12
Online Crimes: Scams, Fraud and Illegal Downloads
I am writing you this mail from my father’s home at … London believing that you will be of tremendous help in my effort to save the last of my family legacy. I choose to reach you through this medium because it is the fastest and most reliable way of communication, as I wish to solicit for your unflinching support and cooperation.
My name is Mr. West Alamieyeseigha, the heir to the Alamieyeseigha’s family. My family’s ordeal started sometime last year when my father, then the Governor of Bayelsa state in Southern Nigeria was at loggerhead with the Federal Government following his campaign against the insensitivity of the government to the plight of the Niger delta region, the region that produces the country crude oil – the major foreign exchange earner of my country. Shortly before his arrest in London UK, my father had series of meeting with the federal authorities part of which was aimed at getting him drop his campaign for true federalism and resource control but he turned down all the juicy promises that was offered him hence the plan to get him set up. He was arrested and detained in London last year. Somewhere along the line, he escaped to his State Bayelsa but not without the collaboration of the UK authorities who claimed he jumped bail. My ill mother of 50, Mrs. Margaret Alamieyeseigha was also humiliated in London and charged for money laundry offences.
I am certain you know much about this case however, you can make further enquiries. However, my reason for contacting you is to solicit your support and collaboration in securing my family legacy. I am contacting you on the instructions of my mother who asked me to seek for a reliable foreigner who will help us invest some of the undetected fund belonging to my father kept in private safes worth over $20,000,000.00. I shall provide you with details of how to access the money if you provide me with investment information in your country. For this Information and your collaboration, 30% of the entire money will be your reward for your assistance.
I shall detail you further when you indicate interest to help us. Meanwhile you may reach me on … (Example of a Nigerian email scam; Whitty & Joinson, 2009, p. 57–58)
In Chapter 11 we looked at online deception, focusing predominantly on everyday deception while pointing out the importance of distinguishing between lies told in everyday conversation and those told for the purpose of engaging in criminal activities. This chapter focuses on deception that criminals engage in online as well as the reasons why some people are tricked by this deception. In particular, we will focus on phishing, MMF and illegal downloads of online material, such as music and videos.
12.1 PHISHING
Phishing is the use of social engineering and technical subterfuge to trick individuals into giving up personal and financial information in order to fraudulently access a person’s real account. This usually begins with an email message purportedly from a well‐known and trustworthy organization (e.g., PayPal, eBay, a well‐known bank) that requests the user to validate their information by logging on to the organization’s website. However, the link provided does not lead to the official website – instead it directs the user to a mock‐up. Similar messages can also appear on social media, such as Facebook. Technical subterfuge schemes plant crimeware onto users’ computers to steal credentials from the user’s system, by intercepting the user’s online account usernames and passwords or by corrupting local navigational infrastructures to misdirect consumers to counterfeit websites (Anti‐Phishing Working Group, 2014). Given that these attacks are sent out en masse, the term ‘phishing’ has been employed to describe this type of attack, as it is like a fishing expedition where the criminal puts a lure out hoping to fool at least a few of the prey that encounter the bait. An example of what a phishing email might look like can be seen in Figure 12.1. As the illustration shows, if the user examines the weblink, they will realize that the real website address reads nothing like a Nationwide authentic website.
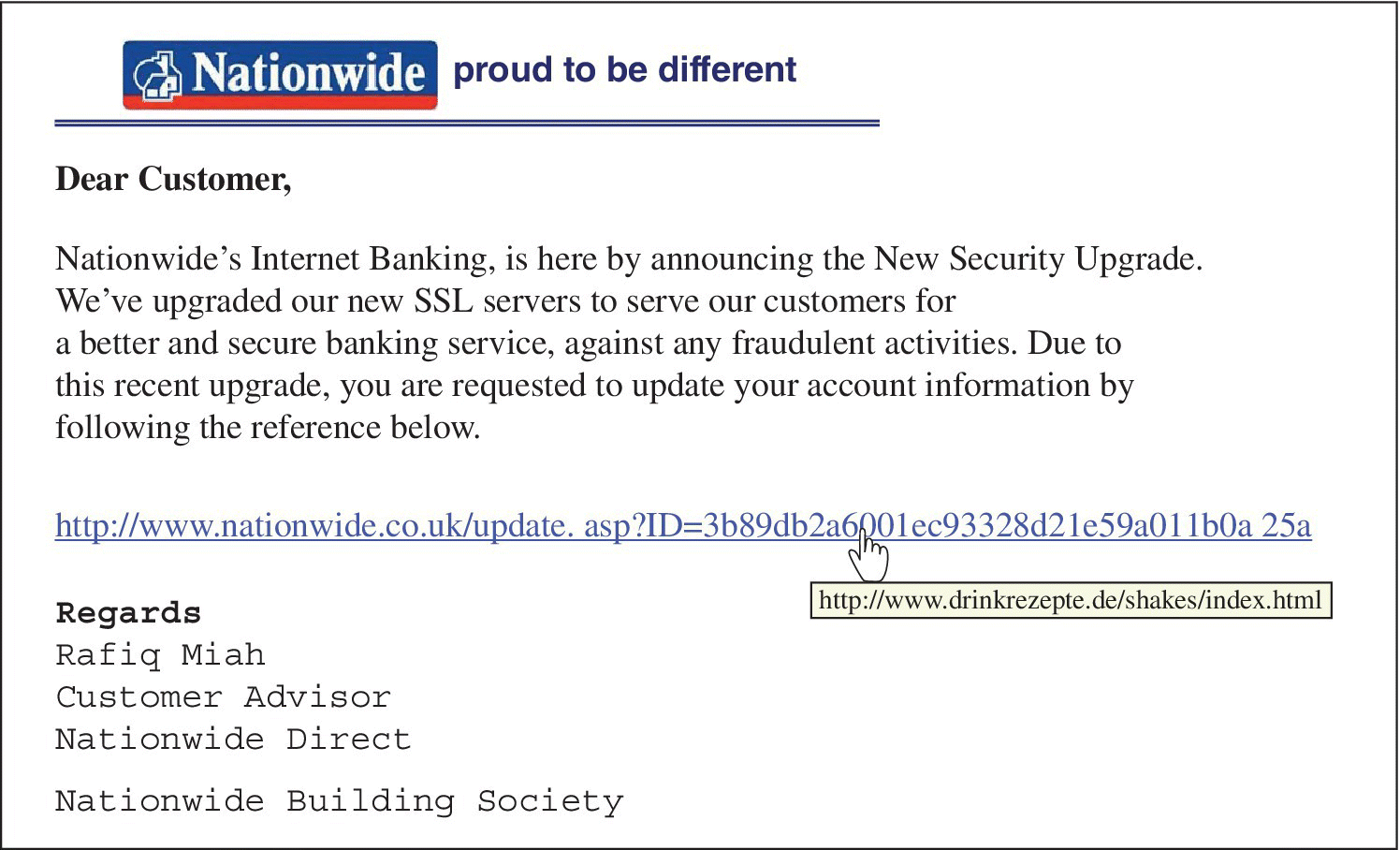
Figure 12.1 Example of a phishing email
The Anti‐Phishing Working Group identified 17,320 unique phishing websites in December 2014. It also identified that 300 brands were targeted by phishing campaigns in December 2014. Examining a breakdown of the most‐targeted industry sectors in December 2014, it found that retail services were the highest targeted industry (29.4%) followed by payment services (25.1%) and financial services (20.8%). Due to improved detection techniques, about half of phishing sites are shut down within a day (Rao, 2015). Nonetheless, the numbers that are in existence on a daily basis illustrate that these sites are still a problem that requires improved methods to detect and prevent. Moreover, their existence demonstrates that criminals, at least, perceive them as a successful method of defrauding victims.
In addition to phishing, readers might be aware of ‘spear phishing’, which is similar to phishing but, instead of a random hack, there is a specific target. As with phishing, spear phishing messages appear to come from a trusted source. However, unlike phishing, spear phishing attacks use specific knowledge about individuals and organizations. Hong (2012) gives the example of an attack on military personnel, which might contain an invitation to a general’s retirement party, asking the recipient to click on a link to confirm that they can attend. Therefore, individuals might be more likely to respond to a spear phishing attack compared with an ordinary phishing attack, given that it appears to come from a known source.
12.2 VISHING
Individuals continue to be confronted by new scams, and criminals persist in finding new ways to use media to convince potential victims that they are genuine. Vishing, for instance, is the use of the telephone by criminals in an attempt to scam users into disclosing private information that will be used in identity theft. The scammer typically pretends to be a legitimate business (e.g., a bank) and tricks the victim into believing that they are requesting personal information for legitimate reasons. In other versions, the criminal asks the victim to enter personal details into a website or convinces the victim to transfer their money into another account, persuading them that it is to protect their finances when, in reality, these are the accounts of money mules.
12.2.1 Number of victims
Despite the number of awareness campaigns and training workshops that organizations make available to end users, many individuals fall victim to phishing attacks. In a report conducted in 2015, Get Cyber Safe, which is sponsored by the Canadian government, estimates that about 10% of Canadians who click on a phishing link fall for the scam, which is about 800,000 individuals (Get Cyber Safe, 2015). A report compiled by Verizon in the UK claims that in 2014 about 25% of employees were likely to open a phishing email (BBC News, 2015).
12.3 WHY ARE PEOPLE TRICKED BY PHISHING?
Some researchers have examined the reasons why victims believe phishing emails are genuine. In research conducted by Wang, Herath, Chen, Vishwanath and Rao (2012), participants were presented with an image of a ‘real’ phishing email with the subject title ‘UPGRADE YOUR EMAIL ACCOUNT NOW’. The email asked recipients for their username, their password, their date of birth, a security question and an answer. Recipients were also told that they would lose their email accounts if they did not send the requested information within seven days. Participants were not informed that this was a phishing email but were asked how likely they were to respond to the email and were asked a series of questions devised to help the researchers develop a theoretical model to predict which users are more likely to respond to phishing emails. They found that attention to visceral triggers, such as stressing the urgency to respond, increased the likelihood of responses, while attention to phishing deception indicators (such as grammar errors and the sender’s address) decreased the likelihood of responses. Interestingly, these researchers found that the cognitive effort expended in processing the phishing email was not significantly related to the likelihood of responding to the email.
Alsharnouby, Alaca and Chiasson (2015) carried out experimental research asking participants to consider a series of websites (14 phishing and 11 genuine) to help understand why users are tricked by phishing scams. Participants were required to view each of the websites and were asked to determine whether each website was legitimate or fraudulent, their level of certainty, and how they arrived at their decision. In addition, participants were required to wear an eye‐tracker device, which recorded their eye gaze data while they viewed the websites. These researchers found that the longer the participants spent looking at the security indicators in the browser Chrome, the more likely they were to notice the security indicators – although they note that this was not a strong effect.
In some noteworthy research carried out by Vishwanath (2015a), the relationships between Facebook use and vulnerability to phishing attacks was examined. Vishwanath points out that attempted phishing attacks that take place via social media, such as Facebook, are much more likely to be successful compared with email phishing attacks. He also argues that the reason for this success rate is that social media’s interfaces, functionalities and user protections are constantly changing, making it difficult for users to achieve a degree of mastery over the use of the platform. Phishing attacks via social media take place in two stages. The first stage requires the user to accept a friend request that, when accepted, has the potential to provide the criminal with a wealth of data about the user. In the second stage of the attack, the criminal can use the messaging aspect of social media (such as Facebook’s Messenger) to request information directly from the user. Vishwanath gives the example that the knowledge that someone is a dog lover could be used to then request a donation to a dog charity via Messenger, when in reality the victim is clicking on a link with hidden scripts and viruses that could infect the device used to access the message. The message from this study was that habitual Facebook use (including frequency of using Facebook and maintaining a large social network) and being unable to regulate these behaviours were the biggest predictors of individual victimization in social media attacks.
Although Vishwanath (2015b) acknowledges that social media phishing is more likely to be successful at scamming victims than email phishing, he has nonetheless been interested in learning more about the sort of person who tends to be susceptible to email phishing attacks. In this particular study (Vishwanath, 2015a), he sent a sample of students (200 out of 400, with 192 valid responses) enrolled in an undergraduate degree a phishing email, which contained a warning about email account closure and a tight deadline to click on a hyperlink to prevent the closure of the email account. The hyperlink was hidden using a shortened URL. Those who had not clicked on the link were sent a reminder a week later. Overall, 83% of the participants (n = 159) clicked on the hyperlink. Vishwanath argued that the joint influence of email habit strength (i.e., whether individuals automatically respond to receiving an email) and of cognitive processing predict susceptibility to phishing attacks. He also hypothesized that the personality traits of conscientiousness and neuroticism influence email habits. As predicted, it was found that those who scored high on conscientiousness and high on neuroticism were more likely to report safe email habits. Vishwanath found that individuals who checked their emails more habitually had increased chances of victimization. He also found that heuristic processing, also referred to as ‘cognitive shortcuts’, significantly increased the chances of victimization (e.g., the email might appear to come from a credible source, such as the student’s university) and that systematic processing (a detailed assessment of the content of the communication) significantly decreased the chances of victimization. Email habits, however, were found to be the strongest predictors of victimization, suggesting that prevention needs to focus on changing habits in order to reduce susceptibility.
12.4 IMPROVING DETECTION
Understandably, detection software as well as training programmes to help the user recognize phishing emails have been developed to help reduce the number of people who fall victim to phishing emails, as well as to help protect organizations from the harm caused by employees who click on such emails. Jansson and von Solms (2013), for instance, have provided training to individuals who in the past responded to a solicited phishing email to determine whether their training programme was effective. After participants clicked on a link from a phishing email, their computers showed a red warning screen, alerting them to their ‘insecure’ behaviour, together with an email message making them aware of their ‘insecure’ behaviour. In addition, the email provided a hyperlink inviting them to participate in an online training programme. After engaging with the programme, the participant’s likelihood of being attacked again was evaluated via a short set of questions asking about their understanding of security. The researchers argue that their findings show that being exposed to simulating phishing attacks, together with embedded training, can increase resilience in responding to phishing attacks; notably, however, this study did not employ randomized control groups.
In an earlier study, Davinson and Sillence (2010) developed a training programme that informed users about the common types of phishing attacks and how to identify them. In this study, participants were randomly assigned to one of four conditions: group 1 were told they were at low risk and did not complete training; group 2 were told they were at low risk and received training; group 3 were told they were at high risk and received no training; and group 4 were told they were at high risk and received training. The training programme involved an interactive game that trained the user to defend themselves against phishing attacks. They found that an apparently tailored risk message increased participants’ intentions to act in a secure manner regardless of whether they were told they were at high or low risk. Raising awareness of risk, however, did not appear to increase secure behaviour. In addition, the researchers found that the training programme did not influence secure behaviour seven days after the training. The research stresses the importance of evaluating training programmes and highlights the need to develop more effective training programmes.
12.5 MASS‐MARKETING FRAUD
Fraud can be broadly defined as trickery used to gain a dishonest advantage, which is often financial, over another person or organization. Mass‐marketing fraud is a type of fraud that exploits mass communication techniques (e.g., email, instant messaging, bulk mailing, SNSs) to con people out of money. It is believed that the money criminals acquire from this crime is often used for more sinister crimes (e.g., drug trafficking, terrorism).
This chapter began by presenting an example of a Nigerian email scam, a MMF presumably known by most readers. This scam is also known as the ‘advance fee fraud’ or the ‘419 scam’ (so named because of the section number of Nigerian criminal law that applies to it) and actually began as a postal mail scam. In most cases, the mail appears to be sent from an African country and/or an individual who is typically Nigerian, although others are sent from other African countries and in recent years from Asia and Eastern European countries. Advance fee frauds often refer to a large amount of funds that are trapped or frozen for a variety of reasons (e.g., unclaimed estate, corrupt executive, dying samaritan). In each case the sender offers the recipient rich rewards for simply helping government officials or family members out of an embarrassing or legal problem. Those who respond to such emails (and surprisingly there have been a number of people conned) then gradually experience problems with the financial transaction. Initially, the paperwork is said to be delayed, then excuses are given for why more money is needed – for example, to bribe officials. The money asked seems insignificant in light of the huge windfall the recipient will ultimately gain. Delays continue and more financial support is asked of the recipient. It becomes more difficult for them to refuse, given that they have already invested a significant amount of their own money into the deal. The scam only ends when the victim has learnt and accepted that they have been conned, and that it is highly unlikely that they will ever see their money again or that the criminal will be caught and arrested.
The Internet has opened up the floodgates to MMF given that criminals can use it to target many more potential victims with very marginal effort, to trick them into making electronic and even crypto‐currency transfers on the basis of mistaken charity, investment or love. This crime can also have an impact on the digital economy, as citizens start to mistrust particular online sites that criminals use to target individuals. Banks and money transfer organizations have the problem of dealing with fraudulent transactions affecting not only their own trade but also the lives of their customers, to some extent irrespective of whether the customers were actually negligent or complicit.
Some MMFs are low‐value, one‐off scams of a large number of victims, while others involve developing a relationship (e.g., romantic, business, friendship) where money is defrauded over time, again with multiple simultaneous or sequential victims. Examples of MMF include:
- Boiler room scam/investment scam: This scam, like the classic 419 scam, cons victims into believing they will make large sums of money, very quickly. The criminal contacts the victim, offering worthless, overpriced or non‐existent shares. The motivation for the victim is to make a large profit.
- Online dating romance scam: In this crime, criminals pretend to initiate a romantic relationship through online dating sites and then defraud their victims, often of large sums of money. The motivation of this scam for victims is to develop a long‐term committed relationship. Since about June 2012, the scam has moved on to include another variation, whereby victims who meet the criminal on an adult dating website (set up to cheat on their partner) are videoed performing sexual acts and later blackmailed (a threat is made to send the video to loved ones and places of work).
- Charity scam: The charity scam involves a criminal scamming money for what appears to be a genuine charity. Scammers either pose as agents of legitimate, well‐known charities or create their own charity name. Criminals set up false websites to look similar to those operated by real charities. These scams do not necessarily involve one‐off payments and can con victims over a long period of time. The motivation of this scam for victims is to give money to others, rather than a hope to gain profits for themselves.
- Emergency scam: In this scam, real details about a person have been garnered from the Internet (e.g., through Facebook) and one or more of the people on an individual’s contact list is contacted to say that the individual is in trouble and needs money immediately (e.g., has been in a car accident or is in trouble in a foreign country). Unlike the boiler room and the romance scams, this scam works rapidly. The motivation is to help a loved one in need.
- Inheritance scam: In this scam, a criminal posing as a lawyer tells victims that a rich person who shares the victim’s family name or a name very similar has died and that, unless the lawyer can identify any of the person’s relatives, the money will go to the government. The lawyer imposter suggests that, given the victim shares a similar name, the lawyer could pay the money to the victim and split the money, rather than handing it over to the government. Like other advance fee frauds, victims are asked to pay fees, such as taxes and legal fees, in order to release the funds. This can be a difficult scam to detect because legitimate companies do exist that make a living from tracking down heirs. Some victims of this crime may believe that they are not entirely acting within the law.
Reports suggest that significant proportions of individuals have been affected by MMF – either as victims themselves or as the loved one of a victim. The National Fraud Authority (2012) in the UK has estimated that fraud costs in the UK equate to over £78 billion a year, with £3.5 billion lost to MMF alone in 2011. The National Fraud Authority conducted a nationally representative study of more than 4,000 UK adults and found that, in 2011, 1 million UK adults (just under 2%) sent money in reply to unsolicited communications, with just under half of them being defrauded as a result. They also found that three quarters of UK adults (37 million people) received unsolicited communications in 2011 (the majority by email). Similarly, in a representative sample of 2,000 UK adults, Whitty (2013a) found that in 2012 approximately 800,000 adults were defrauded by MMF in the UK. In 2010, the UK Office of Fair Trading reported that ‘just under half of UK adults are targeted by scams, and eight per cent will be a victim at least once in their lifetime’ (p. 1). Whitty and Buchanan (2012) found from a representative UK sample that at least 230,000 individuals had been scammed by the online dating romance scam. As these statistics indicate, the financial costs of MMF are serious. The financial costs are not just to victims, their family and friends but also include the costs to law enforcement as well as those to social and health support services.
Mass‐marketing frauds are believed to be underreported, due to the embarrassment and shame experienced by victims, the lack of hope that criminals will be caught and the fear that law enforcement will not treat the crime with the seriousness it warrants. Reporting bodies in the UK, such as Action Fraud, estimate that less than 10% of victims actually report this type of crime. In the US, according to the Internet Crime Complaint Center (IC3) in 2014, 123,684 victims reported to that body financial losses as a result of Internet crimes, many of which were MMFs. It is estimated that only 10% of victims report the crime to IC3. In Australia, just over AUS$94 million was reported lost by victims of MMF in 2012 (Australian Competition & Consumer Commission, 2012).
Victims of MMF suffer both financial loses and psychological impacts, with psychological effects sometimes outweighing the financial impact, even when large sums of money are lost (Button, Lewis & Tapley, 2014; Lea, Fischer & Evans, 2009a; Levi & Burrows, 2008; Whitty, 2015; Whitty & Buchanan, 2016). Psychological harm can include shame, guilt, embarrassment, depression, feeling suicidal, grief, anxiety and loss of trust. Moreover, victims often lack the support offered to victims of other types of crime (e.g., family, friends) due to a lack of understanding of the crime and because victims are often blamed for their situation. Some victims have been known to move on to commit criminal acts, such as working as ‘money mules’ for fraudsters, sometimes unwittingly and sometimes to recoup their losses.
Catching and prosecuting MMF criminals is a difficult task. This is the case for three main reasons: (1) the criminals often live in a different country from the victims, (2) the methods the criminals use make them difficult to trace, and (3) prosecution is very time consuming, owing to the large amounts of online data that need to be analysed to establish evidence against the criminals and gain intelligence about their whereabouts and operating tactics. Given these factors, novel strategies are needed to prevent and detect this crime. Dating sites, for instance, have been asked to share known fake profiles in order to help reduce the number of criminal profiles (created for the romance scam). Facebook has attempted to take down known fake profiles (which criminals create to enable a number of different types of MMFs). Anti‐money‐laundering regulations increase the identifiability of transactions and recipients when money is transferred via money transfer companies, such as Western Union and MoneyGram.
12.6 AWARENESS CAMPAIGNS
Similar to prevention strategies for phishing scams, various awareness campaigns have been devised to help prevent MMF. There are numerous websites and phone apps available that attempt to educate users about scams in an attempt to prevent victimization arising from MMF. These campaigns typically suggest basic rules such as never click on a link in an email; never respond to an email asking for confirmation of your banking details; and never send any money to strangers you meet online. As demonstrated earlier in this chapter when discussing training programmes developed to prevent phishing scams, warnings about online security often focus exclusively on idealized individual behaviour and assume that people fall for scams because they lack knowledge. One of the problems with this approach, at least for MMFs, is that many victims of MMF have heard of these scams prior to becoming defrauded. Lea et al. (2009a) have argued that detailed knowledge of a scam increases vulnerability, as these individuals often develop an ‘illusion of invulnerability’. It has been found that, even when authority figures (e.g., police, law enforcement, bank managers) attempt to alert a person to the fact that they have become a victim of a romance scam, the victim often has difficulty believing them. Moreover, even when the victim questions the criminal about their authenticity, the criminal will employ persuasive techniques to convince the victim (Whitty, 2015). The number of repeat victims also suggests that this is a difficult population to help to recognize scams. Given that knowledge about a scam, therefore, may not be enough to prevent individuals from becoming defrauded, other types of interventions are needed. In order to help devise effective campaigns to prevent individuals from becoming defrauded as a result of MMFs, it is important to understand the reasons why individuals are tricked. As a way of assisting with prevention and detection, researchers have, for example, examined how individuals cognitively process information when presented with a scam, the sorts of individuals who are more likely to be conned and the stages involved in scams.
12.7 COGNITIVE AND MOTIVATIONAL ERRORS
It has been argued that ‘falling for a scam comes down to errors in decision‐making’ and that ‘scammers create situations (with their scam offers) that increase the likelihood of poor decision‐making’ (Lea et al., 2009a, p. 35). Cognitive (e.g., overconfidence in a specific topic) and motivational (e.g., the scam triggers positive emotions) processes also explain the psychological reasons why people respond to scams. The main reasons include ‘appeals to trust and authority’ (i.e., the use of people or institutions of authority to make the scam appear legitimate) and ‘visceral triggers’ (triggers employed to make potential victims focus on huge prizes and imagined positive future emotional states). Another error victims frequently make is the belief that they are acting according to the social norm. Norms ‘can be seen as rules of thumb based on social knowledge: they tell us how we “ought” to choose, and furthermore how people are likely to choose’ (Lea, Fischer & Evans, 2009b, p. 25). A comprehensive list of the common errors Lea et al. (2009a) believe victims of MMF fall for is summarized in Table 12.1.
Table 12.1 Errors in decision‐making with respect to scams (identified by Lea et al. 2009a, p. 24)
| Motivational | Cognitive |
|
Visceral influences Reduced motivation for information processing Preference for confirmation Lack of self‐control Mood regulation and phantom fixation Sensation seeking Liking and similarity Reciprocation Commitment and consistency |
Reduced cognitive abilities Positive illusions Background knowledge and overconfidence Norm activation Authority Social proof Altercasting |
12.8 WHAT TYPE OF PERSON TENDS TO BE SUSCEPTIBLE TO MMF?
In addition to considering cognitive processes, researchers have examined the types of individuals who tend to be susceptible to MMFs. Furnell (2005) argued that greedy and naive individuals are more likely to be conned. Lee and Soberon‐Ferrer (2005) found that victims of fraud tend to be older, poorer, less educated and single. Holtfreter, Reisig and Pratt (2008) looked broadly at ‘consumer fraud’ victimization and found that fraud victims were more likely to have low self‐control. Buchanan and Whitty (2014), in contrast, found that those high in sensation seeking were not more likely to be scammed by the online dating romance scam. Instead, they found that high scores on the romantic belief of ‘idealization’ were associated with the likelihood of being a victim. There may be a generic typology for scam victims; however, given the distinctive nature of some of these scams (e.g., the emergency scam requires an immediate response; the romance scam usually takes several months before victims are defrauded), there might be specific risk factors depending on the type of scam. Understanding the sorts of people who are susceptible to online MMFs and the sorts of scams certain individuals are more susceptible to could be advantageous for prevention, as knowing who is more likely to be a victim of these crimes can help with tailoring the right message to the relevant people.
12.8.1 The role of the Internet
Very few studies have considered the role the Internet might play in persuading individuals to part with their money. Given that the Internet usually plays a role in the initiation or implementation of MMFs, an examination of the potential influence of communication via this medium could help to elucidate new ways to prevent these crimes. In Chapter 3 we summarized Walther’s hyperpersonal theory. This theory has been further drawn upon by Whitty (2013b) to examine the online dating romance scam. She argues that in this particular scam a one‐sided, ‘hyperpersonal’ relationship develops between the victim and the scammer. According to Whitty, victims idealize the fake persona, believing they have found the perfect romantic partner. Whitty elaborates on the role the Internet has to play in this scam in her stage model (described in the next section). Further research might focus more on how certain features of media might be used by criminals to scam victims of MMF.
12.9 STAGES INVOLVED IN THE ONLINE DATING ROMANCE SCAM
Considering scams as a series of stages might provide a useful method to enable individuals to gain insights into the anatomy of these scams. Research has found that the online dating romance scam progresses over a number of stages and that various media are used by criminals to persuade victims to part with their money (Whitty, 2013b). The stages identified are as follows:
- Stage 1: potential victims need to be motivated to find the ‘ideal partner’.
- Stage 2: potential victims are presented with an ideal profile and given the promise of exclusivity by the scammer.
- Stage 3: potential victims are groomed by the criminal to gain trust and love and the criminal tests the waters to gauge whether the potential victim might be ready and willing to part with their money.
- Stage 4: the criminal employs techniques to persuade the potential victim to send money (e.g., a narrative about a crisis where money is urgently needed or the ‘foot‐in‐the‐door’ technique).
- Stage 5: the criminal employs further techniques to keep the scam alive (e.g., inventing a further crisis or employing the ‘door‐in‐the‐face’ technique).
- Stage 6: some victims may believe the scam is over but subsequently be revictimized (e.g., the criminal admits to the victim that they have been scamming them but has nevertheless fallen in love with them; the scammer then asks the victim for more money).
12.10 ILLEGAL DOWNLOADS
Major music labels are suing filesharing application Aurous for ‘wilful and egregious copyright infringement’ just days after its earliest alpha version launched.
US industry body the RIAA has filed a lawsuit on behalf of labels including Universal Music, Sony Music and Warner Music subsidiaries Warner Bros, Atlantic and Capitol seeking an injunction against the software as well as damages.
The Spotify‐style application enables its users to search for songs to stream and download, and while its developer has said it intends to become an aggregator for music and licensed streaming services, the RIAA’s lawsuit claims its sources are piracy sites. (Dredge, 2015)
The activities described so far in this chapter are clearly criminal; however, there are some activities conducted online that the user might not know to be illegal or might believe to be such common practice as to not be treated as crimes. Such activities include the practice of downloading copyrighted material illegally from the Internet (e.g., music, videos, books). Studies have shown that users have few ethical concerns about unauthorized downloading (Siegfried, 2004). Hardy, Krawczyk and Tyrowicz (2013) argue that, ‘as a matter of fact, mere popularity of file sharing services seems to suggest that either millions of people are morally rotten or strongly object to equating online “piracy” with traditional theft’.
Given that many question whether engaging in such activities is morally wrong, prevention of this form of cybercrime might require a nontraditional approach. A large amount of money has, in fact, been invested in raising awareness and in educational campaigns in the hope of reducing online file sharing or ‘piracy’. These campaigns, however, have been for the most part unsuccessful – doing little to change opinions or behaviour (D’Astous, Colbert & Montpetit, 2005). In fact, the number of end users engaging in online piracy appears to be continuing to rise (Cesareo & Pastore, 2014). Many of these campaigns equate traditional offline acts of theft with online theft. They also typically focus on the negative personal consequences associated with online piracy, such as fines and imprisonment. In 2012, the Serious Organised Crime Agency in the UK (now known as the National Crime Agency) took down the music site RnBXclusive, leaving a warning on the website that users could receive up to 10 years’ imprisonment and an unlimited fine. This effort was in part successful, given that at least one other site, as a consequence, took itself offline voluntarily. However, the action did not appear to change end users’ attitudes, with some calling this a bullying tactic and scaremongering (Geere, 2012; Moody, 2012). More recently, the City of London police have started placing banner advertisements on websites believed to be offering pirated content illegally; however, to date, there has been no follow‐up research to investigate the effectiveness of this latest strategy.
Some of the problems with the previous strategies are the lack of insight into the psychology of changed behaviour as well as the personal ethics individuals hold regarding such acts. Fear campaigns have often had little success, given that campaigns that induce too much fear are often ignored by viewers in order to avoid feeling too much anxiety from paying attention to the message (see Bada & Sasse, 2014). Online security and stop smoking campaigns are good examples of advertisements that instilled too much fear and had little impact in changing behaviours. Researchers have argued that users have a different ethical stance regarding online piracy compared to traditional theft (see, e.g., Blythe & Wright, 2008; Moores & Chang, 2006). Moreover, as the theory of planned behaviour predicts, if individuals believe that something is the social norm and, in particular, if their peers are engaging in the activity, they are also likely to engage in that behaviour. Interestingly, Hardy et al. (2013) found that, even when an individual’s ethical views are just as strict for online as for traditional appropriations, when people perceive the social norm is ‘lax’, they are more likely to engage in piracy.
Online piracy, therefore, is an interesting crime that might need new approaches to help reduce it. It might even mean developing new business models with respect to paying for online material. For example, Magnatune is a record label, started in 2003, that gives half its profits to artists and offers a sliding scale for purchases via PayPal. Some researchers believe that this approach might prevent illegal downloads. In a study on consumers’ attitudes towards Magnatune, Regner (2015) concludes:
the success of voluntary payment‐based models, documented in a series of studies, is intriguing and it is important to improve our understanding of PWYW. Various underlying motivations have been identified as a determinant for voluntary payments. Based on this evidence it appears plausible that a combination of fairness, reciprocal concerns, self‐image concerns, norm conformity and strategic concerns drives behaviour in PWYW settings. (p. 212)
The example of Magnatune might be the way forward; however, industry and researchers may well consider other approaches that draw from theories in psychology to help predict their success.
12.11 CONCLUSIONS
This chapter focused on two types of online criminal behaviours: scamming and illegal downloads. The types of scams focused on here included phishing, the various subsets of phishing (e.g., spear phishing and vishing) and MMFs. The catching and prosecution of these criminals is challenging and time consuming, which is why other approaches, such as educational and awareness programmes, have been developed to help in the prevention of these crimes. The discipline of psychology has much to offer these programmes, in helping developers to understand how to change individuals’ behaviour, the psychological characteristics of those vulnerable to scams, and the cognitive and motivational errors victims make when approached by a scammer.
DISCUSSION QUESTIONS
- Given the evidence as a whole, what sorts of users are more likely to be scammed by a phishing attack? What are the limitations and strengths of the currently available research?
- Consider some of the studies on training programmes to prevent phishing attacks. What are some of the critiques (including strengths and weaknesses) you might make of these programmes?
- Have you known anyone who has been scammed by an MMF? Why do you think they were tricked?
- What are your views about downloading music and/or videos illegally? Do you think it is morally wrong to do this? Why, or why not?
SUGGESTED READINGS
- Alsharnouby, M., Alaca, F. & Chiasson, S. (2015). Why phishing still works: User strategies for combating phishing attacks. International Journal of Human–Computer Studies, 82, 69–82.
- Cesareo, L. & Pastore, A. (2014). Consumers’ attitude and behaviour towards online music piracy and subscription‐based services. Journal of Consumer Marketing, 31(6/7), 515–525.
- Davinson, N. & Sillence, E. (2010). It won’t happen to me: Promoting secure behaviour among internet users. Computers in Human Behavior, 26, 1739–1747.
- Lea, S., Fischer, P. & Evans, K. (2009). The psychology of scams: Provoking and committing errors of judgement. Office of Fair Trading. Retrieved 7 April 2016 from http://webarchive.nationalarchives.gov.uk/20140402142426/http://www.oft.gov.uk/shared_oft/reports/consumer_protection/oft1070.pdf
- Vishwanath, A. (2015). Examining the distinct antecedents of e‐mail habits and its influence on the outcomes of a phishing attack. Journal of Computer‐Mediated Communication, 20, 570–584.
- Wang, J., Herath, T., Chen, R., Vishwanath, A. & Rao, R. (2012). Phishing susceptibility: An investigation into the processing of a targeted spear phishing email. IEEE Transactions on Professional Communication, 55(4), 345–362.
- Whitty, M. T. (2013). The scammers persuasive techniques model: Development of a stage model to explain the online dating romance scam. British Journal of Criminology, 53(4), 665–684.
- Whitty, M. T. (2015). Mass‐marketing fraud: A growing concern. IEEE Security & Privacy, 13(4), 84–87.