses are proposed:
Hypothesis Four: There is a significant relationship between perceived usefulness and intention to use social media.
Hypothesis Five: There is a significant relationship between intention to use and actual use of social media.
Trustworthiness (TW) of Social media
Rauniar, et al. (2014) defined trustworthiness as the extent to which a user is confident of the implicit contracts with the social media site and other users and the user’s confidence towards the websites concerning freedom from risk of danger or doubt during the e-service process.
The provenance, reputation, privacy and security of Web and email data are having a great deal of discussion. The material that people are posting to the public nowadays, would only have been seen by their close friends, and this in turn is changing the nature of privacy (George, 2006). Determining the accuracy of data from a given Web source becomes more difficult due to the large volume of information available (Anderson, 2007).
There is a concern with respect to some of the more doubtful aspects of search engine optimization, in which search engines are manipulated so that certain websites would appear higher in the rankings. This is for the purpose of having an excessively high score in search engine rankings and the potential for Semantic Web spam, which deliberately falsified published information (Mann, 2006). For this reason, trust is at the highest levels of the Semantic Web model (Matthews, 2005). For instance, there are large numbers of spam and email filters on the market, and they are still not regarded as fully adequate (Anderson, 2007). Brondsema & Schamp (2006) have been argued that such filters should make more use of trust ratings determined from social networks. Therefore, the following hypothesis is proposed:
Hypothesis Six: There is a significant relationship between trustworthiness and intention to use social media.
Based on the review of previous literature on social media and TAM model, few empirical studies have been conducted to scientifically evaluate and examine the usage behavior of social media (Rauniar, et al., 2014). In fact, a validated instrument of usage behavior of social media can provide usability experts and practitioners with a validated tool to assess social media acceptance and usage behavior. In this regard, Boyd and Ellison (2007) claimed that such instrument could gain a better understanding of “who is and who is not using social media, why and for what purposes”. Figure 5 illustrate the research framework along with the proposed hypotheses based on the literature review.
| Figure 5. |
|---|
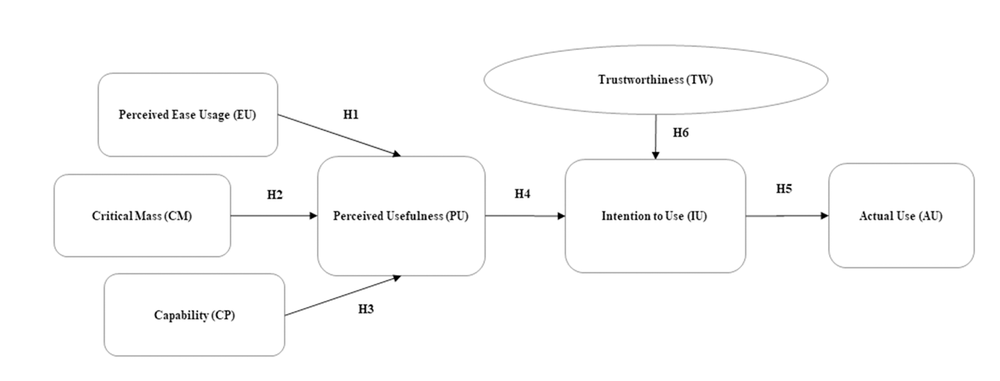 |
Research Hypotheses
Hypothesis One: There is a significant relationship between perceived easy usage and perceived usefulness of social media.
Hypothesis Two: There is a significant relationship between critical mass and perceived usefulness of social media.
Hypothesis Three: There is a significant relationship between capability and perceived usefulness of social media.
Hypothesis Four: There is a significant relationship between perceived usefulness and intention to use social media.
Hypothesis Five: There is a significant relationship between intention to use and actual use of social media.
Hypothesis Six: There is a significant relationship between trustworthiness and intention to use social media.
Methodology of The Study
Research Instrument and Tools
Data for this research was gathered through a quantitative method, in which a questionnaire was used as a primary data and the measurement of the variables is highlighted in Table 2. The questionnaire items were measured by means of five-point Likert scale from 1 to 5 rating from strongly disagree to strongly agree. The scales for these items were adapted from prior studies who have already established their reliability and validity, as it is illustrated in Table 2. However, the language of these items was modified to reflect the measurement of each variable for social media users. A Cronbach’s Alpha test was re-conducted to test the reliability of the research instrument as it will be shown later in Table 4. Spearman’s rank correlation was conducted to determine whether there is evidence of a linear relationship between the variables as per each hypothesis generated previously. All collected data were analyzed statistically using SPSS v25.0 software.
Operational Definitions of Variables
Operational definitions are used to define a given variable in terms of a process needed to determine its existence. The scale for this research variables are adapted from various literatures of which have already established their reliability and validity. For instance, the scale of perceived usefulness, perceived ease usage, intention to use and actual use were adapted from (Davis, 1986, 1989; Mathieson, 1991; Moore & Benbasat, 1991; Taylor & Todd, 1995; Venkatesh & Davis, 1996), critical mass was adapted from (Rouibah & Abbas, 2006), capability was (Rauniar et al. 2014), and trustworthiness was adapted from (Telzrow ey el. 2007; Fogels & Nehmad 2009).
In order to empirically examine the revised TAM model, a total of 25 items were generated. However, after conducting the reliability test using Cronbach Alpha, the initially adapted items were modified, dropped and re-worded for clarity and relevance for this research. The finalized items were 20, of which two items measure perceived usefulness, five items measure perceived ease usage, three items measure critical mass, two items measure capability, two items measure intention to use and two items measure actual use. The description of finalized items are illustrated in Table 2.
Table 2. Operational definitions of variables
| Variables | Measurement | Source |
|---|---|---|
| Perceived Usefulness (PU) | 1. Using social media makes it easier to stay in touch. | Davis, 1986, 1989; Mathieson, 1991; Moore & Benbasat, 1991; Taylor & Todd, 1995; Venkatesh & Davis, 1996 |
| 2. Using social media makes it easier to stay informed with my friends and family. | ||
| Perceived Ease Usage (EU) | 1. Social media is flexible to interact with. | |
| 2. Interaction with social media is clear and understandable. | ||
| 3. It is easy to become skilled at using social media. | ||
| 4. I find it easy to get social media to do what I want to do. | ||
| 5. I find social media easy to use. | ||
| Critical Mass (CM) | 1. Social media is popular among my friends. | Rouibah & Abbas (2006) |
| 2. Most of my friends are on social media. | ||
| 3. Most of my colleagues are on social media. | ||
| Capability (CP) |
1. Social media provides clear instructions for posting. | Rauniar et al. (2014) |
| 2. Images and videos can easily be downloaded or uploaded on social media. | ||
| Intention to Use (IU) | 1. I intend to use social media for communicating with others. | Davis, 1986, 1989; Mathieson, 1991; Moore & Benbasat, 1991; Taylor & Todd, 1995; Venkatesh & Davis, 1996 |
| 2. I will continue to use social media for my social networking. | ||
| Actual Use (AU) |
1. How often per day do you visit your social media accounts? | |
| 2. How many hours do you spend on your social media accounts per day? | ||
| Trustworthiness (TW) | 1. I trust social media for my personal information on my profile. | Telzrow ey el. (2007); Fogels & Nehmad (2009) |
| 2. Social media provides security for everything I post. | ||
| 3. I feel safe in everything I post in social media. |
Research Sampling
A convenient sampling was applied, in which the most easily accessible managers and employees in MOI were chosen. This is due to time constraints and difficulty in reaching the entire population of MOI. The total sample size was 170, while the valid returned questionnaires were 165 and thus the response rate was 97%, as it is illustrated in Table 3.
Table 3. Response rate
| Description | No. of Questionnaires |
|---|---|
| No. of Questionnaires Distributed | 170 |
| No. of Questionnaires Retrieved | 165 |
| Response Rate | 97% |
Demographic Profile of Respondents
First Dimension: Gender
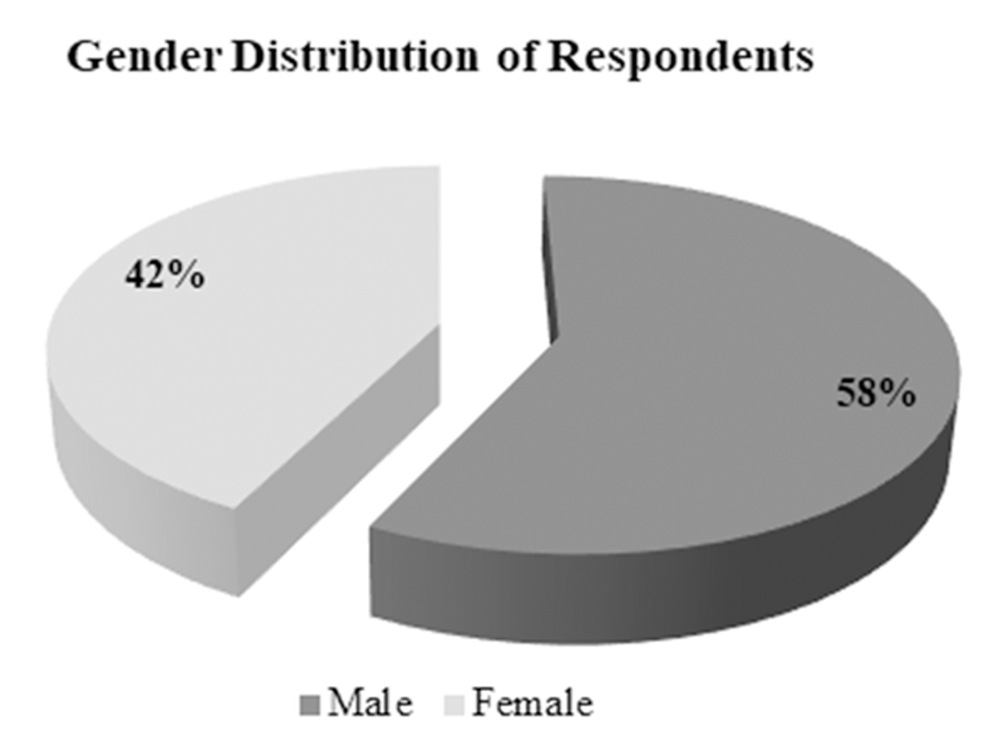
Figure 6 below shows the respondents’ gender, in which 58% of the respondents were male, while 42% were female of the total number of respondents. This implies that the sample size of this research is approximately mixed of both gender.
| Figure 6. |
|---|
 |
Second Dimension: Age
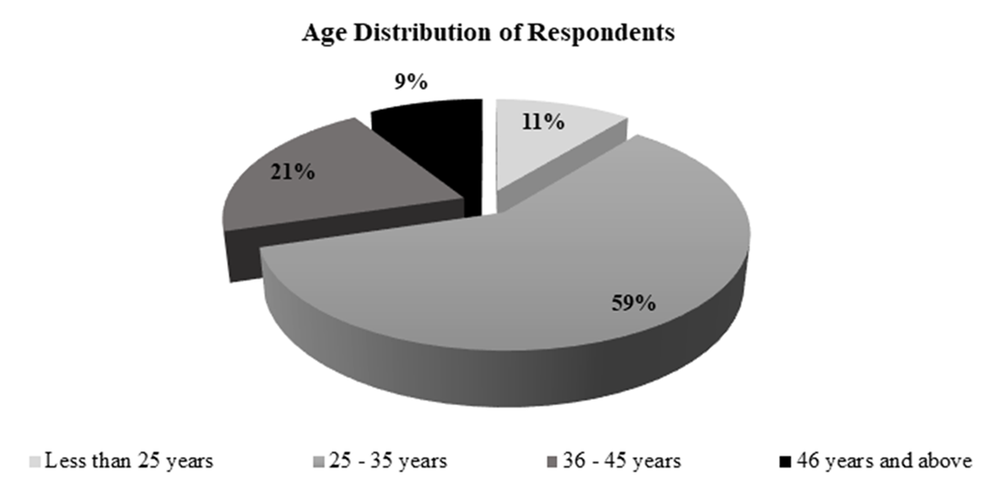
Figure 7 below shows the percentage of respondents’ age. Based on the analysis, it was found that 59% of respondents were between 25 - 35 years old, followed by 21% for the age group between 36 - 45 years old. However, only 11% of respondents were less than 25 years old and 9% of respondents were 46 years and above. This implies that the majority of respondents are young adults. However, still the questionnaire is consisted of a mixed age groups, which indicates that the sample of this study is of a varied age groups. This in turn assures true interpretation of answers and prevents biases.
| Figure 7. |
|---|
 |
Third Dimension: Educational Level
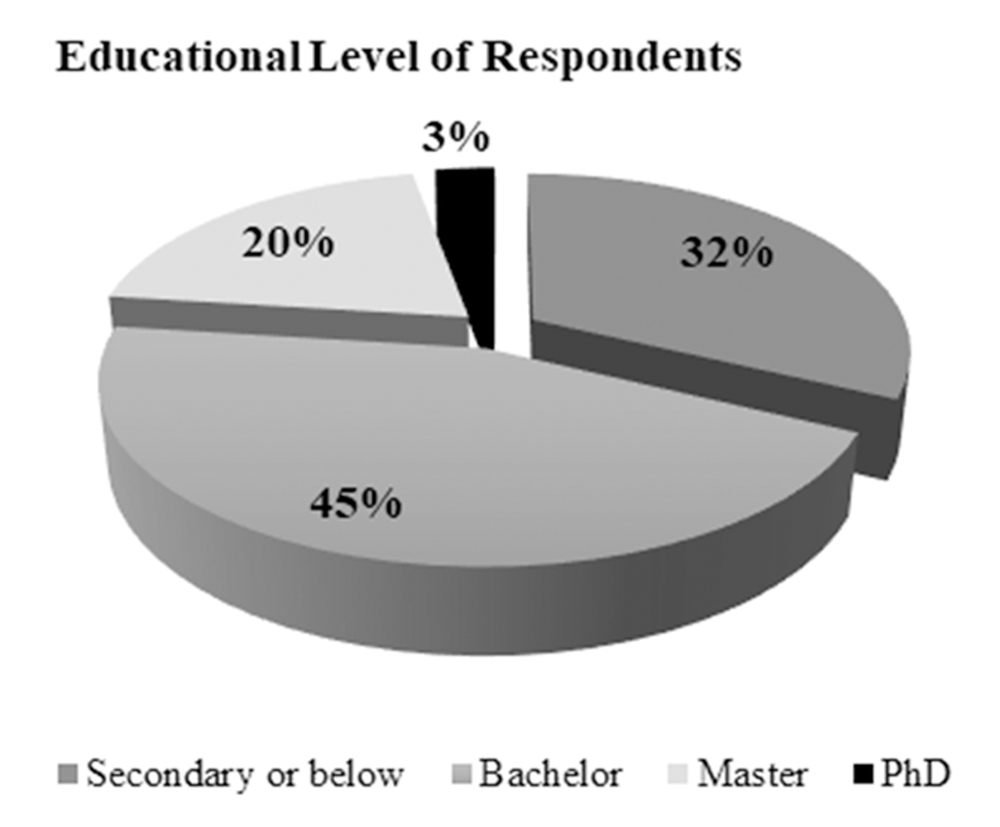
Figure 8 below represents educational level of the respondents. Based on the analysis, it was found that 45% of the respondents have Bachelor’s degree, while only 3% of total respondents have a PhD degree. This implies that the majority of the respondents have the required knowledge and understanding in order to fill the questionnaire. Moreover, their responses were consistent and accurate and only few clarifications were provided to some of them.
| Figure 8. |
|---|
 |
Fourth Dimension: Occupational Level
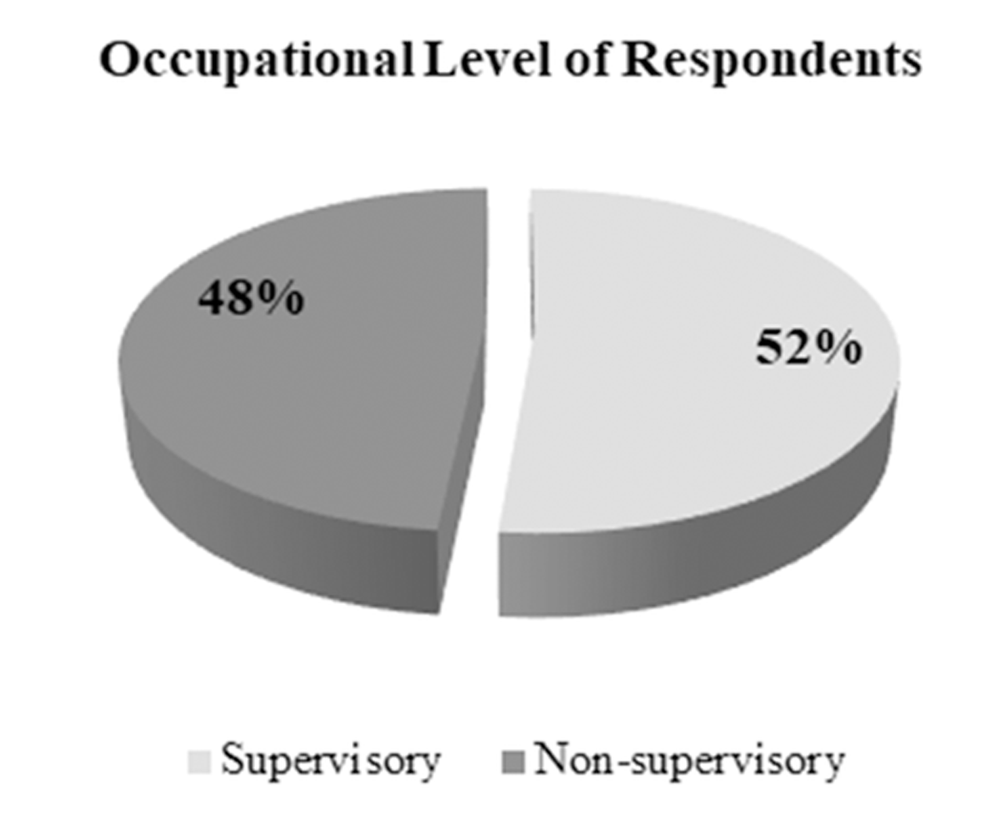
Figure 9 below represents the occupational level of respondents. Based on the analysis, it was found that the respondents were approximately divided equally, in which 52% of them were of supervisory level, while 48% of them were of non-supervisory level. This implies that the sample of this study is of different occupational levels. This in turn assures true explanation of answers and prevents biases.
| Figure 9. |
|---|
 |
Fifth Dimension: Years of Experience
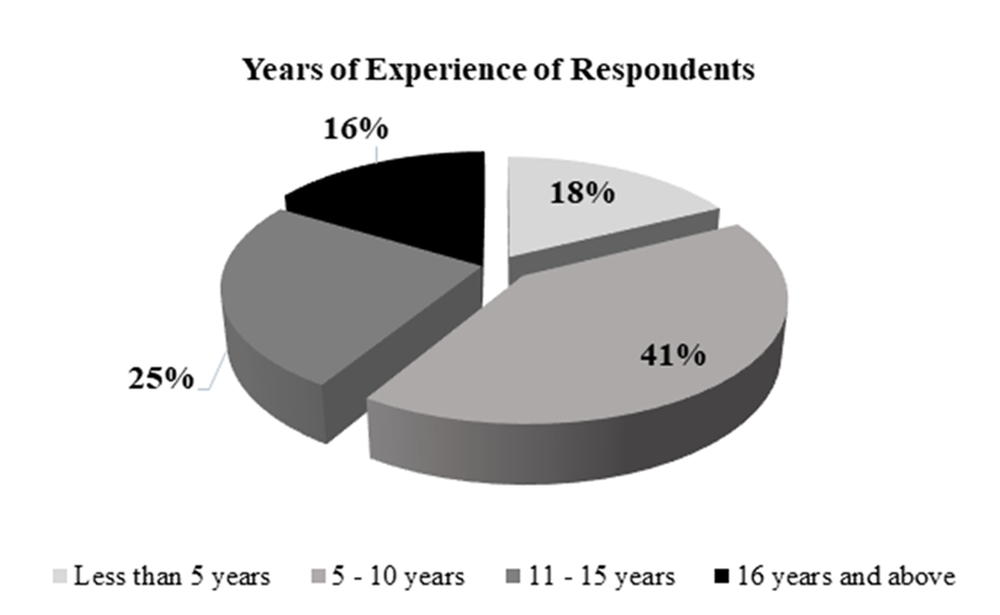
Figure 10 below shows work experience of respondents in years. Based on the analysis, it is apparent that the majority of respondents have work experience between 5 to 10 years i.e., 41% and 25% have work experience between 11 to 15 years. However, those with work experience of 16 years and above constitute 16% of the total respondents. This implies that respondents have moderate work experience. They have been working within the Ministry for some time and their responses were based on what they have been experiencing at their work.
| Figure 10. |
|---|
 |
Scale Reliability Analysis
Cronbach’s Alpha test was utilized in order to test the reliability of the research instrument. All returned questionnaires were included in the scale reliability. The overall scale reliability exceeded the minimum required Cronbach’s alpha which is 0.70. This is an indication of a strong internal consistency among the variables’ items. This implies that a respondent who intended to select a high score for one item of a variable also intended to select high scores for the others; similarly, a respondent who selected a low score for one item intended to select low scores for the other variable’s items. Table 4 shows scale reliability analysis of the research instrument in this study:
Table 4. Scale reliability analysis
| No. of Items | Cronbach’s Alpha | |
|---|---|---|
| Overall Scale Reliability | 20 | 0.839 |
Spearman’s Correlation Analysis
Spearman’s rank correlation coefficient is a nonparametric statistical measure of the strength of a relationship between paired data, in which the correlation ranges from -1 to 1 (-1< rs< 1).
Table 5 below represents the correlations among the variables as per the hypotheses.
Table 5. Correlation analysis
| Correlations | ||||||||
|---|---|---|---|---|---|---|---|---|
| Perceived Usefulness | Perceived Ease Usage | Critical Mass | Capability | Trustworthiness | Intention to Use | Actual Use | ||
| Spearman’s rho | Perceived Usefulness | 1.000 | ||||||
| Perceived Ease Usage | 0.286** | 1.000 | ||||||
| Critical Mass | 0.334** | 0.406** | 1.000 | |||||
| Capability | 0.324** | 0.460** | 0.413** | 1.000 | ||||
| Trustworthiness | 0.318** | 0.181* | 0.067 | 0.276** | 1.000 | |||
| Intention to Use | 0.607** | 0.404** | 0.463** | 0.453** | 0.438** | 1.000 | ||
| Actual Use | 0.247** | 0.257** | 0.201** | 0.156* | 0.183* | 0.326** | 1.000 | |
| ** Correlation is significant at the level (2-tailed) | ||||||||
From the above table the following results are generated:
Hypothesis One: There is a significant relationship between perceived ease usage and Perceived Usefulness of social media with a correlation coefficient of 0.286.
Hypothesis Two: There is a significant relationship between critical mass and perceived usefulness of social media with a correlation coefficient of 0.334.
Hypothesis Three: There is a significant relationship between capability and perceived usefulness of social media with a correlation coefficient of 0.324.
Hypothesis Four: There is a significant relationship between perceived usefulness and intention to use social media with a correlation coefficient of 0.607.
Hypothesis Five: There is a significant relationship between intention to use and actual usage of social media with a correlation coefficient of 0.326.
Hypothesis Six: There is a significant relationship between trustworthiness and intention to use social media with a correlation coefficient of 0.438.
This study explained the impact of trustworthiness of social media on the intention to use it among employees in the Ministry of Interior, Kingdom of Bahrain, as a case study using the revised TAM model by (Rauniar, et al., 2014). For this purpose, the data was collected through questionnaires that were distributed to a convenient sample in the Ministry, in which the most easily accessible managers and employees were chosen. The research instrument was helpful to reach the objectives of the study and the results were accurate and provided proper understanding.
Based on the data collected through the questionnaire, it was found that the relationship between the variables - as per the hypotheses - are all significant positive relations. For instance, there is a significant positive relationship between trustworthiness and intention to use and between perceived usefulness and intention to use. This suggests that the higher the level of trust in social media, the higher will be the intentions to use it among employees in MOI. Similarly the higher the perceived usefulness of any given application, the higher will be the intentions to use it. Moreover, there is a significant positive relationship between perceived ease usage and perceived usefulness. With respect to the perceived ease usage, Bugawa & Mirzal (2017) have suggested that the Web 2.0 technologies offer a huge space for ease sharing experiences that could contribute to the reformation in the traditional learning concepts among users. Furthermore, critical mass is significantly related to perceived usefulness, in which MOI employees strongly believe that social media is popular among their friends and that most of their friends are using social media. This in turn makes it easier for them to stay in touch with their friends and family. In fact,
Rauniar, et al. (2014) have already mentioned that psychological concept of social influence is rooted from the assumption that a person’s behavior is heavily influenced by the behavior and presence of others, and this what was founded among employees in MOI. Moreover, Bugawa (2016) demonstrated that the interactivity with peers through using Web 2.0 technologies is critical for promoting more engagement and communication and it is a powerful technological tool to enhance the user’s learning experience. In fact, it is been stated that the use of social media amongst digital natives enhances a huge amount of informal learning to occur through the interaction with peers (Brown & Adler, 2008).
The study recommends the examination of the impact of security awareness on the usage of social media in public sector in Bahrain in future studies. In this study, the main challenge was the accessibility for data collection.
A case study was conducted in the Ministry of Interior, Kingdom of Bahrain to study the impact of trustworthiness of social media on the intention to use it among employees in the, using the revised TAM model by (Rauniar, et al., 2014). The study applied a quantitative method, in which the data was collected through questionnaires that were distributed to a convenient sample in the Ministry, thus the most easily accessible managers and employees were chosen. The research instrument was helpful to reach the objectives of the study and the results were accurate and provided proper understanding.
Through this study, it was found that the level of trust in the Ministry has a significant positive relation with the intention to use social media. Similarly, the intention to use social media and the actual usage were found to be significantly related.
In conclusion, it is apparent that the results of this study is well-matched with the previous literature including Rauniar, et al. (2014), which we have already adapted their model in this study. For instance, they have confirmed that in the context of social media, users may assess a given application or site based on its easiness and effectiveness in helping them accomplish their needs.
Abbate, J. (1999). Inventing the Internet (inside technology) . Cambridge, MA: MIT Press.
Al-adawiZ.YousafzaiS.PallisterJ. (2005, September). Conceptual model of citizen adoption of e-government. The Second International Conference on Innovations in Information Technology. 1-10.
AloulF. A. (2010). Information security awareness in UAE: A survey paper. In 2010 International Conference for Internet Technology and Secured Transactions IEEE.
Alqudsi-ghabra, T. M., Al-Bannai, T., & Al-Bahrani, M. (2011). The Internet in the Arab Gulf Cooperation Council (AGCC): Vehicle of Change. International Journal of Internet Science , 6(1).
Anderson, C. (2006). The Long Tail: How endless choice is creating unlimited demand . London, UK: Random House Business Books.
Anderson, P. (2007). What is Web 2.0? Ideas, technologies and implications for education. Bristol: JISC.
Anhalt, K., Telzrow, C. F., & Brown, C. L. (2007). Maternal stress and emotional status during the perinatal period and childhood adjustment. School Psychology Quarterly , 22(1), 74–90. doi:10.1037/1045-3830.22.1.74
Bahrain ICT Shared Services. (2011). Retrieved from https://www.cisco.com/c/dam/en_us/about/ac79/docs/ps/Bahrain-Govt-SS_IBSG.pdf
Boyd, D. M., & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. Journal of Computer-Mediated Communication , 13(1), 210–230. doi:10.1111/j.1083-6101.2007.00393.x
Brondsema, D., & Schamp, A. (2006). Konfidi: trust networks using PGP and RDF. Models of trust of the Web (MTW 06). WWW2006 Conference, Edinburgh, UK.
Bugawa, A. M., & Mirzal, A. (2017). The impact of the web 2.0 technologies on students’ learning experience: Interactivity inside the classroom. International Journal of Management and Applied Science. , 3(5), 46–50.
Bugawa, A. M., & Mirzal, A. (2018). The Impact of the Web 2.0 Technologies on the Learning Experience of Students in Higher Education: A Review. International Journal of Management and Applied Science , 13(3), 1–17.
Bugawa, A. M. M. (2016). The impact of the interactivity of web 2.0 technologies on the learning experience of students in higher education (Doctoral dissertation). Brunel University London.
Cameron, A. F., & Webster, J. (2005). Unintended consequences of emerging communication technologies: Instant messaging in the workplace . Computers in Human Behavior , 21(1), 85–103. doi:10.1016/j.chb.2003.12.001
Carlos Martins Rodrigues Pinho, J., & Soares, A. M. (2011). Examining the technology acceptance model in the adoption of social networks. Journal of Research in Interactive Marketing , 5(2/3), 116–129. doi:10.1108/17505931111187767
Chami, K. (2019). FinTech in the Gulf Cooperation Council (GCC). Retrieved from https://gomedici.com/how-gulf-countries-are-embracing-fintech
Daft, R. L., & Lengel, R. H. (1986). Organizational information requirements, media richness and structural design. Management Science , 32(5), 554–571. doi:10.1287/mnsc.32.5.554
Davis, F. D. (1986). A technology acceptance model for empirically testing new end-user information systems. Cambridge, MA: Academic Press.
Davis, F. D. (1989). Perceived usefulness, perceived ease of use, and user acceptance of information technology . Management Information Systems Quarterly , 13(3), 319–340. doi:10.2307/249008
Davis, F. D., Bagozzi, R. P., & Warshaw, P. R. (1989). User acceptance of computer technology: A comparison of two theoretical models. Management Science , 35(8), 982–1003. doi:10.1287/mnsc.35.8.982
Fishbein, M., & Ajzen, I. (1975). Belief, attitude, intention and behavior . Academic Press.
Fogel, J., & Nehmad, E. (2009). Internet social network communities: Risk taking, trust, and privacy concerns. Computers in Human Behavior , 25(1), 153–160. doi:10.1016/j.chb.2008.08.006
George, A. (2006). Things you wouldn’t tell your mother. New Scientist , 191(2569), 50–51. doi:10.1016/S0262-4079(06)60502-2
Ghannam, J. (2011). Social media in the Arab World: Leading up to the Uprisings of 2011. Center for International Media Assistance, 3(1), 1-44.
Gikas, J., & Grant, M. M. (2013). Mobile computing devices in higher education: Student perspectives on learning with cellphones, smartphones & social media. The Internet and Higher Education , 19, 18–26. doi:10.1016/j.iheduc.2013.06.002
Igbaria, M., Parasuraman, S., & Baroudi, J. J. (1996). A motivational model of microcomputer usage. Journal of Management Information Systems , 13(1), 127–143. doi:10.1080/07421222.1996.11518115
Klemperer, P. (2006). Network Effects and Switching Costs: Two Short Essays for The New Palgrave. Working Paper Series. Social Science Research Network.
Lee, Y., Kozar, K. A., & Larsen, K. R. (2003). The technology acceptance model: Past, present, and future. Communications of the Association for Information Systems , 12(1), 50.
Liebowitz, S. J., & Margolis, S. (1994). Network Externality: An Uncommon Tragedy. The Journal of Economic Perspectives , 8(2), 133–150. doi:10.1257/jep.8.2.133
Madden, M. (2010). Older adults and social media. Pew Internet & American Life Project, 27.
Mann, C. C. (2006). Spam+ Blogs= Trouble Splogs are the latest thing in online fraud-and they could smother the Net as we know it. Wired , 14(9), 104.
Manuel, C. (2013). The Impact of the Internet on Society: A Global Perspective. Retrieved from https://www.bbvaopenmind.com/en/articles/the-impact-of-the-internet-on-society-a-global-perspective/
Mathieson, K. (1991). Predicting user intentions: Comparing the technology acceptance model with the theory of planned behavior. Information Systems Research , 2(3), 173–191. doi:10.1287/isre.2.3.173
Matthews, B. (2005). Semantic web technologies. E-learning , 6(6), 8.
Meeker, M. (2014). Internet trends 2014-code conference. Academic Press.
Merchant, G. (2009). Web 2.0, new literacies, and the idea of learning through participation. English Teaching , 8(3), 107–122.
Miniwatts Marketing Group. (2010). World Internet Usage and Population Statistics. Retrieved from https://www.internetworldstats.com/stats.htm
Moore, G. C., & Benbasat, I. (1991). Development of an instrument to measure the perceptions of adopting an information technology innovation. Information Systems Research , 2(3), 192–222. doi:10.1287/isre.2.3.192
Qasem, M., & Zolait, A. H. (2016). Determinants of Behavioral Intentions towards Using E-Government Services in the Kingdom of Bahrain. International Journal of Computing and Digital Systems , 5(04), 345–355. doi:10.12785/ijcds/050406
Rauniar, R., Rawski, G., Yang, J., & Johnson, B. (2014). Technology acceptance model (TAM) and Social media usage: An empirical study on Facebook. Journal of Enterprise Information Management , 27(1), 6–30. doi:10.1108/JEIM-04-2012-0011
Rogers, E. M. (1962). Diffusion of Innovations . New York, NY: Free Press.
Rouibah, K., & Abbas, H. (2006). A modified technology acceptance model for camera mobile phone adoption: development and validation. ACIS 2006 Proceedings, 13.
Seely Brown, J., & Adler, R. P. (2008). Open education, the long tail, and learning 2.0. EDUCAUSE Review , 43(1), 16–20.
Selman, Z., & Faiq, K. (2018). Technology in the GCC. Retrieved from https://www2.deloitte.com/eg/en/pages/about-deloitte/articles/transform-saudi-arabia/gcc-technology.html
Taylor, S., & Todd, P. A. (1995). Understanding information technology usage: A test of competing models. Information Systems Research , 6(2), 144–176. doi:10.1287/isre.6.2.144
Tim, O. (2005). What is web 2.0? Design patterns and business models for the next generation of software. Academic Press.
TRA Annual Report. (2017). Retrieved from http://www.tra.org.bh/media/document/TRA%20Annual%20Report%202017%20-%20English2.pdf
Van den Hooff, B., Groot, J., & de Jonge, S. (2005). Situational influences on the use of communication technologies: A meta-analysis and exploratory study. The Journal of Business Communication, 42(1), 4-27.
Venkatesh, V., & Davis, F. D. (1996). A model of the antecedents of perceived ease of use: Development and test. Decision Sciences , 27(3), 451–481. doi:10.1111/j.1540-5915.1996.tb01822.x
Venkatesh, V., & Davis, F. D. (2000). A theoretical extension of the technology acceptance model: Four longitudinal field studies. Management Science , 46(2), 186–204. doi:10.1287/mnsc.46.2.186.11926
Zolait, A. H. S., Al-Anizi, R. R., & Ababneh, S. (2014). User awareness of Social media security: The public sector framework . International Journal of Business Information Systems , 17(3), 261–282. doi:10.1504/IJBIS.2014.064973