Figure 15.1 File share permissions in Windows Server 2012
I am sure that as you make your way through this book, you have begun to realize the vast number of features that have been included in Windows Server 2012. Now we come to probably the single most important new feature, Dynamic Access Control. This is a groundbreaking new feature that will shake up file server administrators forever!
Let’s start with a short example. When you join a company and you get a user account for the computer, you can be almost sure you are part of a default group called Domain Users. Now as you require access to different resources, you submit the relevant forms to the resource owners and are granted access, which usually means you are placed in the security group that has already been granted access to these resources. (For example, if you want access to financial data, the Finance share gives anyone who is part of the Finance group read-write access to the financial data.) As you want access to more and more resources, you get added to more and more groups. As new resources come online, new groups are created to manage access to them.
Think about how many file servers are deployed around the world today and how many groups are created to control access to these shares, and then add the amount of administrative effort to not only create them but maintain everything afterward. This is the reality of file server administrators today.
Now let us introduce Dynamic Access Control (DAC). This truly is the next generation in securing information that needs to be secure and controlling access to resources to which only authorized people should have access.
Imagine that a not-so-tech-savvy financial director of a large corporation decides to record all the directors’ salaries in an Excel spreadsheet and doesn’t password-protect it or put it in a secured folder. A disgruntled employee gets hold of this document and publishes it to the world. How embarrassing would that be not only to the company but also to the financial director!
Now imagine a world where the financial director does the same silly thing but the data is automatically secured because it contains keywords that trigger a process to classify the data as sensitive and allow access only to certain groups. Wouldn’t that be simply amazing! This is one of the groundbreaking features within DAC. Hopefully, now you get a picture of what we are about to dive into and master!
The key thing to remember is that DAC is not a single piece of technology. It is a file-server solution. It brings together conditional expressions (for example, is this user part of a group, or does the computer a file is accessed from need to be domain joined?), file classification (such as high business importance, classified, and the like), and Central Access Policies (centrally manage all the authorization policies), and with the use of Kerberos it validates “claims” from users. In turn, these technologies come together to form DAC and allow you to create a centrally controlled governance policy across your file servers.
In this chapter, you will learn to:
We assume if you are reading this chapter that you know the basics of file shares: how to create them and manage them. If you don’t, stop! And turn back to Chapter 13 where you will learn all this. If you are familiar and are ready to proceed, let’s go!
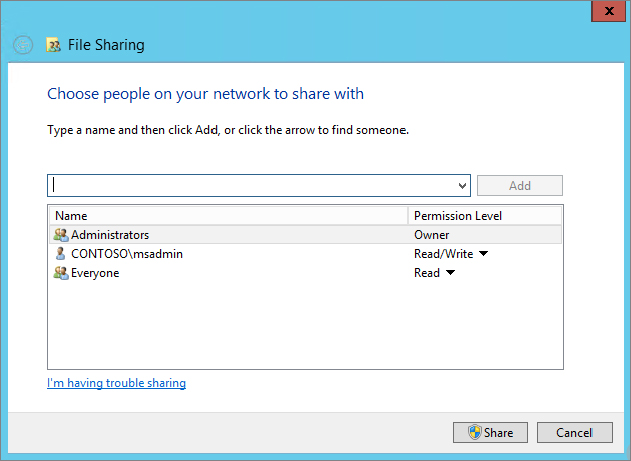
Let’s dive straight in and look at the share permissions on a file share, as shown in Figure 15.1.
Figure 15.1 File share permissions in Windows Server 2012

As you can see, no major changes have happened there. The real power in securing file shares is through the security properties, as displayed in Figure 15.2.
Figure 15.2 Security tab for a file share
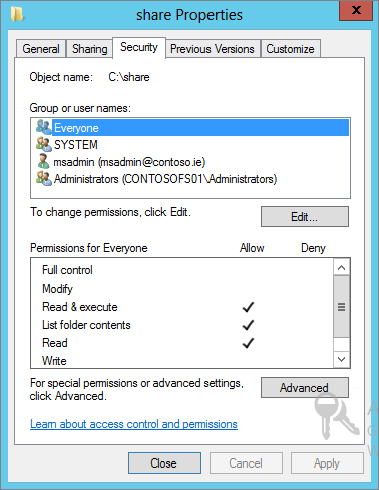
This Security tab dictates the NTFS permissions to not only the folder but the files as well. But as you can see from this tab, it doesn’t look much different than in previous versions of Windows.
Since this is most definitely an advanced feature, it is rightly placed under the Advanced button located at the bottom of the Security tab; see Figure 15.2.
Figure 15.3 shows the Advanced Security settings for a file share, and it is where we can begin to configure the basics of DAC.
Figure 15.3 Advanced Security settings for a file share
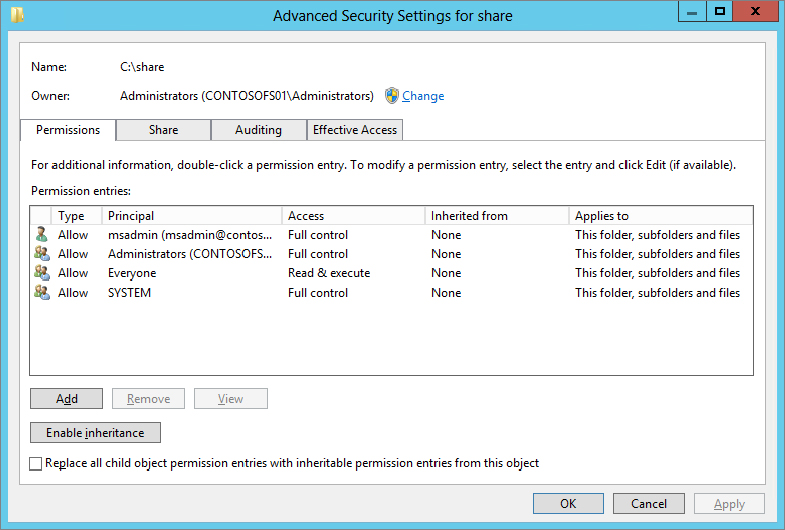
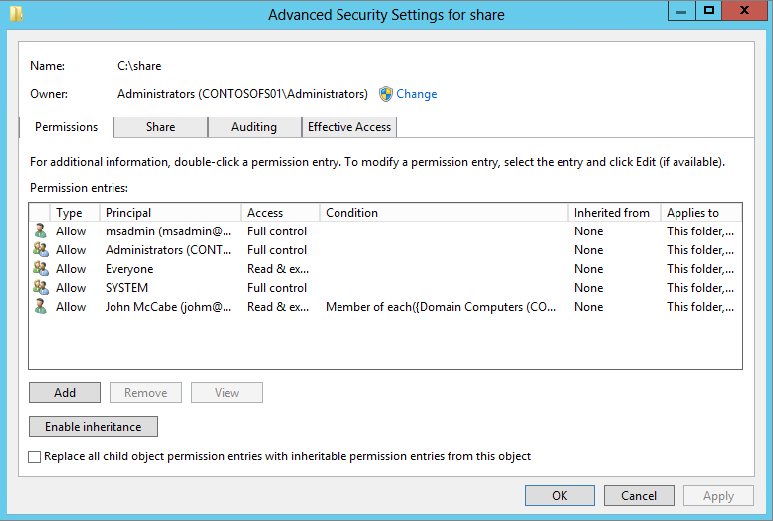
In this example we have a single folder called share. It is shared to everyone for read-only access via its share permissions and read-only via its NTFS permissions, and we also allow our administrators Full Control. As you can see from Figure 15.3, however, the Everyone principal has Read & execute access. Now you can start to see the granular control the Advanced Security settings offer, but this is still not DAC.
Click Add from the Advanced Security Settings screen, and you will be brought to the “Permission Entry for share” screen, as shown in Figure 15.4.
Figure 15.4 Permission Entry for share
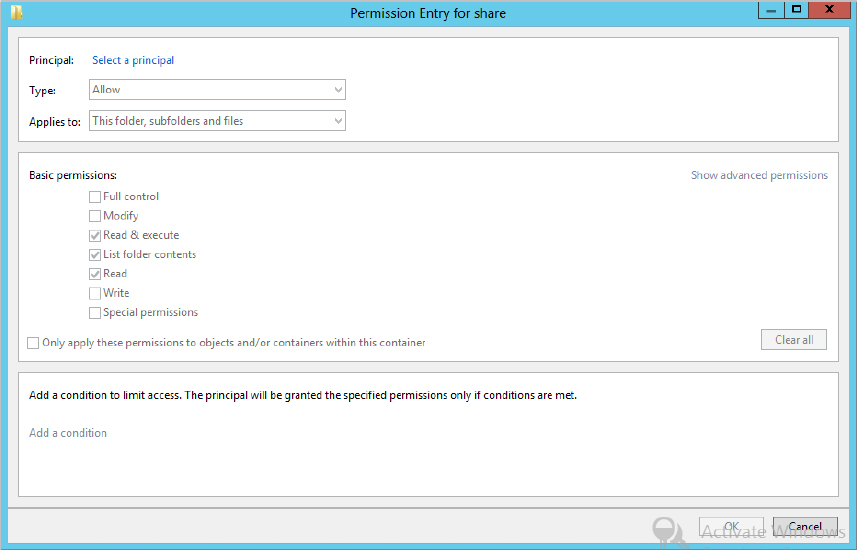
In order to progress, you must select a principal. A principal would be, for example, a user account or a group to which you want to assign privileges. If you don’t select a principal at this stage, all the elements will stay grayed out.
As you can see, quite a few options look familiar from previous versions of Windows. However, now there is a new section where you can add a condition. This is where the power of DAC begins: with conditional expressions.
When you click “Add a condition,” you will get the chance to create a condition, as shown in Figure 15.5.
Figure 15.5 Adding a condition
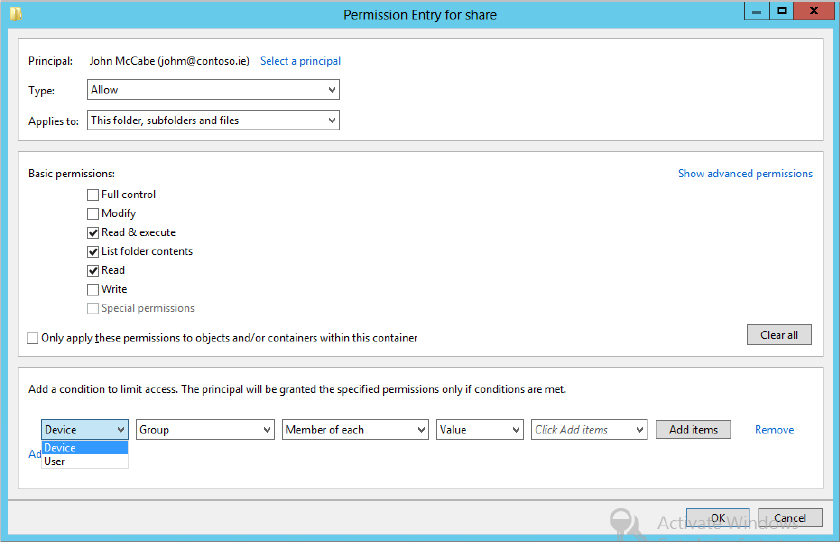
The first condition to choose from is a device or a user. Now you can secure data not only down to the user account but also from the device from which they access the resource. You can ensure that they have to access the resources from a corporate device but not their home laptop. That way, you can ensure the security of the data because you control the corporate laptop/desktop.
In the example in Figure 15.6, we have allowed John McCabe (johm@contoso.ie) Read & Execute, List Folder Contents, and Read permissions, but we have now added a condition that in order to access the share he needs to be on a computer that is part of the Domain Computers group.
Figure 15.6 “Permission Entry for share” dialog adding a condition
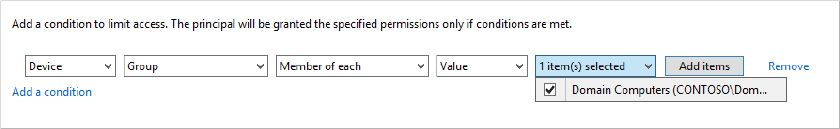
Now, returning to the “Advanced Security Settings for share” screen, you can see the new principal added but the Condition column for John McCabe is now populated, as shown in Figure 15.7.
Figure 15.7 Advanced Security Settings with Condition listed
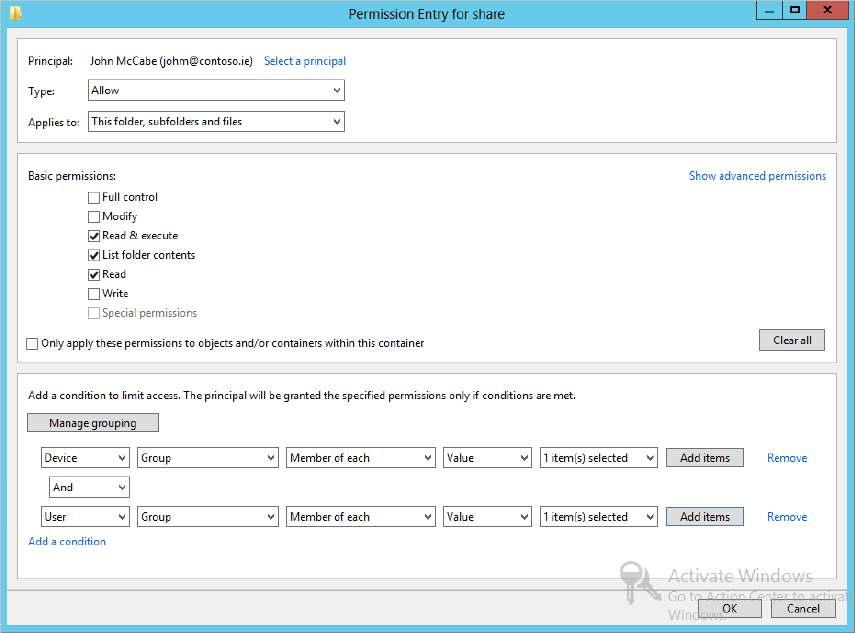
If we re-edit the principal John McCabe (johm@contoso.ie), we can add additional conditions and apply Boolean logic to the conditions using “And” or “Or.” “And” ensures that all conditions are true. For example, we could set a device condition to be part of the Domain Computers group and a user condition to be part of the IT group. If both conditions are not met, access is not granted. In the “Or” case, if either condition is true, then access will be granted. See Figure 15.8 for a sample “And” condition.
Figure 15.8 Sample “And” condition
As you saw in the previous section we could select a principal (and remember, a principal could be a user or a group) and assign a condition, and then based on the condition, access will be granted or denied. This leads back to an age-old problem of administration of groups.
Think about it. In an enterprise or even a small business, how often do groups in Active Directory get cleared out, and how often are privileges for the existing user base assessed to ensure they are still valid? Should someone really be part of the IT Admins group now that they are a truck driver? What if now you could, for example, change the Department field in the user account in Active Directory, and it would then change the access permissions?
Active Directory stores lots of information with different tags to identify the data, called attributes. For example, when you create a user account, the most basic information you enter would be the first name and last name of the person. This information is stored in an attribute in Active Directory. These attributes can be reviewed and edited (but do be careful because it is not pretty if you mess up). Figure 15.9 shows a sample of some attributes; in this case we are viewing the given name (first name) for the user David McCormick.
Figure 15.9 Department Active Directory attributes
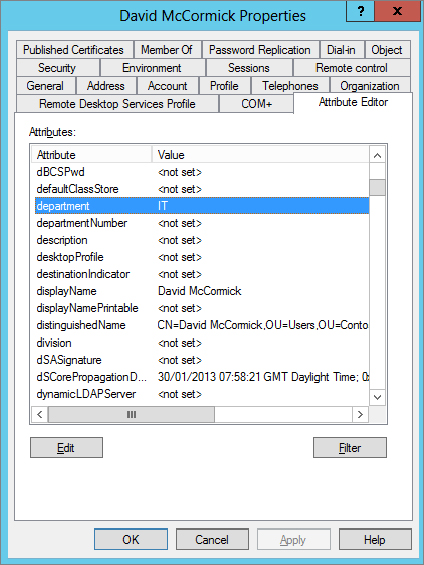
A very useful attribute you can use to help secure information is the Department attribute. As you see in Figure 15.9, our user David is part of the IT group. We know IT contains lots of sensitive information, and we certainly don’t want usernames and passwords or sensitive network information falling into the wrong hands.
If you review all the attributes available for a user, you will see it’s a very long list. In reality only a few fields may prove useful in controlling access to the data. Some examples of this would be EmployeeType (you may not want part-time staff to access certain types of data), Company (you don’t want a child company accessing data from Contoso), and PhysicalDeliveryOfficeName (you might not want employees in London accessing data in the New York office).
Don’t be limited by the options I mentioned; you can come up with your own options. If the attribute you want doesn’t exist, you can create it and use it. This is obviously not for the faint hearted, but it illustrates just how flexible DAC can be.
In Figure 15.5 we had only the User and Device options. Now we have a new option called Resource; see Figure 15.10.
Figure 15.10 Resource option in the “Permission Entry for share” screen
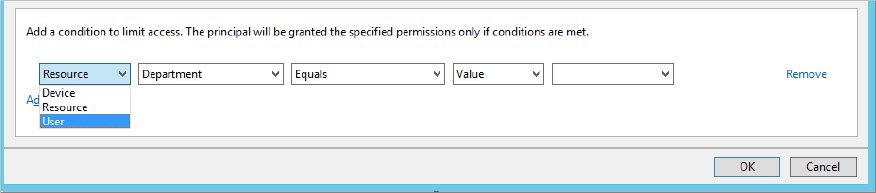
The Resource option gives you the claim types (essentially the attributes you publish to present as authorization claims to access resources) you have published. In our example, once we select Resource, the Department option is displayed. Don’t worry for now how it got there; we will show you how later in the chapter.
The same logic conditions of Equals or Not Equals exist, but now the last options field automatically provisions a list of common departments to select from. See Figure 15.11.
Figure 15.11 Department selected and potential values
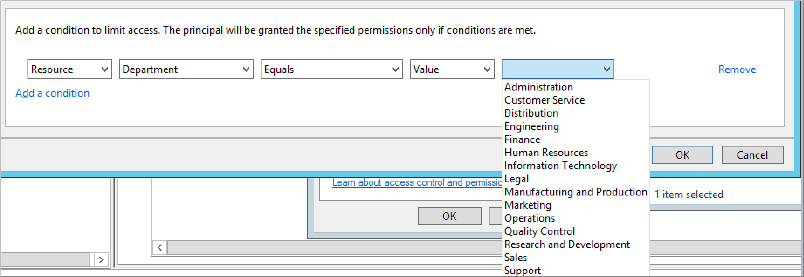
This list is not pulled from a summary list of all users in your Active Directory. It is a default list provided by DAC when you publish an attribute as a claim type; you can modify it if needed.
Don’t jump ahead! In order for DAC to work, you need to build up the solution, and it is important that you understand the concepts before configuring the solution.
In recent years many companies have had to address the bring-your-own-device (BYOD) craze. It has become common for staff to use their own money to purchase the latest devices that suit their personal needs but will also allow them to access data on the corporate network. These include tablets and laptops and on rare occasions home desktop computers. From an IT administrator’s perspective, this can be frustrating when you are asked to tightly control access to information. You can see the problem: because the enterprise doesn’t own the asset, there is only so much they can do to control the security of the device. The big issue is how these devices can operate in an environment but be restricted to information that is not sensitive.
Take a few seconds to review Figure 15.5 again; you will see that we have a Device option. This option allows us by default to decide whether a computer is part of a group and whether to allow access to a resource. Imagine you create four groups: one group for desktop machines, the second group for laptops, the third group for Finance, and the fourth group for Engineering. Now you could create rules requiring that only the desktop computers and laptop computers that are also part of the Finance group can access all information contained within the Finance share. That way you can encrypt the Finance machines (desktop or laptop) so that if a user does copy data off the central share, the information is protected. It’s a simple example, but straight away you can see how much more control you can implement to protect your company’s information.
You now have a powerful tool to control access to resources, but if you had to manually implement this, it would obviously take a huge amount of time. Like most things in IT now, centralized is best! Could you imagine taking the power of DAC but having to implement it for every file server in your environment?
Windows Server 2012 has a management utility called Active Directory Administrative Center (ADAC). This utility can be found in Server Manager under Tools.
Once the ADAC is launched in the navigation section on the left side, you will see Dynamic Access Control listed. When you click Dynamic Access Control, it brings you to the core area, where you will centrally configure the DAC rules for your environment. Take a look at Figure 15.12, which shows the Active Directory Administrative Center.
Figure 15.12 Dynamic Access Control in the ADAC
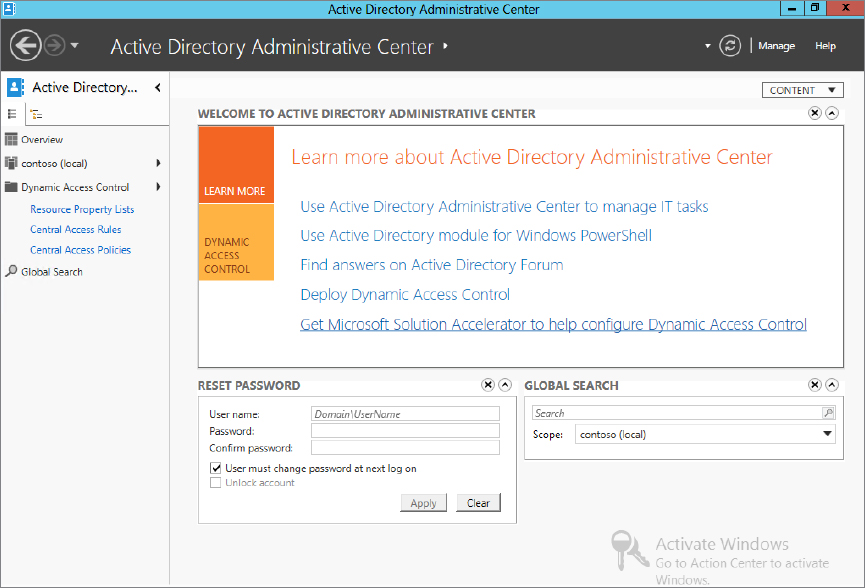
We’ll take a minute to explain each of the items you see listed under the main Dynamic Access Control window. These will become important as we progress:
Figure 15.13 Central Access Rules
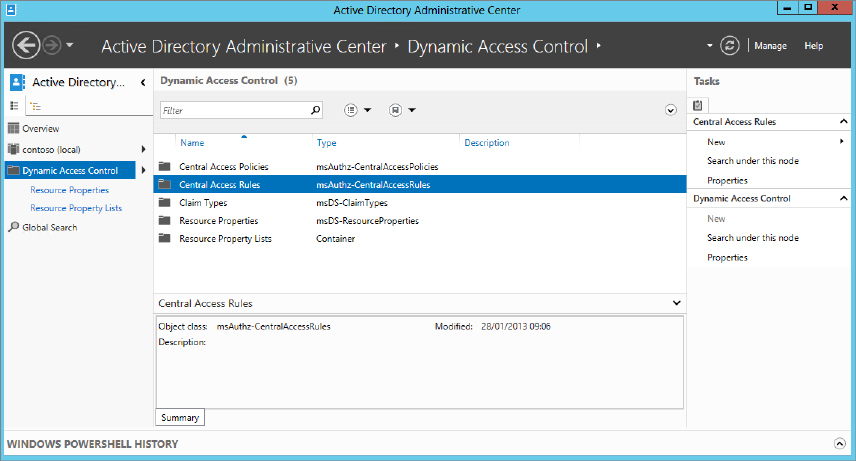
Later in this chapter we will show you examples of creating all these particular elements and bringing them all together.
Let’s say your company has applied a Central Access Policy to a test share on your file server. This share has several subfolders containing simple folder names based on three departments: Sales, Accounts, and Engineering. The administrator has already configured the policies to authorize access to the each individual folder only by the department.
The administrator wants to ensure that policies are working correctly. With the use of effective permissions you can achieve this, and you can also test individual user accounts without having to obtain their credentials and test their access.
Don’t worry if you don’t fully understand this right now. Later in this chapter we’ll show you how to use effective permissions, and we’ll include the appropriate screenshots.
By now you’re aware of the considerable power Dynamic Access Control can bring. Think about all the information contained within the files that are hosted on the network shares within your company and then try to imagine how you are going to protect every one of them.
Traditionally, protecting data was a manual process, and what was worse, you had to ensure that the IT administrators and users understood how to manage their documents correctly.
Imagine if someone put the payroll Excel spreadsheet in the wrong place, which didn’t have the traditional permissions to protect it! Imagine if your company had intellectual property and it was not secured correctly! Finally imagine the stress of managing and trying to guarantee the security of the data.
In modern IT infrastructures, centralized management—where as many tasks as possible are automated—should be the minimum base for an organization. Applying this simple principle to the classification of data is extremely important.
Using the resource properties mentioned early in this chapter, you can do this! These resource properties allow you to manually set classifications, but when you combine these with the File Server Resource Manager (FSRM) in Windows Server 2012, you can automatically classify the documents. If an end user does misplace a document in a file share, you are confident that no sensitive information can be accessed by unauthorized parties. Later in this chapter we will give you a demonstration on how to complete this.
As we progressed through this chapter so far, we touched on the key players in DAC and what makes it work. Before we start enabling DAC and walking you through scenarios, we’ll recap on these players and provide some more information about them.
Let’s start with the user. A user, as we all know, is generally how we identify ourselves and is the primary method of authorization. You can grant access to resources on just the user object. However, user accounts contain an enormous amount of information, which when properly populated will let you use these fields (attributes) to provide additional authorization to resources.
Like users, devices also have a huge amount of information that you can use. You just need to select the attributes you need. A good example would be for sensitive information; to prevent leakage of this data, it would be great to be able to limit access to this information to devices that you know will always be physically located in and connected to the corporate network. You can restrict access to such information based on location. For desktop computers, you can simply enter Onsite in its Location field, and for laptops you can enter Mobile.
Normally for desktops, corporations restrict access to removable media and physically secure the asset. Because a laptop by its very nature is mobile, it is very difficult to physically secure the asset, and there may be a valid business reason to enable access to removable media. A user can now access the sensitive information, copy it to their laptop, and then copy it onto a USB device. However, with a Device claim you can restrict access to this sensitive information by the type of device the user is on, even if they have full access assigned. If the user is not on a physically secure asset, they can’t access the sensitive information, thus preventing data leakage.
Resources are key. If they haven’t been defined, they should be defined. They help classify the data on your file servers, and they will work with the File Server Resource Manager to ensure this happens automatically. This solves the big issue of how to apply this retroactively to your current environment. Microsoft has already done a lot of work out of the box on defining resources within DAC, and it is my opinion that it is best to see what is there. Remember, you must spend time planning your resources; if you don’t, it will become a big problem later on.
A claim is information from a trusted source about an entity. It is a method of authorization that is based on an attribute (either a device or a user normally) to provide additional security to resources. It could be your office location or your department or any other attribute that is defined to provide you access to information. For example, if your office location is New York, then you can access the America user share.
Claims are of three different types (we’ve already discussed user and device claims, so we’re providing just a brief overview here):
You now know the key players, and as you progress enabling DAC and configuring it for your environment, you will begin to put this information into context.
Let’s begin.
In this section of the chapter I assume you have Windows 2012 installed and ready to play. In our lab environment we have three servers running Windows 2012 and a client running Windows 8. The servers are configured as one domain controller and two file servers. There are several user accounts with certain attributes (for example, Manager, Location, and Department) configured to allow you to create claim types later on.
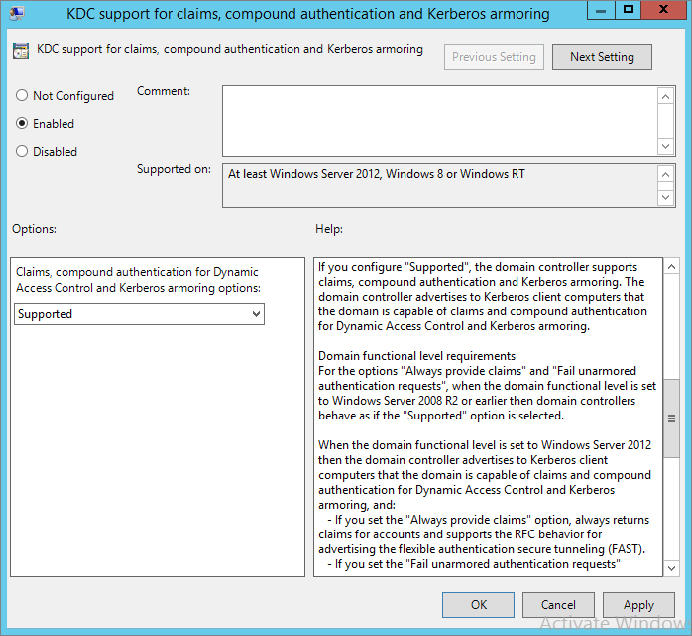
First, you need to enable support for claims, compound authentication, and Kerberos armoring in the Kerberos Distribution Center (KDC), which is where your Kerberos authentication tickets are generated via Group Policy.
 Domains
Domains  yourdomain.com
yourdomain.com  Domain Controllers and locate the Default Domain Controllers Policy, as shown in Figure 15.14.
Domain Controllers and locate the Default Domain Controllers Policy, as shown in Figure 15.14.
Figure 15.14 Group Policy Management Tool showing the Default Domain Controllers Policy
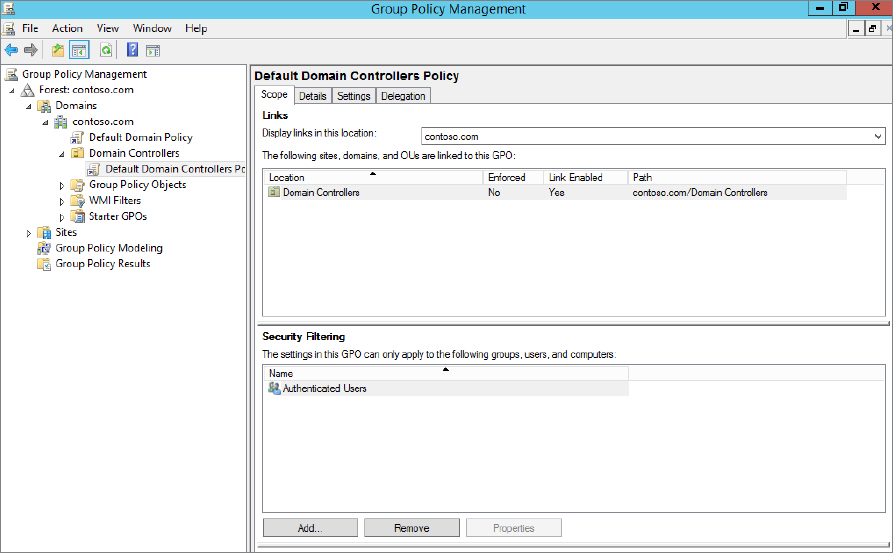
Figure 15.15 Group Policy Management Editor
 Policies
Policies  Administrative Templates
Administrative Templates  System, as shown in Figure 15.16.
System, as shown in Figure 15.16.
Figure 15.16 Location of policy to edit to enable KDC support
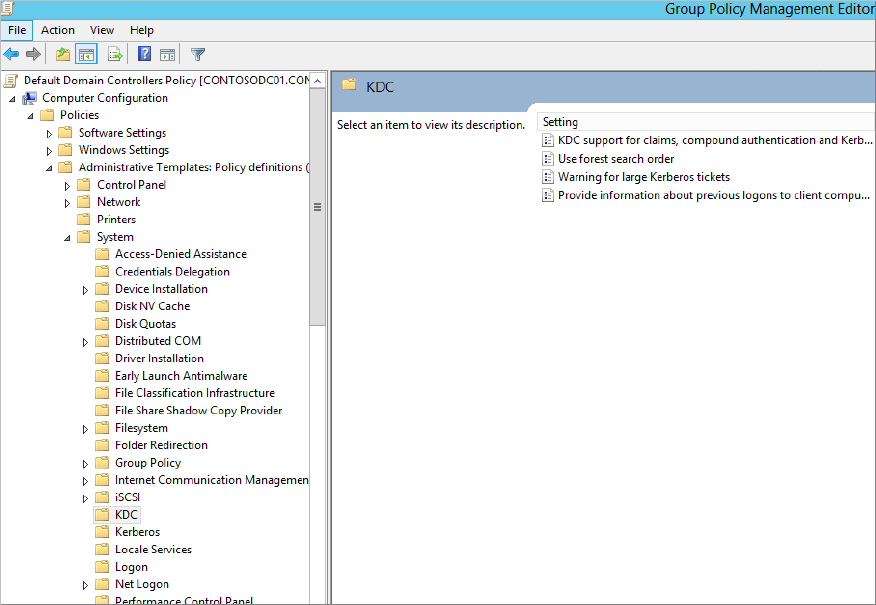
Figure 15.17 Configuring “KDC support for claims, compound authentication and Kerberos armoring”
Earlier in this chapter we showed you the Active Directory Administrative Center. This is where you will configure Dynamic Access Control.
You have learned that in order for DAC to work you have several prerequisites to configure: the claim types, the resources, and the central access rules. We also mentioned that we want to minimize the management overhead. This is where Central Access Policies come into play. They bring all of our configuration work together to easily administer and control access to the information within our environments. In the following pages we will show you how to secure your file servers using DAC centrally and how this can be applied across your organization. The best way to really get to grips with this new technology is to dive right in. Let’s build a simple access policy.
Open the Active Directory Administrative Center and click Dynamic Access Control, as shown in Figure 15.18.
Figure 15.18 Active Directory Administrative Center
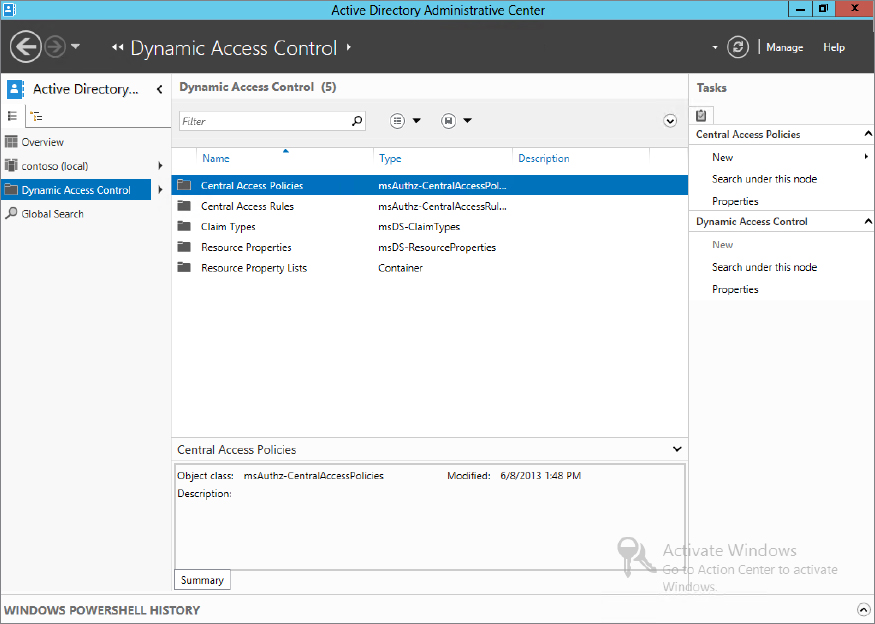
At this point, if you try to create a Central Access Policy, you will not be able to. As we mentioned, you have to create resources, claim types, and central access rules to create a policy.
One thing to notice is the various options in the center window. When you click through them, the Tasks menu on the right changes to suit the option you have selected. First, you will create a new claim type:
 Claim Type, as shown in Figure 15.19.
Claim Type, as shown in Figure 15.19.
Figure 15.19 Creating a new claim type
Figure 15.20 Displaying the dNSHostName property
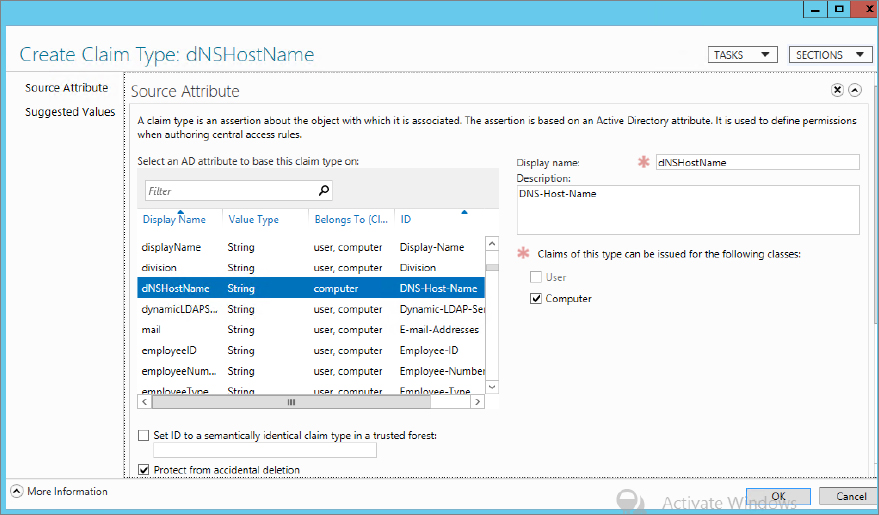
Figure 15.21 Modifying the department attribute to create a claim type
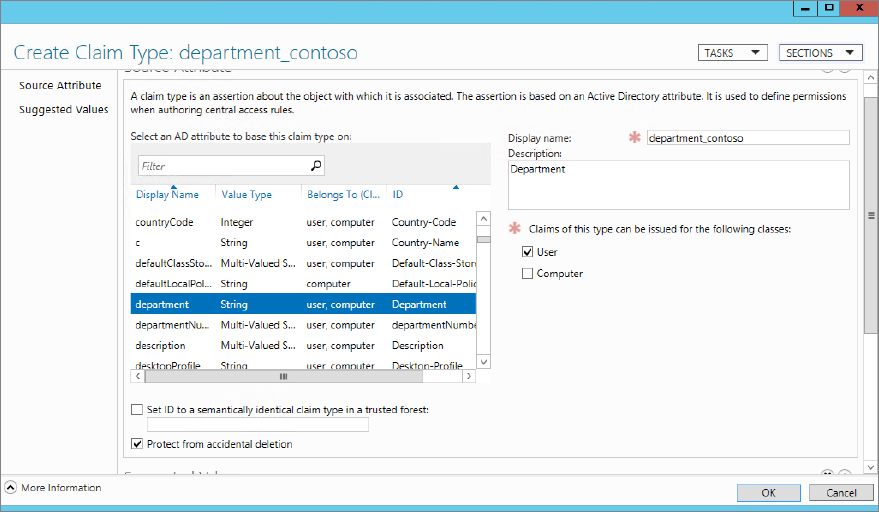
Figure 15.22 Assigning values to claim types
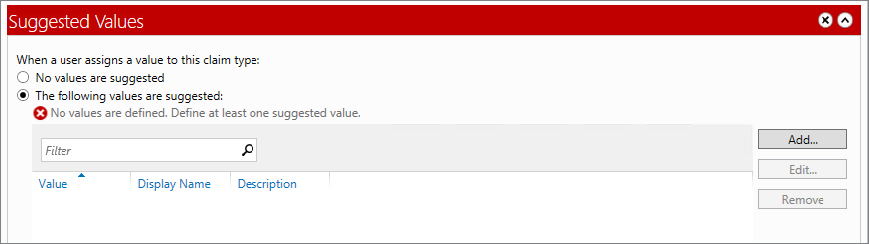
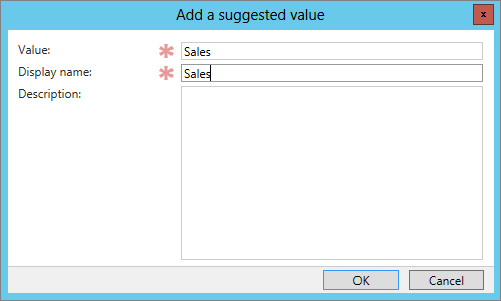
Figure 15.23 Adding a suggested value
Now you need to create a resource property:
Figure 15.24 Create Reference Resource Property screen
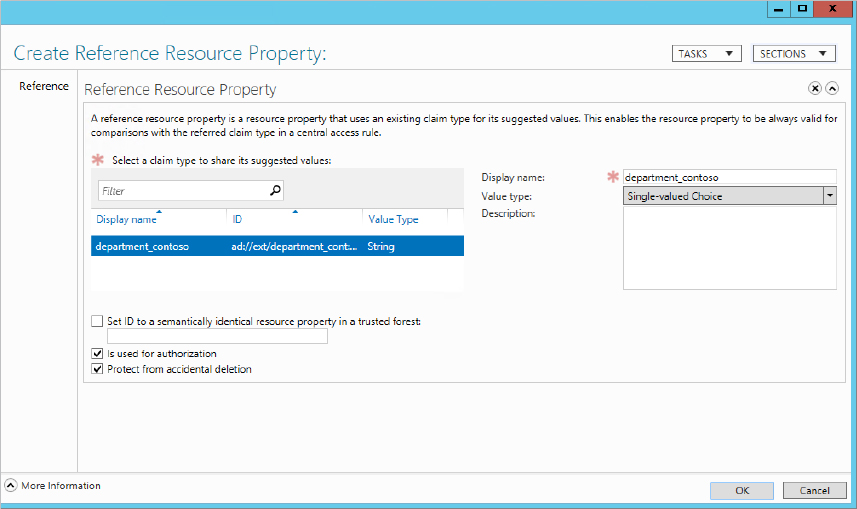
Figure 15.25 Creating a new resource property

For reference purposes, this task is the procedure for creating a resource property for which a claim type doesn’t exist, for example, if you don’t want to use the resource properties that Microsoft has provided or if they simply don’t meet your needs. Another example would be if you created a custom attribute in Active Directory and wanted to use it as a claim type.
When you’ve completed the previous exercise, the New Resource Property window will open. Then follow these steps:
 Resource Property.
Resource Property.At this point you will return to the Resource Properties screen, as shown in Figure 15.26.
Figure 15.26 Resource Properties screen
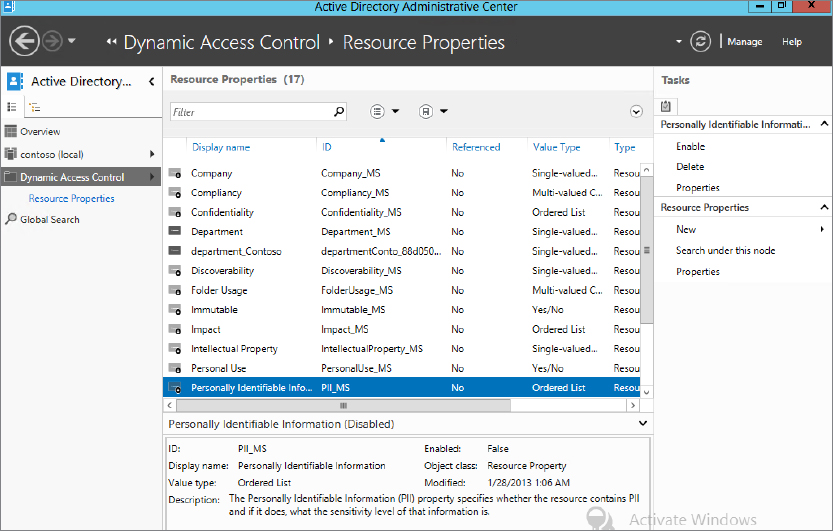
Remember when we mentioned that Microsoft has already done a lot of work to allow companies to deploy Dynamic Access Control quickly? Part of the overall goal was to make Dynamic Access Control quick to deploy, and although you have to put some thought into what rules/properties/claims types you need to create you will see from the next guide that there are a lot already done for you and all you have to do is select them.
Figure 15.27 Main Dynamic Access Control windows
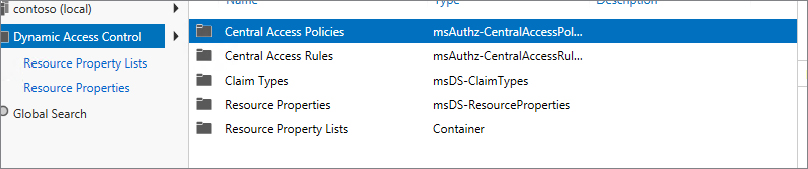
Figure 15.28 Resource Property Lists showing the Global Resource Property List
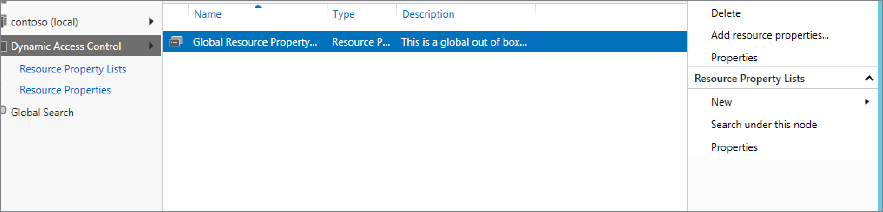
Figure 15.29 The Global Resource Property List screen
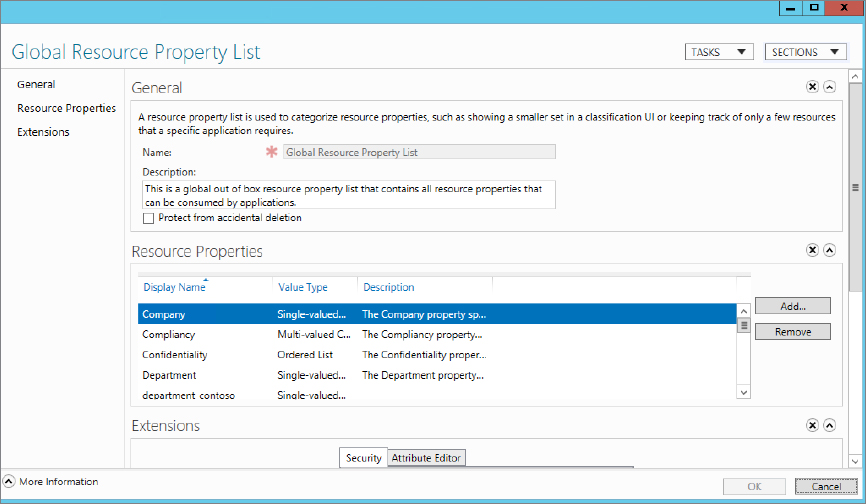
Figure 15.30 Adding a new resource property to the Global Resource Property List
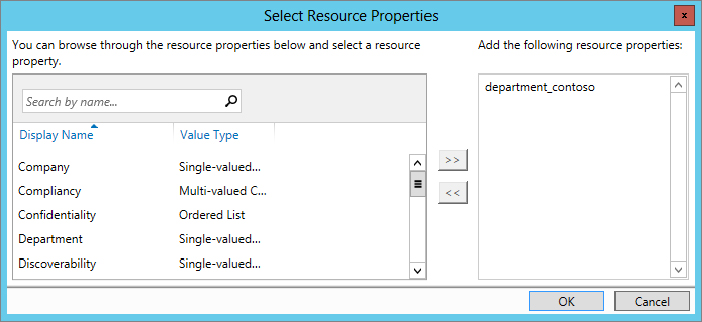
You have created a new claim type, a referenced resource property, and added it to the Global Resource Property List. Next, you need to create a Central Access Rule:
 Central Access rule.
Central Access rule.Figure 15.31 Create Central Access Rule screen
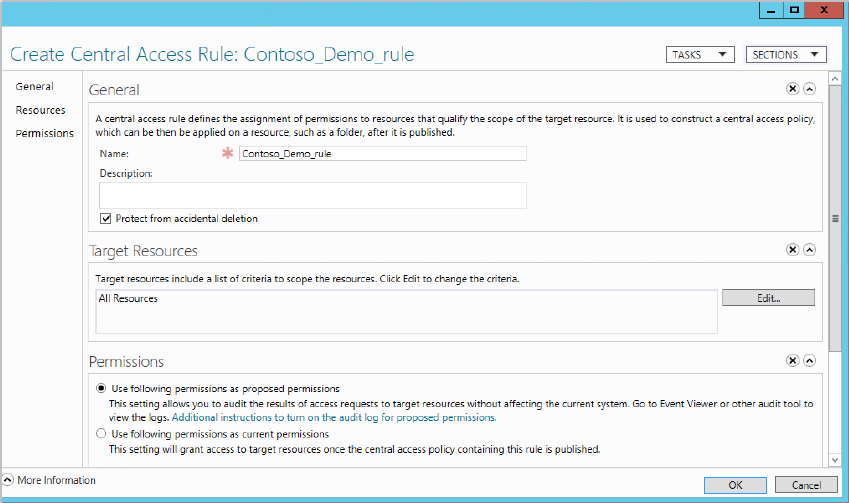
Figure 15.32 Adding permissions for a central access rule
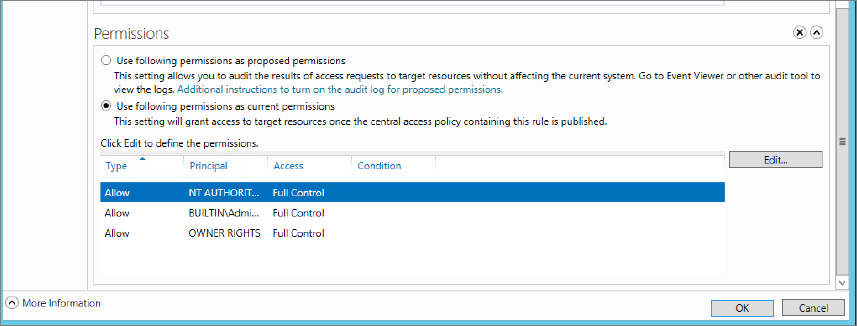
Figure 15.33 Advanced Security Settings for Permissions screen
Figure 15.34 Permission Entry for Permissions screen
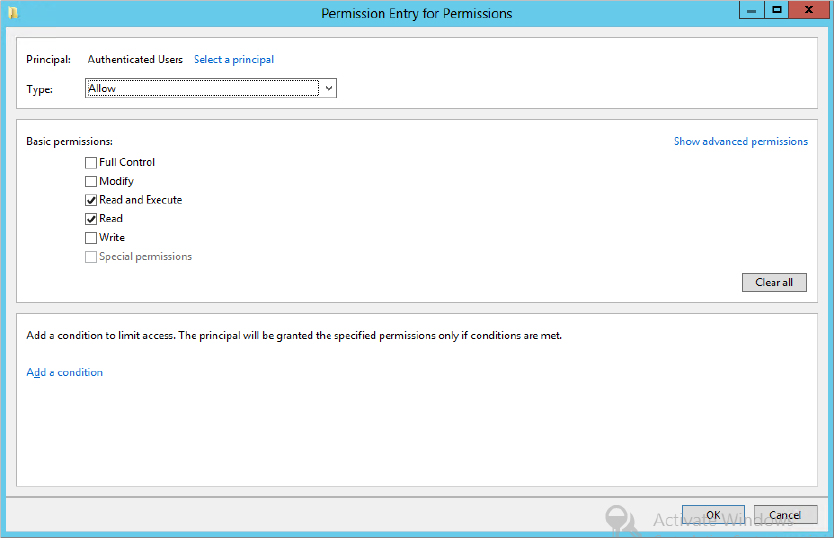
Figure 15.35 Adding conditions to a Central Access rule
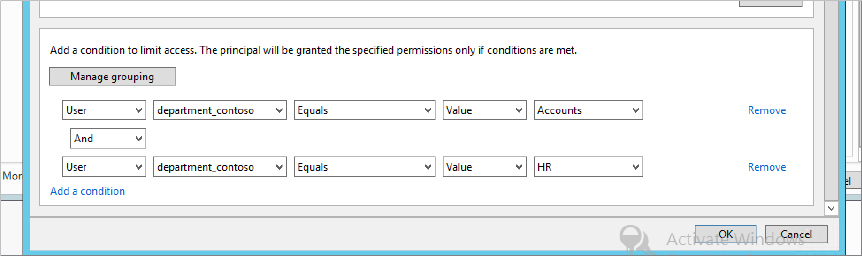
Great! You are nearly finished, now you need to create a Central Access Policy that you will then use to deploy to your file servers:
 Central Access Policy.
Central Access Policy.Figure 15.36 Create Central Access Policy window
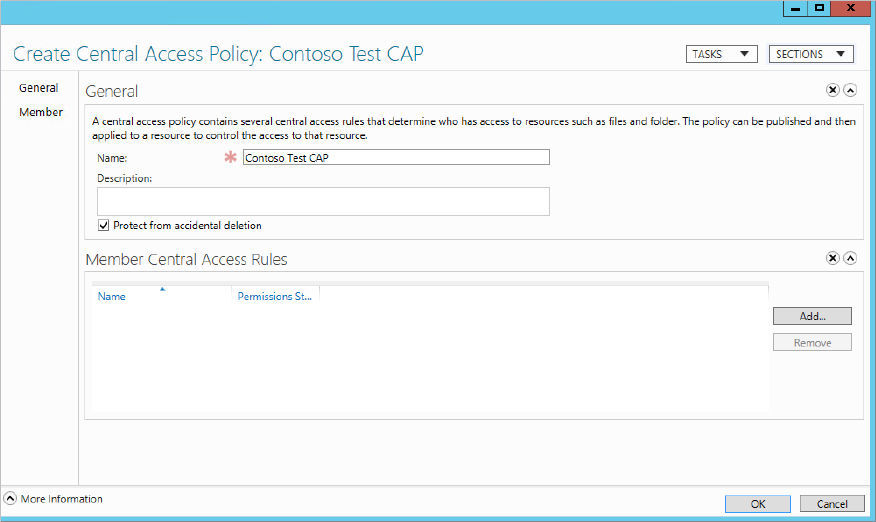
Figure 15.37 Adding a Central Access rule to a Central Access Policy
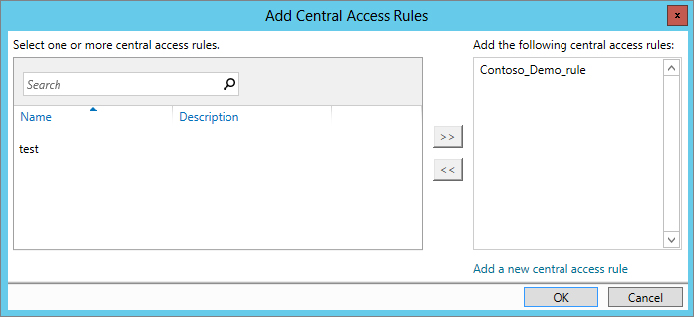
You have created a Dynamic Access Control policy, but you need to apply it to your servers in order for it to become effective. This is done via Group Policy. By deploying it via Group Policy you have amazing flexibility to start targeting specific server groups and roll it out further as necessary.
In Chapter 9 you would have become familiar with Group Policy; if not, skip back now and read it.
You need to use the Group Policy Management console to create a new group policy to roll out your Central Access Policy. To recap, the Group Policy Management console is located in Server Manager  Tools.
Tools.
In our example, our Group Policy Management console is located on our domain controller. (We assume at this point that you are familiar with this tool.)
You are now going to create a group policy just under the root level of the domain contoso.ie and target it to just your file servers. But before you start, here’s some best practice advice:
Let’s begin:
Figure 15.38 Creating a GPO for Central Access Policy deployment
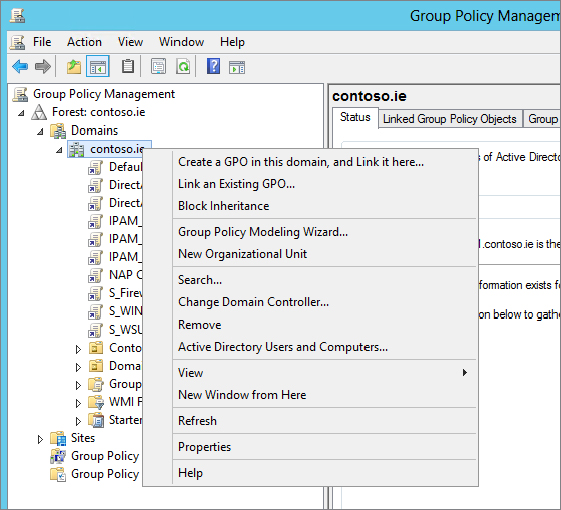
Figure 15.39 New GPO window
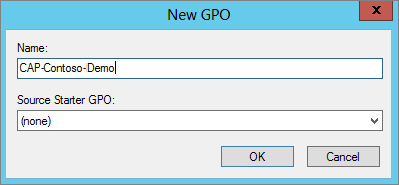
Figure 15.40 Removing Authenticated Users

Figure 15.41 Ensuring the name resolves in the search window
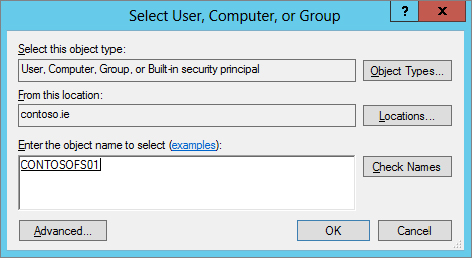
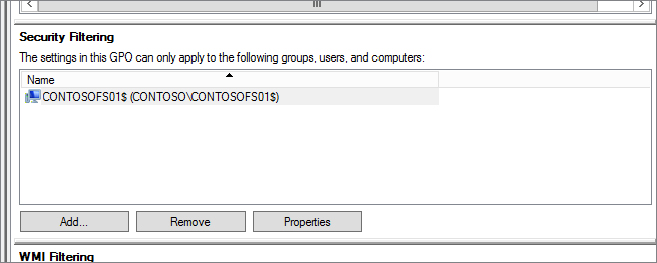
Figure 15.42 Computer account added to Security Filtering field
 Windows Settings
Windows Settings  Security Settings
Security Settings  File System
File System  Central Access Policy, as shown in Figure 15.43.
Central Access Policy, as shown in Figure 15.43.
Figure 15.43 Central Access Policy location in Group Policy Management Editor
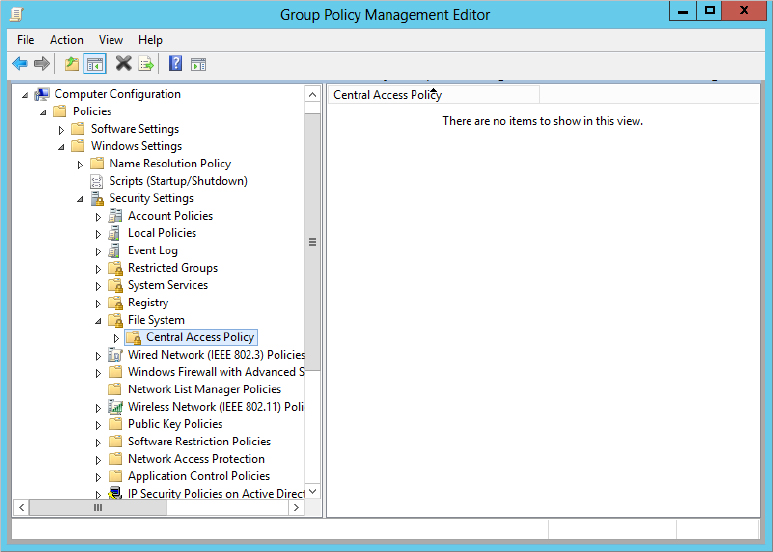
Figure 15.44 Manage Central Access Policies
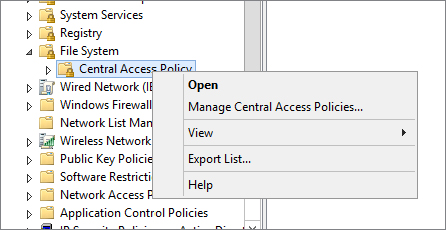
Figure 15.45 Selecting Central Access Policies to apply
 Audit Policies
Audit Policies  Object Access, and double-click Audit Central Access Policy Staging, as shown in Figure 15.46.
Object Access, and double-click Audit Central Access Policy Staging, as shown in Figure 15.46.
Figure 15.46 Enabling Central Access Policy Staging
Figure 15.47 Configuring auditing
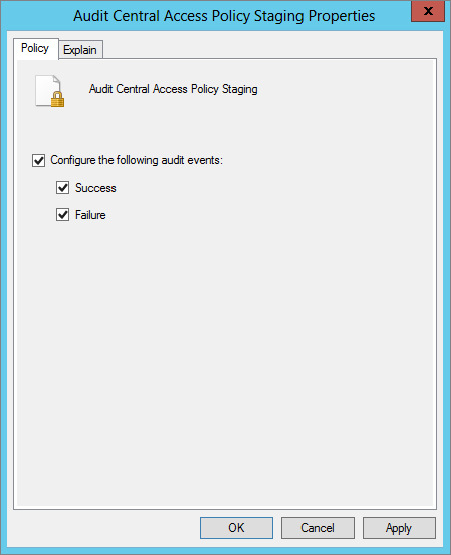
Figure 15.48 NTFS permissions
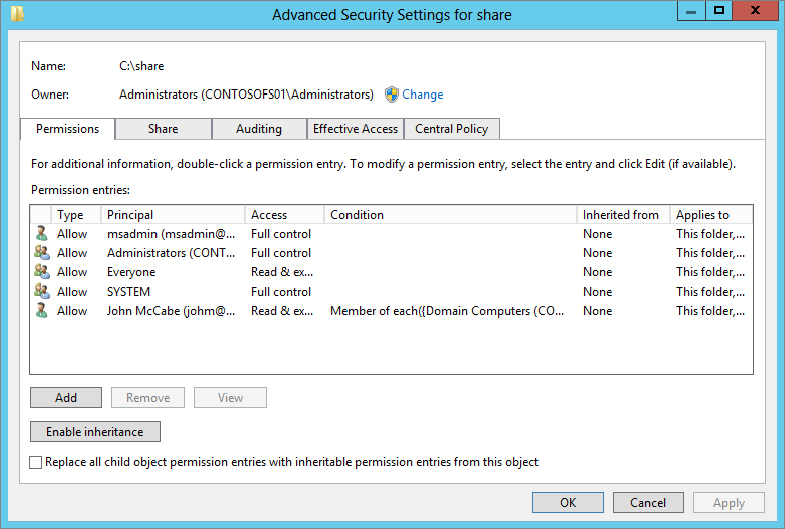
Figure 15.49 Share permissions
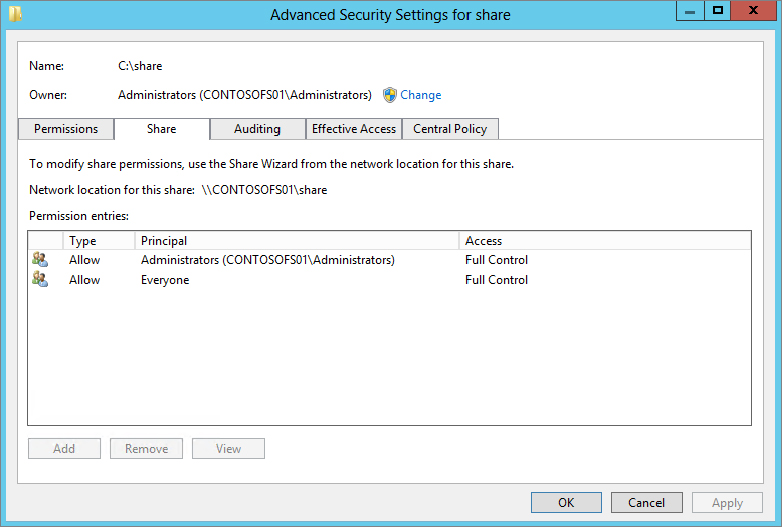
You have now applied a preconfigured Central Access Policy to your file server share. If you look at Figure 15.48 and Figure 15.49 again. For the permissions, you will see that the Everyone group has been given read-acess to the folder and share after the Central Access Policy has been applied. This isn’t really ideal, but it’s a common problem in most environments.
Technically speaking anyone should be able to access this share and retrieve the valuable information contained within. So let’s test it:
Figure 15.50 “Advanced Security Settings for share” window
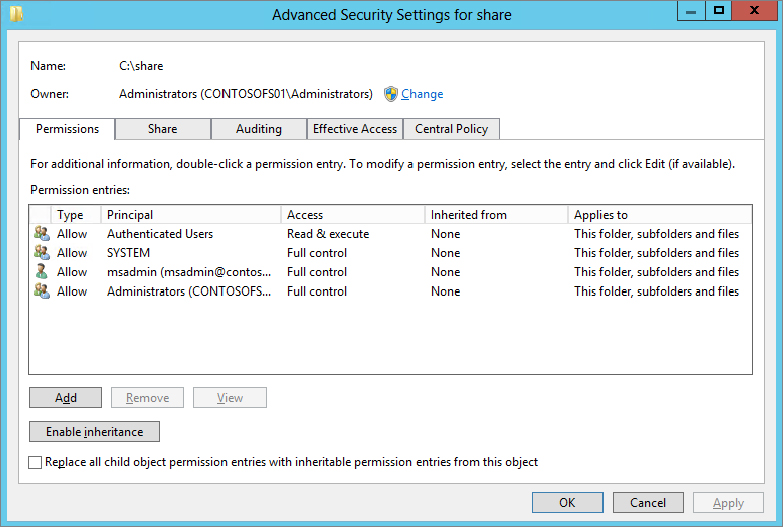
Figure 15.51 Effective Access tab
Figure 15.52 Selecting a user to test effective access
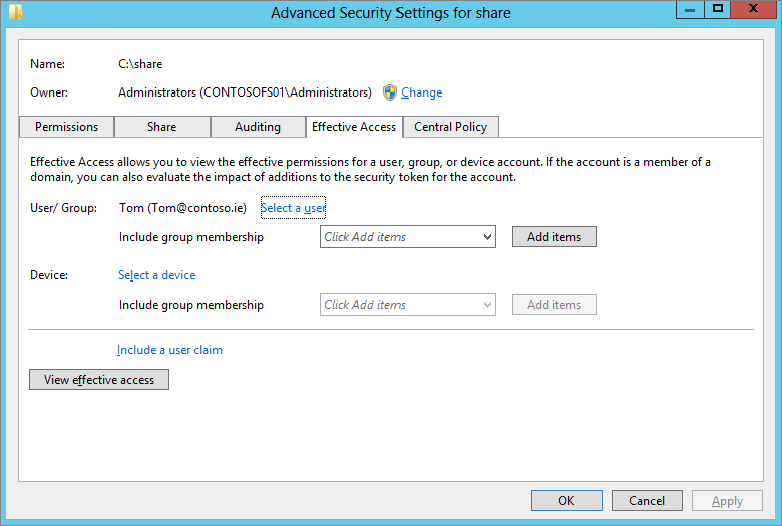
Figure 15.53 Effective access results for Tom
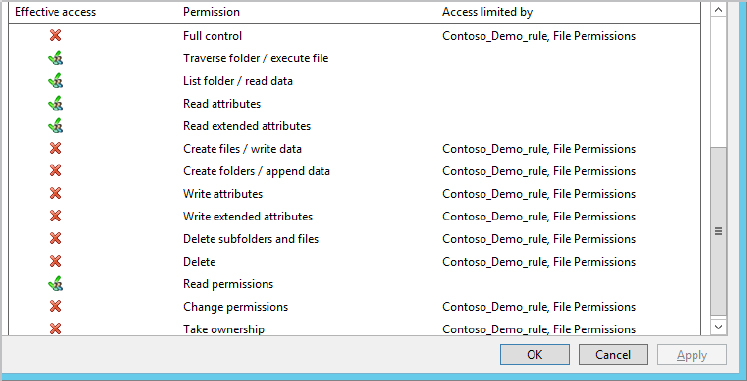
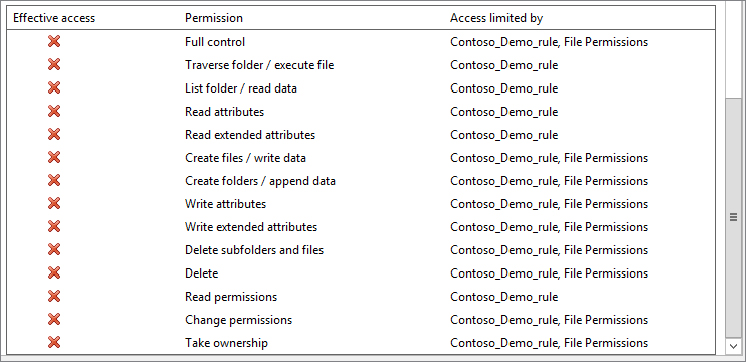
Figure 15.54 Effective access results for Ken
Try it out now on a Windows client, and see if you can access the share. For further fun, change your Department field in Active Directory. Then log off and log on and see if you have access.
On a daily basis in a large enterprise, the number of permissions that are being added and removed by help desk is astonishing. This is a manually intensive task, and it takes time to complete. Windows Server 2012 has introduced access-denied assistance to alleviate the burden and has put the responsibility of access control back on the data owner or requires the data owner at least give relevant information to the help desk to allow them to perform a quick turnaround on the access-denied problem.
Access-denied assistance can be configured in two ways:
First, we are going to show you how to configure it via Group Policy. Later in this chapter when we are dealing with classifications, we will demonstrate its configuration via File Server Resource Manager.
Let’s configure a new GPO for access-denied assistance, which will be applied organization-wide:
 Administrative Templates
Administrative Templates  System
System  Access-Denied Assistance, as shown in Figure 15.55.
Access-Denied Assistance, as shown in Figure 15.55.
Figure 15.55 Group Policy Editor with Access-Denied Assistance selected
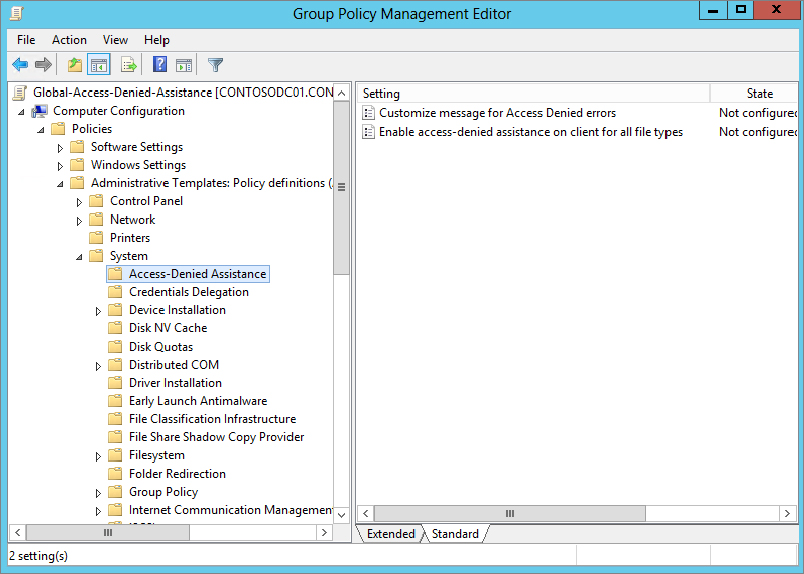
Figure 15.56 “Customize message for Access Denied errors” window
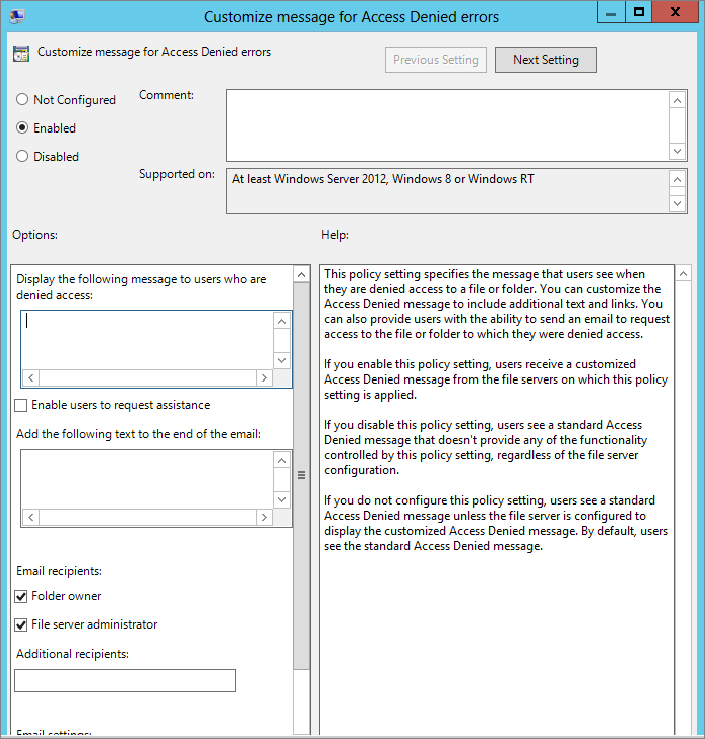
Figure 15.57 Access-denied custom message from client
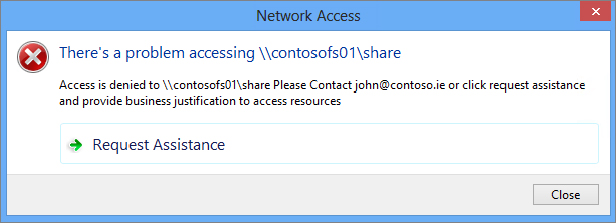
Figure 15.58 Request Assistance window
We have walked you through a basic example of securing data using the Department field. Now we’ll go one step further and secure data based on the office location and the job title. For this example, we are going to use our two users from the previous example, Tom and Ken. Both have become engineers, and Tom is located in the Empire State Building, while Ken is located in the Chrysler Building.
Our share on ContosoFS01 has two subfolders: Accounts and Engineering. We have applied our previous Central Access Policy to the Accounts folder to restrict access to Accounts and HR. We used an “Or” case for this, so if you were in either Accounts or HR, you would get access to the resource. In this case we want to ensure only engineers “And” staff in the Empire State Building get access to the Engineering resources.
Let’s begin. First, we will summarize the steps we have to proceed through:
I would highly recommend trying this before we walk you through the scenario. Need the walk-through? No problem. Because we provided screenshots for the previous sample, we are going to omit them here to provide a little challenge.
First, as per our steps, we are going to create two new claims.
Perform the following steps to create a claim:
 Claim Types.
Claim Types.| Value | Display Name |
| Engineer | Engineer |
| Accountant | Accountant |
| Reception | Reception |
| Director | Director |
Now, using these same steps, you need to create a new claim type of the following office buildings:
It is often the case that the display field in an Active Directory user’s account does not literally map to the attribute you expect. For example, in Figure 15.59 the Office field is listed.
Figure 15.59 Office field in the Active Directory user account properties
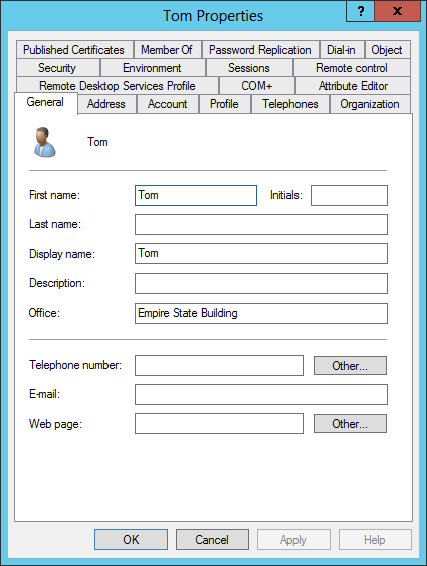
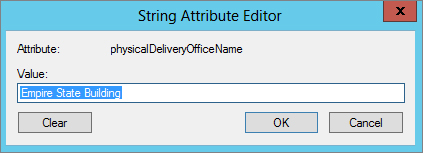
However, there is no Active Directory attribute called Office. The actual Active Directory attribute for the Office field is physicalDeliveryOfficeName; see Figure 15.60.
Figure 15.60 Actual Active Directory attribute for the Office field
Perform the following steps to create the resource property:
 Referenced Resource Property.
Referenced Resource Property.
This step is kind of a trick, because title and physicalDeliverOfficeName are already known attributes. You will find that they already exist in the Global Resource Property List. Verify that they exist before creating your rules.
Perform the following steps to create Central Access rules:
 Central Access Rule.
Central Access Rule.Perform the following steps to create a Central Access Policy:
 Central Access Policy.
Central Access Policy. Policies
Policies  Windows Settings
Windows Settings  Security Settings
Security Settings  File System.
File System.Perform the following steps to apply the policy to the Engineering folder:
Don’t close the window!
Perform the following steps to test with effective access:
The permissions are set as Central Access Policies logical “And” NTFS permissions.
Try it out for yourself.
First, we’ll quickly explain what is meant by classification. I am sure you are all familiar with army movies, and you’ve seen a file being opened with a big stamp on it saying “Top Secret.” This is classification. Simple, eh? Essentially you are being up front with people about the contents of a file. In today’s enterprise, documents can be classified based on what’s important to the company. For example, for a hospital, patient information is highly sensitive and may be classified with the tag “Sensitive.” A common scale consists of three classifications:
It is extremely important to understand the need to classify documents within an enterprise. Simply put: do you really want information leaking to outside the company that could, for example, expose a trade secret, causing irreparable harm to the company?
Classifying documents gives companies a chance to stop this type of data leakage. For example, with the Rights Management Service, which is part of Windows Server, you can detect that a document is top secret using different rules, and you can encrypt its contents or block it from being opened by unauthorized personnel.
The big problem, as you can imagine, is how to classify all the existing documents in an enterprise. Chances are it has not been the practice to write such information in the file’s properties when saving the document. If an enterprise wants to retrofit classification onto their documents, it is a costly job in both time and money.
In Windows Server 2012 you have the ability to automatically classify documents, so you can secure the contents if necessary with RMS or block access with Dynamic Access Control. It is interesting to note that file classification has been available since Windows Server 2008.
It is possible to classify a document manually. In our lab environment under C:\share\accounts we have a file called Finance.rtf.
Figure 15.62 Finance Properties screen
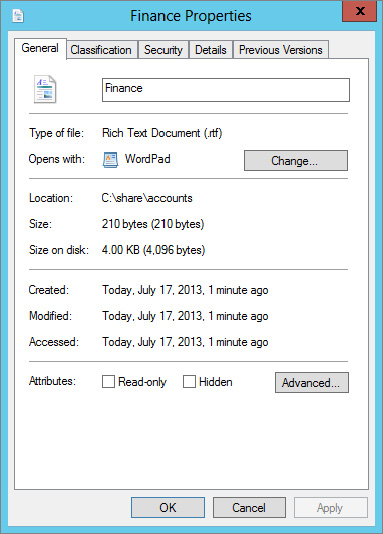
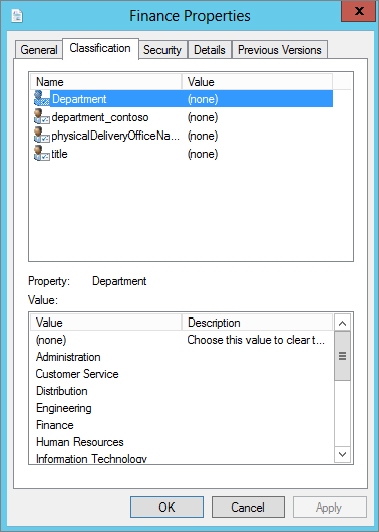
Figure 15.63 Classification tab
As already mentioned, this would be a painful approach if you had to do this to all your documents. Windows Server 2012 includes a tool called File Server Resource Manager (not installed by default), located in Server Manager under Tools.
 Tools
Tools  Click File Server Resource Manager; this will open the MMC, as shown in Figure 15.64.
Click File Server Resource Manager; this will open the MMC, as shown in Figure 15.64.
Figure 15.64 File Server Resource Manager MMC
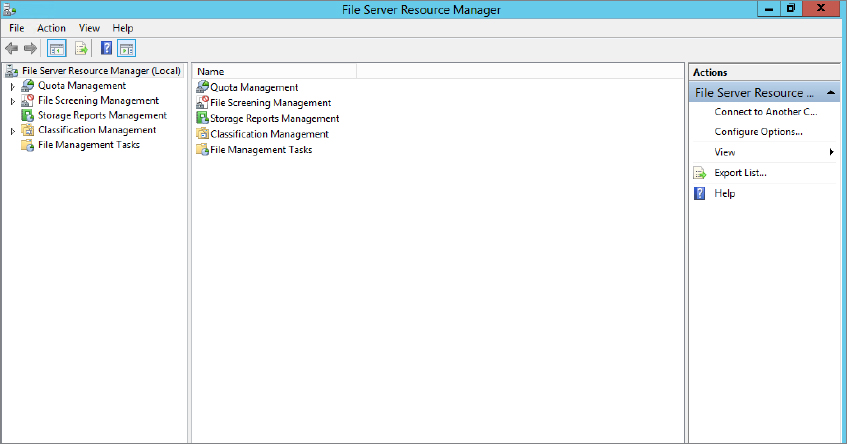
Classification properties can be inherited via Dynamic Access Control or locally set. You can configure Authorization, File Classification, and Folder Management. You can also configure Access-Denied Assistance from here for the local file server only.
Note that you can’t modify items with a scope of Global in this console because they are inherited from DAC.
Classification rules allow you to set up conditions that will automatically classify documents for you. We are going to be diving deeper into this in our example. Over the next few steps we will show you how to create the appropriate rules to allow you to classify your documents and folders. We will walk you through all the steps required and demonstrate how automatic classification works.
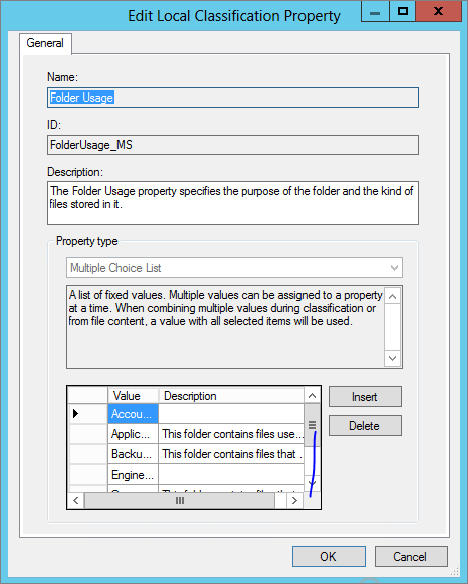
To classify documents automatically you need to create a classification rule. First, to aid in the configuration and explanation of some items later on, you need to map your folders using Folder Usage:
Figure 15.65 File Server Resource Manager showing the Folder Usage property
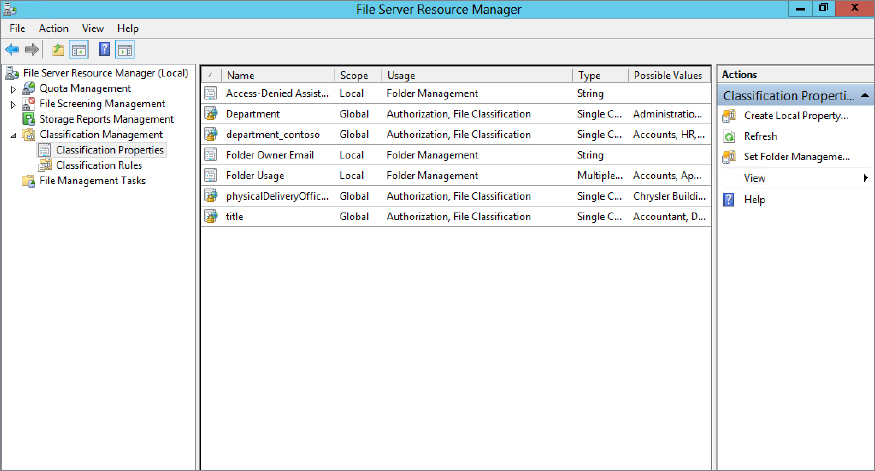
Figure 15.66 Adding values to the Folder Usage property
Now let’s configure our folders:
Figure 15.67 Set Folder Management Properties screen
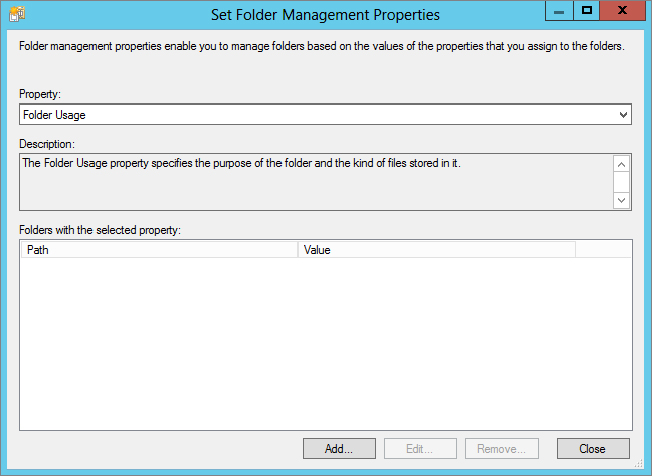
Figure 15.68 Adding a value to Accounts
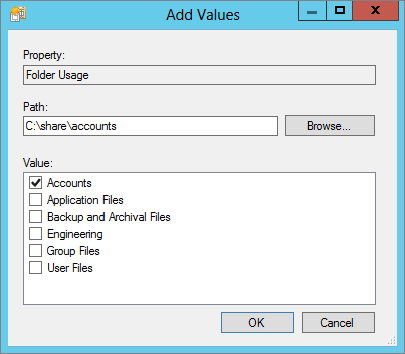
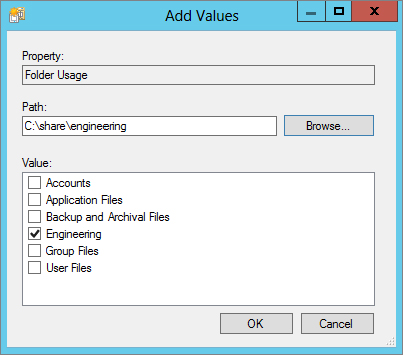
Figure 15.69 Adding a value to Engineering
This work will aid you later when creating your classification rules, because the properties that you have just confirmed will be available for selection during the building of a classification rule.
Figure 15.70 Create Classification Rule
Figure 15.71 Scope classification rule

Figure 15.72 Classification configuration
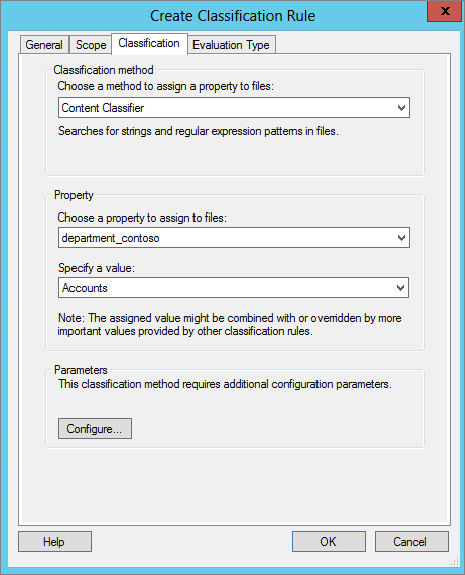
Figure 15.73 Classification Parameters screen
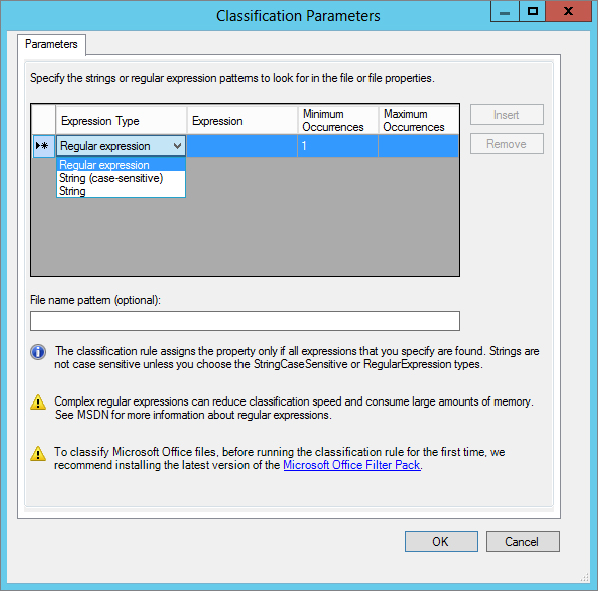
These are explained in the next two sections.
Regular expressions are used to identify patterns in data, similar to the Find option in Notepad, where you can press F3, type in a string to search for, and Find will find it. Regular expressions do the exact same thing. Traditionally, they are used in the programming world or in the telephony world for detecting patterns in data or manipulating telephone numbers. An example is that you can create a regular expression to detect a credit card number.
We are going to provide a quick primer on regular expressions in the next few pages because they are extremely powerful. But first, we are going to show you how to detect a simple string pattern called Finance and how upon detection of the Finance string within a document the regular expression will classify it appropriately:
Figure 15.74 Evaluation Type tab
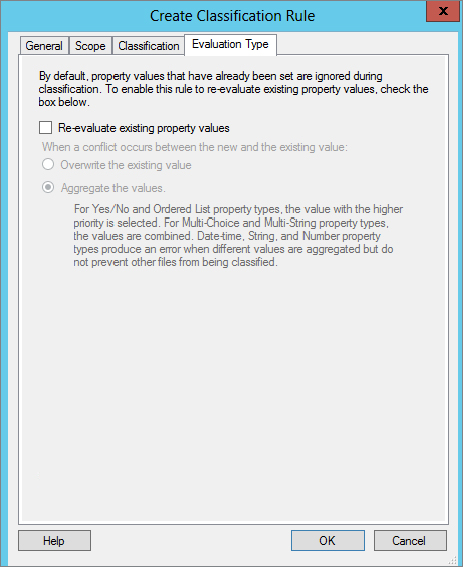
Your classification rule is complete. All you have to do now is either manually run it by selecting the rule, and in the Actions menu click Run Classification Rule or wait for the Task Scheduler to execute it.
When you manually run the classification you are prompted to choose to either run the task in the background or wait for it to complete, as shown in Figure 15.75.
Figure 15.75 Options for manually running the classification with all rules
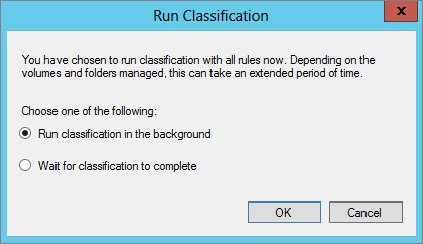
We’ll choose the automatic option, which allows the Task Scheduler to execute the task on a scheduled basis. First, however, we need to configure the options for automatic file classification:
Figure 15.76 Configure Options for automatic file classification
Figure 15.77 Options to configure for scheduling automatic file classification
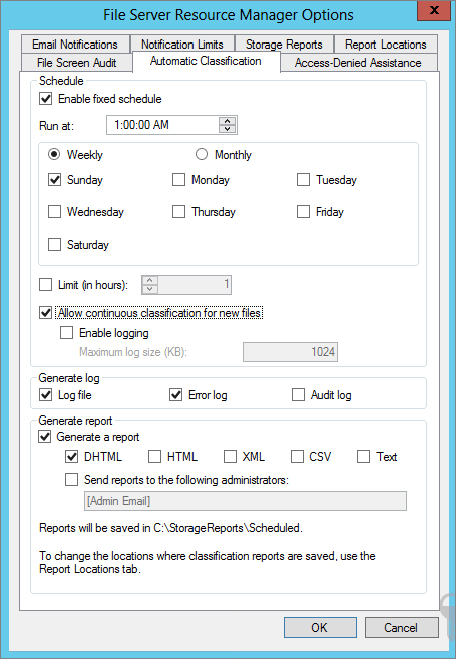
You can verify that the schedule has been set up in the Task Scheduler:
 Microsoft
Microsoft  Windows
Windows  File Server Resource Manager.
File Server Resource Manager.
Since you want to run this right away and not wait until 1:00 a.m., you will want to run the manual classification and select Complete as a background task, but not yet.
Figure 15.78 Contents of Private Data.rtf
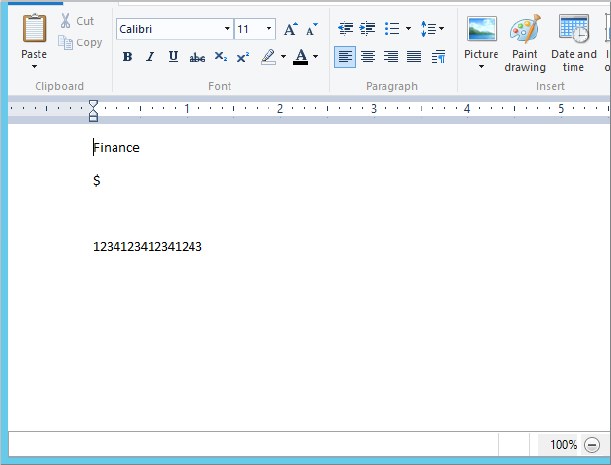
Figure 15.79 Private Data.rtf classification
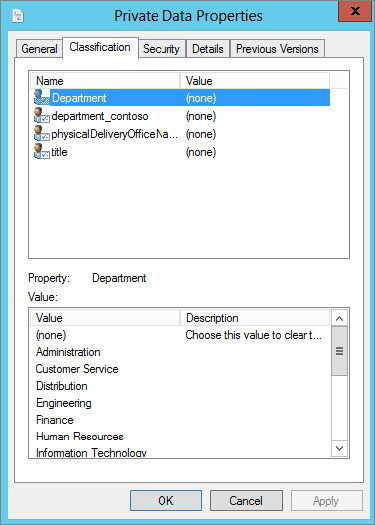
Figure 15.80 Private Data.rtf classification set
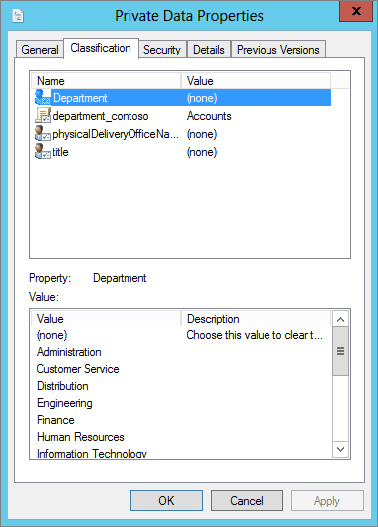
Before you start thinking that I am mad and that I also included the Engineering folder, let’s check its contents and file classification. In our lab we included a file under C:\share\engineering called Engineer Scope.rtf, and as you can see in Figure 15.81, even after the File Classification Wizard has run, the classification of the file is not set. Why? Because we set no rules specifically for it.
Figure 15.81 Engineer Scope.rtf classification

Try out different combinations and create new rules yourself now to really embed the principles of what we have covered so far.
I promised to give you a quick demonstration of regular expressions. This is something you should ask experienced programmers or telephony engineers about because they are wizards at this stuff and usually have a great ability to construct exceptionally complex but useful expressions.
Also, in your favorite search engine search for “Regular Expression Cheat Sheets.” There are a few really cool links available that you can use as a reference.
As with most things, regular expressions won’t make sense until you use them for something. So let’s look at a basic example. Say you want to detect a credit card number. First, you should look at what characteristics a credit card number has, and to my thinking the simplest one to start with is that it always has 12 numbers. We’ll start with that.
In order to detect a 12-digit number with regular expressions you would have a query like this:
"\d{12}"If you break this down, very simply the \d means “detect a digit” and the {12} means “exactly 12 characters long.”
Another way of writing this if the credit card number is stored like 1234-1234-1234-1234 is:
"\d{4}-\d{4}-\d{4}-\d{4}"Simple, eh! Hopefully you won’t have too many 12-digit numbers that are not credit cards in your environment that get classified unnecessarily with this basic rule. However, we can get a bit more focused. For example, let’s say Visa cards start with the number 4 and then use a combination or 11 other digits. What would the regular expression for that look like?
"\d[4]{11}"Here it is in standard credit card number format:
"{\d[4]{3}-\d{4}-\d{4}-{\d{4}"Now let’s look at a different example. Two things that come to mind that companies often do not want leaked to the public are intellectual property and payroll information. Hopefully you agree! To my mind these pieces of information need to be protected, and on that note let’s build another regular expression. We will also reuse the following example later on when integrating this into our Dynamic Access Control configuration.
But first, what would a regular expression look for detecting the words intellectual property?
It can be as simple as this: "intellectual.*property"
Quick test: What do you think it might look like for payroll?
Think of a few more examples, like wages or pensions.
Here are a few useful links to regular expressions to get you going:
http://msdn.microsoft.com/en-us/library/ae5bf541(v=vs.80).aspx
http://www.solmetra.com/scripts/regex/index.php
http://www.regular-expressions.info/reference.html
http://www.cheatography.com/davechild/cheat-sheets/regular-expressions/
Been able to detect patterns like this and even more complex ones can give you great flexibility in the enterprise to classify data in the correct way so that you can secure it automatically with a range of other tools like Rights Management Server.
For the final piece of this chapter let’s examine a real example you’ll come across in the workplace. Most businesses now deal with credit card numbers at some point. And it is the company’s responsibility to ensure that this data is secure. Hopefully these numbers are stored in encrypted databases in the real world, but in our example company, Contoso, they have been storing them in a Word document.
We need to safeguard not only the company but also the information so it isn’t leaked. We don’t want engineers logging on to the file share and being able to copy the credit card number file. That would be disastrous.
With all this in mind, here’s what we are going to do:
Okay, let’s go. First, create the three documents you need:
 Rich Text Document; see Figure 15.82.
Rich Text Document; see Figure 15.82.
Figure 15.82 Creating a rich text document
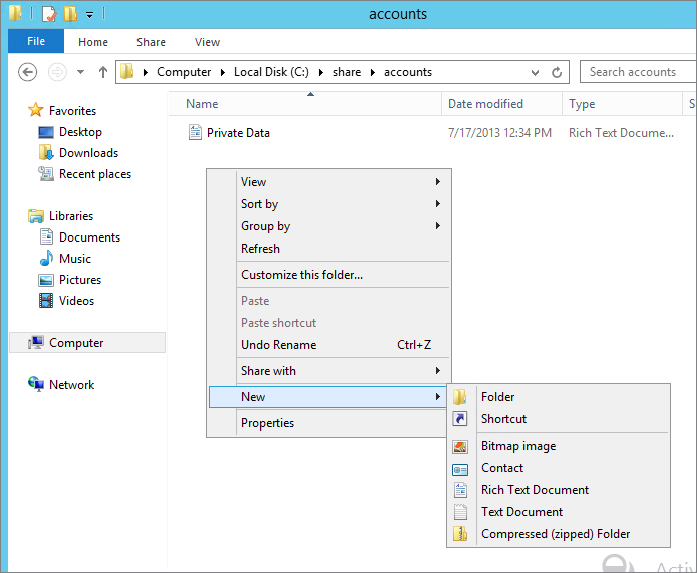
Next, let’s create the classification rules to automatically classify the documents:

Your file-classification rules are in place and you have now verified that they work. It would make sense now to build a policy so that only Accounts or HR people can access these types of documents.
Prep time first! To ensure this is done correctly and you understand the flow, take some time to remove all Central Access Policies already applied to your folder:
 Security Advanced
Security Advanced  Central Policy
Central Policy  Change
Change  No Central Policy Applied, and click OK.
No Central Policy Applied, and click OK.Now you’ll need to re-secure your data with Central Access Policies:
 Central Access Rules.
Central Access Rules. Central Access Rules.
Central Access Rules.Figure 15.83 Resource targeting
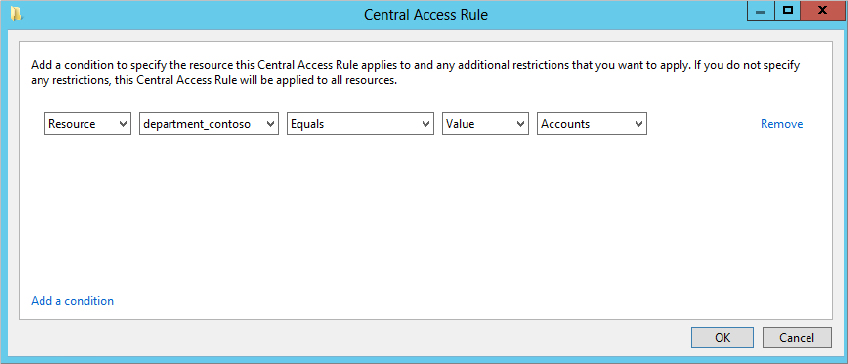
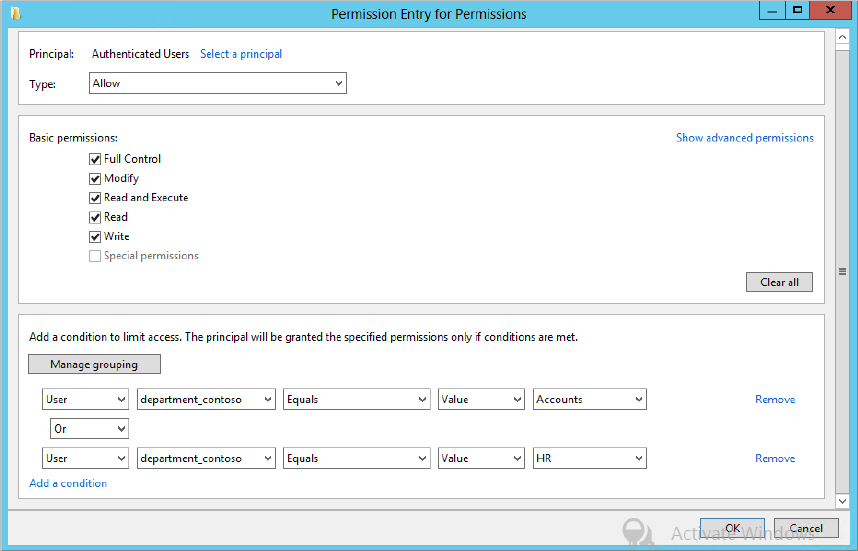
Now you need to set the permissions; you want only HR and Accounts staff to have Full Control over the documents:
Figure 15.84 Permissions and condition logic
Next, you need to create a Central Access Policy so you can then deploy this to your file servers:
 Central Access Policies.
Central Access Policies. Windows Settings
Windows Settings  Security Settings
Security Settings  File System
File System  Central Access Policy.
Central Access Policy.