1 Introduction
In today’s progressing world technologies are becoming smarter and everything is being computerized or being linked to the global Network. Due to fast developments and technological advances many ordinary things of humans’ routine have already become faster, easier and cheaper. And so has telephony.
As a result, a large number of users nowadays hardly even uses normal telephone communication, preferring modern and cheaper ways to connect with each other. And the name of this new way of communication is IP Telephony.
There are many definitions of this term, but the most precise one in my point of view is the following one: “IP telephony (Internet Protocol telephony) is a general term for the technologies that use the Internet Protocol’s packet-switched connections to exchange voice, fax, and other forms of information” [1, 2]. IP Telephony is—simply put—a general concept for online voice transmission and to implement this concept a special protocol is needed. A protocol used to transmit voice over the Internet is called VoIP—what stands for “Voice over Internet”. Another related term is SIP—Session Initiation Protocol. It is a communication protocol for management of multimedia communication sessions (voice or video call over the Internet) [3]. It basically deals with call establishment, the first and important phase of a call. After a call has been set up, various other protocols come into play, which handle data transmission (voice packets) between telephones [4].
The main difference between SIP and VoIP is that VoIP is responsible generally for making or receiving IP calls and SIP establishes, adapts and finishes this multimedia session [5]. The terms “IP Telephony” and “VoIP” are often mixed up. In this paper, we will still use them both as synonyms because they both mean the same concept in general.
Basically, IP Telephony has the same principles as cellular (also called mobile) network or traditional analogue phone system [6]. Traditional phone system is called “Plain Old Telephone Service” or POTS. Though these technologies are completely different, they all are based on “signaling, channel setup, digitization of the analogue voice signals, and encoding” [7, 8] In fact, no real difference can be observed superficially: the voice is transmitted from user to user both, be it through POTS, cellular network or VoIP technologies. The real difference is hidden behind the transmission itself: while traditional phone communication is carried out through circuit-switched connections (telephone network) in which two nodes establish one communication channel and have to stay connected for the whole period of communication, mobile network “transmits data through a global network of transmitters and receivers” [9, 10].
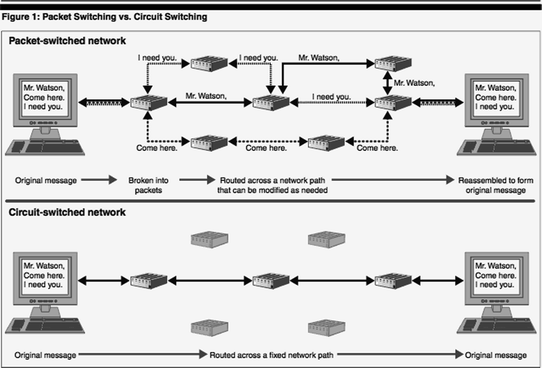
Packet switching versus circuit switching [14]
1.1 Advantages and Disadvantages
Cost saving: Internet calls reduce costs of communication because network infrastructure is used both by data and voice [15]. Cost saving is notable in relation to long distance and international calls. The only fee to charge is an Internet fee. An example of the Virgin Entertainment Group proves this idea and shows a big difference among POT and VoIP: since they switched to VoIP instead of POTS, the cost for long distance calls reduced in $700,000 per year [16].
Additional features: Standard telephone line, as well as mobile communication, cannot even compete with modern VoIP software as the latter offers a huge variety of additional facilities, for instance: video conversation, messaging, number identification, data files transfer during a call, voicemail, identifier of user’s availability (if a user is currently busy or can take a phone)
Security threats: VoIP telephone systems can be attacked by hackers and as a result, calls can be intercepted. Furthermore, confidential information can be stolen if some important services are integrated to the VoIP software. However, it is possible to address to VoIP-ready firewall, which control for risks of IP telephony [17].
Dependence on the Internet: to provide constant availability, it is necessary to maintain constant Internet availability. Furthermore, the quality of calls depends on the quality of internet connection, Internal Network configurations, router [18].
Dependence on power: VoIP phone service, as well as any mobile phone system, needs power supply to function properly.
2 Literature Review
In this part, a short literature review will be presented in which an appearance of the term “IP telephony” in various databases will be inspected.
The sources which have been taken into account were the following: Scopus, Web of Science, Google Scholar, Science Direct, ProQuest, Wiley, IEEE, ACM (Guide to computing literature), EBSCO (Library information science and technology abstracts), Springer.
Firstly, it is important to point out the reasons for choosing the named databases and libraries. The first 3 of them from the list (namely, Scopus, Web of Science and Google Scholar) are known to be major bibliometric databases.
As for Scopus, it currently covers over 69 million of records and over 1.4 billion cited references, including cited references dating back to 1970 [19]. It delivers not only papers on science, engineering, social sciences, but also gives a deep overview of interdisciplinary fields. In addition, it offers powerful tools for sorting and filtering the results by country, document type or research area to get a detailed overview.
Concerning Web of Science (WoS), its coverage goes back to 1900 (for Science Citation Index) [20]. Apart from books, patents and conference proceedings, it indexes approximately 12,000 scientific journals, containing in its’ core collection literature in the art, humanities, sciences and social sciences [20]. Its platform also offers various tools for filtering the results, such as: filtering by year, document type, research area or category.
And finally, Google Scholar—a search engine that indexes scientific and scholarly literature, covering books, academic journals, conference papers, patents and other scholarly literature [21]. Google Scholar does not provide any information on the size of its database, but according to third-party researchers, it contained approximately 160 million documents as of May 2014 [22]. The remaining libraries were chosen because they offer rather rich research databases.
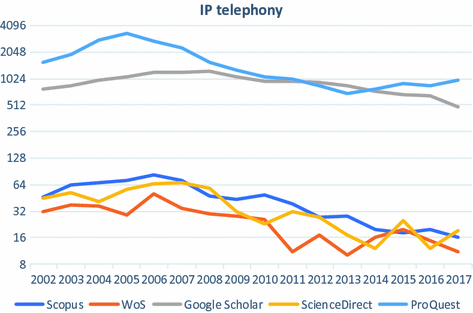
Results for “IP telephony” by year
The most noticeable thing about this chart is that the number of results based on ProQuest is the highest. The number of publications starts to grow considerably and quickly in 2003, reaching the peak in 2005. Afterwards, it immediately started to slump and in 2008 the decline took on a moderate character. After reaching its lowest point in 2013, it started slightly to recover.
As for the results from “Google Scholar”, there are no dramatical ups and downs. The line chart is more or less flat and the highest point (which is honestly not considerably high compared to the remaining results) was in 2008.
The results based on Scopus, Web of Science and ScienceDirect all follow the following pattern: the line started with a gradual growth reaching the highest point in 2006. Afterwards, the number of results stated to decline rapidly and by 2017 the number of results is lower than ever (according to Scopus and Web of Science they keep falling; based on the results of ScienceDirect, there is a slight increase).
In a next step, we are going to inspect the document types which are the most popular with the terms. The results were acquired by filtering the results of databases by category “document type” where it was possible. It came out that 6 databases offer such an option, namely: ScienceDirect, Wiley, Scopus, Web of Science, ProQuest and Springer.
Unfortunately, not all categories of document type had same names (titles) in all named sources. For that reason, it was decided to combine similar categories as they in fact have the same content though are called differently. These combined categories can be recognized by a slash sign (“/”) between document types names.
Another thing concerning merger of different document types into 1 common group, is a combined category called “Miscellaneous”. In this category, we included the following document types: editorial, editorial material, review, conference review, feature, dissertation/thesis. It was done because the numbers in each category were relative low and there was no sense to keep them as separate categories.
As a result, the following categories of document types took shape: “Article/journal”, “Miscellaneous”, “Proceedings paper/conference paper”, “Book chapter/Chapter”, “Research/Market research”, “Book” and “Reference work/Reference Work Entry/Encyclopedia”.
Results for “IP telephony” by document type
SD | Wiley | Scopus | WoS | ProQuest | Springer | Total | % | |
|---|---|---|---|---|---|---|---|---|
Article/journal | 0 | 200 | 317 | 200 | 5866 | 267 | 6850 | 53.4 |
Miscellaneous | 18 | 0 | 77 | 107 | 23 | 0 | 225 | 24.0 |
Research/market research | 356 | 0 | 0 | 0 | 907 | 0 | 1263 | 9.9 |
Proceedings paper/conference paper | 0 | 0 | 413 | 338 | 0 | 418 | 1169 | 9.1 |
Book chapter/chapter | 202 | 0 | 6 | 10 | 0 | 0 | 218 | 1.7 |
Book | 0 | 211 | 0 | 2 | 0 | 0 | 213 | 1.7 |
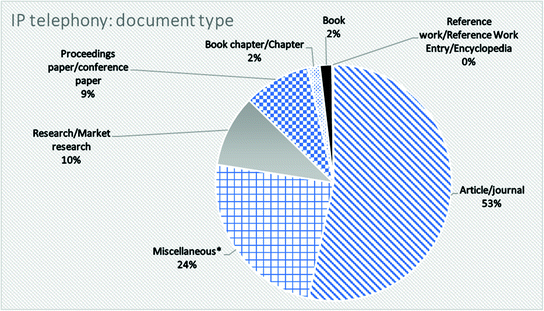
Results for “IP telephony” by document type: pie chart
The chart in Fig. 3 represents document types for a term “IP telephony”. At first glance, it is clear that a category with the most result is “Article/journal” with more than half of total number of results (namely, 53.4%). “Miscellaneous” is again at the second position with almost one quarter of a whole number (24%). The next on the list are document types “Research/Market research” and “Proceedings paper/conference paper” with 9.9 and 9.1% respectively. Categories “Book chapter/Chapter” and “Book” have the same score of 1.7% while a category “Reference work/Reference Work Entry/Encyclopedia” gained less than 1% (0.2%).
3 History and Evolution
According to Joe Hallock, two main technologies that made VoIP communication possible, are telephone and the Internet [12]. It means it is necessary to address to the history of these two great inventions of the humanity to observe the roots of the VoIP technology. The aim of this chapter is to demonstrate the evolution of telecommunication from the beginning until now and to prove that the advances in communication technology have changed the way people communicate in a relative short time. To begin with, as telephone was invented earlier as the Internet, we would like firstly to do a short digression into the 19th century when it all began.
3.1 Telephone
Though the dispute about telephone invention still remains unsettled, a person whose name is often mentioned in a context of a telephone invention is Alexander Graham Bell. Despite all claims and complaints, Alexander Graham Bell was the first inventor to be granted with a U.S. patent for a telephone in 1876 [23]. Originally, he intended to improve telegraph but in 1876 ended up inventing a telephone [24]. The telephone, invented by Bell, was a short-range one [25].
Originally, he wanted to invent an optimized telegraph (so-called “harmonic telegraph”) [26], so that it could transmit multiple messages over a single wire at once [27].
The first versions of a telephone were telegraph-like as there was only one wire both for sending and receiving voice using a single-wire ground return path [28].
The next inconvenience was that users could not speak and listen simultaneously as there was only one opening for sound [29].
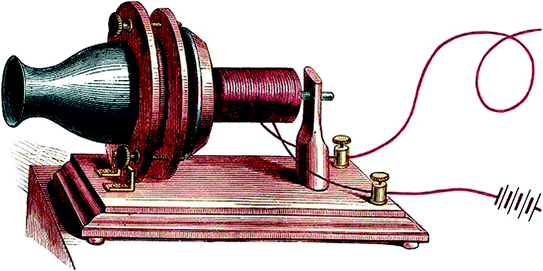
Alexander Graham Bell’s original telephone [30]
First users could use only paired telephones in their own lines till 1889, when an American inventor Almon B. Strowger came up with an idea how to connect one line with up to 100 other lines [31].
At the beginning of the 20th century telephone users could not make long distance calls from their own telephones and had to use a special telephone booth at an arranged time [29].
During the whole 20th century a telephone design stayed unchanged. A rotary dial phone was the most wide-spread one until a new technology—namely a push-button telephone—came into play [32].
3.2 Internet
The next essential component of the VoIP concept is undoubtedly the Internet. The original idea was to create an independent packet switching network for data and information exchange. Its forerunner was called ARPANET (standing for Advanced Research Projects Agency Network) and was created in 1969 [33]. ARPANET was funded by the U.S. Department of Defence and was used for communication purposes within a private network relying on packet switching [34]. It was also claimed that a decentralized model of ARPANET will be robust and resistant enough to withstand in a case of a global war [12].
University of California, Los Angeles (UCLA)
The Augmentation Research Center at Stanford Research Institute (now SRI International)
University of California, Santa Barbara (UCSB)
The University of Utah School of Computing [35]
ARPANET 1974 [37]
Since the first steps were taken, a real revolution has begun. In only several years the Internet has been taken over by commercial Internet providers. Technological revolution including emerging of mobile- and smartphones as well as relative availability of PCs in combination with the Internet have made a communicational breakthrough. Nowadays the Internet is a means for education, business, entertainment as well as communication including chatting, social networks, messengers and VoIP calls.
3.3 Voice Over IP
As the background has been outlined, it is time to observe an evolution of VoIP itself.
It is hard to believe, but in fact a Voice over IP technology will celebrate its 45th birthday in 2018. Though it seems to a be modern way of communication, which is nowadays widely used in communication apps and messengers, it firstly became its shape in 1973 due to Danny Cohen [7], a computer scientist, who developed a protocol to transmit packets with voice on a real time through the network (called ARPANET) [38]. After termination of ARPANET project in 1990, it became a real matter of interest for commerce, involving such technology giants as Microsoft and Intel.
As for the first publicly available Voice over IP application, it was developed in 1995 by a small Israeli telecom provider company called VocalTec, Inc. and was called InternetPhone for voice calls over the Internet. A VoIP audio transceiver was invented and patented by VocalTec co-founders Alon Cohen and Lior Haramaty [39]
Originally, the application could carry out only PC-to-PC voice calls. 3 years later, in 1998, PC-to-phone and even phone-to-phone connections became possible [12]. A microphone, speakers and sound cards were required so that the software functioned properly. As a pioneer, the application was not that flawless as its sound as well as connection quality were relative poor. But on the other side, it has become clear that there was a huge and promising field for investigation and development. In addition, this modern solution did not require any charge even for international calls, what represented a real revolution of those times.
Some years later not only PC-to-phone but even phone-to-phone connections became possible. The first PC-to-phone application was issued by company Net2Phone in 1996 [40]. Though a public switch telephone network and an IP network transmit different types of media, it became possible to establish voice communication between them due to media gateway. According to Search Unified Communications.techtarget.com, a media gateway is “any device…that converts data from the format required for one type of network to the format required for another” [41]. Thus, if one user wants to make a voice call from his phone to his friend’s computer, the sound stream will be converted into packets and transferred over the IP network. Vocaltec, Vienna Systems and Cisco were among those companies which were first to make and use media gateways [40].
Since then the era of digital communication began. Due to new gadgets, devices and technology, which enabled sending and routing VoIP traffic (including media and VoIP gateways), a new way of communication started to expand firstly in the United States and then in other (mainly in European) countries. According to available data, by 1998 Voice over IP traffic made 1% of the whole traffic in the United States. 2 years later, in 2000, the percentage came to roughly 3% of all voice traffic [40] and in 2003 of voice calls expanded considerably and as a result reached 25% of total number of voice traffic [12].
In 2003 a new player—Skype—entered a VoIP market. The next chapter deals with its evolution and features.
4 Skype
Nowadays Skype is widely known all over the world as it connects millions of users every day. According to available data, the number of Skype users reached 660 million worldwide in 2010 [42]. What is more, Skype makes up 13% of world’s total international calls in minutes [43].
Skype web interface [44]
4.1 Skype: Historical Digression
Skype was released in 2003 by a group of Estonian developers as a service for peer-to-peer free Internet calls and later low-cost PC-to-phone calls [47].
The name “Skype” derives from original project’s name “Sky peer-to-peer”, which was later shorted to “Skyper” and then transformed into “Skype” [48].
By the time of its launch, Skype could only make PC-to-PC calls, which were available only for Skype users.
In July 2004, Skype launched “SkypeOut”, which allowed users to call mobile or standard phones all over the world at low cost, charged per minute [49].
In April 2005 Skype extended its offer with another similar concept called “SkypeIn”. It offered users to receive calls from external landlines [43].
In 2005, when eBay acquired Skype [50], videotelephony between Skype users was launched for the 1st time [51].
In 2008, when 35% of users used Skype for business purposes, Skype for SIP, a service for businesses, was launched [52]. This product allowed businesses with SIP phone systems to connect to Skype directly and make low cost international calls [43].
In May 2011, Skype was taken over by Microsoft. Shortly after that, Microsoft began to replace Skype peer-to-peer service by centralized Microsoft Azure cloud computing service. In addition, Microsoft developers adopted Skype app user interface so that instant messages became the main issue of the app, shifting from the idea, that Skype is primarily a VoIP service [53].
Though there are lots of other messengers with the same features of voice and video calls, a VoIP service of Skype has remained the most reliable solution both for private as well as business purposes. Today the application, which can be installed and used both on a PC and a mobile device, offers online messaging (for sending text, images, documents and videos), voice, video calls and additionally video conference calls [54].
4.2 Skype Architecture
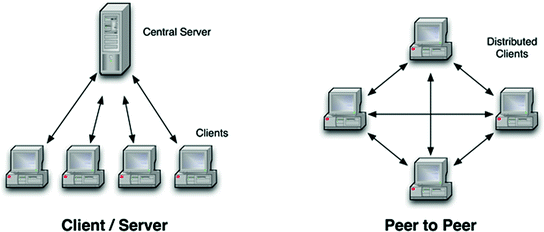
Client server and Peer to peer [56]
As a peer-to-peer system, Skype stores and transmits data over the Internet using devices of its users, which are known as “nodes”. Some of the most suitable nodes (no firewall or operating system restriction, sufficient CPU power, memory etc.) are then selected and used by Skype as “supernodes”, which handle data transmission between Skype users (normal nodes which have firewall restriction, for instance), indexing as well as serve as networking address translation (NAT) nodes [57]. According to Mark Gillett, CVP, Skype Product Engineering & Operations, calls do not pass through supernodes, they just help “normal” nodes find each other [58].
After Microsoft acquisition all supernodes were replaced by servers hosted by Microsoft [58].
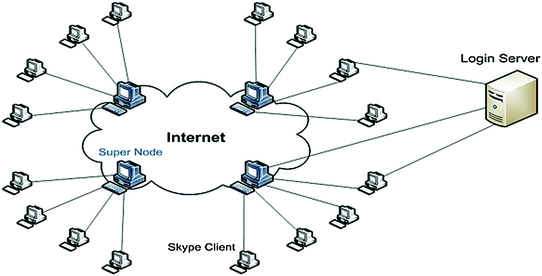
Skype Network [60]
Looking at Fig. 7, it is possible to see that Skype represents a combination of both systems. On one side, nodes can establish connection between each other directly or through “supernodes”. On the other side, there is still a central server that stores account information and contacts.
As it has already been mentioned in the historical part of this chapter, Skype changed from P2P to central cloud computing model. The main issue was model’s inefficiency to handle with a huge (and continuously growing) number of users. Supernodes could not maintain appropriate connection and a diversity of emerging platforms like iOS and Android required a new and a common solution [57].
Due to a cloud infrastructure with dedicated supernodes instead of randomly chosen ordinary users’ PCs, Skype can perform faster and more efficient, especially at large scales. Thanks to cloud server, it became possible to save battery on a device as well as to send messages to users who are currently offline [61]. This happens because cloud storage can hold data when a recipient is unavailable, so that a sender does not need to wait for a peer to show up online [62].
Skype protocol is proprietary. According to PCmag, a proprietary protocol is “a non-standard communications format and language owned by a single organization or individual” [63]. Moreover, protocol’s specifications are openly unavailable. Skype software is closed-source as well [64], what means that software developers retain property rights for it [65]. In other words, the software cannot be reviewed by anyone who is not its developer and users have to rely on developers when it comes to security [66].
Skype’s compatibility with many other VoIP systems is impossible without Skype license [67].
In 2014 Microsoft replaced former Skype protocol with MSNP24 [68].
Concerning, calls to landline and mobile phones, they are not encrypted.
Concerning security, Skype is not really a safe way to transmit sensitive information. According to the Guardian, calls over Skype network are not affected by end-to-end encryption. It allows third parties like Microsoft as well as government to intercept and wiretap calls easily [69]. When end-to-end encrypted, all sent data get encrypted on sender’s system and only an addressee can decrypt it [70].
Nevertheless, Skype-to-Skype communication (voice, video, files, instant messages) is protected by client server encryption, which uses public key, which is less secure compared with end-to-end encryption [71]. But if Skype user makes calls over PSTN (to mobile or landline phones), they will not pass through encryption [72].
5 WhatsApp
Similarly, to Skype, Whatsapp is considered to be a pioneer in its branch—mobile messaging. Opposed to Skype, its main function is not VoIP calls, though it offers this service as well.
Whatsapp mobile interface [73]
In contrast to Skype, all data, transmitted through Whatsapp, pass through end-to-end encryption. It secures, that nobody except a user and his recipient, can access and read sent information. According to Whatsapp official website, due to end-to-end encryption, each message is protected with an individual lock and it is only a recipient device which owns a special key to unlock the message [74].
Opposed to Skype proprietary protocol, Whatsapp is an open encryption protocol Signal [66]. Though Whatsapp encryption protocol is an open standard, the application itself is closed source. Moreover, an open source software can be reviewed to verify the presence of malware (malicious code). Closed source (proprietary) software, like Skype, on the contrary, does not allow anyone to get in and thus users have to trust the developers unconditionally [66] It means, the other application parts except its protocol, are not available for others and it is impossible to verify other issues which can influence the security (as encryption is not the only factor which is responsible for security) [66].
Moreover, its client software is available for Android, iOS, Windows Phone, BlackBerry OS, Symbian [75].
5.1 WhatsApp: History
The story of Whatsapp took its roots back in 2009, when former Yahoo employees Brian Acton and Jan Koum decided to create a messaging app, inspired by iPhone’s App Store and strongly believing, that such an app would be a real breakthrough [75]
At first, the main concept of Whatsapp was different as it was not intended to develop a messenger, rather than a status indicator, which would inform all contacts about user’s availability for a call. This is how Whatsapp functioned by the time of its 1st release. Shortly after that, Apple launched push notifications and this made Jan Koum rethink the whole concept of his development. The main pillars, on which new Whatsapp would rest, were: compatibility with multiple platforms (cross-platform), easiness of logging in (mobile phone number as a login) and user’s phone contact folder as a base for potential Whatsapp contacts. According to Jan Koum, he wanted to develop an app which would be easy in use and would “just work” [76].
Already in the year of its release, 2009, the function of picture messaging (sending photos) was added [75].
In 2013 voice messages were introduced [77].
Further important milestone of Whatsapp history is Facebook acquisition in 2014 [78].
In July 2017, the number of Whatsapp users reached 1300 million, making Whatsapp the most popular messaging app in the world of all the time [79].
In 2015 Whatsapp Web was launched, enabling users to stay connected using a PC, syncing with a device [80].
Furthermore, in 2015 Whatsapp started offering VoIP service—a function of making voice calls since then was available for Whatsapp users [81].
In March 2016, WhatsApp introduces its document-sharing feature, initially allowing users to share PDF files with their contacts [82].
In 2016 Whatsapp stops charging annual fee in the amount of 99 cent (1st year of usage was free). Instead of charging a fee, Whatsapp owners intended to develop a service for businesses to create a revenue from this offer [83]. In February 2016, Whatsapp hits another strike with 900 million users, remaining the most popular messaging app at the time [84].
Additionally, in 2016 video calls became available to Whatsapp users [85].
5.2 WhatsApp: Encryption and Server
As it has already been mentioned, Whatsapp uses end-to-end encryption. Concerning system, opposed to Skype, Whatsapp has a client server system. The latter means, that all messages and data sent through Whatsapp have to pass through the server and are not directly sent from user to user, as Skype system does [86].
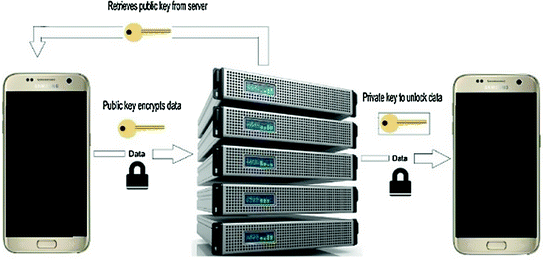
End-to-end encryption [87]
Before sending a message to B, A requests a public key which applies for B by a central Whatsapp server. To encrypt his message, A uses a public key. Afterwards, the message goes from A to the server. Then the server directs the encrypted message to B. To decrypt a received message, B uses his private key, which is available only on B’s device and which B receives from the server [86].
All in all, Whatsapp is a safe and secure solution for sending sensitive data: if messages are once intercepted, it still will be almost impossible to read them as the private key to encrypt them is stored on a recipient device. In addition, Whatsapp regularly changes key, so if someone steals user’s keys, he will be able to encrypt only a fraction of user’s messages-the whole part will still be unavailable [89].
6 Comparison of Applications
It is time, at last, to review some more other application and software to see what specific features they can offer and mark both advantages and disadvantages of each of them. After a brief review, a comparative matrix with the main characteristics for each program will be provided.
6.1 Viber
Viber [93]
Concerning price, Viber is free. Additionally, it offers landline-calls or calls to mobile phones with a help of its’ paid service called “Viber Out” with a price starting at 1.9 cents/minute, depending on a country. Viber users call each other for free [94].
As for its Voice over IP feature, voice calls over Viber are available only to iPhone, Android, Microsoft’s Windows Phone and from a desktop [95].
Viber allows users to link one account with multiple devices.
Concerning the PC version (desktop application), it syncs all contacts and a record of calls from the phone account automatically [96].
Moreover, it offers push notifications and enables to create chats with up to 100 participants [97].
The app is convenient to sign in, as no usernames and passwords are required. Users need only a mobile number for verification [98]. In addition, communication over Viber is rather secure, as end-to-end encryption is used to protect VoIP calls, video calls, text and files. Thus, Viber has the same architecture as Whatsapp: all messages and calls pass through Viber server. Before establishing a connection, user A requests public key by Viber server, sends a message to B through the server, the server directs the encrypted message to B, which decrypts it with its private key [99].
6.2 Telegram

Telegram [101]
According to the data available in February 2016, the number of active monthly users reached 100 million [102].
Each account is linked with a phone number of a user and it is possible to link multiple devices to one account. Moreover, it is possible to change an active number any time. Like in almost every messenger, both text and multimedia messages can be sent and groups can be formed with up to 5000 participants [103].
One of the most rare and useful feature of Telegram is that it is possible to delete mistakenly sent messages on both sides within 48 h [104].
Telegram is considered to be secure as well, as it uses end-to-end encryption [105].
Concerning architecture, Telegram is a mixture of peer-to-peer and client server systems. If it is possible, peer-to-peer connection will be established. If not, Telegram servers will establish connection among users [105].
6.3 Facebook Messenger

Facebook [108]
As a usual standard messenger, it offers text and voice messages, voice and video calls as well as file exchange and even playing games [109].
To log in a user needs to have a Facebook account and it is possible to use one account from multiple devices.
According to Techcrunch, Facebook messenger reached 1.2 billion users in April 2017 [110].
Moreover, Facebook Messenger offers end-to-end encryption [111, 112].
6.4 Google Hangouts

Google Hangouts [114]
The main advantages are: the program is free and every Android user has automatically a Google account, so he can easily use Google Hangouts without any additional registrations and passwords.
It is applicable for Mac OS X, Windows, Chrome, Ubuntu and other Debian-based Linux distributions [115].
Google Hangout uses peer-to-peer connection. If it is not possible, it switches to client server model [116].
Google Hangouts does not use end-to-end communication, though sent data are encrypted “in transit”. Thus, Google has a full access to text, photos, voice and video conversations [117]. In addition, Google Hangouts users can make calls to mobile and domestic phone numbers [118].
To sign in, user can use their Google+ account [119].
6.5 Comparison Matrix
Comparison matrix
Operating system | License | Cost | Price inside network | Calls to mobile/PSTN | Encryption | Features | Protocol | |
|---|---|---|---|---|---|---|---|---|
Google Hangouts | Mac OS X, Windows, Chrome, Ubuntu and other Debian-based Linux distributions [115] | Proprietary [92] | Free | Free | Yes; PSTN, mobile | SRTP3 (Secure real-time transition protocol) | Text, voice, video, screen sharing [71] | Open: XMPP (Extensible messaging and presence protocol) [92] |
Facebook Messenger | iOS, Android 6; PC version [106] | Proprtetary [71] | Free | Free | No | End-to-end | Text, voice, video [71] | Open; MQTT (Message queue telemetry transport) [112] |
Telegram | Android iOS WD, Microsoft OS, Windows, Mac, Linux, macOS, web version, Chrome app [100] | Proprietary [71] | Ftee | Free | Yes; PSTN, mobile | End-to-end | Text, voice, video [71] | Proprietary [92] |
Viber | Windows, macOS, Linux, Android, iOS, Windows Phone, Win 10 Mobile, Bada, BlackBerry OS, Series 40, Symbian [92] | Proprietary [92] | Free | free | Yes | End-to-end | Text, voice, video [71] | Unknown [92] |
Android, iOS, Windows Phone, BlackBerryOS, Symbian [75] | Proprietary [71] | Ftee | Free | No | End-to-end | Text voice, video [71] | Open:XMPP (Extensible messaging and presence protocol) [92] | |
Skype | Windows, macOS, Linux, Android, iOS, Windows mobile, BlackBery, HoloLens, XboxOne Amazon Kindle Fire HD X, Amazon FireHD [45, 46] | Proprietary [92] | Free | Free | Yes; PSTN, mobile | Client saver | Text, voice, video, P2P extension (games) [71] | Proprietary P2P [92] |