15 The foundationalist debate in computer ethics
15.1 Introduction
There are issues that are more abstract and basic than the substantive issues with which most information ethics theorizing is concerned. These issues are thought to be ‘foundational’ in the sense that we cannot fully succeed in giving an analysis of the concrete problems of information ethics (e.g. are legal intellectual property rights justifiably protected?) until these issues are adequately addressed.(K. E. Himma 2007a, p. 79)
Himma proposes one rationale for why foundational issues in information and computer ethics1 warrant philosophical analysis. Independently of whether his provocative claim can be substantiated, however, we will see
that there are many compelling reasons for examining foundational issues in computer ethics (CE). We will also see that various
models for understanding CE's foundational issues have been proposed and continue to be debated.
This chapter begins with a brief analysis of a model defended by Floridi and Sanders (2002) for examining foundational issues in CE via five ‘approaches’. Next, we propose an alternative model, which frames CE's
foundationalist debate in terms of three principal questions. The remaining sections analyse these questions in detail. In
proposing answers to each question, the chapter incorporates some insights from CE's leading theorists.
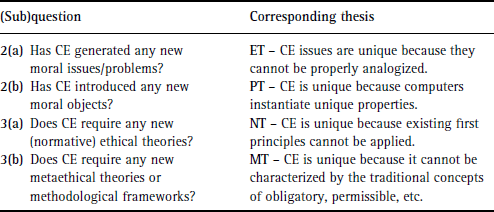
15.2 The Floridi/Sanders model
According to Floridi and Sanders (2002, p. 2), the foundationalist debate can be viewed as ‘a metatheoretical reflection on the nature and justification of CE and
the discussion of CE's relationship to the broader context of metaethical theories’. The authors examine various conceptions
of CE that have evolved from a ‘random collection of heterogeneous computer-related ethical issues’ to a discipline that is
now more ‘coherent and cohesive’. Floridi and Sanders articulate five distinct ‘approaches’ that have emerged in the evolution
of CE as a field of applied ethics (see Table 15.1): the No-Resolution Approach (NA), Professional Approach (PA), Radical Approach (RA), Conservative Approach (CA) and Innovative
Approach (IA).
In the NA approach, CE problems are seen as presenting us with ‘unsolvable dilemmas’ and thus are a ‘pointless exercise [with]
no foundation’ (Floridi and Sanders, p. 2). However, the authors also point out that even though NA provides only a ‘minimalist
starting point’, it is ‘useful’ because it prompts the other four approaches, and it sensitizes people both to the fact that computer technology has social and ethical consequences and to the kinds of ethical issues that arise from the use of computer technology.
PA stresses professional-responsibility issues affecting the development of computing technology. It has been defended by
Gotterbarn (1995) and others (e.g., Buchanan 2004). Floridi and Sanders (p. 3) describe PA as a ‘pedagogical methodology’ that has been used in the instruction of computer
science professionals, including software engineers. According to Gotterbarn, PA introduces computer science students to the
‘responsibilities of their profession’ and to the ‘standards and methods used to resolve non-technical questions about their
profession’. Floridi and Sanders note that PA takes seriously issues such as technical standards and requirements for professional
guidelines, and thus stresses the vital importance of CE-education. A significant disadvantage of PA, however, is that its
exclusive focus of professional-responsibility concerns provides us with a very narrow conception of CE as a field of applied
ethics (Tavani 2007, 2010).
Both NA and PA can be construed as non-theoretical, or pre-theoretical, approaches in that they do not directly engage ethical
theory in their analyses of CE issues. As such, they can be contrasted with the RA and CA approaches. Whereas RA stresses
the novelty of CE's issues, suggesting that new ethical categories are needed, CA assumes that issues in CE can be handled
by conventional ethical categories. Some proponents of RA, such as Maner (1996) and Barger (2008), claim that the use of computer technology has introduced new ethical issues or dilemmas, unique to computing. Advocates
of CA, on the contrary, reject the view that CE has any new or unique features, even though some CE issues may initially seem
to pose a challenge for ‘ordinary ethics’. Johnson (2009) has defended a version of CA via an evolutionary metaphor
Table 15.1 The Floridi/Sanders model for analysing foundational issues in CE.
(involving genus and species) in which ethical issues raised by computer technology are understood as ‘new species’ of (existing)
generic moral problems. In this scheme, CE issues can be viewed as old (traditional) ethical problems, but with a new variation
or new twist.
Floridi and Sanders defend a scheme called IA, as a mid-way position between CA and RA. IA is based on a macroethical framework
that Floridi (1999b) calls Information Ethics (IE). Floridi and Sanders argue that IE is neither conservative nor radical, but rather ‘innovative’.
We will analyse IE in detail in Sections 15.5.2 and 15.6.2. The CA and RA positions are examined in Sections 15.5.1 and 15.6.1, while PA is briefly considered in Section 15.4. NA, however, will not be further examined because it is not essential to our analysis of the foundationalist debate.
Table 15.1 summarizes the five approaches in the Floridi/Sanders model, which inform our analysis of foundational issues in CE in the
remaining sections of this chapter.
15.3 An alternative model for analysing the foundationalist debate
Whereas Floridi and Sanders frame CE's foundationalist debate in terms of the five ‘approaches’, identified above, the same
debate may be analysed via three distinct, but related, questions:
Although each question is conceptually distinct, and thus deserves to be analysed independently, aspects of the three questions
also intersect at some points or overlap at others. For example, an adequate answer to (1) may depend on answers to (2) or
(3), or both. And (3) is significant if the answer to (2) is ‘yes’. Questions 2 and 3 are each further subdivided into two
sub-questions affecting the debate about foundational issues in CE. Questions 2(a) and 2(b) are analysed in Section 15.5, while Questions 3(a) and 3(b) are examined in Section 15.6. First, however, we consider Question 1.
(1) Is CE a legitimate field of applied ethics that warrants philosophical consideration?
(2) Are any aspects of CE new or unique in a philosophically interesting sense?
(a) Have any new ethical issues or problems been generated?
(b) Have any new ethical objects been introduced?
(3) Does CE require a new ethical framework?
(a) Are any new normative ethical theories required?
(b) Are any new meta ethical theories or methodological frameworks required?
15.4 Is CE a legitimate field of applied ethics that warrants philosophical analysis?
As already noted, some have questioned the legitimacy of CE as an independent field of applied ethics worthy of philosophical
consideration. For example, Floridi (1999b) has suggested that CE's legitimacy as a philosophical field is threatened because it lacks an appropriate ‘methodological
foundation’. Others argue that CE should be conceived of simply as a branch, or sub-field, of professional ethics. According
to PA, for example, CE can be understood as a sub-field of computer science concerned with identifying and analysing issues of
ethical responsibility for computer professionals. PA's supporters draw some comparisons between the computer profession and
other professional fields, such as medicine and law. They point out that in medical ethics and legal ethics, the principal
focus of analysis has been on issues of moral responsibility that affect individuals as members of those professions. Continuing
with this analogy, some proponents of PA support the view that the principal, and perhaps even the sole, focus of CE should
be on issues of professional responsibility for computer-science and software-engineering professionals.
Defending the view that CE can best be understood as a branch of professional ethics (for the computing profession), Gotterbarn
(1995) claims that many issues associated with CE are not really computer-ethics issues at all. He argues that computer-assisted
crimes (that have captured the popular media's attention) should not be viewed as issues in CE, just as a crime involving
a murder committed with a surgeon's scalpel should not be thought of as an issue in medical ethics. In the same way that medical ethics examines issues in the medical profession that are relevant for medical
professionals, so too can CE be understood as a field that examines ethical issues that affect computer professionals.
Gotterbarn uses some instructive analogies to defend his version of PA. For example, he notes that, historically, the introduction
of some technologies profoundly affected our daily lives. In particular, he mentions the printing press, the automobile and
the airplane. He points out that each has had a significant, and arguably ‘revolutionary’, effect on our social institutions.
But Gotterbarn also notes that we do not have categories such as ‘printing press ethics’, ‘automobile ethics’ or ‘airplane
ethics’. So, he asks why we need a field of computer ethics that is independent of a sub-field of computer science or professional
ethics to examine issues in CE-proper, which are limited to ethical issues that affect the professionals responsible for the
design, development and maintenance of computer systems. In other words, he questions the legitimacy of CE as something more
than an area (of computer science) that examines ethical issues that affect computer professionals.
One might argue that, in the era of computing prior to the Web, the view of CE as mainly a field of professional ethics was
plausible. During that period, a proportionately high number of computer users were also computer professionals; in fact,
in the early days of computing, the majority of computer users may indeed have been computer professionals. But that phenomenon
changed significantly with the advent of the personal computer in the early 1980s and especially with the widespread use of
the Internet in the early 1990s. Because the number of ordinary computer users now far exceeds the number of users who are
computer professionals, one might easily infer that, today, PA would seem to be a less plausible position than it might have
been at one time (Tavani 2007, 2010).
If our critique of PA is correct, a different answer is needed for a positive response to the question posed at the beginning
of this section: Is CE a legitimate field of applied ethics that warrants philosophical consideration? An insightful answer
has been proposed by Moor (1985, p. 266) who describes CE as
the analysis of the nature and social impact of computer technology and the corresponding formulation and justification of policies for the ethical use of such technology.
First, we should note that Moor's definition goes beyond, but does not exclude, the principal claim of PA that CE must address
ethical issues affecting computer professionals. His conception of CE as an academic discipline is much broader in scope than
Gotterbarn's, and this difference is apparent in Moor's arguments for why CE is justified as an independent field of applied
ethics. Moor argues that, because computer technology is ‘logically malleable’, it allows for new kinds of actions that were not previously possible. These actions sometimes stretch
and strain our legal and ethical norms and introduce what Moor calls ‘policy vacuums’. Before these vacuums or voids can be filled with either revised or new policies, we sometimes need to clarify
one or more ‘conceptual muddles’ that can also arise (Moor, pp. 266–267). In Moor's view, one justification for continued research in
CE as a separate field has to do with the number and kinds of policy vacuums that arise.
Others suggest that CE is justified as an academic field or discipline because it has some ‘unique’ aspects or dilemmas. For example, Maner (1996), whose arguments are examined in Section 15.5.1, claims that CE ‘must exist as a field of study worthy of existence in its own right’ because it has unique aspects. And
Barger (2008, p. 14) argues that the ‘nature of the computer and its operation gives certain dilemmas in computing a difference in degree
that approximates a difference in kind and that certainly makes computer ethics a unique field of study’. Himma (2003) describes these views of CE as examples of the ‘disciplinary thesis’, and he questions the alleged logical relationship
between the justification of CE as a discipline and the requirement that CE has some unique aspects. According to the disciplinary
thesis,
ethical problems arising in connection with computer technologies represent a class that is indistinguishable in principle from other areas of applied ethics and should be studied by applied ethicists specializing in such problems.(Himma, p. 234)
In this view, CE is a legitimate field if and only if CE either (a) has some unique issues or dilemmas, or (b) requires a
unique ethical theory. Himma rejects the view that such a logical relationship is required, arguing that CE could be justified
as a distinct field of applied ethics independently of either (a) or (b). In doing this, he draws some comparisons between
medical ethics and computer ethics, and he shows that just as the former field of applied ethics needs no unique ethical issues
or new ethical theories to justify its philosophical worthiness as a distinct field of applied ethics, neither does the latter.
Unlike Gotterbarn, however, Himma does not draw on professional-related ethical issues in his analogies involving medical
ethics and computer ethics. Instead, Himma notes that just as some medical technologies, such as those affecting reproduction
and cloning, have helped to define parameters of the field of medical ethics, so too have issues affecting computing technology
itself contributed to the cluster of issues examined in CE. Thus, there is no compelling reason to believe that any unique
ethical issues affecting computing technology are required to justify CE as a legitimate discipline. Like Himma, the present
author (Tavani 2002, 2007, 2010) has also argued that the legitimacy of CE as an independent field of applied ethics is not contingent on the existence of
any unique issues, properties, etc. (even if it turns out that such issues, properties, etc. are generated in CE).
We next consider the second of the three questions in our model for analysing foundational issues in CE.
15.5 Are any aspects of CE new or unique in a philosophically interesting sense?
As already noted, proponents of RA have argued that CE has some unique aspects, e.g., unique issues or dilemmas, unique attributes
or properties, and so forth. Henceforth, we refer to the claim that computer ethics is unique (in some sense) as the CEIU thesis (Tavani 2002). In our examination of the arguments for and against this thesis, we will see that those who defend CA tend to reject CEIU,
arguing that claims about the uniqueness of CE have been vastly overstated. RA's defenders, on the contrary, tend to embrace
one or more elements of the CEIU thesis. For example, some suggest that CE is unique because it generates new ethical issues,
while others claim that CE has some features that distinguish it from other fields of applied ethics.
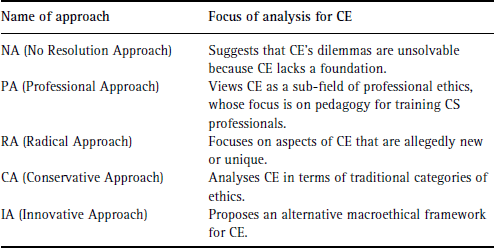
Himma (2007a) argues that claims inherent in CEIU can be analysed in terms of four distinct ‘theses’, which he calls the Meta-ethical Thesis, the Normative-ethical Thesis, the Epistemological Thesis and the Properties Thesis. We will refer to
these positions as MT, NT, ET and PT, respectively.
According to MT, ‘there are acts in computer ethics that cannot adequately be characterized by the traditional metaethical
concepts of obligatory, permissible, good, and supererogatory’. In the NT view, ‘computer technologies present ethical problems
that cannot, as an objective matter, be adequately resolved by recourse to existing normative-ethical first-principles’. According
to ET, ‘computer technologies present ethical problems that resist the analogies that enable us to see how ethical theories
and first-principles apply in other fields of applied ethics’. PT has two variations: a ‘strong’ properties thesis, and a
‘weak’ one. In the latter variation, computers ‘instantiate ethically significant properties’ (including the possibility of
‘moral personhood’), whereas the strong view asserts that computers instantiate ethically significant properties that are
not instantiated by any other ‘thing or being in the universe’ (Himma, p. 80). We limit our discussion of PT to the view that
Himma describes as the weak thesis. Himma's analysis of CEIU via the four theses informs our analysis of the foundationalist
debate in the remaining sections of this chapter. Whereas aspects of ET and PT are examined in Sections 15.5.1 and 15.5.2, MT and NT are considered in 15.6.1 and 15.6.2. Table 15.2 summarizes Himma's model.
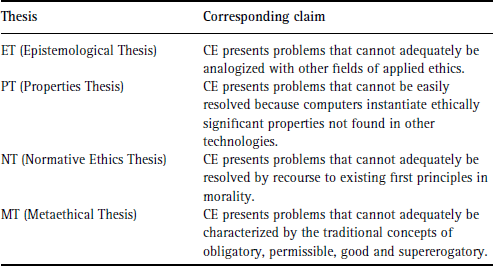
We next analyse the two components of Question 2: (a) Has computing technology generated any new moral issues/problems? (b)
Has computing technology introduced any new moral entities/objects? These correspond to issues affecting ET and PT, respectively.
We begin with an analysis of Question 2(a).
Table 15.2 Himma's model for analysing CEIU via four theses.
15.5.1 Have any new ethical issues or problems been generated?
An issue/problem in applied ethics can be viewed as a controversial topic that warrants ethical analysis. Among the topical
areas associated with controversies affecting computing technology are (general) categories such as security, anonymity, privacy,
property, access and so forth. In this scheme, concerns affecting ‘personal privacy’ would be an example of a typical issue in CE that is also fairly general in scope – privacy concerns raise
ethical issues because they typically involve one or more fundamental or core moral notions such as autonomy, fairness, justice and
so forth. At a more specific level, privacy threats affecting spyware, cookies or RFID technologies are examples of some ‘particular ethical issues’ associated with privacy and computing technology.
Maner (1996) argues that computer technology has generated some moral issues that did not exist before the advent of computing technology
and that could not have existed if computers had never been invented. It is unclear, however, which (specific) ethical issues
he has in mind. If Maner meant that some new issues qua topical areas (in general) have been generated, it would have been helpful if he had explicitly identified them: but he has not done this.
So perhaps he meant something less controversial – viz., that some new instances of existing moral issues (e.g. under traditional
classificatory schemes such as personal privacy or intellectual property) have been introduced. In one sense ethical issues
affecting RFID privacy or software piracy would have been impossible if computer technology had never been developed. Yet,
this is true only in a trivial sense. The (general) underlying concerns of both issues – i.e., surveillance involving the
unauthorized collection of personal information, and theft involving the unauthorized copying of proprietary information – existed long before the introduction of computing
technology (Tavani 2007). If all that Maner meant was that new variations of (traditional) moral problems have been generated, one could reasonably
ask whether his position differs in any significant respect from claims made by some who embrace CA, such as Johnson (2009), as opposed to those who defend the more radical claims in RA about CE's alleged uniqueness.
A second interpretation of what Maner meant is that computer technology possesses some unique features or ‘properties’ that
are ethically relevant. For example, he points out that computers are ‘uniquely malleable’, ‘uniquely complex’, ‘uniquely
fast’ and ‘uniquely coded’. In focusing on the unique attributes or properties of computers, Maner can be interpreted as holding
a variation of Himma's properties thesis (PT) regarding CEIU. However, one may wonder whether Maner's claim, so interpreted, entails the more controversial
claim that computers have generated new ethical issues (qua topical areas or qua specific instances of topical areas). Although
technological features, such as malleability, might indeed be unique to computer technology, it does not follow that any unique
ethical issues have emerged because of this technology's malleability. Proponents of CEIU, who argue that CE issues must be unique because certain features or aspects
of computing technology are unique, commit the ‘computer-ethics-is-unique fallacy’ (Tavani 2007, 2010): computer technology has some unique technological features; the use of computer technology has generated ethical concerns;
therefore, such ethical concerns must be unique. This line of reasoning is fallacious because it mistakenly assumes that characteristics that apply to a certain technology
must also be inherited by the ethical issues associated with it.
A third, and final, interpretation of what Maner intended in his defence of CEIU can be found in his remarks about the lack
of an ‘effective analogy’ for understanding CE issues. There, he claims that our inability to find ‘satisfactory non-computer
analogies’ for moral issues involving computers ‘testifies to the uniqueness of computer ethics’. This claim would seem to
correspond to the view expressed in Himma's epistemological thesis (ET) – i.e., the interpretation of CEIU stating that ethical problems generated by computers resist
analogies with ethical problems handled by standard ethical categories and theories. But a claim about the lack of an effective
analogy for understanding CE issues is a very different sort of claim from one asserting that CE has introduced new ethical
issues that are also unique to computers. Also, we can ask why these analogies with ordinary ethics are unsatisfactory (even
if computer technology has properties that are vastly different from those found in other kinds of earlier technologies).
Unfortunately, Maner does not elaborate on why a lack of effective analogies with other technologies entails that CE issues
are unique. So, it would seem that, when Maner's claims about the uniqueness of CE are examined from the perspective of ET,
they fail to support CEIU.
If the CEIU thesis cannot be defended, does it follow that there is nothing special about CE or that CE does not merit the
attention of philosophers and ethicists? Moor (1998) points out that CE raises some concerns that fall outside the scope of ‘routine ethics’. It is important to note, however,
that Moor does not claim that CE issues are unique ethical issues, even though he argues that computer technology has been
used in ways that raise special ethical problems. Recall Moor's claims affecting the logical malleability of computer technology and the kinds of policy vacuums and conceptual muddles that result because of
the malleable nature of that technology. Moor (1985) also argues that the use of computers has generated ‘new possibilities for human action’, which, in turn, raise ethical
concerns. In determining whether these new possibilities for human action, made possible by computing technology, have also
introduced any new objects that deserve moral consideration, we turn to Question 2(b).
15.5.2 Have any new ethical objects been introduced?
Jonas (1984) argued that ‘modern technology’ – though he does not specifically mention computer technology – has made possible certain
kinds of actions which, in turn, have disclosed ‘new objects of ethical consideration’. According to Jonas, our traditional
scheme of ethics is no longer adequate in the era of modern technology because the nature of human action has changed in fundamental
ways and this requires a change in ethics in which ‘new objects’ must be added. Prior to the twentieth century, most philosophers
and moral theorists, at least in the West, assumed that the sphere of ethical consideration applied only to human beings.
That view was eventually challenged by animal rights proponents, who argued that animals deserved moral consideration (because they are sentient beings), and by
some environmentalists who believed that ethical consideration should also be extended to trees and plant life (because they are
biological life forms). However, Jonas argued that the sphere of moral consideration needed to be expanded further to include
additional ‘objects’, such as future generations of human beings as well as (the whole of) nature itself.
Floridi (1999b) argues that we need to extend the domain of moral consideration beyond the boundaries proposed by Jonas, because non-biological
or inanimate objects can also have moral status and thus must be granted consideration. According to Floridi (2008e, pp. 10–11), all entities in the Universe can be viewed as ‘clusters of data’, which he calls ‘informational objects’. Floridi
defines these ‘objects’ as ‘encapsulated packages’ that are ‘discrete’ and ‘self contained’. To understand why these objects
warrant moral consideration, we need to analyse some key components of Floridi's Information Ethics (IE) framework, which
he describes as a ‘patient-oriented, ontocentric, ecological macroethics’. IE is a macroethics (as opposed to a microethics), Floridi argues, because it is like utilitarianism, Kantianism, and other standard theories
of ethics in terms of their breadth of application. But he also shows why it is different from those conventional macroethical
theories, which Floridi claims to be either anthropocentric or biocentric. Whereas utilitarian and deontological (macroethical)
theories have tended to be anthropocentric (focusing on ways that human actions affect other humans), environmental and ecological
macroethical theories are life-centred or biocentric (taking into consideration the interests of life forms in addition to
humans). Like the ecological (macroethical) theory, IE avoids anthropocentrism; but IE goes one step further by replacing
biocentrism with ‘ontocentrism’.
According to IE, there is something more elemental than life – viz., being (i.e., what Floridi (p. 12) describes as the existence and flourishing of all entities and their global environment). And
there is something more fundamental than suffering, viz., a condition that Floridi describes as ‘entropy’. It is important to note, however, that Floridi's notion of entropy is not the same as the physicist's concept of
thermodynamic entropy. For Floridi, entropy refers to ‘any kind of disruption, corruption, pollution, and depletion of informational
objects’ which could result in any ‘impoverishment of being’. IE is concerned with the well-being of the infosphere and the ‘evil’ (i.e., the harm) that can be suffered by objects in the infosphere. So, IE shifts the emphasis away
from traditional concerns affecting only the well-being of humans, and in some cases only the well-being of biological life forms, to concerns about the well-being of the whole infosphere (and the informational
objects that comprise it, including humans and biological life forms as well).
Although Floridi argues that all entities, qua informational objects, have intrinsic moral value, he also notes that the moral
value of informational objects can be ‘quite unusual’ and that it is ‘overridable’. But informational objects are nonetheless
moral patients that are owed at least some ‘minimal degree of moral respect’. Floridi (p. 12) also holds that duties owed to informational objects (as moral patients)
by moral agents are evaluated either (i) ‘positively’, if an agent's actions contribute to the growth of the infosphere or
(ii) ‘negatively’, if an agent's actions adversely impact the infosphere (i.e., through the depletion of informational objects,
the degradation of information and informational resources, and so forth).
Floridi draws some important distinctions between moral patients and moral agents. In IE, both the infosphere and the informational objects that comprise it are moral patients
that (a) need to be recognized as being at ‘the centre of some basic ethical claims’ and (b) are owed some respect by moral
agents. As Floridi (p. 17) puts the matter, an agent's
decisions and actions should always be based on how the latter affects the well-being of the infosphere, that is, on how successful or unsuccessful they areTable 15.3 Four (sub)questions corresponding to Himma's four CEIU theses.in respecting the ethical claims attributable to information entities involved, and hence in improving or impoverishing the infosphere.
In this sense, IE suggests an ‘ontological shift’ in our thinking about the kinds of objects that can qualify for moral consideration
and about the kinds of obligations that are owed to these objects qua moral patients by (human and non-human) moral agents.
Thus far, we have only briefly described some of the duties that moral agents have in preserving the well-being of the infosphere.
In Section 15.6.2, we examine the concept of moral agency in more detail. We conclude Section 15.5 by summarizing some key points in our analysis of two interpretations of CEIU. First, we saw that there were no compelling
reasons to believe that CE has generated any unique or new ethical issues. Next, we saw that, if IE is correct, a ‘new’ category
of objects (viz., informational objects) deserve at least some moral consideration. But it is also important to note that
IE does not claim that these objects either (i) have been introduced solely because of computer technology, or (ii) deserve
moral consideration because they have some properties that are unique to computers.
Next, we turn our attention to the final question in our analysis of the foundationalist debate, Question 3, which also has
two component parts. Whereas Question 3(a) asks whether a new (normative) ethical theory is needed for CE, Question 3(b) inquires
into whether a new metaethical theory or a new methodological framework is needed. Both questions, as in the case of Questions
2(a) and 2(b), overlap with two of Himma's four ‘theses’ underlying CEIU (summarized above in Table 15.2). Table 15.3 describes the corresponding relationships that obtain between Questions 2(a) through 3(b) and Himma's four theses.
15.6 Does CE require a new ethical framework?
In answering this question, it is helpful to understand some of the claims that may be labelled as ‘traditionalist’ and ‘expansionist’
(Tavani 2005). Whereas the traditionalist position corresponds closely to Floridi and Sander's notion of CA, the expansionist position
is similar to their category of RA. Traditionalists answer ‘no’ to Question 3 because they believe that our existing framework
of ethics, including our standard concepts and theories, is adequate to analyse CE issues. Among those who defend the traditionalist
view are Johnson (1994) and Gert (1999). Although Johnson views CE issues as a ‘new species of existing moral problems’, she also claims that ‘ordinary ethics’
is sufficient to handle these issues. Gert, who also believes that no new theory is needed, offers a different kind of rationale.
Unlike Johnson and others, who embrace traditional ethical theories such as utilitarianism, Kantianism and so forth, Gert
argues that his own system of ‘common morality’ is superior. He then shows how his system can be successfully applied to ethical
issues in computing by examining the question whether it is permissible to copy proprietary software, and concludes that no
new or special ethical theories are required to analyse issues in CE. Unfortunately, an examination of Gert's rich and interesting
moral system, in the detail that it deserves, is beyond the scope of this chapter. The purpose in mentioning his theory, as
well as the traditionalist's position in general, is to draw a contrast with the expansionist's claim that a new ethical framework
is required.
We next examine some specific claims that expansionists have put forth with respect to Question 3(a).
15.6.1 Are any new normative ethical theories required?
Expansionists such as Adam (2005) and Górniak-Kocikowska (1996) claim that we need a new ethical theory to understand and resolve issues in CE. It is important to point out that neither
Adam nor Górniak-Kocikowska argue that a new theory is needed because CE has any unique features or issues. It is also worth noting that they provide two very different accounts of the kind of
ethical theory that is needed, as well as very different kinds of answers to the question of why a new theory is needed.
Adam argues that conventional ethical theories, such as utilitarianism and deontology, are insufficient for analysing CE issues
because they have either ignored or greatly underestimated the importance of gender in CE. This, in turn, has resulted in gender issues being ‘under-theorized’ in CE research. Arguing that a gender-based
ethical theory is needed to remedy this problem, she puts forth a theory that is based on a feminist ethics – in particular,
on the ‘ethic of care’. Adam then offers some reasons why an ethic of care can improve our understanding of gender issues affecting CE. For one thing, she claims that it helps us better understand ethical
concerns and controversies affecting power and privacy. With regard to the former, a gender-informed framework enables us
to see some of the relations of power that are involved in the development and use of computers. Regarding the latter topic,
she holds that her theory can help us to see that the concept of privacy can be different for men and women. As a result,
Adam argues that a gender-informed theory can help us to understand CE issues involving cyberstalking and Internet pornography
in ways that the standard ethical theories cannot.
Even if we accept Adam's arguments for why the standard ethical theories used in CE are inadequate, it is still unclear why
the gender-informed theory she articulates is peculiar to issues affecting computing per se, as opposed to broader areas of
applied ethics that also are affected by controversies surrounding privacy and power. For example, ethical concerns affecting
privacy and power for women could arise in other fields of applied ethics, such as legal ethics, bioethics and biotechnology
ethics. So, her arguments for a new, gender-informed ethical theory for CE would also entail that such a theory would be required
for other fields of applied ethics as well. In that case, Adam's thesis is as applicable to contemporary applied ethics in
general, as it is for CE in particular. Thus, any need for a new ethical theory, based on the account that Adam provides,
would not seem to arise solely from concerns affecting computer technology.
Górniak-Kocikowska presents a very different kind of case for why a new ethical theory is needed for CE. Her argument can
be analysed into two stages. The first stage begins with a historical look at how certain technologies have brought about
‘social revolutions’. For example, she notes that the ‘revolution’ brought on by the printing press affected both our social institutions and our (theorizing about) ethical values in profound and fundamental
ways. She then draws some comparisons with the ‘computer revolution’, claiming that it too has affected our institutions and
values in the same ways. The second stage focuses on the ‘global’ aspect of computing technology. Górniak-Kocikowska claims that, because the computer revolution is global in its
impact, we need a ‘new global ethical theory’. In particular, she argues that we need a new ethical theory that can respond
to problems generated globally by computer technology, in much the same way that new ethical theories arose in response to
social issues that resulted from technologies such as the printing press and the ensuing ‘printing-press revolution’.
The first stage of Górniak-Kocikowska's argument suggests that new ethical theories might be required whenever a ‘revolutionary
technology’ is introduced. But, what will count as a technology that is ‘revolutionary’ vs. one that is merely influential?
For example, the automobile, when introduced, might have been viewed by many people as a revolutionary technology. Yet, we
did not need a new ethical theory to address social issues affecting the impact of automobiles. Turning to the second stage of her argument, it would seem that new ethical theories are needed to
handle technologies that have a ‘global impact’. But is a new ethical theory needed for CE merely because of the global impact
that computing has had to date? Consider that many other technologies, such as aviation, space travel or reproductive technologies
(such as in vitro fertilization), have also had a global impact. However, no one has argued that we need a new (universal) ethical theory to
account for their global impact. So, it is unclear how Górniak-Kocikowska's argument can convince us that a new ethical theory
is needed for CE, at least on the basis of the evidence she provides. We next turn to Question 3(b).
15.6.2 Are any new methodological frameworks required?
While some novel, methodological frameworks have been proposed for CE, many proposals have also been based on the modification
and extension of existing applied-ethics frameworks that can be tailored in ways to address specific concerns affecting CE.
An example of the latter is articulated by van den Hoven (1997), who has argued for a method of ‘reflective equilibrium’, based on the model introduced by Rawls. Such a methodological scheme is applicable for CE (and for
engineering ethics as well), van den Hoven claims, because it provides the appropriate levels of generality and particularity
needed to ‘shuttle’ back and forth between specific cases affecting computing technology and general principle and theories
that can be applied within and across the various cases.
Van den Hoven (2008, p. 59) has described some recent methodological trends in CE, as well as in engineering ethics, in terms of a ‘design turn’. He notes, for example, that just as there was a shift in ethical analysis from metaethics to applied ethics
in the second half of the twentieth century – i.e., an ‘applied turn’ in ethics – a more recent shift has occurred in that significant attention is being paid to the role that design
decisions can play in the analysis of applied-ethics issues. For example, some ethicists now focus much of their early analysis
of ethical problems involving technologies (and practices affecting those technologies) on the various kinds of values that
can be either consciously or unconsciously built into those technologies. While some of the proposed methodological frameworks
have been fairly modest, others include requirements that are more controversial. We next examine a model, ‘disclosive computer ethics’, introduced by Brey (2000) as a methodological framework for CE. It is relatively modest in terms of the required changes it proposes.
Brey argues that the standard methodology used by philosophers to conduct research in applied ethics needs to be modified
for CE. The revised method that he proposes builds on some of the models advanced by analysts working in the area of ‘value-sensitive design’ (or VSD). For example, Friedman et al. (2008) have argued that implicit values, embedded in computing technologies, need to be identified at the design stage of their
development. They claim that designers need to understand which kinds of values they are ‘building in’ to technologies they
develop and implement. Brey argues that, in the case of computing technology, this requires some changes in the standard or
‘mainstream’ method of applied ethics. Because that model was developed to analyse (already) known moral controversies, Brey
worries that it can easily fail to identify features and practices that may have ‘moral import’ but are yet unknown. He describes
such features and practices as ‘morally opaque’, which he contrasts with those that are ‘morally transparent’. While the latter kinds of features and practices
are easily recognized as morally problematic, it can be difficult to identify some morally opaque features and practices affecting
computer technology. For example, Brey notes that many people are aware that the practice of placing closed circuit video surveillance cameras in undisclosed locations may be controversial, from a moral point of view. Many
people may also be aware that computer spyware can be morally controversial. However, Brey argues that other kinds of morally
controversial practices and features involving computer technology might not be as easily discerned because of their opaqueness.
Brey notes that a practice or a feature affecting computer technology can be morally opaque for one of two reasons: (a) it
is yet unknown, or (b) it is known but perceived to be ‘morally neutral’. An example of (a) includes computerized practices
involving cookies technology, which would be ‘unknown’ to those who are unfamiliar with Internet cookies. An example of (b) includes
practices affecting online search facilities, a technology with which most computer users are familiar. However, users may
not be aware that this technology is used in practices that record and store information about a user's online searches, which
may be controversial from a moral point of view, as some learned for the first time in 2005, when the US Government subpoenaed
the search records of users for Google, MSN and Yahoo.
According to Brey, an adequate methodology for CE must first ‘disclose’ any features and practices affecting computers that
otherwise might not be noticed as having moral implications. Appropriately, he calls his methodology the ‘disclosive method’
of CE because its initial aim is to reveal any moral values embedded in the various features and practices associated with
computer technology. It is in this sense that the standard applied-ethics methodology needs to be expanded to accommodate
specific challenges for CE. It remains unclear, however, why the disclosive method should be limited to CE. For example, medical
technology also includes features and practices that are morally opaque. Consider that in vitro fertilization and stem cell research are examples of medical technologies that, initially at least, had morally opaque aspects
that needed to be ‘disclosed’. So the methodological changes proposed by Brey for CE would seem to have far wider applications for applied ethics in general.
Because Brey's ‘disclosive method’ mainly expands upon the standard method used in applied ethics, it is not a radically new
framework. However, others argue that we need an altogether different kind of methodological framework for CE. Perhaps the
most provocative proposal is Floridi's Information Ethics (IE) methodological/macroethical framework.
We have already examined some important aspects of IE in Section 15.5.2, where our focus was on the status of informational objects that qualified as moral patients in the infosphere. In this section,
our primary emphasis is on how IE also functions as a macroethical theory/methodological framework for CE. In Section 15.5.2, we saw how Floridi's IE macroethics was different, in several key respects, from standard ethical theories such as utilitarianism,
Kantianism and virtue ethics. We next examine some of Floridi's arguments for why IE is a superior methodological framework
for CE. They are based on distinctions he draws between: (i) macroethical vs. microethical issues; (ii) patient-centred vs.
agent- and action-centred systems; and (iii) (non-moral) agency and moral agency. We begin with a brief look at Floridi's
arguments involving (i).
Floridi (1999b) claims that one virtue of IE, as a methodological framework, is that it enables us to distinguish between macroethical and
microethical aspects of CE. He argues that IE, as a macroethics, helps us to analyse specific microethical issues in CE, such
as privacy, in a way that the standard macroethical frameworks cannot. Floridi notes that the concept of privacy is not well
theorized by any of the standard macroethical theories used in CE, and he shows how IE can help us to understand some of the
ontology-based considerations that need to be taken into account in analysing the concept of privacy and framing an adequate
informational-privacy theory. Floridi (2005d) advances a theory, called the ontological theory of informational privacy, which he argues is superior to the classic theories of informational privacy. His ontological privacy theory is provocative
for several reasons; for one thing, it shifts the locus of a violation of privacy away from conditions tied to an agent's
personal rights involving control and ownership of information to conditions affecting the information environment, which
the agent constitutes. In this sense, his theory provides us with a novel way of analysing the impact that digital technologies
have had for informational privacy. However, one critique of Floridi's privacy theory is that it does not explicitly distinguish
between descriptive and normative privacy regarding claims about privacy expectations for informational objects. As a result,
one might infer that, in Floridi's theory, every informational object deserves normative privacy protection (Tavani 2008). Unfortunately, we cannot further examine Floridi's privacy theory here, since doing so would take us beyond the scope of
this chapter.
We next examine some of Floridi's arguments for (ii). As we saw in Section 15.5.2, Floridi holds that one advantage that IE has, over the standard macroethics frameworks, is that the former is patient-centred, as opposed to being merely action-oriented or agent-oriented. Whereas virtue ethics is ‘agent oriented’ in that it focuses on the moral character development of individual agents, Floridi characterizes
both utilitarianism and deontology as ‘action oriented’ because they are concerned with the consequences and motives of individuals
engaged in moral decisions. And because action-oriented and agent-oriented theories focus primarily on agents and on the actions
(and character development) of agents, Floridi claims that they do not adequately attend to the recipients of moral actions
(i.e., moral patients). He argues that the IE methodological framework provides the conceptual apparatus needed to understand
our role, as well as the roles of artificial moral agents, in preserving the well-being of the infosphere. This brings us
to (iii), Floridi's accounts of agency and moral agency. We noted earlier that in IE, informational objects can qualify as
moral agents (in addition to being moral patients).
How does IE differentiate a moral agent from a moral patient? Floridi (2008e, p. 14) describes a moral agent as an
interactive, autonomous, and adaptable transition system that can perform morally qualifiable actions.(italics Floridi)
By ‘interactive’, Floridi means that ‘the system’ and its environment ‘can act upon each other’. A system is ‘autonomous’ when it is able to ‘change state without direct response to interaction, i.e., it can perform internal transition
to change its state’. To be ‘adaptable’, the system's ‘interactions (can) change the transition roles by which it changes state’. Finally, an action is
‘morally qualifiable’ when it can cause some ‘good or evil’. So any (interactive, autonomous and adaptable) individual or
system that is capable of causing either good or harm in the infosphere qualifies as a moral agent in IE.
Floridi points out that the moral agents, inhabiting the infosphere, include ‘artificial’ agents, which are not only ‘digital agents’ but also ‘social agents’ (such as corporations). These artificial
agents also qualify as (artificial) moral agents if they can be held ‘morally accountable for their actions’ (Floridi, 15). But we should note that in IE, accountability is not identical to moral responsibility.
Floridi draws a distinction between moral responsibility, which requires ‘intentions, consciousness, and other mental attitudes’, and moral accountability, which he argues does not require these criteria. Whereas responsibility is associated with ‘reward and punishment’, Floridi
argues that accountability can be linked to what he calls ‘agenthood’ and ‘censure’. Thus, Floridi claims that there can be
agency based only on accountability but in the ‘absence of moral responsibility’.
In IE, humans are special moral agents, who have what Floridi and Sanders (2005) call ‘ecopoietic responsibilities’ – i.e., responsibilities towards the construction and well-being of the whole infosphere.2 ‘Ecopoiesis’ refers to the ‘morally informed construction of the environment’, based on what Floridi describes as an ‘ecologically
neutral perspective’. Floridi (2008e) believes that humans, qua members of Homo Poieticus, have a moral obligation not only to be concerned with their own character development but also ‘oversee’ the ‘well-being
and flourishing of the whole infosphere’. More specifically, Homo Poieticus, as a human moral agent, has special responsibilities to the infosphere that are guided by four moral principles (Floridi,
p. 17):
The four principles are listed in order of increasing value. In IE, a moral agent is accountable for any action that increases
the level of entropy (defined in Section 15.5.2) in the infosphere. In particular, human moral agents can be held accountable for the evil produced – i.e., the harm caused
to the infosphere (as well as harm caused to the ecosphere and to other humans). Because of this, Floridi argues that human
moral agents have special moral responsibilities that exceed those of other moral agents (in the infosphere). And because
of IE's attention to the roles that moral agents play vis-à-vis moral patients, Floridi argues that IE is able to address
issues that the standard moral methodological frameworks are unprepared to handle.
(1) entropy ought not to be caused in the infosphere;
(2) entropy ought to be prevented in the infosphere;
(3) entropy ought to be removed from the infosphere;
(4) the flourishing of informational entities as well as the whole of the infosphere ought to be promoted by preserving, cultivating
and enriching their properties.
IE provides a robust methodological framework for CE, but it has also been criticized on several grounds. Floridi (p. 18)
notes that two general types of criticisms tend to recur in the CE literature: one that centres on conceptual challenges for
IE's accounts of agency and moral agency;3 and one based on the notion that IE is ‘too abstract’ to be useful in applied ethics. In responding to these criticisms,
Floridi points out that IE is not intended to replace the standard macroethical theories. Instead, he proposes that IE can ‘interact with those theories’ and thus ‘contribute an important new
perspective’ from which we can analyse CE issues (Floridi, p. 20). In this sense, IE can be construed as a methodological
framework that is intended to supplement (rather than replace) the standard macroethical frameworks used in CE. So, Floridi claims that his IE framework is not as radical as some
of his critics have suggested.
We conclude this section by summarizing some key points in our response to Question (3b). If IE is correct, then our standard
or methodological framework for applied ethics, as well as Brey's method of disclosive computer ethics, will fall short. However,
we have seen that IE has been criticized and thus has not been fully embraced, at least not yet, as the received methodological
framework for CE. But we have also seen that one of IE's strengths is the way that it anticipates CE issues affecting agency
and moral agency; even many of IE's critics are acutely aware of the controversial roles that artificial agents may soon be
capable of performing. Also, Floridi argues that IE provides a ‘common vocabulary’ for identifying and analysing a wide range
of microethical problems that will likely arise in the not-too-distant future, in connection with highly sophisticated ‘bots’
and other artificial agents. From the perspective of a new macroethics, IE arguably has heuristic value in that it causes
us to question some key assumptions about many of our foundational metaphysical and ethical concepts, in addition to agency
and moral agency. However, the question of whether a new methodological framework, such as IE, is required for CE research is one that still remains open.
15.7 Concluding remarks
In this chapter, we critically examined several claims underlying the foundationalist debate in CE. We framed that debate
in terms of three principal questions. In our analysis of Question 1, we argued that CE qualifies as a legitimate field of
applied ethics that warrants philosophical analysis. In our response to Question 2, we concluded that there were no convincing
reasons to believe that computing technology has either (a) generated any unique or new ethical issues, or (b) introduced
any new ethical objects. In answering Question 3(a), we argued that there are no compelling reasons to believe that a new
normative ethical theory is required for CE. We also saw that Question 3(b) poses some challenges that are not as easily answered
at this point. If IE's claims regarding agency and moral agency are correct, CE may require a more robust framework than what
is currently provided in the alternative methodological approaches used in applied ethics.
Acknowledgements
1 Himma uses the expression ‘information ethics’ to describe the field of applied ethics that we refer to as ‘computer ethics’
in this chapter. The two expressions are often used interchangeably, but they can also refer to two distinct fields or sub-fields.
Floridi (2008e) notes that ‘information ethics’ has ‘come to mean different things to different researchers working in a variety of disciplines’,
from computer science to philosophy, to library and information science, and so forth. To avoid this ambiguity, we follow
Floridi in using the expression ‘computer ethics’ in our analysis of the foundationalist debate. We will see that ‘Information
Ethics’ (or ‘IE’) is used by Floridi (1999b) and others to refer to a particular macroethical theory/methodological framework for computer ethics, as opposed to a specific
field of applied ethics.
2 Floridi and Sanders distinguish between ‘Homo Poieticus’ and ‘Homo Faber’. Whereas the latter is a tool maker who uses the
infosphere as a resource, the former considers the well-being of the whole infosphere.