• Control program. See Omega Programming- Universal Function Codes for internal system codes for body programs. Sometimes these body programs are filed with a combination of hebrew and zodiac signs. Greek letters are also file no.s of at times of body programs. Rivers of blood -circulation control program. This program totally controls the circulatory system. The victim may think they are losing lots of blood & go into heart failure. Octopus- strangulation suicide program The internal defenses consists in part of body programs that are triggered if the Mind-controlled slave steps out of line. Here is a good list of some of these body programs each of which has its own codes:
Auditory problems, Blood flow/circulation, Burning as if on fire, Digestive failure, Headaches-split brain, Heart failure, Histamine production, Optic problems, Respiratory failure, Sleep deprivation, Sleeping program, and Temperature change. The suicide programs that can go off include Armageddon, Clowns cutting, Cutter program “Pain is Love”, Disembowelment, Drug overdose, Gethsemane, “Hypnosleep”,
Injection of bleach (poison), Octopus, Red Sea, Shooting Programs (shotgun, russian roulette, shooting family, etc.), War in the Heavens & Wrecking the car. Along with the suicide programs that can be triggered are programs that jerk the victim's mind every which way, which include: Bee Stinging Program (put in by placing the drugged victim being near large swarms of bees humming & then letting a bee(s) sting the victim), Busy Cleaning Program, Crazy program, Flooding (from Atlantis), Isolate & Hibernate Program, Memory Erasure Program, Pain Programming, Paper Doll Program, Protection by trance, Revolving switching, Scrambling Program, and re-Structuring Programming, Tumbleweed program, Waterjar Shaking program (Ahab stomping the grapes Bible-based program making mush out of the brain.)
Cutting programs are often hidden behind the Bee Swarming program. Alpha and Omega is a strong program. Sometimes saying “ALPHA & OMEGA” helps alleviate headaches.
JDNA (This uses a lot of number codes.) This is a double-helix which is used as an elevator shaft running down through a system. Numbers are used and the names of cities to go down the elevator shafts. This programming is said to be done in hospitals.
JCard Codes -- Regular playing cards have developed from the occult Tarot cards. The four suits correspond to magick, the spades mean the power from the spear of destruction, the diamond means is a double pyramid or demonic power of wealth, and the club is a clover meaning fortune and fate, and the heart means devotion and loyalty. The four suits work well in programming because anything that is broken down in 4's or a multiple of 4 can be coded with cards. Anything that can be broken down into 12's or 13's can be given cards too. Since clocks work off of 12's, card codes work well with clocks. The suits can denote seasons. With Jokers one gets 13 cards per suit with four suits gives 365 unique symbols to denote the days of the year.
Dominos can also be used on a base 13 code system. The blank will equal 13.
^Carousel System. There is a back side to enter the Carousel.
J Carrier Pigeon (slave's who send coded or uncoded messages) and their contact codes
Birds used for contacts. That is birds in cages are often used as a sign of a meeting place. The contact would say “What did the bird say?” or “A little bird told me ...,Then the courier pigeon delivers her message.
“I've come a long long way to see you. words to say by System to John or to person to be met. There is an endless variety of contact phrases to indicate that the right person has met the right person.
Sample Code for passing drugs-“RHINESTONE COWBOY” to which the response from the slave would be “I'M NOT A COWBOY, I'M A COWGIRL.”
Emerald ear rings have been the visual signal to customs agents to allow a person carrying drugs through customs. (SEE D. DELTA for deeper Carrier Pigeon codes.)
May need a special ring worn by and turned by the handler.
CSP94OYP587 -- code to designate a flower tieing 3 generations. UMBRELLA PROGRAM CODE -- “R x 4 x 5Y58876”
1 - Aries - diamond
2 - Gemini - topaz
3 - Cancer - cat's eye
4 - Leo - ruby
5 - Virgo - emerald
6 - Libra - opal
7 - Scorpio - amethyst
8 - Sagittarius - turquoise
9 - Capricorn - black onyx
10 - Aquarius - crystal
11 - Pisces - sapphire
“STAND IN ORDER ACCORDING TO RANK AND SERIAL NO.”- part of a stacking command to get alters in sequence together to work on them. Dominoes and cards are used as part of the stacking cues.
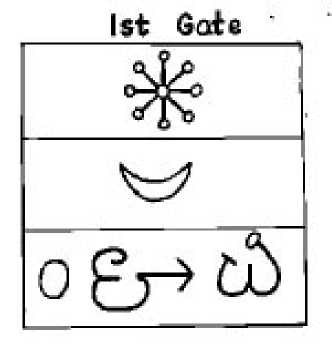
Dr. Star's Programming which places Pentegrams into people uses Sigils as codes--the occult symbols for the various demons, along with a color, a gate, and a number form a complete code.
For example, 1st Gate is the god Nanna, #30, color-SILVER, LADDER OF LIGHTS, GOD OF THE MOON. (see Illustration)

To access a System the abusers often have an object as part of the pickup code, such as a set of car keys, a special coin token, a business card, jewelry, or certain clothes or packages. A Popper liquor drink is knocked 3 times on the table when it is served. (Who would be the wiser that three knocks is an access code?)
•word matrices
A word-matrix code is where the victim is given two lists of words and then each word on the left list is paired with a word on the right list to form a code.
Randy Noblitt, a therapist, gave an example of a basic pattern for a Word-Matrix. And this is simply quoted from his example to give the reader an idea.
started
between
endless
throughout
get out
over
fun
win
first
form
beginning
tonight
thorough xenophobe
thoughts
beginning
forever
trepidation
beneath
the end
execute
lose
then
benign
end
last morning
B. BETA (sexual)
J SEXUAL ALTERS -- most of the following codes are for deep sexual alters. In Illuminati Systems these are called Beta alters, in CIA systems they create Beta models whose primary function is to provide sex, usually perverted sex and S&M for the perverts who run our secret government and visible government. BETA models are those who are primary job is sexual, such as service as a Presidential Model (sex slave for a President). These System models are numbered BETA 1, BETA 2...BETA 601, etc
Domino codes for spinners can be 6-3, 6-4, 8-4, 8-5, 10-5, 10-6, 12-7,
12-8. The 13th kitten then would be left blank. Spinner dominos have spinner kittens off of them, when a spinner domino code is used. In this case 6-2 could take you to the Beta level.
“10 LITTLE INDIANS, 9 LITTLE INDIANS...”, “1 LITTLE, 2 LITTLE.. .“--assoc. w/ morse code-call back telephone no.s. “3 LITTLE KITTENS HAVE LOST THEIR MITTENS...” -The Kitten alters have stepped outside of their programming and need fixed by the Master.
“Hotel California” means a place to have sexual gratification.
Stroking under chin along with “HAVE A BALL TON IGHT” (Cinderella programming) Stroking under the chin along with “PURR FOR ME KITTEN.” Magic shoes or red slippers are used to switch to get specific sexual alters. The slippers are clicked 3x to get deeper sexual alters.
“COME HERE MY KITTEN, AND LET ME PET YOU. PURR FOR ME NOW. ..THAT'S A FLUFFY KITTEN. PURR DEEP.” “COME HERE LITTLE ONE.”--call for young sexual alter
“PASSION” used 3x with other words as a sexual trigger, such as “SHOW ME YOUR PASSION.” Passion is a strong program word for sex.
“RED DOT, SPIN SPIN SPIN, BECOME ANOTHER PERSON.” this is said to a mother kitten before she is told which spin kitten to get from her litter. It is a preparatory command meaning “call your spinner”.
Spin Kittens “WE GOTTA GET DRESSED.. .IN 5 MINUTES” along with being spun produces specific sexual kitten.
9 lives of kittens -- means 9 sexual alters taken in sequence. When spun in a counterclockwise fashion, the sexual menu is from 1 to 9. With 3 & 5 being oral sex. “Heat of hell” are used as trigger words in this programming. The 10th revolution is to beg to be whipped. “TURN AROUND 10” “SPIN FOR ME.” The heat of hell ignites after the 6th spin.
“RIDE PONIES”--means to do sex for both eng. & ger. slaves; “PLAY HORSEY--sexual games; “MOUNTING A HORSE”--[obvious] “CAT NAP” -sex; “CAT NIP -- cocaine
Tweedle Dee and Tweedle Dum --S&M programs involving mirror image alters. Not to be confused with Humpty Dumpty self-destruct program.
“SIX IS SEX. SEVEN IS HEAVEN. EIGHT IS GREAT. NINE YOUR MINE.”--This means to fall under the master submission, has sexual overtones.
“ ITSY BITSY BOOB” -- access code pertaining to Betty Boob programming (which is a certain type of female behavior).
BETA ONE MARY A=1, B=2, C=3, D=4 “BETA TWO MARY A=4, B=3, C=2, D=1”
“BETA THREE MARY A=3, B=4, C=1, D=2”
Then these might be said in combination “3412 4321 1234” (x3)
An amer. sys. used w/ Latin Amer. may have a Beta alter activated by the movement of 2 small Mexican flags & a code word in spanish “USTA CA-NATA” (cream).
C. CHI (return to cult)
Chi programming uses a lot of idiosyncratic phrases, and little ditties. Some of the nursery rhymes listed in the song section will be Chi programming. Some of the Chi programming has been listed in the Alpha programming section.
D. Delta (assassination)
JDelta alters --are activated to kill by the following three things: seeing specific clothing, items held in a persons hand, and particular words. Since these items would specific for a particular murder there is no particular specifics that can be given.
^Courier Pigeon -- Alters (In Illuminati systems--these are Delta-Beta alters). “FLOCK” --word meaning the stable of carrier pigeons of DIA
To turn a Genie free, pop a cork: “TURN YOUR GENIE FREE...POP A CORK.” An internal controller must activate the umbrella or genie bottle pop the cork program to release a delta or delta-beta alter.
“YOUR WISH IS MY COMMAND” I Dream of Jeannie Programming
“YOU-ARE-WHAT-YOU-READ” passbook program. Programming to remember bank numbers and other specific numbers.
“I SENT A MESSAGE IN A BOTTLE.”
Distinctive jewelry & clothes. Emerald ear rings used as a signal to others that a message was being carried. Emeralds mean drugs, rubies mean prostitution, diamonds (rhinestones) presidential model work. Red, White & Blue worn sometimes by presidential models. High level reporting alters forget their messages with “REFILE # #, (name of alter).” Some Systems have one name w/ several different numbers attached to indicate alters within one area and purpose. Sergeant 1, up to Sergeant 60. Or say “Access 1143 Marcy” & then other Marcys are numbered with other numbers. Spaceships & flags are assoc. w/ Sargeant alters.
Delta Black Widow alters have a web, fangs, poison, eggs, and silk strand connectors. Viper is the demon associated with Black Widows, and they are programmed to re-connect their strands if all of the connectors are not taken out.
Index finger pointed at head means russian roulette.
E. EPSILON (animal alters)
These codes aren't known. One method that may be used, for instance, is for the Raven alters who are to tear the body's flesh, the story of Noah's ark where he sent the Raven out will be paired with the word TWIG, and a code formed from TWIG. There are some alters which are to actually act like animals, and their codes somehow tie in with what they are.
F. OMEGA (internal computers)
The Omega programming works along with an Executive Control Board (or Grand Druid Council) and Internal programmers. The Executive Control Board is associated with both numbers of the clock, and precious gems and metals such as “9 O'CLOCK GOLD”. The Beast computer can be accessed with Scripture triggers associated with the Vision of Daniel of the Beast, and its ten toes. The Ten Toes are
important part of the code in some models.
Key manual -- 33123113211
Program computer -- 22133113332 function computer 11123132221 Ren computer -- 13321321332-55434232312 L\S 55434232312 reenlist Reprogram no.s -- 2231231; 4432312; 33231223
An input code is 666fff666fff666 the reverse of this code is F6F6F6F6F6F6F6F6F6F6F6. One victim's computer ran on code “WAR GAME”. Some Beast computers have 666 666 666 as an access code and 999 999 999 as a beast back out and close out code. There are various computers--one on each level. These have some standard codes and some individual codes.
UNIVERSAL FUNCTION CODES -- COMPUTER CODE -- 5543423231 2 which hold the following codes:

abduction
4511321


anger 4213261
assignment coordinator 1613212







assassination bank of lies blindness brain disorder body gesture body functions call back ritual
5332135
3124532
2566553
6325512
1332221
4311322
6664113
|
child control |
3214441 |
|
circle in fields |
3332241 |
|
confusion |
6643252 |
|
control |
4321341 |
|
deaf |
3324553 |
|
death |
1451621 |
|
denial |
2311444 |
|
despair |
3223412 |
|
distortion |
6233322 |
|
disorder of bones |
4561321 |
|
disorder of breathing |
5532111 |
|
disorder of eating |
3342136 |
|
division |
3211652 |
|
false memories |
3314532 |
|
fear |
2665132 |
|
fleeing |
5613354 |
|
game playing |
1561321 |
|
guilt |
4321231 |
|
hatefulness |
5331241 |
|
hopelessness 1 |
112364 |
|
illness |
1566432 |
|
infiltration |
2231335 |
|
insanity |
2144312 |
|
inside reporters |
1133265 |
|
J loyalty to group |
3364112 |
|
J mute |
2213541 |
|
J murder |
3221456 |
|
J nonsense |
2665443 |
|
J outside reporters |
1132256 |
|
J reprogram others |
4555643 |
|
J reprogram self |
1133432 |
|
J respond to triggers |
4441221 |
|
J retardation s- |
1314555 |
|
J m- |
1314556 |
|
J sabotage |
1135461 |
|
J seduction |
2134121 |
|
J self body harm |
3321343 |
|
J sex |
2116652 |
|
J shame |
3122115 |
|
J suicide |
3113246 |
|
J trigger |
1324652 |
|
J trigger others |
4442211 |
|
J zombie |
3321556 |
Under each of these codes, other codes may be attached. For instance, under Body Gestures, the following functions are coded and a sample coding scheme would look like this:
J talk verbally 3456343
J touch chest 2322132
J touch hair 3323221
J touch mouth 5434232
J touch nose 5443232
Rainbow an alter which speaks only in rhymes. Ribbons are in a box with Rainbow. A ribbon might be accessed by several slaps on the face and “Rubicon 2,4,6,8...” (3x)
J Hickory Dickory Dock rhyme is associated with the vortex which is tied to turning the system and also to some death alters.
J Dominoes set off flooding programs to overload the person.
J Program numbers on some slaves are put in by touching the third eye with the index finger and speaking the number.
G. GAMMA (demonology)
In Satan's realm, demons are fathered or split off in families like alters are. There will be a Moloch number 101, and a Moloch 10,321. The victim has alters which are numbered such as Sally 1 and Sally 10. For a better understanding of this area of programming see Chapter 10 section I. Gamma Programming includes all the demonic activity. In this section one can add the Kabballa's Tree of Life which has alphabet codes, back up programs to regenerate, associated with Greenbaum or Greentree. In the Illuminati slaves, the deeper parts of their system are ritual and the demonology pertains to the various rituals that are done. The following is a sampling of Illuminati rituals. The blood rituals are used to attach demons to possess alters in a particular way. These rituals can't be separated from the programming. They are part of the programming.
J Assembling of the Quarter Regents
J Beltaine -- with hunts of slaves, fire festivals, and blood rituals J Bride of Satan Ceremony -- (Mar. 24)
J Demon revels J Drawing down the moon J Druid Feast Day -- on Jan. 1
J Duels to the death -- like gladiators where the heart is cut out and eaten
J The Grail Mass
J Grand Climax -- human sacrifice & sex rituals
J Invocation of Hecate as Crone
J Lammas sabbat -- where a female is sacrificed
J Pathworking -- (done before 16 with Cabalistic Tree of Life pathways.)
J Rite of Deification
J Rod of Light ceremony -- (consists of text from Cabala, black candles, ram's horn blown, and victim's mother's name sounded)
J Sealing ceremony -- at 19 yrs. for Mothers of Darkness level
J Secret ceremony -- where people paint their faces half black and half white.
J Sister of Light rebirthing water ceremony -- (victim is bound and then pulled from water and wrapped up in linen, and a green branch is place on the chest)
J St. Agnes Eve
J St. Bartholomew's Day
J St. Walpurgis
J Summer Soltstice Orgy
For those who are not familiar with occult terms the following are ritual items: Paten (the holy dish), Athame or Glaive (the knife used to sacrifice with), the wand or sceptre (a ornamental staff which represents authority & usually has an electric shock), and the censer (to distribute burning fragrance).
H. HYPNOTIC INDUCTIONS
‘‘Kaleidoscope eyes'' -- used in hypnotic induction and spinning “20, 19, 18, 17, 16, 15, 14, 13,...1”
For many slaves the sign of satan done with the fingers puts them into a trance, and deeper alters come out.
“100, 91,82, 73, 64, 55, 46, 37, 28, 19, 10, 1”
Touching the head in a particular fashion is done. ‘‘DEEPER AND DEEPER AND DEEPER DEEPER AND DEEPER AND DEEPER, DOWN, DOWN, DOWN, INTO THE DEEP, DARK VELVETY MIST, DEEPER AND DEEPER AND DEEPER.”
“DEEP, DEEP, DEEP, SLEEP, SLEEP, SHEEP, SHEEP, SHEEP” SLEEP,
“YOU'RE BEAUTY WARMS MY EMBERS. SEE THEM GLOWING DEEP WITHIN THE DARKNESS OF MY EYES... IGNITING INTO FLAME... BLACK FLAME.”
Seeing a Hand of Glory (severed left hand) will induct people into Peter Pan programming. (Books describing the occult use of the Hand of Glory in Ireland go back to 1830. It is an ancient practice. Baring Gould's book Curious Myths of the Middle Ages describes the recipe for using the hand of glory as a gruesome lantern during the witchcraft of the Middle Ages.)
“I AM THE SAND MAN, AND BLOWSAND IN YOUR EYES” said while simultaneously moving the hand over the face to create the illusion of placing sand in the eyes.
3-2-1,3-2-1,2-1-1, 1-2, 1, You are now relaxed.
Lights, in certain colors and sequences, have been used to trance alters out, for instance a flashing red light may trance certain alters out. Tunnels were used as a powerful hypnotic suggestion. Bear in mind, that people induct a. when phys. or mentally relaxed, b. when their senses are overloaded or sens. deprivation, c. when their equilibrium is disturbed, d. their motion is restricted or e. their eyes are fixated on something.
Main link to a System's programs to ALEX coded 44334223112. Scramble code to ALEX is 34424313221. Individual code to ALEX = 55434232312. Link to JANUS coded 3323432123. Report back- X441062F
Main JANUS tracking/reprogramming code-JAN US 9341 00569XXY99632 [x3]; its back up code X44420-61F. (There is a Janis 2 computer at 666 Connecticut Ave. Washington, D.C. Disinformation by the Network is that the PACER computer equipment is called Janus/Janis). Main AMBASSADOR code 67302986ZZ9861 (suicide/fire) sub codes- Fire 97643F4200L; Cut 97642C42DIL L ; Suicide 9762354202L; towards violence 97613V4203L
Main EMPEROR - [dot, dot, dot] 79622109MM861 1
Most slaves have end-time programming. When a slave is called in with end-time programming they have pages upon pages of coded messages. A number of Monarch slaves have been de-programmed enough that they began accessing and spewing out pages and pages of these activation codes. Part of a sample of one of these is as follows:
'O “ISRAEL IS RISING
'O ACTIVATE 366 UNITED NATIONS
'O 900 BLUE BIRD PILOTS RISE
NATIONS IN PLACE
RED CHINA CALL BACK
'O COUNT DOWN, ACTIVATE ALEX
3.7 LC :o 94
:0 CIRCLE FARMS AROUND THE SQUARE BRITISH SOLDIERS RISE J MOUNTAIN GOAT COME 'O EASTSIDE OF PEAK 'O 39 ACTIVATE 'O 52 ACTIVATE 'O 42 ACTIVATE RED CHINA RISE
1.7 ACTIVATE
THE HOUR COMES, A. C. SON J ACTIVATE AFRICA 'O ARISE IN NUMBERS OF 90...”
A team leader will have a down line of around 4 people--which are coded red ray, yellow ray, green ray, blue ray. When the activation code hits a slave team leader during the end times, they will in turn activate their people, who in turn will have people who are team leaders and have a down line. At least two false callback alarms will be sounded (tested) before the real one.
J. THETA (psychic warfare)
Capt'n or Cap'n (captain) represents the programmer in Peter Pan programming. Tinkerbelle is a young alter created under Peter Pan programming.
‘TRANCE DIMENSIONAL TRAVEL RIGHT FROM YOUR OWN BACKYARD. THE DIMENSIONS OF YOUR PYRAMID ARE TO BE 9 BYE 9 BYE 9 BYE.”
Alien programming by NWO (also involves Peter Pan programming)
“RIDE THE LIGHT” -Peter Pan programming meaning to go into hypnotic induction attached to a light that is seen when given a high voltage shock. This is given to make experiences seem like in another dimension.
CROSS PROGRAMMING -- (With for instance a mother and a daughter team)
Two seals are placed on this cross programming, a “seal of cover” and a “seal of rain”
Code: mother - [minus] mother = 3/4 -- daughter holds 1/4 daughter - [minus] mother 1/4 -- daughter holds 3/4
Teams will be given code words for each alter who is part of a 2-System team. One System may serve as a father figure to the other System. Teams will be trauma and sexually bonded, as well as having mirror images with each others names. A leader will have an upline and a downline for the colored rays. A leader will call the different colored rays, to activate their programming.
An Illuminati team ritual to create oneness & open their team boxes up to work together (Illuminati twinning ritual): the team kneels face to face, draws a magical circle on the ground, joins Delta team hands forming a clasp ring. (Blue is associated with this.) then they all say, “Star within a star, Circle within a circle, Mind within a mind, body within a body, Soul within a soul.” Then the team places Palm, their hands
Palm to Palm, and then speaks 4 times, “Bone to Bone, flesh to flesh, Spirit to Spirit, Forever together - never apart.”
Then a 5 pointed star is traced in the air. To close the Delta team twinning box, the reverse is done. Then other things are to be said in the joining and opening ritual. A double deck of cards is used to program an Illuminati team of “twins”. One type of Criss-cross programming involves 1. a flower, 2. the stem, & 3 the root. The root involves blood sacrifices. This programming ties two generations together such as mother -[minus] daughter.
Songs & Nursery Rhymes Used As Triggers (note all of these songs have been used on other slaves too.) Songs with Monarch programming meaning & access parts soliciting behavior or thinking include:
J Brahm's Lullaby
J Hickory, Dickory Dock (flips the system)
J “Hickory, Dickory Dock, The Mouse Ran up the Clock [computer], the clock struck one [time for system rotation], The Mouse ran down, Hickory Dickory Dock.” “INTO THE MOUTH [vortex] RUNS THE MOUSE, AND FLIPS THE HOUSE [turns the system over).
J Froggy Went a Courtin' He did Ride
J Hickory, Dickory Dock
J I had a little pony
J I'm in Love With a Big Blue Frog
J Jack and Jill
J Mary Had a Little Lamb (call to ritual connotation)
J Tones of “Mary had a little Iamb” or other telephone created tones, such as high pitched noises to call people to meetings.
J Mary Mary Quite Contrary (reminds the slave that abusers are all-seeing)
J Old King Cole (Old King Cole was a merry old soul, ... he'd call for his masters 3 [the 3 programmers])
J Peter, Peter Pumpkin Eater
J Puss in Boots (this story is porn programming)
J Ring Around the Rosy
J Ten Little Monkeys Jumping on the Bed
J Three Blind Mice (omega programming connotation with hour glass)
J Twinkle, Twinkle Little Star (Sometimes associated with “I'm dead.”)
SONGS (Most of the Beatles' songs were used for programming. Charles Manson was programmed with Beatles' music. The programmers know ahead of time what are going to be the next hits, and they regularly call in slaves and hypnotically make the lyrics to be cues for the slaves before the music comes out. For instance, the lyrics of “Ain't that a Shame” will make certain alters angry. For another slave the lyrics “Everything is relative, in its own way” reminds the person of the cult family & obedience.) -J Angie (popular song for programming)
J A Mighty Fortress is Our God J Back in Black Blue Velvet 'O Butterfly
J The Candyman Can (Candyman represents drug use for Monarchs, plus other things.)
J CHRISTMAS CAROLS (Christmas carols were used a lot on Monarchs.)
J Country Roads song with the programmed meaning take me [the
slave] “home” to a meeting site.
J Crazy (to reaffirm loyalty to the master)
J Deja Vu
J Die Walkure
J Fire and Rain
J Frere Jacques (Catholic “Father John”, sexual abuse connotation)
J Get Me A Ticket on a Fast Train (substitute “master” for “baby” in song)
J Grandma's Feather Bed
J Ghost Riders
J Green Green Grass of Home (go home program, slave is not happy 'til they go home to green fields
J Greensleves
J Hallelujah chorus (many Christian songs like this one are played while the victim is tortured.)
J Handel's Messiah
J Have Thine Own Way Lord (“thou art the potter, I am the clay, mold me & make me...” III. Charismatic slave programming.)
J Heartache Tonight (song used to announce a ritual over the radio)
J Hotel California (sexual/ritual connotation, the song says, “go to the chamber of the Master's Feast, We are programmed to receive.” This song also tells the story of how LaVey started the Church of Satan in 1966.)
J I Surrender All
J Imagine (John Lennon presents the New Age script for people to be “nowhere people.”)
J John Brown's Body
J Lucy In the Sky with Diamonds
Little Red Riding Hood (song played with hunts of slaves)
J Mary was an only child (from Art Garfunkel's Angel Claire album)
J Moon River
J Over the Rainbow (obvious Wizard of Oz programming)
J “Playing with the Queen of Hearts, knowing that it really smarts, the Joker is the only fool who'll do anything with you” (reinforces the warning not to play (tamper) with the programming. The Queen of Hearts is the emergency Mayday signal to a handler. To play with this will really smart-hurt.
National Anthem No More Mr. Nice Guy Revolution 9
Rivers of Dreams (by Billy Joel. words are about “walking in the dark, going through a river.. .turn on the light on your internal world.”
Satin Sheets
She's Leaving Home
Sins of the Fathers
Southern Nights (loyalty to the programs -- the leaves and trees) Stairway to Heaven
Teddy Bear (Programmer, helpless teddy bear slave connotation) Tennessee Waltz (handler is “forced” to prostitute slave)
The Blood Will Never Lose Its Power
Tom Dooley (suicide, “hang down your head Tom Dooley, hang down your and...)
Victim of Love
“When you wish upon a star” song used for programming.
White Rabbit (Alice In Wonderland Theme -- made into a triggering Karaoke CD.)
J Wooden Heart
J Yellow Submarine (drug connotation)
O. ZETA (snuff films)
Zeta is the sixth letter, and it's ancient meaning was a sacrifice.
These codes are purely a representative model-not any particular real system. The overall system code at times consists of [birthdate + programming site codes + birth order + number of generations family
was in the Illuminati.] For our hypothetical system Mary we have the hypothetical system code of: 6-13-51- 14 -02- 12. In order to give the codes for a hypothetical alter system we will have to explain some things as we go. The Programmers have for each slave both medical programming files, and a grey or black binder with the programmed access, trigger, codes & cues, & structure. A typical Illuminati system will be a cube (although spheres and pyramids are also used). The principle alters will be the “a” alters. A typical section of alters will consist of a 13 x 13 grid of alters. These are alters who live in a world together and must function together. A 13 x 13 section will have 13 families of “a” through “in” alters. The “a” alters will be the primary alters that the Programmers will interact with. The Programmer may call up an “a” alter and ask it to go get the “c” alter in its family, rather than directly asking for it. This initial page of alter codes will be the primary or “a” alters. If we are dealing with a 13 x 13 x 13 cube of alters, then the initial page has 13 “a” alters of each section. Each of these alters will have an access code which will often include the following components: AN ASSIGNED COLOR + AN ALPHA NUMERIC CODE + A PERSONALIZED MAGICAL NAME. This will equal 1/3 their access code. These code words must be repeated three times to pull the alter up. However, if an alter is trained well, and hears his master's voice, an alpha-numeric code can pull the alter up. For many of the alters, the reversal of their access code puts them back to sleep. This is an important point, because some alters would be dangerous to leave in control of the body. The “a” alters are regular alters. Many of them have been hypnotically age advanced to see themselves as teenagers or adults. Sometimes “b” and “c” alters are also aged. The “d” through “in” alters are generally left as they were split and most of them are infantile, with little concept of how old they are. The little ones will be the ones who often remember the programming very well, and know things about the system. The top alters will also sometimes receive personal names from their handler. This is in addition to all their codes. If the alter is responsive to its master, the personal name might pull the alter up too. Do all of the alters get charted? There are several groups of alters which get charted separate from the rest or don't get charted at all. Because of the competition and distrust between the different programmers, they often place in secret back doors into the person's mind that only they know about. Worlds of secret alters loyal and devoted to the programmer may be built into the system and not appear on the regular charts. The core, and some of the primal splits from the core will not appear on the regular grids. They will be placed on a separate sheet, and their codes will be in some magical language. The Illuminati commonly employs 20 magical languages, and Hebrew, Latin and Greek are also often used for charting the core and its primal splits. Enochian is a good example of a magical language used by the Illuminati. Some alters will be created solely by the slave in order to cope with life. For instance, say the slave is travelling with someone who is not a handler, but who is a dangerous person. This dangerous person murders several people and forces the slave to help. The slave is likely going to have front alters out, and they are simply going to have to create new alters to meet the demands of the situation. These alters made to deal with one-time emergency will just slip into cracks in the system. Lots of odds and ends alters end up in the nooks and crannies within a system just detached and floating. The programmers and the victim work hard at structuring and cleaning up things--but the honest truth is that trauma-based mind-control is messy. Any time you shatter someone's mind into thousands of pieces with horrendous torture, you have a shattered mess, in spite of the good fronts that the programmers are able to construct. Some of the more elaborate access methods are for alters that are not on the “a” chart. Hour glass alters have entire sentence access codes. Deaf & blind alters need their access code signed on their hands by moving their fingers up and down, etc. End time alters may have access codes that may entail reading an entire page. Reporting alters are often small children, that are hidden in each section, and may require slaps to the face or jabs with a needle to pull them up. Spinner kittens will be accessed via their mama cat, who acts like a Madam in a “cat house”. The codes for this was given in the Beta section codes. The reader will be given the hypothetical codes (which resemble closely the actual codes of an actual scenario) for our hypothetical Mary. A Sample Chart of the “A” alters--these are the primary alters-- has been prepared in the same fashion as it would appear in the handler's 3-ring binder.
Mary's Core Protector 1 will have a shutdown code of “REVERSAL 1 BEGINNING” and the second Core Protector will have the shutdown code of “REVERSAL 2 CREATION”. Of course, these codes are said 3 times. The first three alters on the far left section at the top of the chart are Silences who can be woken up by singing. Also at least one of these, will wake up by a kiss from the prince (programmer) to the third eye area. The first alter can be shut down by “COSMOS 15 31 06 2BAB PINK”. One of the groups of alters attached to one of these early alters is “MA.C3.10-53 Rejects (7) 10-53”. To shut this alter(s) down just say the reverse of the access code. A mirror image of each of these alters exists too. The mirror images can be pulled up via a three step process. The birth memory in our example will be coded as A5 10 79. The spider torture memories that are attached to these alters is A5 10 79. The reader will notice the following on the hypothetical chart on the previous page for the first Section (which is numbered 6 to be deceptive): This section is front alters. Basic code pattern = color + Genesis + no. [1 thru 13] + letter [a thru m]. Individual codes 1st section general-”N.I.F.6”, 1st section mother Eve “EV.E5 10 51 ACE” (Eve is the balancing point & the ace code is high or low). The alter Explorer is “EI.G7”, Mammy “MI.H8”, Angel “Red, AI.19 Jack Genesis 4” (or it could be done “red, AI.J10 Genesis 4”), George “Silver, GI.K11 ”, Zsa Zsa “gold, ZI.L.12”, and Shadow “Clear SI.M 13”. You won't find on the main chart codes such as: Eve's memory “EI.D5.2.1952 ACE” or the Infant alters -- “1-000 10-49 REJECTS 3-9” The master may say for example: “Green GENESIS 1-A” (3 times) to get this alter which is the balancing point. Fragments/dead alters were dumped into areas named concentration camps and given the names of the famous german concentration camps. The camps were placed under the Mt. of Olives. Fire or Bomb children are found throughout the system and are triggered to come up by programming. They come up behind other alters and make them burn. Some of this level can be woken up by saying, “It's time to wake up in the morning” (7 times), which is in contrast with most codes which are said 3x. Another way to look at it, is that the alters are on 4 dimensional structure and they require a 4dimensional access code. Height, depth, width, and color are the four dimensions. This breaks down for this 1st section as: COLOR (4th dimension) + Genesis (Section code) +1 (level) + “a” (depth). The following message will be used on the phone for this System's recording machine, this example has been used nationally. “IF YOU WOULD LIKE TO MAKE A CALL PLEASE HANG UP AND TRY YOUR CALL AGAIN. IF YOU NEED ASSISTANCE, PLEASE DIAL YOUR OPERATOR. CODE 911.” This will cause section 1 or section 2, etc. to call their master. Also, standard Illuminati Hand signals work with Mary. “ALONE AND CRYING (3X)”- is a code for a few special parts not on the first grid.
Section 2 gatekeeper alters. Basic code pattern color + Revelation + no.[1 thru 13] + letter [a thru m] In our hypothetical example: “ORANGE
REVELATION 4-A” (3X) However a shortcut is “REVELATION 4” and the primary Revelation 4 alter will come up. “ORANGE REVELATION 4 B” would get a small child on the pedestal with Revelation 4a. At times the handler will say “THE DECK IS DOUBLE-DECKED” in order to activate the clone doubles of all alters in a particular area--such as the front area of the system. The clones are tied to the Pink Room of the dollhouse-looking computer. Since alters are also coded to cards, a FLUSH will pull up an entire section. Special alters who skinned men alive are kept in black holes in Section 2. They are special trauma alters created solely by the victim as a safety measure. Section 2 computer (like all levels) is empowered by an emerald blue light. This power source was deactivated by unscrewing the light to the left (which took it physically out so to speak) and then saying “PEACE BE STILL” (3X). If “PEACE BE STILL” is not said three times then the War in the heavens program kicks in. Also “DAD WEEPS OVER HIS CITY” must be said when deactivating the computer otherwise the “children” (alters) become sick and everything kicks back in--which it does eventually anyway if the deeper computers are not deactivated or taken out. Section 3 has programmer alters & fragment armies, not to be confused with the clones which hide everywhere. The clones, by the way, can be identified with serial no.s at base of head gear such as 151.00 [system birth date]. This sections has 3 faceless Programmers called the 3 adepts of Atlantis. Each of them has a different color of hair. They may also be the commanders of armies--the commanders of the Egyptian armies have names Ra, Horus, and Set. Section 4 alters are Entertainment alters. Basic code pattern = Color + double number + a name of a one of the 13 tribes of Israel + the number of the alter again (3x)
Example: BLUE 2001-13A REUBEN 1 (3X) However, the color doesn't always need to be said it is a sufficient shortcut to call the alphanumeric code three times. Second example 2002-12A SIMEON 1 (3X). The numbers of the 2000 code go up while the corresponding number 13 to 1 go down. In other words it is a double code. The Tribal names are arranged according to their Biblical birth order.
Mother Kitten 8,10 and 12 have ten spinner kittens under neath each of them. To get a spinner kitten, one gets the mother kitten and then has her in the proper position which is the over-the-rainbow mode. The choice of what spin kitten to get is “WE GOTTA GET DRESSED ... IN 3 MINUTES.” 3 minutes means spinner no. 3. Specific instructions such as “PURR FOR ME KITTEN” gives the abuser fellatio. Tweedle Dee & Tweedle Dum is a S&M program. “5 FIDDLE” and “FOLLOW THE YELLOW BRICK ROAD” are important for the slave to follow instructions. The alters will be sent to never-never land where what they do is unreal. Some kitten alters are keyed to pop out if certain areas of the body are touched, such as the space beside the big toe, or the thighs. A handler will also have standard hand signals for things, such as putting his hands on his thighs to mean “Come here and take care of me, Kitten.” “COME KITTEN, TO PAPA COME” “BLUE TOPAZ” serves as 4 keys. Pisces is associated with Blue Topaz. There are also 4 keys which are: silver shoes, sun bright, birds singing, and yellow road. Section 2 & 1. Reprogramming sections. At this point, the computer codes given previously apply, SEE OMEGA CODES on previous pages. The first major computer services the top 6 sections and has a red room, a closet, a pink room, as well as other rooms. Actually the computer should be set in at Section 0, which would break up the grid evenly, but since our Mary is hypothetical we put the front main computer at section 1. A system like this will have 13 computers/1 per section and 5 computers which set between pairs of sections, which join a pair of sections together, and then 2 main computers. This means a System like Mary's will have 20 internal computers. With all the codes and a fair understanding of the alters in a section, it is a good day's work to shut down a computer. Before one could possibly get all the section computers shut off, they would reprogram (reboot) themselves back up. Computer erasure codes include: “FULL HOUSE ACES HIGH. ALL TRUMP. FULL HOUSE ACES LOW.” The drawers in the dollhouse can be pulled out with “ROYAL FLUSH”(3X). Another code is “PINK SECTION 5.
FULL HOUSE. ACES HIGH. 2 DEEP.” A partial code to a computer is “......
8-9 RED.” Our hypothetical Mary might be accessed by a woman who taps on the shoulder and says, “PHOENIX 360 [tel. area code], OUT OF ORDER”. The library alter has an important access ring. A “Button Bright” alter type works with the librarian. The dwarfs are accessed by “ISOLATION + no.” Judges which sit on the council give warnings to alters “CAT EYE AT THE DOOR.” This reflects the programmers' control. The judges have the “Keys to the Kingdom.” “MR POSTMAN WAIT AND SEE” indicates a message from the master. Ribbon alters have the names of archangels. Silver cords are attached to the ribbons. Section 0. Mothers of Darkness alters. basic code pattern = SILVER + LEHTEB [which is bethel or house of God spelled backwards] + [who knows what else] + a blue topaz ring being turned on the master's finger a certain way. Green is a sensitive color for this System. Some alters may be accessed from certain areas in the System via 4 tones, and others by pin pricks at certain locations in the body, along with their verbal code. The Reporting alter can be accessed by repeated slaps across the face. There is Ultra Green Section tied to the Cabala (Green tree). The Library in the big castle, which is guarded by lions and other big cats, has a passage way in it to a second world. Codes with the Cabalistic Tree of Life involve Cabalistic magic and its symbols. This section is guarded by a hostile entity. Certain rings, topaz, quartz, diamond, ruby, black onyx etc. are used for triggers. Certain rings are needed to get into certain parts of a System, such as the castle. To access the Mothers, the Black Onyx ring must be rotated. The programming of a ring may go something like this, “This ring fills
Daddy's house with stars.. .Catch a falling star, put it in your pocket.”
Section 9. Delta-Beta alters. Kept in a genie bottle. Obviously something is rubbed to get them out. “BUTTON BUTTON, WHO'S GOT THE BUTTON, BUT ITS THE KISS OF DEATH” this code is involved with the “good witch” who kisses upon the forehead. Buttons are on the boxes of Programmer Green and are constructed onto the boxes so they can be used to open the boxes up.
Section 7. This hypothetical system also has a series of codes based on gems--ruby, diamond, etc. which have numbers attached to the codes. An Hour glass w/ 12 disciples like grains of sand tied to Jolly Green Giant programming which have sentence access codes. Each sentence is a phrase of satanic philosophy. The bottom level is called the Hell Pit and contains the City of Petra. The City of Petra has an erasure code. “YELLOW - CUTTER ROOM 7 SECTION 7—ROYAL FLUSH--LA CUTTER EGGS” Invisible field section 7. Room 7 --cards has eggs with demons. Lacutters are like imps and are invisible. They are assigned to guard various things in the system including the cutting programs. “Dad” “Catch a falling star”.
Main computer protected by deaf and dumb alter using a sign language equation as its access code and the reversal of its access code is its shut down code. The Brack Master is a Master Programmer.
Each of the 13 sections of 169 alters (a section is a 13 x 13 grid of alters) will then have a computer assigned to it. The computer is made up of dissociated parts of the mind--which are like alters, but have not been given histories or names. Each section has a computer which makes 13 section computers. Section 1 and section 7 are main computers. The first is the main computer for the top half, and the second is the main computer for the bottom half of the System. The second main computer is in the hell pit, and has been put in at the lowest level of the mind. Section 6&5 computers are connected by a connecting computer, as well as 4&3, 2&1, 0&12, 10&9. This makes 5 connecting computers. In total then we have 13 section computers, 2 main computers, and 5 connecting computers, for a subtotal of 20 computers. Since things are being built on the basis of the magical number 13, six more computers are installed which are decoy or false computers for therapists to work on. This makes a total of 26 computers (or 2x13). Since there are 26 letters of the alphabet, this lends itself well, and each computer is assigned a letter of the alphabet. Since the computers are put into the slave when it is a young child, the child has just learned how to count and say the alphabet. The Illuminati has been using a large dollhouse with 26 rooms using 13 colors of paint, giving two rooms per color. Each room is a computer. In accord with the practice of double coding, each letter of the alphabet is given its sequence number, so the names for the computers are Al, B2, C3, D4, E5, F6, G7, H8, 19, J10, K11, L12, M13--the thirteenth is assigned the 1st main computer. N1, O2, P3, Q4, R5, S6, T7, U8, V9, W10, X11, Y12, Z13. Rather, than use the number 13, the number 0 will be assigned, thus changing things to M0, and Z0. This is simple enough for a child's learning mind, but difficult enough that it serves as a viable code. As codes are assigned, the bottom of the alphabet is assigned the top (front side) of the system. The middle point MO, is the normal access point for all the computers for the handler. The code for this is associated with the name of an airplane hanger, so that the concept of taking off into the sky (trancing can be associated with it.) Each computer needs an access code to go along with its alpha-numeric name. A deck of cards lends itself well to a code of 13. Bear in mind each computer has a color assigned to it. Colored scarfs and dollhouse rooms were used with electroshock to teach the child his color coding. When the programming is going on trance depths and runways(mental image for flying off into a trance) and the structure of the System will all be tied together in one neat package. Everything is built on its own x-y axis. Each 13x13 grid has the middle rows both vertically and horizontally set up as runways. The x-y axis also makes up the hourglass lines or the butterfly wings. Both images are used with slaves. Because thing are set up in thirteens in Mary's system, and things are double coded, thirteen becomes 13-1 and one is 1-13. This allows us also to link 13-1 and 1-13, so that everything becomes a circle. The circle within a circle, box within a box concept, triangle within a triangle situations makes the slave feel he is trapped in an infinity loop of programming that has no end and no beginning. 13 and 1 make 14. An entire deck of cards can be used in a double code that also adds to 14, such as the 8 of spades and the 6 of diamonds, or the Ace of spades and the King of Diamonds. Here then is the codes for Mary's computers. Two cards from opposite suits that add to 14. Since a deck of regular playing cards came originally from Tarot cards, the playing card used as a code also carry some occult significance to the codes. It is also training the child who is programmed this way to be interested in cards. And everytime the child plays cards they will reinforce at an unconscious level their computer coding. The computers will then have programs set in on 13 x 13 quadrants. Quadrant 6.6 will have a program such hopelessness. Other quadrants may hold aloneness, recycling, cold, heat, burning, cutting oneself, pulsating loud heart beat, and hundreds of other programs. These programs have the type of codes assigned them that are given in the Universal Function Codes. Many of the functions can receive a standard code, but other items require individual codes. Telephone tones are frequently used to be able to key in (that is access or trigger) parts of the computer program matrix. Dominoes also are used for the computer programming. The dominoes are put in so that the programmers can get a dominoe effect, if they want to set off a series of programs. Dominoes and flashing sequences of lights were used to train the child to automatically respond to a certain pattern of dots. Our hypothetical Mary will also have hundreds of other codes for all kinds of miscellaneous things such as the following random codes: “RUBY RED LIPS” “TO HAVE POWER” AND “TO BE THE POWER”, which are also found in the Tall Book of Make Believe in the Shut Eye Town. Dominoes help with the code: “2-4-6-8 WHO DO YOU APPRECIATE?”. More examples are, “I LOVE DADDY.” “JACK BE NIMBLE JACK BE QUICK 13-1 12-2...” “PUMPKIN HEAD--an access code. To go away- “Ta RA RA BOOM-DE-AYE”,”CRYING OVER YOU (3X)”, “SILKEN GIRDLE”-- a golden caterpillar plays a bittersweet tune. A gold pocket watch with Roman numerals is associated with the words “Eagle on it.” When Mary gets scared and begins to get into revolving switching, sometimes spinning can be slow down by saying, “10--YOU ARE SLOWING DOWN 9--YOU ARE SLOWING DOWN 8--YOU ARE GETTING SLOWER AND SLOWER...” A system's coding is a reflection of their programmer. If the programmer is a pilot which many of them are, then they may have pilot lingo in their codes, such as the system may be turned by pitch & degrees. If the programmer is a sailor the system may have nautical codes, such as “RED RETURN RUNNING'' , ‘‘SAFE HARBOR'' (for ‘‘Home''), and DOWN RIVER (away from “Papa”).
Q. Catholic Programming (by Jesuits etc.)
KEYS TO THE KINGDOM = world domination by mind control. VOW OF SILENCE is a keep quiet program activated by “THE WALLS HAVE EARS & THE PLANTS HAVE EYES SO YOUR SILENCE IS TANTAMOUNT TO SUCCESS.” This is explained to the victim that the sea shells and the plants have the ability to hear, and that a sensitive occultist (programmer) can psychically pick up what the plants and sea shells hear. “MAINTAIN IT” --is a command to maintain the Vow of Silence “MAINTAIN IT & LISTEN.”-- a command to keep silent and listen to a command.
“ENTER INTER INNER DIMENSION TWO” - this is a standard Jesuit infinity program (2 is a sacred voodoo no.)