1 Introduction
A further shift from clinical to ambulant treatment.
Reductions in the per user/patient workload of medical and care staff.
Improvements in the quality of medical and care services for users/patients.
And finally, significant reductions in the medical treatment and care cost per user/patient.
The attention, and hype, around the Internet of Things (IoT), and, in particular, IoT-driven eHealth, has further increased the visibility and expectation of eHealth [26–28].
In this chapter, the authors make an effort to give a reasonable, qualitative evaluation of what can be expected of IoT in eHealth and IoT-driven eHealth itself. They look at the possible contributions of IoT to eHealth, the requirements that need to be met, the benefits and limitations of eHealth, and the entry barriers [19, 25]. Important attention is given to security and privacy, representing an important set of issues [13, 47].
However, the authors conclude that these are not the first issues to be addressed: first there needs to be a joint understanding between the users/patients and health and care providers that there are benefits for both the users/patients and health and care providers in applying eHealth [39]. The conditions for business plans and accompanying value chains are realistically analyzed, and the resulting implementation issues and commitments are discussed [35, 43]. As a result, the chapter contributes to the literature by reviewing, innovatively, business models, strategic implications and opportunities for IoT-driven eHealth, as well as its deployment and evolution.
This chapter is comprised of ten sections and is organized as follows. Section two provides a theoretical view on the IoT-driven eHealth in the context of knowledge management and considers evolution of knowledge-based management practices in healthcare. Section three focuses on contributions of IoT to eHealth, considering IoT as enabler and discussing IoT-based medical-relevant eHealth systems. Section four provides an analysis of requirements for IoT-driven eHealth. Section five considers the limitations of eHealth. Section six defines the entry barriers. Section seven outlines security and privacy issues; however, it confirms these issues are not the first topics to be addressed, but instead, the benefits of applying eHealth. Section eight analyzes the conditions for business plans and accompanying value chains and calls attention to the associated implementation issues and commitments. Section nine contains summary and conclusions, following by references.
2 Theoretical View on IoT-Driven eHealth in a Context of Knowledge Management
2.1 Views on eHealth
Everybody talks about eHealth these days, but few people have come up with a clear definition of this term. The term was apparently first used by industry leaders and marketing people rather than academics, and they used this term in line with other “e”-words such as eCommerce, eBusiness, eTrade and so on.
So, how can the authors define eHealth in the academic environment? It seems quite clear that eHealth encompasses more than a technological development.
The authors can define the term and the notion as follows: eHealth is an emerging field in the intersection of medical informatics, public health and business, referring to health services and information delivered or enhanced through the communication technology, i.e., the Internet, and related technologies. In a broader sense, the term characterizes not only a technical development, but also a state-of-mind, a way of thinking, an attitude, and a commitment for networked, global thinking, to improve health care locally, regionally, and worldwide by using information and communication technology. As such, the “e” in eHealth does not only stand for “electronic”, but implies a number of other “e’s,”, which together, perhaps, best describe what eHealth is all about, or what it should be [11].
2.2 Views on IoT
IoT is a system that relies on autonomous communication of groups of physical objects. IoT, in context of the digital revolution, is an emerging global communications/Internet-based information architecture facilitating the exchange of knowledge, services and goods [5, 7, 8, 30]. The authors expect that main domains of IoT will be transportation and logistics; healthcare; smart environment (home, office and plant, integrated in the environment); and personal and social area [10, 31, 38, 46].
Realms in the ubiquitous society and in the multiverse
Variables | Realm | ||
|---|---|---|---|
1. Time | Space | Matter | Reality |
2. Time | Space | No-matter | Augmented reality |
3. Time | No-space | Matter | Physical reality |
4. Time | No-space | No-matter | Mirrored reality |
5. No-time | Space | Matter | Warped reality |
6. No-time | Space | No-matter | Alternative reality |
7. No-time | No-space | Matter | Augmented virtuality |
8. No-time | No-space | No-matter | Virtuality |
The new service designs, architectures and business models are needed in the multiverse, not only in the universe. What is obvious is that managers must work in order to manage these critical eight realms of the ubiquitous society. The applications of IoT are numerous, basically meaning smart things and smart systems such as smart homes, smart cities, smart industrial automation and smart services. IoT systems provide better productivity, efficiency and better quality to numerous service providers and industries.
IoT is based on social, cultural and economic trust and associated trust management skills, which broadly speaking mean developed security services and antifragility operations. Critical issues of the IoT security field are trusted platforms, low-complexity, encryption, access control, secure data, provenance, data confidentiality, authentication, identity management, and privacy-respecting security technologies. Security of IoT requires data confidentiality, privacy and trust. These security issues are managed by distributed intelligence, distributed systems, smart computing and communication identification systems.
Finally, key systems of global economy are markets, networks and crowds. IoT can be found among these key systems of global economy. Probably, there is a lot of potential for smartness between these key systems. Data, information and knowledge about communication and interaction of these systems are vital issues for the future of management.
Especially the Internet of Intelligent Things (IoIT), defined by experts as smart Machine-to-Machine (M2M) communication, provides much potential for crowdsourcing of markets and networks. IoIT provides also much potential for smart networking (between markets and networks and between various networks).
The authors expect that one obvious consequence of IoIT will be a broader scope of deliberate democracy. Additionally, the legal framework of IoT/IoIT is still considered rather vague, or absent in a certain sense. Such issues like standardization, service design architecture, service design models, data privacy and data security create management and governance problems, which are not, or at least not completely solved inside current service architectures. IoT has also become subject to power politics because of risks of cyber war, cyber terror and cyber criminality.
Finally, the authors can see that IoT will be central for the collection of raw Big Data, captured from the environment, human beings and robots and AI applications.
2.3 Views on IoT and Big Data in a Context of Knowledge Management
The Data-Information-Knowledge-Wisdom (DIKW) model is an often-used method, with roots in knowledge management, to explain the ways to move from data to information, knowledge and wisdom with a component of actions and decisions. Simply put, it is a model to look at various ways of extracting insights and value from all sorts of data, big, small, smart, fast and slow. It is often depicted as a hierarchical model in the shape of a pyramid and known as the data-information-knowledge-wisdom hierarchy, among others [2, 9, 16, 40].
Data is the result of a relatively accurate observation, and it may or may not be inspired by a problem to be solved. Data comprises objective facts, signs and numbers, and it does not need relationships with other elements to exist, but if to take each data individually, it does not communicate anything and does not contain any meaning. Data is something perceived by the senses (or sensors) but it has no intrinsic value until it is put in a context. Data becomes information only when it is placed in context, through contextualization (in fact), categorization, processing, correction and synthesis.
Information, deduced from the data, includes all data, giving them meaning and gaining added value compared to the data. Information is the choice to put some data in a context, fixing some as premises, and making a series of inferences, then drawing conclusions. These conclusions are called information but do not become knowledge if they are not related to the knowledge and experience of a specific person.
Knowledge is the combination of data and information, to which is added the opinion of expert persons, competence and experience, to build a valuable asset that can be used to aid decision-making. Knowledge cannot be lost in the same way in which one can lose data and information. In the domain of competence, the more to move from data to knowledge, the greater is the dependence on the context. Davenport and Prusak had offered the following definition [9]: “Knowledge is a fluid mix of framed experience, values, contextual information, and expert insight that provides a framework for evaluating and incorporating new experiences and information. It originates and is applied in the minds of knowers. In organizations, it often becomes embedded not only in documents or repositories but also in organizational routines, processes, practices, and norm”. Knowledge is always individual and cannot be transmitted because it is generated from the individual’s previous experience and knowledge; what one can transmit is only the narration of the experience.
Wisdom is immaterial, intangible. Wisdom is the judgement, the ability to add value and is unique and personal. Wisdom is something that goes beyond the concepts of information and knowledge and embraces both, assimilating and transforming these into individual experience. Wisdom accompanies knowledge and allows to make the best choices.

The traditional DIKW pyramid
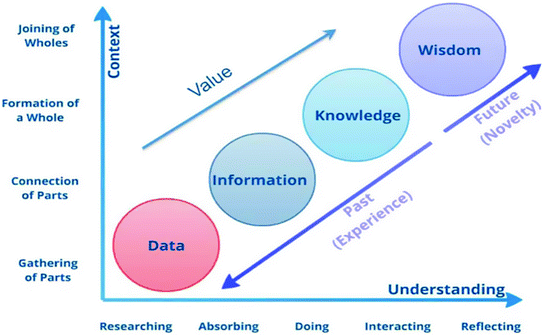
The traditional DIKW model on a Cartesian plane
Figure 2 highlights the rising value, from data to wisdom. In Fig. 2, the first three categories refer to the past; they deal with what has been or what was known. Only the fourth category, wisdom, deals with the future because it incorporates vision and design. With wisdom, one can imagine the future and not just grasp the present and the past. But achieving wisdom is not easy; one must go through all the other steps/categories [40].
As in the case with all models, the traditional DIKW model has its limits. The authors suggest the model is quite linear and expresses a logical consequence of steps and stages with information being a contextualized “progression” of data as it gets more meaning. Reality is often a bit different. Knowledge, for instance, is much more than just a next stage of information. Nevertheless, the traditional DIKW model is still used in many forms and shapes to look at the extraction of value and meaning of data and information.
One of the main criticisms of the traditional DIKW model is that it is hierarchical and misses several crucial aspects of knowledge and the new data and information reality in this age of IoT, Big Data, APIs and ever more unstructured data and ways to capture them and turn them into decisions and actions, sometimes bypassing the steps in the DIKW model, as in, for instance, self-learning systems [13]. The data must be of a certain type to really add value to an organization [29]. Big Data does not necessarily mean more information: the belief, rather widespread, that more data = more information does not always correspond to reality [42]. Among Big Data, there are obviously interpretable data and data that cannot be interpreted, sometimes because of lacking metadata or place/time references [32, 44]. Among the interpretable data, there are relevant data, i.e., the signal, and irrelevant data, i.e. noise, for our aims. Relevance is a characteristic of data, not only subjective, i.e., what for one is the signal could be noise to another; but also, contextual, i.e., what may be relevant depends on the context to be analyzed.
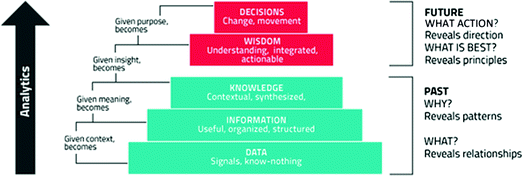
What matters: actions and decisions in the DIKW model
The traditional DIKW model, as all models or ways of looking at things in a more or less structured way, has been discussed and looked upon from various angles with some suggesting to omit wisdom, others debating the exact definitions and the relationships between them and a few telling to add a dimension of truth and moral sense to it, with the addition of something even higher than wisdom: “enlightenment”. The authors suggest the traditional DIKW model as one of several ways to define, illustrate and explain the various forms of data, information, etc. in a business, transformation and customer/stakeholder perspective. They have nothing against enlightenment as a step beyond wisdom, usually defined as “evaluated understanding” or “knowing why”, which they would then call truly understanding the purpose of information in a context of what people need and want, beyond the more factual knowledge. The enlightened business? Who knows [26].
The traditional DIKW model is also mapped to different types of management information systems. For instance, data is related with transaction processing systems; information with information management systems; knowledge with decision support systems; and wisdom with expert systems.
On the other hand, what the authors are most interested in, is the decision and action part, because without decisions and actions there is little sense in gathering, capturing, understanding, leveraging, storing and even talking about data, information and knowledge. The authors mean the decisions and actions as in business and customer outcomes, creating value in an informed way. However, in the bigger picture, the authors state that the decisions and actions can simply be learning, evaluating, computing or anything else [26].
2.4 Effects of IoT and Big Data to Knowledge-Based Management Practices
Organizations use information and knowledge both for improving the quality of decisions and for legitimizing decisions including also decisions made by poor knowledge [4]. The authors consider that organizations often fail to use information in an effective way in decision-making because of the oversupply of information, caused by biased organizations incentives for information in result of tendency to underestimate the costs of information gathering relative to its benefits. Typically, decisions about information are made in a different part of an organization than where the actual information gathering is conducted. This separation of using and gathering information enable managers to initiate information gathering process that may have value for them, but from the organizational perspective create more costs than benefits. This kind of behavior is rational for managers as it creates an illusion of managing uncertainty [9].
Rationality of information oversupply relates also to strategic value of information. This can be seen in cases where information is not, in the first place, used for doing sound decisions, but for persuading someone to do something.
Despite of increasing academic, as well as practical efforts, there is a difference in views on knowledge in decision-making either seen as a static asset owned by an organization or as a social construction emerged from interaction. Static view on knowledge implies the manageability of knowledge, where as social view emphasizes that knowledge cannot be managed, only enabled. Static view treats knowledge as object that can be identified and handled in information systems, when social view deems the role of IT as useful but not critical because it emphasizes assessing, changing and improving human individual skills and behavior. Related to differences in the role of IT, including IoT and Big Data, the two views on knowledge have also contributed two different knowledge management strategies [30–32, 35].
The authors evaluate possibilities that come along with the emergence of IoT and Big Data. Do IoT and Big Data lay down a basis for more smart, intelligent and even wise decision-making? Do IoT and Big Data bring knowledge-based decision-making into higher level? In order to reflect on these questions, the authors have had to analyze the functions of knowledge and information in decision-making.
One possible useful approach to analyzing decision-making is defining it as a moment which divides time into two eras, before and after decision. It is important to recognize that while decisions fulfill expectations they simultaneously produce insecurity in the sense that it becomes obvious that a different decision could have been reached. To manage uncertainty-related decision-making, organizations need information and knowledge to convince internal and external stakeholders that choices are made rationally. Although, conflicting interests and problems of gathering the all relevant information means that rationality in decision-making is only bounded. The authors suggest that by information and knowledge it is possible to create an impression of rational and reasoned behavior, which, in turn, contributes to internal trust and to preserved external legitimacy. This means that sound knowledge before decision also helps the implementation of decisions. It is also good to understand that the problem of bounded rationality is key motivation for organizational foresight activities.
The discussion shows that information is gathered, and knowledge used both for improving the quality of decisions and for mitigating potential decision consequences. Occasionally organization’s knowledge behavior is based on rationalistic ideal, whereas sometimes it is highly symbolic. Adopting the conventional view of IoT and Big Data, the authors suggest that the true value of IoT and Big Data in decision-making lies on their ability to simultaneously promote bounded rational behavior, i.e., provide the best possible information and to limit symbolic use of information, i.e., oversupply of information that have no value in improving decision’s quality. More generally, the authors assume that IoT and Big Data predict a new start of knowledge management and the revision of the traditional DIKW model [26].
Perhaps, the division of knowledge management strategies into codification and personalization strategies should also be reconsidered [23, 45]. For instance, Jennex had stated that society and organizations manage by planning [16]. Resources are limited, time is limited, and planning applies thought before action. The output of planning is a plan or strategy, a statement of how something will be done. Society and organizations need to have a strategy for managing the layers and technologies, including IoT and Big Data, in the revised DIKW model.
Identification of users of the knowledge pyramid layers and transformation processes.
Identification of actionable intelligence needed to support organizational/societal decision-making.
Identification of sources of the Big Data, data, information, and knowledge.
Identification of Big Data, data, information, and knowledge to be captured.
Identification of how captured Big Data, data, information, and knowledge is to be stored and represented.
Identification of technologies, including the IoT, to be used to support capturing and processing Big Data, data, information, and knowledge.
Generation of top management support.
Establishment of metrics for Big Data, data, information, and knowledge use.
Establishment of feedback and adjustment process on the effectiveness of actionable intelligence use.
Interpretation of operating environment: open system.
Agency: network (i.e., organizations as information flows).
Accountability: horizontal + vertical.
Organizational copying mechanism: foresight-based resilience.
Leadership: business intelligence.
Information flows: intra-organizational.
Innovation philosophy: open.
Production logic: service-based logic (i.e., customers first).
Change philosophy: immanent, emergent, cyclical.
Certainly, there are some organizational drivers that enhance Big Data utilization in data-driven ecosystems. As organizations operate in open system as networks, the role of information becomes a valuable commodity. Knowledge, based on information from intra-organizational information flows and incorporated to organizational life through the mechanisms of foresight and planning, is the foundation of business intelligence. This requires a new understanding on the organization’s accountability function, with an emphasis on measuring and analyzing accountability both vertically, i.e., reporting the outputs and outcomes of an organization from the bottom up; and horizontally, i.e., reporting to constituents including customers, citizens and the media.
This new requirement of understanding concerns the innovation and change philosophy held by organizations [26, 41]. The innovation paradigm opens because of the availability of information—tomorrow’s strategies and innovations are developed together rather than in organizational silos. Big Data also strengthens the transformation from mass-production logic towards more customized and personalized-production logic. To achieve advantage in the increasing competition, more focus should be put on both the products and services that organizations deliver.
Jennex concluded the goal is a top-down strategy approach based on decisions and actions [16]. The authors also note the digital revolution in management process, i.e., integrated knowledge management, by developing and utilizing smart solutions like utilization of IoT and Big Data, impact strategies based on decisions and actions as in business and customer outcomes, creating value in an enlightened way [26].
2.5 Effects of IoT and Big Data to Knowledge-Based Management Practices: Knowledge Integration and Sharing in Healthcare
Knowledge in healthcare is a multifaceted concept with multi-layered meanings. Due to this nature, it has become important to manage knowledge in order to drive performance by ensuring that relevant knowledge is delivered “to the relevant person in the right place in a timely fashion” (or simply put right knowledge is delivered to the right person at the right place at the right time) [6].
Apart from existing in the human mind, i.e., tacit knowledge, knowledge can exist in physical records, i.e., explicit knowledge, such as patient records and medical notes, which needs to be accessed more readily in paper or in computerized form. The major focus of knowledge management in healthcare is to create environments for knowledge workers to develop, leverage and share knowledge. For this to happen effectively knowledge management requires deep-rooted strategic and behavioral change. From this point of view knowledge management represents an evolution towards greater personal and intellectual freedom empowering individuals to engage more actively in their work by sharing ideas, thoughts and experiences. Once knowledge has been discovered, storing it, reusing it and generating new knowledge from it, is important to adding value to data to create shared knowledge.
Continued progress in technology makes sharing knowledge easier, and the Internet with collective portals makes knowledge accessible to a wider range of audience. The rise of networked computers has made it easier and cheaper to codify, store and share knowledge. There is no shortage of technologies to aid in managing knowledge in a healthcare environment; rather the prevalence of such technologies can create confusion.
The goal of knowledge management in healthcare is to enhance the performance by providing efficient access to knowledge and communities of healthcare professionals. It aims to combine the information from different sources (tacit, implicit and explicit), bridge and provide it on a platform which allows applications to be built on it. It aims to prioritize, share, consolidate and provide consistent and accurate information and performance indicators to help with efficient decision-making processes.
As workers in a knowledge-intensive environment, healthcare professionals inevitably hold a considerable amount of experiential knowledge, which can be used to solve day to day problems. It is important that knowledge used to solve such problems is captured, shared and reused in order to prevent the lack of nourishment, i.e., update and replenishment, of that knowledge and to improve knowledge of context. The knowledge process in a healthcare environment can be used to increase collaboration among clinicians, nursing staff with social service agencies for purposes of innovation and process improvement. Updating of knowledge assets cultivates the collective knowledge in healthcare, enriching effective management, smoothening the flow of knowledge to enable better problem-solving and increase knowledge potential.
Knowledge management in the healthcare industry when applied effectively can result in increased efficiency, responsiveness, competency and innovation, which results in superior performance in potentially critical applications. The challenge is, therefore, to create a knowledge management system that can acquire, conserve, organize, retrieve, display and distribute what is available in a manner that informs, educates and facilitates the discovery of new knowledge to contribute to the benefit of the organizations.
Knowledge management in the healthcare industry can, therefore, be viewed as an integrator that offers a framework for balancing the technologies and approaches to provide valuable decision-making actions. It integrates into a seamless whole by aligning organizational information and practices with the organization’s objectives. This fits into an employee’s daily work activities, manages content effectively, and encourages the potential opportunities of knowledge sharing with external agents.
The healthcare industry has been called “data rich while knowledge poor” as its functions hold large amounts of data (e.g., patient records, outcomes of surgery and medical procedures, clinical trial data, etc.) and still the knowledge potential of many actions is yet to be fully exploited because much of the data is not translated into knowledge, i.e., there is low added value, in order to provide a wider context, a deeper understanding and to help with strategic decision-making. Knowledge appears to be underutilized at the point of care and need. This limits the ability of experienced personnel to harvest knowledge and provide a clearer understanding of the involved process and factors by providing “a window on the internal dynamics of the healthcare enterprise”.
Multidisciplinary healthcare teams harvest personal expertise essential for patient safety, learn from it, adapt it to local situations and individual patients, then distribute it via reliable networks to care givers to improve care quality. The healthcare application with a high value form of information that allows sharing of the lessons learned from past experiences improves the context of knowledge potential processes in future. A fundamental challenge faced by clinical practitioners and healthcare institutions is in the ability to interpret clinical information to make potentially lifesaving decisions while dealing with large amounts of data.
Clinical practice is quantitative and very much qualitative too. The tacit knowledge acquired by clinicians and nurses over the years, mainly through experience, represents a valuable form of clinical knowledge. Knowledge management in the healthcare industry involves understanding diseases, hospital systems and, most importantly, patients. The authors note that clinical methods exist for understanding diseases and illnesses, but clinical methods or models are not so readily available for understanding patients. When quantitative and qualitative methods complement each other, and when various modalities of knowledge are used, a holistic view of a situation is best obtained, consequently leading to efficient decision-making.
Knowledge management strategies in the healthcare industry can be broadly classified into codification, where knowledge is identified, captured, indexed and made available, and personalization, where tacit knowledge is shared by means of discussion, effective communication through a multidisciplinary approach, allowing for case by case specific knowledge to be created, which in turn allow creative problem-solving. Therefore, the use of both strategies of understanding diseases and patients is according to the different scenarios. When dealing with routine cases, the codification strategy can be applied and when dealing with a situation where a more creative solution is required, the personalization strategy can be applied. This approach, however, usually only works when the required knowledge is shared, i.e., processed, successfully.
Furthermore, the authors consider IoT as a tool contributing to a solution to some knowledge management problems in the healthcare industry. As noted previously, IoT is an abstract concept in which physical objects are identified and connected to each other and have the ability to communicate with and to interact with their surroundings, providing some intelligence in their functionality. IoT is focused on the network of smart devices that communicate with each other and with cloud-based applications in order to provide a better quality of life. The term and the notion refer to implementing networked RFID technologies with a view to providing a better quality of life and increasing knowledge sharing. The implementation of IoT may drive advancements in all areas of human life by extracting knowledge from the raw data provided, with the possibilities of solving many socio-technical interaction problems [26].
Therefore, the aim of IoT in healthcare is to create a better quality of life and increasing knowledge sharing by connecting things, which can be people (e.g., patients and medical staff), objects (e.g., medical equipment) and systems (e.g., patient monitoring systems), and integrating them seamlessly into network with the internet technology and connectivity. The integration, evolution and adaptation of emerging biomedical technologies will also provide a foundation for the IoT [26, 37].
In 2008, the number of things connected to the Internet already exceeded the number of people on earth, and it is possible that 50 billion things will be interconnected by the year 2020 [27, 28]. A technological evolution of telemedicine is taking place, in which healthcare professionals can now monitor patients’ vital signs remotely and continuously.
In addition, the technology supports per-signalization, in which patients with chronic conditions can live independently in their own homes or secure housing, i.e., in a non-hospital setting, using IoT technology to support their life and lifestyles. Such devices include Lifeline Home Units, Personal Pendants, Wandering Client Alarms, PIR Movement Detectors, Fall Detectors, Bed Occupancy Sensors, Temperature Extreme Sensors, Automatic Medicine/Pill Reminders and Dispensers, Talking Color Detectors for blind and partially-sighted people and assisted GPS/GSM technologies, which recognize when the user/patient goes outside the chosen safety zone [26, 33]. The number of such devices and their applications is increasing daily.
3 Practical View on IoT-Driven eHealth
3.1 Analysis of a Case Study on Improving the Patient Discharge Planning Process Through Knowledge Management by Using IoT
3.1.1 Background
The UK National Health Service (NHS), a publicly funded organization, provides healthcare for all UK citizens (currently more than 62 million people). The NHS is faced with problems of managing patient discharge and the problems associated with it, such as frequent readmissions, delayed discharge, long waiting lists, bed blocking and other consequences [1]. The problem is exacerbated by the growth in size, complexity and the number of chronic diseases under the NHS. In addition, there is an increase in demand for high quality care, processes and planning. Effective Discharge Planning (DP) requires practitioners to have appropriate, patient personalized and updated knowledge to be able to make informed and holistic decisions about a patients’ discharge.
The NHS case study [18] examines the role of knowledge management in both sharing knowledge and using tacit knowledge to create appropriate patient discharge pathways. It details the factors resulting in inadequate DP and demonstrates the use of IoT and Big Data as technologies and possible solutions that can help reduce the problem. The use of devices that a patient can take home and devices that are perused in the hospital generate information that can serve useful when presented to the right person at the right time, accordingly harvesting knowledge. The knowledge when fed back can support practitioners in making holistic decisions with regards to a patients’ discharge.
3.1.2 Discharge Planning Dilemma in the NHS
Discharge is defined as when an in-patient leaves an acute hospital to return home or is transferred to a rehabilitation facility or an after-care nursing center. DP should commence as early as possible in order to facilitate a smooth discharge process. Discharge guidelines have been prescribed by the UK Department of Health (DH) and different trusts implement discharge pathways or process maps following these guidelines. Several DP improvement attempts have been made and reasonable improvements have been noticed. Several methods by which DP takes place have been identified in two UK hospital trusts, including DP commences on admission: patient and care giver are involved in the decision-making process; a clinical management plan where an expected date of discharge is predicted based on actual performance in the ward or, on benchmarking information from past cases; multidisciplinary teams make a decision based on experience during their meetings. A bed management system stores information on beds occupied and weekly meetings are held to decide the discharge date for patients.
All of these methods involve knowledge management [26]. It is seen that, a rough DP is currently drafted for patients upon entry to hospital according to their diagnosis, and a tentative discharge date is provided in line with recommendations. Changes are made over the course of the patient’s stay and records are manually updated by nurses, upon instruction by the doctors. This sometimes results in confusion and even disagreement on discharge dates by different doctors, i.e., when treating the patient for different symptoms; and nurses, i.e., when a change of shift occurs. This case study proposes that patient DP requires viewing the whole system and not as isolated units. In the discharge plan the patient and care giver involvement needs to be considered, however very little indication has been provided on these. To date, clear guidelines are not present on what information needs to be collected, stored and reused on patients.
3.1.3 Analysis by the Authors
The UK NHS is facing problems of managing patient discharges while having to meet waiting time, treatment time and bed usage targets. Patient discharge is currently being driven by quantitative measures such as targets (e.g. to reduce “bed-blocking”) and problems resulting from this situation has received a great deal of popular press attention recently and political capital has been made from this. Targets are prioritized while compromising patient’s after-care quality. Being target-driven (rather than knowledge driven) implies that the healthcare system fails to consider the factors that affect the effective recovery of a patient after treatment and discharge. Hospitals focus on accomplishing and achieving internal targets, resulting in compromised patient safety and well-being after discharge.
The exact situation with regard to patient discharge and readmissions is not really well established, as there are variations in discharge methods between trusts. However, it is reported in the popular press that doctors have to make quick decisions about patients just to “get the clock to stop ticking” resulting in deteriorating trust between doctors and patients. More precisely, doctors find themselves torn between meeting targets and providing their sick patients with the best treatment. These claims in the assorted news media have been reaffirmed by Andrew Lansley, the Secretary of State for Health in the UK Government [18]. “The NHS is full of processes and targets, of performance-management and tariffs, originally, all designed to deliver better patient care, but somewhere along the line, they gained a momentum of their own, increasingly divorced from the patients who should have been at their center.” [18, 26].
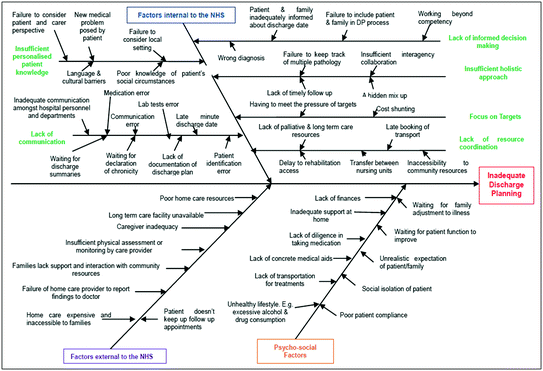
RCA of factors resulting in inadequate DP
A carefully designed DP supported by KM can ensure more efficient utilization of hospital resources and will encourage better inter-department communication to ensure that tacit knowledge makes better informed decisions about patient discharge. It is believed that this in turn will allow for better coordination of the external factors and will give hospital personnel more time to inform patients and their families, accordingly addressing the psychosocial factors. At discharge, preventable and undetected errors can occur. These can be reduced by knowledge sharing among hospital staff and having patient centric discharge pathway leading to improved DP. Patient participation and understanding in DP will help reduce potential readmissions and delayed discharge. Patient participation in the discharge process is a legally stated right in the UK and therefore more active participation of patients is encouraged. The failure to assess a patient’s care needs correctly can result in a disproportionate delay in patients being discharged [26].
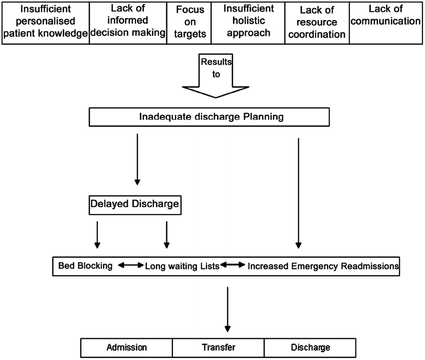
Problems resulting from inadequate DP
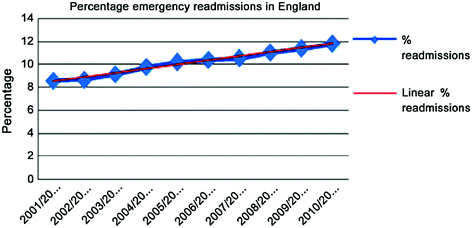
Emergency readmissions in england as percentage of admissions
The problem of inadequate DP does not just concern readmissions, however. “Bed-blocking” due to delayed discharge has equivalent negative implications. It is reported by the NHS confederation that one in four patients are occupying beds when they could be recovering at home, which results in longer waiting lists, loss of confidence in the NHS and escalating expenditure. The average number of patients and days of delayed discharge per month in England for the year 2012 according to the Department of Health was 3997 patients and 114,386 days respectively [18, 26].
Approximately £250 m was spent on “delayed discharges” between August 2010 and the end of 2011, amounting to £550,000 a day [18, 26]. Apart from the financial implications the delay in discharge is clearly disadvantageous to the well-being of patients, the morale of their relatives and wastes valuable hospital resources. The King’s Fund reports that if it was better organized the NHS could reduce the number of overnight stays by 2.3 million, freeing up 7000 beds and saving the NHS nearly £500 m a year [18, 26]. Mike Farrar, the Chief Executive of the NHS Confederation, indicated that these problems are the result of an “outdated hospital model of care” while a breakdown in communication may also be a possible contributory cause [18, 26].
Many older patients face the brunt of delayed discharge as due to a lack of communication between the NHS and social care homes, they are forced to stay in hospital, causing longer waiting lists for other patients who are seeking urgent treatment. The reasons for the dilemma as described in the case study are clearly a result of inadequate support for DP among NHS staff, including physicians, nurses, social workers, and possibly other health professionals [26].
3.1.4 Knowledge Management for Successful Discharge Planning
A hospital is a dynamic environment, with changes taking place rapidly as patients move from one ward to another and treatments are carried out over time. Similarly, DP involves changes from a stable temporal state to another with an element of unpredictability of what is going to happen next. In this context, the past experiential knowledge of doctors and nurses is useful in assessing situations and deciding on plans. This enables making critical decisions, as their knowledge can be reconfigured and extended to fit the new situation and provide a personalized approach in assessing patients’ journey along codified guidelines.
Knowledge management may have the potential to remove bottlenecks to improve the DP process mapping and identify possible improvement opportunities. Understanding the relevant knowledge for a given situational decision is crucial to this process and a decision can never be completely separated from the context in which it is made. This implies that in a hospital setting when looking at DP the interrelated factors need to be considered in the context of knowledge management process.
Clearly, monitoring and understanding a patient’s condition after discharge is a key part of successful DP. This requires the support of appropriate sensing and monitoring technologies with IoT and Big Data, i.e., medical equipment, patient monitoring systems, and smart devices supporting per-signalization; so that patients with chronic conditions are able to live independently in a non-hospital setting, i.e., in their own homes or secure housing [26].
3.2 IoT in eHealth
Although the authors prefer to use the term IoT for integrating so far not communication-able devices into a digital, communicating infrastructure, often based on the internet infrastructure and services, they hereafter include, in general, communicating sensor and actuator devices, aimed at measuring and, where applicable, controlling health-relevant parameters.
3.3 IoT as Enabler
The technological development of direct and indirect sensor systems, as well as miniaturization, are making available more and more IoT sensor systems that seem to make practical use in eHealth possible, and, thereby, eHealth feasible and accessible.
3.4 Gadgets and Medical Relevance
Most of these sensors require positioning and sophisticated and medical knowledge-based algorithms to make them medical-relevant. In absence thereof, they, unfortunately, stay at the level of gadgets with an indicative value for healthy living and exercising. Moreover, smart applications and algorithms, using the facilities of the current generation smart phones, in particular, accelerometers and cameras, have created another wealth of healthy living and exercising APPs, with even more limited medical relevance [3, 36].
3.5 Dynamic HER and Dynamic EPHR
To provide the on-line, dynamic, very recent past complement to the static EHR and EPHR stored information.
As a tool in support of security mechanisms.
3.6 System Approach Versus “Whatever” Approach
In order for IoT to make an important and necessary contribution to eHealth, a system approach needs to be followed, not a “whatever” approach, as is too often the case with today’s wearables. In a number of the companies and research organizations in the world, there is the infrastructure and multi-disciplinary competence, necessary to develop IoT-based medical-relevant eHealth systems, as is shown by the laboratory prototypes, such as continuous, real-time blood pressure monitoring systems; and even by pre-production prototypes, such as diabetes insulin measurement and control systems.
In the next sections, the authors provide a qualitative evaluation of the technical and business-related aspects of relevance for the system-based approach as such.
4 eHealth Requirements
Efficiency—one of the promises of eHealth is to increase efficiency in health care, thereby decreasing costs: e.g., avoiding duplicative or unnecessary diagnostic or therapeutic interventions.
Enhancing quality of care—increasing efficiency involves not only reducing costs, but at the same time improving quality: it may enhance the quality of health care, e.g., by allowing comparisons.
Evidence based—eHealth interventions should be evidence-based in a sense that their effectiveness and efficiency should not be assumed but proven by rigorous scientific evaluation: to be done.
Empowerment of consumers and patients—by making the knowledge bases of medicine and personal electronic records accessible to consumers, eHealth opens for patient-centered medicine.
Encouragement of a new relationship between the patient and health professional, towards a true partnership, where decisions are made in a shared manner.
Education of physicians through online sources (continuing medical education) and consumers (health education, tailored preventive information for consumers).
Enabling data and information exchange and communication in a standardized way between health care establishments.
Extending the scope of health care beyond its conventional boundaries, in both a geographical sense as well as in a conceptual sense, eHealth enables access to services online from global providers.
Ethics—eHealth involves new forms of patient-physician interaction, posing new challenges and threats to ethical issues as online professional practice, informed consent, privacy and equity issues.
Equity—to make health care more equitable is one of the promises of eHealth, but at the same time there is a considerable threat that eHealth may deepen the gap between the “haves” and “have-nots”.
Medical and/or care relevant and usable systems, including:
Collection of medical relevant data with:
direct and indirect practical measurement, compromise between user/patient comfort and data collection quality and reliability;
suitable sensors used in a way matching the capabilities and limitations of the sensors.
Data pre-processing:
data reduction to avoid data overflow;
generation of reliable warnings (alarms) to make use of data manageable and beneficial.
Data interchange and exploitation with:
Combination with other IoT and non-IoT data, e.g., location information;
Security and privacy;
Trust and reliability;
Anonymization of data where possible;
On-line and off-line data post-processing with medical relevant objectives.
System approach versus “whatever” approach, including:
The users/patients: must be active committed stakeholders/beneficiaries;
The medical and care providers: must be committed stakeholders/beneficiaries;
The infrastructure and service providers (installation, operations, maintenance and repair);
The IT infrastructure (middleware, cloud storage, cloud processing, applications);
The near/on-user/patient systems, smart systems;
The compromise between patient benefits versus black-box/post-mortem benefits; and
Hybrid/dialogue development approach with:
the top-down requirements;
the bottom-up possibilities; and
cost and benefit-driven.
5 eHealth Limitations
The patient benefit versus black-box/post-mortem approach, as it simplifies:
Recording effects of a disease or condition than preventing or curing it; and
Applying negative evidence gathering, e.g. non-compliance with the prescribed diet and medication than directly contributing to overcoming an illness or condition.
Generating warnings and alarms that are essential for the usefulness of eHealth, without risking eHealth to become the black box of Health.
On the other hand, generating warnings and alarms is as good as the quality of the data collection and the applied algorithms; therefore, applying AI and Big Data techniques may be helpful post-processing options. But, the absence of warnings and alarms can never be taken as guarantee for the absence of risks and conditions.
The unjustified cost-saving expectations, meaning the cost of installation, maintenance, technical and medical healthcare operation should be taken fully into consideration, already in the system design and planning phase. Additionally, it may be easier to achieve better quality health care than achieving real cost reductions.
6 eHealth Entry Barriers
Functionality.
Medical relevant data and information;
Time needed to accept and develop procedures and algorithms and AI to handle the reduce data, obtain information and generate reliably warnings and alarms.
Trust.
Security and privacy.
Security and privacy concerns are major impediments to eHealth.
If they are not properly addressed, health care seekers will not feel comfortable in participating, and health care professionals will face huge liability risks.
Usability and “companionship” for both users/patients and health and care providers.
Market development and the required stability in value chains and business plans.
7 Security and Privacy
7.1 Security Safeguards
Although the authors prefer the more general terms, such as Data Ownership and Access Control [24], in this section they mainly use the more familiar terms Security and Privacy [12, 26].
Developing and implementing security and privacy functions in eHealth is a prerequisite for adoption by both users/patients and health and care providers. It concerns, however, a more complex ecosystem than environments currently addressed, requiring new and more sophisticated privacy and security systems, that in turn may find their application also in other more demanding applications, e.g., in Industry4.0, energy, social networks.
In particular, the requirements include: individual privacy, temporary and permanent sharing of subsets of private information, user-controlled access between providers, transferring ownership from a provider to the user/patient or another provider, role-based access, etc., and, a controlled and regulated “break-glass” function for emergency situations.
Note that while security is related to privacy, the two concepts are quite different. The Health Insurance Portability and Accountability Act of the United States (HIPAA) and the Organization for Economic Co-operation and Development (OECD) and other influential sources on the subject of electronic health information clearly distinguish between security and privacy. The eight Fair Information Principles codified in 1980 by the OECD are: openness; collection limitation; purpose specification; use limitation; data quality; individual participation; security safeguards; accountability.
Note that “security safeguards” constitute only one of the eight principles: security safeguards are necessary to achieve privacy, but not sufficient. In fact, most real-life threats come from “secondary use” by insiders with authorized access [12, 26].
7.2 Security Issues
Security is generally defined as the extent to which personal information can be stored and transmitted in such a manner that access to the information is limited to authorized parties. The Health Insurance Portability and Accountability Act of the United States (HIPAA) requires organizations that deal with health care information in electronic form to maintain proper “security safeguards.”
It requires mechanisms for identification, authentication, authorization, access controls, audit trails, accountability, encryption, digital signatures, physical security, disaster recovery, protection of remote access points, protection of electronic communications, software discipline, system assessment for vulnerabilities, and integrity of data. Ironically, many of today’s commercial security technologies even have a highly adverse impact on privacy principles, which deal with the ability of data subjects to limit the collection of identifiable information [12, 26].
7.3 Privacy Issues
Privacy is defined as the claim of individuals to determine for themselves when, how, and to what extent information about them is communicated to others. This implies that the control over the release of identifiable personal information should rest with the data subject. Legislation that places this control in the hands of third parties does not contribute to privacy, nor do trusted third party solutions that are unilaterally imposed upon data subjects. Secondary use concerns information disclosed to one party for a particular purpose subsequently used for other purposes. The five threats to privacy in eHealth systems that the U.S. National Research Council identified refer primarily to insider attacks: insiders who cause accidental disclosures, who abuse their record access privileges, who knowingly access information for spite or for profit; vengeful employees [12].
Privacy is also sought by medical practitioners: many do not like the idea of central parties (e.g. health insurances) being able to monitor all their actions, since this negatively impacts their autonomy. In many situations, they prefer to be able to access information on the basis of their role rather than their identity. Role-based access is also preferred by most researchers for accessing medical information and databases. Ironically, the very technologies that are currently being considered to implement important security safeguards may make it impossible for patients and health care service providers alike to escape systemic identification throughout the HER [12, 26].
7.4 Privacy-Respecting Security Technologies
If at the technical level everything is systemically identifiable, privacy legislation becomes virtually meaningless. The problem can be solved through use of security technologies that do not violate basic privacy principles. This implies that privacy-respecting security technologies must, at the very least, allow individuals to de-identify their own personal information before disclosing it.
It is important to recognize that privacy-respecting security technologies are not all about anonymity or pseudonymity towards parties that subjects are voluntarily interacting with: they are about controlling which parties can learn what, as personal information flows through the system from one party to the next. For instance, role-based signing can be securely implemented through the use of privacy-preserving technologies, in such manner that digital signatures cannot be traced to an identifiable person but only to the role they assumed when signing; at the same time, through the magic of cryptography, in case of a dispute, error, or other mal-event, the signer cannot repudiate his action [12, 26].
7.5 Ownership of Health Records
To ensure that patients have control over their health privacy, they should have control over the access to the information. The question is: to what extent? Electronic Personal Health Record (EPHR) can include patient identification and contact information, and in theory, the aggregation and unification of all medical information about him/her. The EPHR can be stored on the individual’s home computer, on a portable device (such as a laptop, smart card, or smartphone), or on a secure server on the Internet (possibly distributed across multiple trusted parties). With each new consultation with a health professional, the physician is given access to the relevant health information and may update entries in accordance with new findings [14, 26].
The idea of giving patients electronic control over their medical information is not new. Gaunt had listed over 50 internet-based EPHR systems [14]. More in line with the idea of EPHRs are smartcards storing emergency and other health data. According to Waegemann, during the mid-1980s, the vision of patients being in charge of their health information became a leading force [47]. However, from the view of the health care professional, it is one thing for a patient to view his own health information, it is quite another thing to add, delete, modify, or prevent updating of arbitrary data in the HER [14, 26].
Policies on health data ownership differ substantially between delivery networks, states and globally. Larkin had noted that whether patients or physicians provide information for the record is a subject of often intense debate. Ricci had described a health care future where security and privacy issues have been resolved [39]. The question of medical record ownership has totally shifted as consumers have embraced ownership of their own Personal Health Records (PHRs) through secured Web sites [14, 26, 34].
8 Value Chains, Business Models and Strategies, Deployment and Evolution
While eHealth has a major potential and it adoption may even be considered necessary to achieve increased ambulant and remote medical care, increased quality of care, reduced personnel needs, and reduced or reduced increase in costs, the market is not developing as hoped and expected [26].
The separation and/or overlap between private and public health services provision.
The separation and/or overlap between private and public health services insurances.
The role of telecom and communications services providers.
The role of equipment manufacturers.
The role of equipment and communications services installation and services companies.
Investments made near the user/patients would contribute to cost savings in a hospital.
Investments made in a hospital would contribute to cost savings in the public social sector.
The unsettled configuration of the value chains results in uncertainty for the scope and hence of business plans [26]. And this uncertainty in value chains and business plans do not favor the commitment and market development, in turn leading to low interest from industry, hesitant telecom service providers and manufacturers in joint research and development and standardization, essential to arrive at coexistent and interoperable infrastructure and support for common generic and specific applications [20, 26].
Whereas telecom providers tend to try to offer “premium services” for eHealth services, it could be observed that few eHealth applications require high bandwidth, low delay, low Bit Error Rate (BER) services. Instead, eHealth requires rather a reasonable high availability including a short time to repair, 24/7. And, while eHealth, and in fact, our whole society becomes more and more dependent on access to the internet and the services it supports, the availability of networks and Quality of Services (QoS) is not improving, but rather degrading [26]. This may lead to the development of communications service providers that guarantee a service covering support for eHealth equipment and high availability telecom services to address this gap [15, 17, 21, 22, 34].
The time necessary for organizations to arrive, alone or together with partners in the value chain, to decisions to invest and deploy eHealth systems at a large scale is often not sufficiently considered or even ignored. As deployment takes a significant amount of time, and technological development keeps it pace, it is foreseeable that organizations applying eHealth systems will be working in parallel with several generations of equipment [15, 20, 26, 34], using several generations of the telecom infrastructure (second-, third-, fourth-, fifth-generation WAN, Lora, satellite, etc.).
Regarding the functionality, it may be expected that eHealth equipment will develop into fully or partially implanted systems, with an increasingly feedback and control functions.
9 Conclusions
There are theoretical and practical views on IoT-driven eHealth.
Theoretical view on IoT-driven eHealth concerns associated knowledge management issues.
Practical view on IoT-driven eHealth concerns possible contributions of IoT to eHealth, the requirements, benefits, limitations and entry barriers, as well deployment and evolution.
The eHealth has a major potential, and its adoption may even be considered necessary based on:
Increased ambulant and remote medical care;
Increased quality;
Reduced personnel needs; and
Reduced costs potential.
However, it is subject to the following challenges and issues to be addressed:
While the fitness and healthy living market are developing explosively, the real eHealth market development stays behind;
The eHealth reduces personnel needs, but also shifts the need to higher skilled jobs;
Achievable savings are real, but cost estimates seem exaggerated, and do not take into account installing, operating, maintaining equipment and reliability services, nor medical services 24/7;
Large scale deployment of eHealth takes time, comparable to the deployment of telecom networks;
Unsettled value chain and business models do not favor commitment and market development;
Lack of commitment results in technical issues, such as lacking quality objectives, data analysis and alarms, standardization, reliability of devices and services, that are not sufficiently addressed; and
Security and privacy need to be addressed; however, as shown, the resolution of these issues may be more complex and require more time than many have currently recognized.
In addition, since eHealth touches on many areas of public policy, including quality of life, public health, employment, industry, research, one could expect more active and effective government policies in favor of eHealth.
In conclusion, the authors state IoT-driven eHealth can happen and will happen; however, much more needs must be addressed in order to bring it back in sync with medical and general technological developments in an industrial state-of-the-art perspective, and to recognize and get timely the benefits.