University of Bahrain, Bahrain
Royal University for Women, Bahrain
The Social Development Office of His Highness the Kuwait Prime Minister’s Diwan, Kuwait
Cybercrime Prevention in Higher Learning Institutions
The internet has revolutionized the way people communicate, how they manage their business, and even how they conduct their studies. Organizations can conduct meetings virtually and store all their data online. With this convenience, however, comes the risk of cybercrime (CC). Some of the world’s most renowned organizations have found themselves having to incur huge recovery costs after falling prey to CC. Higher learning institutions’ databases are increasingly falling victim to CCs, owing to the vast amounts of personal and research data they harbor. Despite this, the area of CCs in learning institutions remains understudied. This chapter seeks to identify how CC is manifested in such institutions and the specific cybersecurity measures that stakeholders could use to minimize their exposure to the same. The qualitative case study was designed to explore the research questions, and collected data through semistructured interviews. The findings showed hacking, phishing, and spoofing as the most common manifestations of cybercrime in higher learning institutions.
The Internet is a part of daily living in the world today. Activities that traditionally required people to move physically across geographical areas are now conducted conveniently over the Internet. People can communicate easily and cheaply with relatives and friends miles away without the need to visit or travel physically. Similarly, banking activities, access to academic material, government services, and general data transfer have been made easier with the evolution of the Internet. The Internet has revolutionized the way things are done, opening up capabilities that would otherwise have never been realized. Unfortunately, these new capabilities have come at a cost; despite opening up opportunities for progress and prosperity, the Internet has brought new risks to nations, organizations, and individuals.
One of the prominent risks which are associated with Internet usage is cybercrime, namely crime executed with the help of electronic systems (Al-Alawi, 2014; Broadhurst, Grabsoky, Alazab, & Chon, 2014; Okeshola & Adeta, 2013). In order to protect themselves from cybercrime, nations, organizations, and individuals are pushed to put in place cybersecurity measures. This is mainly because, once a computer is connected to another device, it is described as “vulnerable” (Al-Alawi & Abdelgadir, 2006). Developing effective measures, however, requires a succinct understanding of the current landscape of cybercrime, including its nature, causes, and predisposing factors. This chapter focuses on cybercrime within higher learning institutions. It provides insight into the factors that predispose such institutions to cybercrime, the ways in which the same is manifested, and the measures that could be used to minimize the risk of exposure. For clarification purposes, the term “cybercrime” is integral to this text and will be taken to indicate the various efforts that institutions could use to secure their networks. Nevertheless, the precepts the authors present herein will provide guidance to policymakers in learning institutions on how to develop effective cybersecurity mechanisms to protect both data and students.
Problem Statement
Recent incidents depict higher learning institutions as attractive troves for cybercriminals. Several renowned institutions have fallen prey to cybercrime, in recent years, in the United States and beyond. In 2015, for instance, Penn State University fell victim to a data breach that affected the personal information of close to 18,000 students (Harris & Hammargren, 2016). In the same year, Harvard University had its systems in eight administrative offices and colleges compromised, although it is still not clear exactly what information the hackers were after. One of North Dakota University’s databases was hacked, compromising the social security numbers and identities of over 300, 000 alumni. A similar breach was reported at the Indiana University in the same year, compromising the social security information, addresses, and names of close to 146,000 students. Maryland University also fell victim to a data breach in 2014, where the identification numbers, birth dates, and names of over 310,000 employees and students was compromised.
A report by the Ponemon Institute (2015) revealed that, in 2014, educational institutions in the U.S. incurred costs of close to $8 million in cybercrime-related incidents. Studies indicate that colleges and universities are attractive cybercrime targets, because they harbor huge amounts of sensitive student information, including health and financial data. Moreover, university databases harbor huge chunks of research data from which hackers could benefit by selling them (Okeshola & Adeta, 2013).
Despite the growing number of data breaches in higher learning institutions, the area remains severely understudied. Most studies have focused on cybercrime in general, creating a knowledge gap in the area of educational institutions. This chapter complements the existing literature by delving into the understudied area of cybercrime in higher learning institutions. It analyzes the nature of cybercrime in these institutions and the measures that could be taken to promote cybersecurity.
The research questions directing the chapter are:
The chapter aims at realizing the following objectives:
The chapter will be a source of insight for policymakers in higher learning institutions. Its findings will help reduce the prevalence of cybercrime and its associated costs in these institutions.
The chapter uses the qualitative case study approach. The authors propose the ABC University, which has been recently identified as home to the leading cybersecurity program in higher learning institutions, and the XYZ University as case studies. The researchers conducted a qualitative interview with the ABC’s Network Services head to obtain insight into the ways in which cybercrime is manifested in the institution and the measures that the institution’s management has put in place to safeguard against cybercrime. Also, the authors carried out document reviews, particularly in the cybersecurity program of XYZ University, as they were unable to physically visit the institution for data collection. They transcribed the answers they had obtained from the interview, analyzed them alongside those they had obtained from the review, and presented them in prose as the study findings.
This section reviews the literature in the area of cybercrime. Much has been studied and said about cybercrime. However, this review focuses on three areas that the authors deem most relevant to the chapter, namely the theoretical background of cybercrime, the drivers of cybercrime, and the types/tools of cybercrime. Literature focusing specifically on higher learning institutions is limited. Therefore, the review is not limited to articles touching on higher learning institutions.
The Theoretical Underpinning of Cybercrime
As the globe grows into digitization, it approaches more attacks. According to Fellows (2019), institutions of all size face day-to-day, if not every-minute, cyber interruptions, “as criminals, hacktivists, and hostile nations seek to profit from poor IT [information technology] security practices” Due to fast technology transformations, universities are accelerating their digital footsteps. Fellows indicated that a study by VMware and Dell EMC advises further work is needed, if higher educations are not going “to be easy ways to access national secrets.” She added that 25% of top IT management who had studied at United Kingdom’s higher education considered their security systems and defense study may have already been breached, and about 53% indicated that cyberattack on their university had managed “to research ending up in foreign hands” (par.). The targeted incidents in scientific (54%), medical (50%), economic (37%), and defense research (33%) were top of the list. About 50% of the respondents acknowledged that a lack investment in IT is pushing the necessity for more influential cybersecurity. Furthermore, the top IT management stated that cyberattack on their study data can cause critical financial damage for their university.
Gearhart, Abbiatti, and Miller’s (2019) distributed questionnaires to the presidents of 150 higher education institutions in the USA to resolve the extent of top university management’s participation in cybersecurity. The survey findings indicated that the board of cybersecurity strategy was mainly delivered to the top information systems or business managers, that main anxieties are “about the safety of data related to financial, student, faculty, and donor affairs,” and about 50% of the higher education top management, and that about half of college leaders reveal cybersecurity correlated concerns two to six times a week. Besides, Gearhart et al. recommended research on how decisions are made about cybersecurity priorities, as well as how to best provide training for better cybersecurity decision-making.
Beyond the United States, in 2011, the Hawaii University incurred approximately $550,000 in restoration costs after a database was hacked, compromising the credit card details of over 90,000 students (Harris & Hammargren, 2016). An incident of similar magnitude was reported at the New England Elite University, in the UK, in 2015.
Chapman (2019) stated that, throughout 2018, over 1000 distributed denial of service (DDoS) attacks were identified, in contradiction of 241 different UK education and research institutions. Analyzing the timings of these attacks has indicated to assume that “many of them are ‘insider’ attacks launched by disgruntled students” or employees.
Raman, Kabir, Hejazi, and Aggarwal (2016) indicated that currently universities are reached at the top five industries to face unlimited numbers of cyberattacks, due to the huge amount of data of their repositories. Figure1 shows the significant rise in the number of cyberattacks on higher education institutions.
| Figure 1. Data breaches in higher education institutions |
|---|
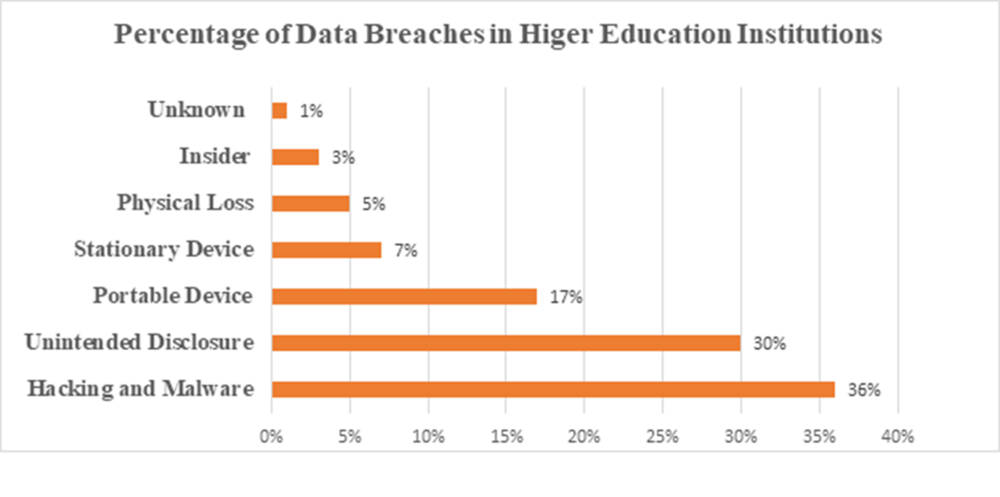 |
Figure 1 illustrates that the highest percentage of data breaches in universities is hacking and malware (36%), and unintended disclosure is the second to the highest (30%).
Raman et al. (2016) reported the cases of a few universities which had been hacked around the globe. The first case was King Saud University, in Saudi Arabia. In January 2012, an anonymous hacker attacked the university’s official Web site, hacked 812 end-users’ accounts, and dropped their contents (e.g., e-mail addresses, mobile phone numbers, and passwords) on a file-sharing site. The second case was University of Delaware, in U.S. In July 2013, the cyberattack target was on the university’s computer system. The hacker exploited a vulnerability in Web-based software Delaware University used, and stole and exposed the identities of more than 72,000 users (i.e., past and currents workers’ names, address, and Social Security numbers. The third case was University of Maryland, U.S. In March 2014, the cyberattack aimed the network, compromising 287,580 data of the faculty members, students’ records, university employees, and affiliated people. The database breach distracted all who had been issued a university ID cards between 1998 and February 2014, and the network was out of services for 3 days. The fourth case was Pennsylvania State University, U.S. In May 2015, two complicated cyberattacks (one of them was from foreign countries) aimed the Engineering College and threaten server holding data relating to 18,000 users that were undetected for someday. The fifth case included six Japanese universities. In July 2015, the networks of these Japanese universities originated a real-time cyberattack affecting 360 records, e-mail addresses, and ID numbers, which the hackers leaked from one university and linked to the Web site administrators of all other universities. The last case was Concordia University, in Canada. In March 2016, several library standing express workstations were breached by detecting Keylogger devices in the libraries. Keylogger devices can capture end-users data, such as login passwords and information. Furthermore, the access to the library’s computers was obtainable for general public use for about 10 minutes a day.
Also, according to another source (“Yale University revealed,” 2018), in June 2018, the IT team of Yale University, U.S., discovered a cyber breach of log during the regular servers security check. The hackers had been able to obtain access to the database to steal sensitive information. An article in The Guardian (Press Association, 2019) reported Lancaster University students’ data and other records were stolen in cyberattacks, and retrieved student applicants for 2019-2020 and false bills sent in malicious hack to the students. The access consisted in phishing cyberattacks. Storm (2017) stated that the Russian hacker Rasputin breached 63 U.S. and UK universities before trying “to sell the stolen data on the dark web” Furthermore, Rasputin similarly attacked 35 universities, namely 24 in the U.S., 10 in the U.K., and one in India. The hacker conducted all of these cyberattacks by SQL injection.
Researchers contend that cybercrime can be explained using the differential association theory (Holt, Strumsky, Smirnova, & Kilger, 2012; Okeshola & Adeta, 2013). Cresey (1954) sustained that individuals acquire motives and attitudes for criminal behavior through their interactions with others. One’s environment influences his/her culture and the norms by which he/she lives. The same environment influences which norms individuals choose to violate. The concept of differential association implies that, when an individual interacts with others and the community, he/she encounters elements that encourage him/her to violate the law and others that discourage him/her from doing so (Al-Alawi & Hafedh, 2006; Okeshola & Adeta, 2013). One is inclined to acquire criminal tendencies, if the elements that encourage criminality exceed those that discourage it (Okeshola & Adeta, 2013). This view supports Holt et al.’s (2012) idea that one is more likely to display criminal behavior, if his/her environment and social circle favor criminality, and if he/she perceives the gains of violation as exceeding those of compliance. Similarly, when one’s legal (pro-social) influences exceed his/her criminal influences, he/she is less likely to display criminal behavior. The authors agree that differential association is more prevalent in socioeconomically disadvantaged areas, which tend to encourage resistance towards those in authority and, by extension, the law.
Okeshola and Adeta (2013) explained the mechanism by which an individual acquires these tendencies. According to these authors, the communication process forms the basis of behavioral acquisition. If an individual repeatedly watches as others in his/her social circle engage in criminal acts, he/she, in time, learns this criminal behavior. Individuals learn the drive, techniques, motives, and attitudes for committing crime. In the process, their ideas and opinions are rationalized such that they no longer perceive criminal actions as wrong.
Applying the differential association principle to cybercrime, the authors opine that cybercriminals learn their criminal acts from their environments and their daily interactions with others (Holt et al. 2012; Okeshola & Adeta, 2013). Cybercriminals are usually tech-savvy, knowledgeable, and very intelligent individuals. Their social circles are composed of individuals who share the same technological interests and who execute most of their interactions in the form of electronic communications. Initially, the individual may not have the inclination to engage in cybercrime as he/she perceives the same as an act of fraud. As he/she repeatedly sees others engage in the same, however, his/her opinions are rationalized and he/she is then influenced into performing acts of cybercrime.
Drivers of Cybercrime
Researchers have given diverse perspectives on the factors that drive individuals to engage in cybercrime. In the article The Economics of Cybercrime, Kshetri (2010) stated that people engage in cybercrime because of the economic attractiveness of the expected results. The author posited that economic disadvantages are a significant driver of cybercrime. Okeshola and Adeta (2013) held a similar view, expressing that economically disadvantaged people are more likely to engage in cybercrime, either because they perceive the laws as oppressive and blame the same for their poor conditions or because they view the target as being economically attractive. This explains why the rich are more likely than the poor to be victims of cybercrime. Indeed, Okeshola and Adeta (2013) conducted an empirical study on sampled perpetrators of cybercrime and showed poverty to be a crucial driver of cybercrime, with 86.5% of respondents identifying the factor as the leading motivator behind their engagement. However, the literature evidences that poverty is only a factor during the initial engagement. Once they have established themselves in the crime, cybercriminals live more flamboyant lifestyles and only engage in the crime to maintain their lavish lifestyles.
Researchers have faulted legislation for the high prevalence of cybercrime in the society today (Oh & Lee, 2014; Okeshola & Adeta, 2013). According to Oh and Lee (2014), when the legal framework is weak and does not advance punishment to cybercrime as it should, the propensity to engage in it is relatively high. The authors contended that countries need to make cybercrime more costly as a way of discouraging people from taking part in such acts. Seventy-four percent of the respondents in Okeshola and Adeta’s (2013) study indicated that they perceived the law as being weak and unable to adequately punish cybercriminals. The society is also identified as a driver of cybercrime. Researchers opine that the society needs to stop idolizing cybercriminals. In most cases, cybercriminals are rated higher than other criminals and exalted, when they should be criminalized. Okeshola and Adeta suggest that societies increase the stigmatization levels of cybercriminals as a way of discouraging engagement.
In another attack to society, the above authors express that the tendency to celebrate wealth without questioning its source encourages individuals to engage in criminal activities, including cybercrime. This is a more prominent factor in developing economies, where a majority of the population is poor and the few rich individuals are idolized and portrayed as positive role models, without critically investigating the source of their wealth. The authors present the views of one respondent, who is also a cybercriminal, and who blames the tendency to celebrate wealth for his indulgent in cybercrime. In this respondent’s view, politicians who misappropriate public funds are called upon to launch community projects and are held in high-esteem, and the society shows no intent of criminalizing them for their actions. Such attitudes portray the society as one which treats crime leniently for the wealthy. Individuals are thus inclined to engage in crime to amass wealth.
Peer pressure is another prominent driver of cybercrime, especially among younger criminals (Dashora, 2011). The famous Bal Bharati incident in Delhi, India, where a teenager was incarcerated for creating a pornographic Web site, offers a perfect example. Following intense interrogations, the court established that the delinquent had acted in response to constant harassment from his peers. Studies have further established that boys are more susceptible to this kind of influence than girls (Ang & Goh, 2010; den Hamer, & Konijn2015; Schneider, O'donnell, Stueve & Coulter, 2012)
Tools of Cybercrime
This subsection illustrates the technologies that criminals use to execute cybercrime. Four cybercrime tools are common across the literature: E-mail bombs, password crackers, and botnets (Goodman, 2015; Loundy, 2003; Snail, 2009).
E-Mail Bombs
E-mail bombs are identified as one of the most commonly used cybercrime tools. In this case, the perpetrator sends huge numbers of e-mails to his/her victim’s mailbox to the extent that the capacity of the mailbox is exhausted. Consequently, the victim, who can either be an individual or an organization, is unable to access and read his/her/its legitimate e-mails. Serious e-mail bombing cases could paralyze an organization’s entire system. The hackers’ intention is to shut down the victim’s Web site, network, or operating system (Snail, 2009).
As Loundy (2003) indicated, one of the most prominent incidents of e-mail bombing was that where the Tamil guerrilla group attacked the Sri Lankan Embassy’s mailbox . Furthermore, they identified several indications of an e-mail flood: Syslog entries, service denial, connectivity losses, and network connection overloading and advises, which, in order to face this type of attack, the user could filter by spamming all e-mails coming from the attacker’s IP address. This would address the problem, if the attacker employs a single IP address. Otherwise, the victim needs to use proxy servers, which identify malware and messages from IP addresses which are deemed suspicious and then filters the same by predetermined rules, before sending them to the clients’ computers.
Password Crackers
Users who forget the passwords to their networks or computers can use password crackers to identify them (Vijayan, Joy, & Suchithra, 2014). Password crackers also present opportunities for people to gain unauthorized access to networks and computers that limit public access. Password crackers can either use dictionary searches or brute forces to identify unknown passwords (EC-Council, 2016). The dictionary search technique requires the password cracker to search the password dictionary word-by-word, in an attempt to identify the right password. Conversely, the brute force involves running through character combinations of a specified length until the right combination for the computer is identified. More advanced programs allow crackers to make searches for hybrids of both numbers and dictionary entries. Vijayan et al. (2014) posited that these programs can be helpful in networks that require users’ passwords to combine numbers and letters.
In Okeshola and Adeta’s (2013) study on sampled cybercriminals, 349 of the 400 respondents reported that they had used password crackers to gain unauthorized access to networks. These statistics supported Vijayan et al.’s position on the prominence of password cracking as a tool for executing cybercrime.
The literature identifies several measures that individuals and institutions could use to minimize the threat password crackers pose. Vijayan et al. suggested the use of complex passwords, perhaps containing both uppercase and lowercase letters, special symbols, and numbers. The authors further advised that network users make their passwords fairly long and change the same frequently (EC-Council, 2016; Vijayan et al., 2014). Alternatively, users could use Syskey to keep their networks secure.
Botnets
The term “botnet” is derived from the combination of two words, namely RobotNetwork. A botnet represents compromised computers in a network capable of being controlled remotely by a cybercriminal. The individual’s compromised computers are referred to as drones or zombies. The attacker controls the zombies through Internet-sent commands. Communication between the attacker’s computer and the zombies/bots is achieved through a command-and-control computer, communications channels, and a remote control (Wilson, 2008). DDos attacks and e-mail spamming are common forms of botnet attacks (Whitman & Mattors, 2010).
The literature identifies several security measures that organizations and individuals could use to protect themselves and their networks from botnet attacks. Whitman and Mattors (2010) suggested the use of updated antispyware and antivirus software. The authors advised users to make use of software that update themselves to remove viruses automatically. As a security measure, users need to set their operating systems in such a way that they can automatically download and install security updates (Al-Alawi,Al-Kandari & Abdel-Razek 2016; Wilson, 2008). Also, users need to keep their firewalls turned on as a way of denying hackers access. Firewalls increase network security by blocking communications from sources which are not authorized by the user. Whitman and Mattors (2010) stated that users of broadband need to particularly enable firewall activity. Users of MacOS and Windows do not have to install firewalls, as these operating systems have the same built-in. Users only need to ensure that the same is turned on.
Other proposed security measures include turning off one’s computer when not in use and verifying the security of e-mail attachments before downloading them. Hackers cannot launch their attacks if their target victim is not online. Users are advised to only download files from trusted sites that have been declared safe to use and visit (Al-Alawi & Hafedh 2006; Whitman & Mattors, 2010). Programs such as SiteAdvisor allow users to verify the status of sites before downloading files.
This review shows that cybercrime is a richly studied area. There are studies focusing on the causes and types of cybercrime, as well as the cybersecurity measures that victims could put in place to minimize the inherent risk. However, most of these studies have taken a general approach, with very little focus on specific organizations. Studies focusing on cybercrime, particularly in higher learning institutions, are almost nonexistent. This chapter addresses this knowledge gap. The research intent is comparing the general precepts the authors presented in this review with the data they collected on the ground to determine how the two compare. More specifically, the aim is to identify the differences and similarities between the general population’s cybercrime and cybersecurity measures and those higher learning institutions use.
This section covers the research procedures the authors used in seeking answers to the research questions. It provides details on the research design, sampling techniques, the research instrument, data collection techniques, and data analysis procedures. The authors determined the research questions directing the chapter as:
Research Procedures
The researchers visited ABC University for the interview with the head of the Networking Department. They had been sought permission to conduct the interview through written correspondence three weeks before its date and had made follow-ups a week before the scheduled date to confirm the respondent’s availability. They conducted the interview at the respondent’s office within the university, based on an interview guide (Table 1).
Table 1. Study interview guide
| Demographic Information 1. What is your networking background? 2. How long have you served as a network administrator at the University? 3. What would you identify as your success factors given the University’s high ranking in the area of cybersecurity? Information Related to the Research Questions 1. What definition do you think best describes: a. Cybercrime? b. Cybersecurity? 2. What cybercrime threats have you encountered working in the networking department at the University? 3. What recovery and preventive measures did you take afterward? 4. What measures do you take to safeguard your networks and databases from cybercrime? 5. What structural frameworks do you have in place in terms of cybersecurity? 6. How many times have you encountered internal cybercrime threats since you started working at the University? 7. How many times have you encountered external threats? 8. How did you manage these threats? 9. How much does the University generally spend on cybersecurity every year? 10. What areas do you think educational institutions need to improve on when it comes to cybersecurity? 11. What factors do you regard as being significant drivers of cybercrime in the society today? 12. What criteria would you use to assess the eligibility of a suspicious e-mail? 13. Do you think cybercrime is as significant an issue in higher learning institutions as the literature and media portray? 14. How do you protect your system and network from virus attacks? 15. How does your department protect itself from botnet attacks? 16. Do you have any measures in place to control the strength of users’ passwords within your network? 17. What factors do you think make it easy or difficult to crack someone’s password? 18. As the head of one of the nation’s most successful cybersecurity programs; what advice would you give to other universities whose run has not been as successful? |
The authors selected ABC University as the reference point for this chapter, owing to its high-standing reputation in cybersecurity.
The researchers conducted a review on XYZ University’s cybersecurity program. These materials were largely available online. The search criteria the authors used to identify relevant materials was “XYZ University cybersecurity program.” They compiled relevant materials from sites they deemed credible. The decision to use document review was driven by resource limitations that made it impossible for the researchers to visit both institutions for interviews.
In this chapter the authors adopted a qualitative approach for two fundamental reasons. First, qualitative approaches bring out the hidden meanings that people attach to events and experiences that they encounter in life (Bogdan & Biklen, 2003). Such techniques help to uncover the hidden meanings that individuals attach to phenomena and are thus preferred in studies that are of an exploratory nature. The open-ended nature of the research questions guiding this chapter supported the choice of qualitative techniques. According to Creswell and Creswell (2017), open-ended research questions begin with “what” or “how” and are best tackled using qualitative techniques that do not restrict respondents’ answers to specific predetermined categories.
Secondly, qualitative techniques allow for the extraction of thought processes and feelings that may not be uncovered using conventional approaches (Strauss & Corbin, 1998). This chapter sought to obtain the lived experiences and perceptions of university staff who are tasked with reducing the risk of cybercrime. Limiting questionnaires would not effectively bring out the participants’ perceptions and attitudes.
Research Instrument
The authors used qualitative case studies to gain an understanding of the phenomenon under investigation. They selected the two universities, namely the XYZ University and the ABC University, as case studies owing to their high-ranking reputations in the area of cybersecurity and based on their potential to contribute to the realization of the study objectives (Maxwell, 2005).
The interview guide in Table 1 was the primary data collection instrument for the chapter. The guide was composed of open-ended questions touching on the respondents’ demographic details and their experiences with cybercrime incidents and cybersecurity measures at the institution. The open-ended questions sought to give respondents the opportunity to give open responses to the interviewer’s questions (Merriam, 2002).
Sample Size
The sample consisted of two universities. The small sample size was informed by time constraints as well as resource limitations, which made it difficult to visit the data collection points. The small sample may not adequately represent the population of number of universities and colleges. All the same, it suffices because the chapter’s aim is not to make generalizations about the population, but to increase the audience’s understanding of the phenomenon under study.
Data Collection
The authors collected data through semistructured interviews and document reviews. Resource limitations impeded to physically conduct interviews in both universities. ABC University document used to obtain data from the XYZ University. The authors obtained the documents they reviewed from the universities’ databases and Web site.
Two reasons supported the authors to use interviews. First, interviews present an opportunity to understand what is in the respondents’ mind (Merriam, 2002). They help the researchers form an opinion from those things that they cannot observe. In this case, obtaining the interviewees’ hidden attitudes towards cybercrime was crucial, as it helped to build a case for which there is need to address this issue. Secondly, interviews allow for data triangulation–the verification of data obtained from other sources—and this increases the study’s credibility (Merriam, 2002).
For this chapter, the researchers interviewed only one participant, namely the ABC’s Network Support Department head. This could be identified as a key informant, given his knowledge and vast experience at the university, spanning over 10 years. The interview was conducted at the participant’s office within the university.
The participant allowed to audio-record the interview as a way of increasing accuracy during the transcription process (Merriam, 2002). In line with Merriam’s (2002) suggestions, it was keen to explain the aim of the research, the expected benefits, and the element of voluntary participation to the interviewee, at the very onset.
Data Analysis
The researchers used Creswell and Creswell’s (2017) six-step framework to analyze the gathered data. In the first step, they transcribed and stored electronically the data which were stored in the audio-recorder and the notes from the reviewed documents. The second step involved familiarizing with the data by reading through to obtain a general perspective of the ideas and opinions therein. In the third step, they organzed the data into categories based on similarities in the ideas being conveyed. They grouped together, in the same category in preparation for coding, sentences or paragraphs advancing the same idea. The fourth step consisted in assigning codes to these categories and using the assigned codes to identify consistent themes. The researchers organized the themes into a general description. In the fifth step, they put the themes together into a qualitative narrative, in such a way that the findings flowed in a logical sequence. The final step involved interpreting the data to make meaning and draw inferences. at the authors analyzed the data from a theoretical perspective, as Creswell and Creswell (2017) advised. Thus, the interpretation of the data was informed by the researchers’ understanding of the topic following the literature review that they had conducted in the early stages of the research.
Limitations and Delimitations
The main limitation of the study is that the authors were able to collect interview data, which was the main basis for the developed findings, only from a single departmental head and could not consider insight from other relevant personnel, such as junior network operators, who deal with cybercrime issues first-hand, on a daily basis. The departmental head’s role is more supervisory than practical, and there is the risk that the related findings may not be applicable to similar contexts. Secondly, since the data the researchers obtained from the interview were dependent primarily on the interviewee, the information may be limited to his or her own experiences and perceptions, which may be different from those of other personnel.
A core weakness of the study was its limited scope to only two case studies. It is not possible to speculate, therefore, that the findings would be similar to universities in other localities. Future studies could replicate this research with a larger sample size and more participants to see whether the findings would be consistent.
RQ1: What Is the Nature of Cybercrime in Higher Learning Institutions?
The study found hacking, phishing, and spoofing to be the most prevalent manifestations of cybercrime in higher learning institutions. Hacking is the unauthorized break-in into a protected network or system with the aim of installing malware, or destroying, changing or stealing information (EC-Council, 2016). Hackers are skilled and knowledgeable about operating systems and can gain access to their target system in several ways, including using password crackers, network sniffers, through virus dissemination, and social engineering. Password cracking involves using brainstorming (brute force) or password dictionaries to identify unknown passwords, and thereby gain unauthorized access to an institution’s database.
Also, commonplace is the strategy of disseminating a virus, usually Trojan Horse, to the target computer network. Trojan Horse works by recording all of the victim’s keystrokes on his/her computer, network or database. Through Trojan, a hacker illegally obtains and records crucial information about the victim, including his/her credit card numbers and account passwords. Hacking through social engineering also came out as a common manifestation of cybercrime in educational institutions. This form involves contacting unsuspecting employees within the institution and tricking them to divulge crucial information. Finally, hackers can make use of packet sniffers, which allow for the interception of logging traffic as it moves across the network.
Phishing is another way through which cybercrime is manifested in higher learning institutes. It involves using e-mail to trick one’s victim to provide his/her personal details. The spoofing technique is also common. In this case, the attacker imitates one of his/her clients’ e-mail headers to make them believe that it came from a different person and duping them to provide sensitive. Many phishing incidents have been reported, so the significance of user awareness, technical measurements, laws, and legislation has been portrayed in governments (Al-Alawi, 2014; Al-Alawi et al., 2016).
Other cybercrime acts, such as cyber defamation, cyberstalking, cyber defamation, cyber identity theft, software piracy, and credit card fraud, though common in the case of the general population, are not common in learning institutions. Administrators and institution heads need to target their cybersecurity efforts towards those forms of cybercrime that are relevant to learning institutions. Targeted approaches are deemed to work more effectively than umbrella cybersecurity solutions.
RQ2: What Cybersecurity Measures Can Institutions Put in Place to Reduce Their Exposure to Cybercrime?
The two institutions the authors investigated in this study propose the best practice of targeting different forms of cybercrime uniquely, rather than devising an umbrella solution without first understanding which of the various forms of cybercrime are prevalent in one’s institution. In order to safeguard their networks against hacking, institutions can take several measures. First, they could adopt the use of Syskey, which is a feature on Windows that provide encryption to a field. Syskey secures data stored in files, making it impossible for attackers to copy the information therein.
The researchers found ABC University offers its staff training opportunities on password development and maintenance. Other institutions could take up this strategy. In order to make users’ passwords more secure, the ABC required all its network users to have passwords that incorporate the letters of the alphabet (both uppercase and lowercase), special symbols, and numbers. Moreover, passwords need to be kept fairly long changed regularly, and must not be constructed using the subject’s identifying elements, such as their age, names, or telephone numbers.
In order to minimize the effect of viruses and dangerous malware, both the ABC and XYZ Universities offer regular trainings to students and staff on how to enable firewalls and other security measures, and how to verify the safety of Web sites before downloading files using software. Staff and students also receive regular trainings on how to detect cyber-attacks through common indicators, such as digital signature and malicious Web sites. The institutions further implement conveniently designed reporting mechanisms, in addition to educating individual members on how to use proxy servers and intrusion detection systems to block IP addresses that look suspicious.
Institutions need to put up effective structural mechanisms for dealing with cybercrime threats. However, this alone is not sufficient. Equal importance needs to be placed on the aspect of training and continuous education to ensure that members remain up-to-date in the wake of changing threats.
CONCLUSION AND RECOMMENDATIONS
As the popularity and usage of the Internet increases, the risk of cybercrime also rises. Some of the world’s greatest companies have found themselves falling prey to cybercrime and losing millions in recovery costs. One area that has suffered greatly as a consequence of the increasing prominence of cybercrime is that of higher education. Higher education institutions have been victims of cybercrime and continue to be attractive targets, owing to the large quantities of research and personal data they handle. Despite this, the area of cybercrime in these institutions remains severely understudied. This study sought to identify the ways in which cybercrime manifests itself in higher learning institutions and specific cybersecurity strategies that institutions could use to counter it. Guided by the literature review and findings from the two case studies, the authors make the following recommendations:
Al-Alawi, A. I. (2014). Cybercrimes, computer forensics, and their impact on business climate: Bahrain status. Journal of Business and Management , 8(3), 139–156.
Al-Alawi, A. I., & Abdelgadir, M. (2006). An empirical study of attitudes and opinions of computer crimes: A comparative study between U.K. and the Kingdom of Bahrain. Journal of Computational Science , 2(3), 229–235. doi:10.3844/jcssp.2006.229.235
Al-Alawi, A. I., Al-Kandari, S. M. H., & Abdel-Razek, R. H. (2016). Evaluation of information systems security awareness in higher education: An empirical study of Kuwait University. Journal of Innovation & Business Best Practice . doi:doi:10.5171/2016.329374
Al-Alawi, A. I., & Hafedh, E. A. (2006). Auditing of information privacy. Journal of Information Technology , 5(1), 177–182. doi:10.3923/itj.2006.177.182
Ang, R. P., & Goh, D. H. (2010). Cyberbullying among adolescents: The role of affective and cognitive empathy, and gender. Child Psychiatry and Human Development , 41(4), 387–397. doi:10.1007/s10578-010-0176-3
Bogdan, R. C., & Biklen, S. K. (2003). Qualitative research for education: An introduction to theories and management (4th ed.). New York, NY: Pearson Education Group.
Broadhurst, R., Grabsoky, P., Alazab, M., & Chon, S. (2014). Organizations and cybercrime: An analysis of the nature of groups engaged in cybercrime. International Journal of Cyber Criminology , 8(1), 1–20.
Chapman, J. (2019, April 4). How safe is your data? Cyber-security in higher education. Retrieved from https://www.hepi.ac.uk/2019/04/04/how-safe-is-your-data-cyber-security-in-higher-education/
Cresey, D. R. (1954). Differential association theory and compulsive crimes. Journal of Criminal Law and Criminology , 45(1), 29–40. doi:10.2307/1139301
Creswell, J. W., & Creswell, J. D. (2017). Research design: Qualitative, quantitative, and mixed methods approach . Los Angeles, CA: Sage Publications.
Dashora, K. (2011). Cybercrime in the society: Problems and prevention. Journal of Alternative Perspectives in the Social Sciences , 3(1), 24–59.
den Hamer, A. H., & Konijn, E. A. (2015). Adolescents’ media exposure may increase their cyberbullying behavior: A longitudinal study. The Journal of Adolescent Health , 56(2), 203–208. doi:10.1016/j.jadohealth.2014.09.016
EC-Council. (2016). Computer forensics. Investigating file and operating systems: Wireless network and storage (CHFI) . Boston, MA: Cengage Learning.
Fellows, L. (2019, May 31). A daily threat – Universities, cyber-attacks and national security in the UK. Retrieved from https://blogs.vmware.com/emea/en/2019/05/a-daily-threat-universities-cyber-attacks-and-national-security-in-the-uk/
Gearhart, G. D., Abbiatti, M. D., & Miller, M. T. (2019). Higher education’s cyber security: Leadership issues, challenges and the future. International Journal on New Trends in Education & Their Implications, 10(2), 11-16.
Goodman, M. (2015). Future crimes: Everything is connected, everyone is vulnerable and what we can do about it (1st ed.). New York: Anchor, Penguin Random House LLC.
Harris, C. E., & Lammargren, R. (2016). Higher education vulnerability to cyber-attacks. University Business. Retrieved from https://universitybusiness.com/higher-educations-vulnerability-to-cyber-attacks/
Holt, T. J., Strumsky, D., Smirnova, O., & Kilger, M. (2012). Examining the social networks of malware writers and hackers. International Journal of Cyber Criminology , 6(1), 891.
Kshetri, N. (2010). The global cybercrime industry . Berlin: Springer. doi:10.1007/978-3-642-11522-6
Loundy, D. J. (2003). Computer crime, information warfare & economic espionage . Durham, NC: Carolina Academic Press.
Maxwell, J. A. (2005). Qualitative research design: An interactive approach . Thousand Oaks, CA: Sage.
Merriam, S. B. (2002). Qualitative research in practice: Examples for discussion and analysis . San Francisco, CA: Josey-Bass.
Oh, S., & Lee, K. (2014). The need for specific penalties for hacking in criminal law. The Scientific World Journal , 16(1), 73–78.
Okeshola, F. B., & Adeta, A. K. (2013). The nature, causes and cons of cybercrime in tertiary institutions in Zaria-Danuna, Nigeria. American International Journal of Contemporary Research , 3(9), 98–114.
Ponemon Institute. (2015, May 23). 2015 cost of data breach study: Global analysis. Ponemon Institute Research Report. Retrieved from http://public.dhe.ibm.com/common/ssi/ecm/se/en/sew03053wwen/SEW03053W WEN.PDF
Press Association. (2019, July 23). Lancaster University students’ data stolen in cyber-attack. The Guardian. Retrieved from https://www.theguardian.com/technology/2019/jul/23/lancaster-university-students-data-stolen-cyber-attack
Raman, A., Kabir, F., Hejazi, S., & Aggarwal, K. (2016, August 25). Cybersecurity in higher education: The changing threat landscape. Retrieved from https://consulting.ey.com/cybersecurity-in-higher-education-the-changing-threat-landscape/
Schneider, S. K., O’donnell, L., Stueve, A., & Coulter, R. W. (2012). Cyberbullying, school bullying, and psychological distress: A regional census of high school students. American Journal of Public Health , 102(1), 171–177. doi:10.2105/AJPH.2011.300308
Snail, S. (2009). Cybercrime in South Africa – Hacking, crack, and other unlawful online activities. Journal of Information . Law and Technology , 10(1), 1–13.
Storm, D. (2017, February 15). Hacker breached 63 universities and government agencies. Retrieved from https://www.computerworld.com/article/3170724/hacker-breached-63-universities-and-government-agencies.html
Strauss, A., & Corbin, J. (1998). Basics of qualitative research: Techniques and procedures for developing grounded theory (2nd ed.). Thousand Oaks, CA: Academic Press.
Vijayan, V., Joy, J. P., & Suchithra, M. S. (2014). A review on password cracking strategies. International Journal of Research in Computer and Communication Technology , 1(1), 8–15.
Whitman, M. E., & Mattors, H. J. (2010). Readings and cases in information security: Law & ethics . Boston, MA: Cengage Learning.
Wilson, C. (2008). Botnets, cybercrime, and cyberterrorism: Vulnerabilities and policy issues for Congress . Washington, DC: Congressional Research Service, the Library of Congress. Retrieved from https://apps.dtic.mil/dtic/tr/fulltext/u2/a477642.pdf
Yale University revealed a data breach which happened a decade ago. (2018, August 5). Retrieved from https://securereading.com/yale-university-revealed-a-data-breach-which-happened-a-decade-ago/