Chapter 6
Making Shopping Easy on Your E-Commerce Site
In This Chapter
 Knowing what makes online consumers click the Buy button
Knowing what makes online consumers click the Buy button
 Sourcing, replenishing inventory, and fulfilling orders
Sourcing, replenishing inventory, and fulfilling orders
 Adding bells and whistles to your site with hosted applications
Adding bells and whistles to your site with hosted applications
 Protecting your customers’ data (and your own) with passwords, firewalls, and back-ups
Protecting your customers’ data (and your own) with passwords, firewalls, and back-ups
 Letting others know who you really are with a personal certificate
Letting others know who you really are with a personal certificate
Walk into any Walmart or other megastore, and you’re likely to feel overwhelmed by the sheer size of the place. Not to worry: Walmart makes life (and spending money) easier for its shoppers by having an employee greet you at the door, and by carefully arranging merchandise in aisles where you’ll find it easily. Online businesses work much the same; in fact, shoppers want to move even more quickly and easily through an online store than a brick-and-mortar one. Your job is to make your sales items easy to find and purchase, and to make customers feel secure so that you’re paid promptly and reliably. You also need to protect yourself financially and guard your business data. In this chapter, I discuss some technologies and strategies that can keep your data secure and make your customers feel at ease, too.
Fostering a good atmosphere for e-commerce is also a matter of presenting your merchandise clearly and making it easy for customers to choose and purchase them. Making changes to your website is relatively easy. You can remake your store’s front door (your home page) in a matter of minutes. You can revamp your sales catalog in less than an hour. Making regular improvements and updates to your online store doesn’t just mean changing the colors or the layout, which is the part of your operation that customers notice, on your website. It also means improving back-office functions that customers don’t see, such as inventory management, invoices, labels, packing, and shipping. When you test, check, and revise your website based on its current performance, you can boost your revenue and increase sales as well as make your website more usable.
Here’s a short list of what you need to do to be a successful e-commerce businessperson: Set up the right atmosphere for making purchases, provide options for payment, and keep sensitive information private. Oh, and don’t forget your main goal is to get goods to the customer safely and on time. In this chapter, I describe ways in which you can implement these essential online business strategies to ensure a positive shopping experience for your customers.
Giving Online Shoppers What They Need
You’ve heard it before, but I can’t emphasize enough the importance of understanding the needs of online shoppers and doing your best to meet them. That’s the best way to end up with a healthy balance in your bank account.
Showing what you’ve got
Customers may end up buying an item in a brick-and-mortar store, but chances are that they saw it online first. Shoppers now routinely assume that legitimate stores have a website and an online sales catalog that is likely to include even more items, accompanied by detailed descriptions, than a shopper would find by going to the store in person.
“It’s not enough to just say we have this or that product line for sale. Until we actually add an individual item to our online store, with pictures and prices, we won’t sell it,” says Ernie Preston, who helped create an 84,000-item online catalog for a brick-and-mortar tool company that I profiled a few years ago for a previous edition of this book. “As soon as you put it in your online catalog, you’ll get a call about it. Shopping on the web is the convenience factor that people want.”
Suppose you don’t have an 84,000-item catalog. Instead, you have only 20–30 items and you’re just starting out. What can you do to build trust and encourage shoppers? Observe three basic rules:
 Make your sales catalog organized so items are easy to find.
Make your sales catalog organized so items are easy to find.
 Talk about yourself and your background.
Talk about yourself and your background.
 Provide lots of details and good photos.
Provide lots of details and good photos.
Here's an example. Nanette Thorell sells egg art (eggshells she has turned into jewelry and other products) on her website, Enchanted Hen Productions (www.enchantedhen.com). She follows the example of "triangulation" that I describe in this book's introduction by selling on eBay, Etsy, and ArtFire, as well as marketing herself with a blog, a newsletter, and on Facebook and Twitter. As you can see from her home page (see Figure 6-1), her links are simple and clearly organized.
Earning trust to gain a sale
Although e-commerce is more and more common, many customers who are relatively new still need to have their fears addressed. They want to be sure that providing their names, phone numbers, and credit card information won’t lead to identity theft. And shoppers who are old pros at shopping online want to avoid being flooded with unwanted e-mails. In regard to the sale at hand, many fear that they will pay for merchandise but not receive it.
State your policies clearly and often, providing assurance that you don't give out personal data without consent. If you plan to accept credit card orders, get an account with a web host that provides a secure server, which is software that encrypts data exchanged with a browser. And be sure to include comments from satisfied customers. If you run an eBay Store or a store on another marketplace such as Bonanza (www.bonanza.com), your feedback rating provides assurance.

Figure 6-1: Encourage shoppers with good organization and plenty of product details.
If you're a member in good standing with the Better Business Bureau (www.bbb.org), you may be eligible to apply for the BBB Business Seal for the Web (www.bbb.org/us/bbb-online-business) to build credibility and confidence among your clients. Businesses that participate in the BBBOnline program show their commitment to their customers by displaying a BBBOnline Reliability Seal or Privacy Seal on their websites.
One of the best ways to build trust in you and your products is to tell visitors about yourself and your background and experience. Figure 6-2 shows Nanette Thorell’s About Me page.

Figure 6-2: Tell shoppers about your experience and knowledge in your area of business.
Pointing the way with links and graphics
Because most customers are comparison shopping, it’s wise to put the cost, measurements, and other important features right next to each item to promote speed and convenience.
You can also direct shoppers through your site by providing plenty of links from one section to another. Even when they’re exploring one section, you should provide links back to the home page or to other areas of your site. In the case of Enchanted Hen Productions (refer to Figure 6-1), if you click Jewelry, you go to a category page with two links: Earrings and Necklaces. Click Earrings, and you see the section opening page shown in Figure 6-4. Even as shoppers are exploring the earrings section of the catalog, clicking a link guides them back to the necklaces section if they wish.

Figure 6-3: Use graphics to call attention to the information your customer wants the most: the price.

Figure 6-4: Graphic links guide shoppers through a sales catalog.
Giving the essentials
One of the big advantages of operating a business online is space. Not only do you have plenty of room in which to provide full descriptions of your sale items, but you also have no reason to skimp on the details you provide about your business and services. Here are some suggestions on how to provide information that your customer may want:
 If you sell clothing, include a page with size and measurement charts.
If you sell clothing, include a page with size and measurement charts.
 If you sell food, provide weights, ingredients, and nutritional information.
If you sell food, provide weights, ingredients, and nutritional information.
 If you sell programming, web design, or traditional graphic design, provide samples of your work, links to web pages you’ve created, and testimonials from satisfied clients.
If you sell programming, web design, or traditional graphic design, provide samples of your work, links to web pages you’ve created, and testimonials from satisfied clients.
 If you’re a musician, publish a link to a short sound file of your work.
If you’re a musician, publish a link to a short sound file of your work.
Don't be reluctant to tell people ways that your products and services are better than others. Visit the Lands' End online catalog (www.landsend.com) for good examples of how this well-established marketer describes the quality of its wares.
The more details you provide about items, the longer someone will stay on your site, and the more likely they’ll click Add to Cart or Buy. In your description, try to engage shoppers’ imaginations. In Figure 6-5, Nanette Thorell provides a list with specifications, a clear photo, an easy-to-find price, and this phrase: “. . . they [the earrings] will turn and sway as you move your head.” The shopper imagines the earrings on her head, which encourages her impulse to purchase.

Figure 6-5: Graphic links guide shoppers through a sales catalog.
Managing Goods and Services
Shoppers on the web are continually in search of The New: the next new product, the latest price reduction or rebate, the latest comment in a blog, or today’s headlines. As a provider of content, whether it’s in the form of words, images, or products for sale, your job is to manage that content to keep it fresh and available. You also need to replenish stock when it’s purchased, handle returns, and deal with shipping options, as I describe in the sections that follow.
Handling returns
Your returns policy depends on the venue where you make your sales. If you sell primarily on eBay or another marketplace, you should accept returns, if only because many of the most experienced and successful sellers do. That doesn’t mean you need to accept every single item that is returned. Most businesses place restrictions on when they’ll receive a return and send a refund. The items must be returned within 14 days, for example; the packages must be unopened; the merchandise must not be damaged.
Adding shipping rates
These days, when shoppers think about shipping rates, they think about a four-letter word: F-R-E-E. Amazon.com, with its free shipping options, has made sellers expect it as a choice. As a result, sellers on marketplaces like eBay are told to offer free shipping if possible (see www.internetretailer.com/mobile/2011/03/31/ebay-bets-free-shipping). Even if sellers build a $10 shipping cost into a $50 item so the buyer pays $60 with "free shipping," customers are still more likely to buy under such circumstances — or so the conventional wisdom says.
Otherwise, as part of creating a usable e-commerce catalog, you need to provide customers with shipping costs for your merchandise. Shipping rates can be difficult to calculate. They depend on your geographic location as well as the location where you’re planning to ship. If you’re a small-scale operation and you process each transaction manually, you may want to ship everything a standard way (UPS Ground, FedEx Home Delivery, or the U.S. Postal Service Parcel Post). Then you can keep a copy of your shipper’s charges and calculate each package’s shipping cost individually.
You can also save time by using the quick shipping calculator provided by iShip (https://iship.com). Just go to the site's home page, enter the origin and destination zip codes, and click Go. You get a set of shipping rates from DHL, UPS, and the U.S. Postal Service so you can pick the most cost-effective option. If you want help with shipping, you can set up your site with the help of a transaction hosting service, such as ChannelAdvisor (www.channeladvisor.com). This company has an agreement with the U.S. Postal Service so that it automatically calculates shipping charges and includes those charges in the invoices it sends to your customers.
Maintaining inventory
Shoppers on the web want things to happen instantly. If they discover that you’re out of stock of an item they want, they’re likely to switch to another online business instead of waiting for you to restock that item. With that in mind, obey the basic principle of planning to be successful: Instead of ordering the bare minimum of this or that item, make sure you have enough to spare. Too much inventory initially is better than running out at some point.
If you have one store with 50–100 items in stock, managing inventory is straightforward. If you manage 13 separate storefronts as well as a brick-and-mortar store, you’d better call in some outside help to keep on top of it all.
Mimi and Peter Kriele operate the website Touch of Europe (www.touchofeurope.net) as an Amazon web store, as well as 12 other specialized sites. The Krieles use Miva Merchant to manage their main website. The inventory for all the other stores is taken from Amazon.com and managed using that marketplace's tools for merchants. These are just two approaches. See Chapter 16 for more on different ways to manage multiple storefronts.
Rely on software or management services to help you keep track of what you have. If you feel at ease working with databases, record your initial inventory in an Access or SQL database. A database forces you to record each sale manually so you know how many items are left. You could connect your sales catalog to your database using a program such as ColdFusion from Adobe (www.adobe.com/products/coldfusion). Such a program can update the database on the www.adobe.com/products/coldfusion-family.html when sales are made. But you may need to hire someone with web programming experience to set up the system for you and make sure it actually works.
If you sign up with an online store solution, like Yahoo! Small Business or a sales management provider like Marketplace Advisor Selling Services from ChannelAdvisor (www.channeladvisor.com), inventory is tracked automatically for you. Whether you do the work yourself or hire an outside service, you have to be able to answer basic questions such as these:
 When should you reorder? Establish reorder points — points at which you automatically reorder supplies (when you get down to two or three items left, for example).
When should you reorder? Establish reorder points — points at which you automatically reorder supplies (when you get down to two or three items left, for example).
 How many items do you have in stock right now? Make sure that you have enough merchandise on hand not only for everyday demand but also in case a product gets hot or the holiday season brings about a dramatic increase in orders.
How many items do you have in stock right now? Make sure that you have enough merchandise on hand not only for everyday demand but also in case a product gets hot or the holiday season brings about a dramatic increase in orders.
An e-commerce hosting service can also help you with questions that go beyond the basics, such as the purchasing history of customers. Knowing what customers have purchased in the past gives you the ability to suggest up-sells — additional items customers might want. But in the early stages, making sure you have a cushion of additional inventory for the time when your site becomes a big success is your primary responsibility.
Keeping Your Website in Top Shape
The job of your hosting service or ISP, of course, is to monitor traffic and make sure your website is up and running. But unless you keep an eye on your site and its availability to your customers, you may not be aware of technical problems that can scare potential business away. If your site is offline periodically or your server crashes or works slowly, it doesn’t just waste your customers’ time — it can cut into your sales directly.
Using software to keep score
Although they take some effort to install, programs are available for between $30 – $200 that continually keep an eye on your website and notify you of any problems. Site24x7 (www.site24x7.com) monitors your website's availability from more than 40 locations around the world. You can try the service for a free 15-day trial period. Three pricing plans are available.
Coping when your service goes out to lunch
Ideally, your web host provides a page on its website that keeps track of its network status and records any recent problems. One site monitoring notification (from a program you install yourself or one that you “rent” as a service from an Application Service Provider [ASP] — see the next section, “Outsourcing your business needs”) probably isn’t cause for concern. However, when you receive a series of notifications, call your web-hosting service and tell technical support exactly what the problems are/were.
If the problem with your site is a slow response to requests from web browsers rather than a complete outage, the problem may be that your server is slow because you’re sharing it with other websites. Consider moving from shared hosting to a different option. In co-location, you purchase the server on which your files reside, but the machine is located at your web host’s facility rather than at your own location. Your site is the only one on your machine. You also get the reliability of the host’s technical support and high-speed Internet connection.
If you really need bandwidth, consider a dedicated server. In this case, you rent space on a machine that is dedicated to serving your site. This arrangement is far more expensive than sharing a web server, and you should choose it only if the number of visits to your site at any one time becomes too great for a shared server to handle. You’ll know a shared server is becoming overtaxed if your site is slow to load.
Outsourcing your business needs
One of the most effective ways to save time and money doing business online is to let someone else install and maintain the computer software that you use. Outsourcing refers to the practice of having an outside company provide services for your business, such as web hosting, form creation, or financial record keeping, rather than installing software and running it on your own computer.
One of the companies that provides web-based services on an outsourced basis is an Application Service Provider (ASP). An ASP makes business or other applications available on the web. For example, when you fill out a form and create a web page on CafePress.com (which I describe in Chapter 15), you’re using CafePress.com as an ASP. Rather than create your web page on your own computer, you use an application on the CafePress.com site and store your web page information there.
How ASPs can help your company
You have to pay a monthly fee to use an ASP’s services. You may also incur installation fees, and you may have to sign a one- or two-year contract. In return, ASPs provide benefits to your company that include the following:
 Shopping cart/store creation: In addition to a website, open an e-commerce store with shopping cart services like ZenCart, 3D Cart, X-Cart, or one of many other providers.
Shopping cart/store creation: In addition to a website, open an e-commerce store with shopping cart services like ZenCart, 3D Cart, X-Cart, or one of many other providers.
 "Shark tank" feedback: Concept Feedback (
"Shark tank" feedback: Concept Feedback (www.conceptfeedback.com) provides experts who evaluate your website's design and usability and suggest improvements.
 Online form creation: FormSite.com (
Online form creation: FormSite.com (www.formsite.com) is a leader in creating a variety of forms that can help online shoppers provide essential functions, such as subscribing to newsletters or other publications, asking for information about your goods and services, or providing you with shipping or billing information. The sample pizza order form shown in Figure 6-6 is an example of the type of form that this particular ASP can help you create.

Figure 6-6: An ASP like FormSite.com lets you create a database-backed web page feature (such as an order form) without having to purchase, install, and master a database program.
 Product presentation: Arqspin (
Product presentation: Arqspin (http://arqspin.com) lets you create 360-degree "spinning" product photography so customers can see your merchandise from all angles.
 Reduced credit card fees: All merchants pay fees to credit card processors to receive customers' credit card payments. FeeFighters (
Reduced credit card fees: All merchants pay fees to credit card processors to receive customers' credit card payments. FeeFighters (https://feefighters.com) helps businesses shop for credit card merchant accounts to save money.
Although ASPs can help you in many ways, they require research, interviewing, contract review, and an ongoing commitment on your part. I illustrate the potential pluses and minuses of outsourcing in Table 6-1.

In many cases, ASPs can provide a software solution and customize it to your needs. Outsourcing not only improves your company’s bottom line, but also helps you convey your message to potential customers that you might never reach otherwise.
Doing your homework before you sign up
After you try out the software or other service that you want to lease, you usually need to sign a contract. Read the fine print. Contracts can last for 12 to 50 months; make sure you don’t get locked in to one that’s longer than you need. You have a better chance of getting the service you want if you do the following:
 Understand pricing schemes. Some ASPs charge on a “per-employee” basis while others charge “per-seat” fees based on each registered user. Still others charge “per CPU,” which means you’re charged for each machine that runs the hosted application.
Understand pricing schemes. Some ASPs charge on a “per-employee” basis while others charge “per-seat” fees based on each registered user. Still others charge “per CPU,” which means you’re charged for each machine that runs the hosted application.
 Pin down start-up fees. Virtually all ASPs charge a start-up fee, or a service implementation fee, when you sign the contract. Make sure the fee covers installation and any customization that you’ll need.
Pin down start-up fees. Virtually all ASPs charge a start-up fee, or a service implementation fee, when you sign the contract. Make sure the fee covers installation and any customization that you’ll need.
 Don’t accept just any SLA. It’s essential to obtain a service level agreement (SLA), which is a document that spells out what services you expect an ASP (or other vendor) to provide. Don’t hesitate to add, delete, or change sections to meet your needs.
Don’t accept just any SLA. It’s essential to obtain a service level agreement (SLA), which is a document that spells out what services you expect an ASP (or other vendor) to provide. Don’t hesitate to add, delete, or change sections to meet your needs.
 Avoid “gotcha” fees. Pricing arrangements are hardly standard with regard to ASPs. Some of the big hidden costs involve personalizing or customizing the service to adapt to legacy systems. You should ask these questions in order to avoid unpleasant surprises: Is there an additional cost for customizing or personalizing the application? Does it cost extra to back up my company’s data and recover it if one of my computers goes down? Is help desk support included in my monthly fee, or will you charge me every time I call with a question or problem?
Avoid “gotcha” fees. Pricing arrangements are hardly standard with regard to ASPs. Some of the big hidden costs involve personalizing or customizing the service to adapt to legacy systems. You should ask these questions in order to avoid unpleasant surprises: Is there an additional cost for customizing or personalizing the application? Does it cost extra to back up my company’s data and recover it if one of my computers goes down? Is help desk support included in my monthly fee, or will you charge me every time I call with a question or problem?
 Make sure your information is secure. Some huge security risks are associated with transmitting your information across the wide-open spaces of the Internet. Make sure your ASP takes adequate security measures to protect your data by asking informed questions, such as: Is my data protected by SSL encryption? Do you run a virtual private network? How often do you back up your customers’ data?
Make sure your information is secure. Some huge security risks are associated with transmitting your information across the wide-open spaces of the Internet. Make sure your ASP takes adequate security measures to protect your data by asking informed questions, such as: Is my data protected by SSL encryption? Do you run a virtual private network? How often do you back up your customers’ data?
If the answer to any of these questions seems inadequate, move on to the next ASP.
Keeping Your Business Safe
Working at home or in a small office carries its own set of safety concerns for small business owners. Chances are you don’t have an IT professional at hand to make sure your files and your network are safe from intrusion. Some safe computing practices, such as using password protection, making regular back-ups, and installing antivirus software, can go a long way toward keeping your data secure, even if you never have to get into more technical subjects such as public key encryption.
Separating the personal and the professional
Many entrepreneurs who run businesses from their homes face a simple logistical problem: Their work takes over their home. Boxes, computers, phones, and other gadgets create disruptions that can drive everyone crazy. Here are some simple steps that can help you set more clearly defined boundaries between work and domestic life.
When the computer is a group sport
A lot to can be said for having at least two separate computers — one for personal use and one for business use. The idea is that you set up your system so that you have to log on to your business computer with a username and password.
If you have only one computer, passwords can still provide a measure of protection. Windows gives you the ability to set up different user profiles, each associated with its own password. User profiles and passwords don’t necessarily protect your business files, but they convey to your family members that they should use their own software, stick to their own directories, and not try to explore your company data.
One phone may not be enough
Having a phone line dedicated to your business not only makes your business seem more serious, but also separates your business calls from your personal calls. If you need a separate line for your online business, consider Google Voice (www.google.com/voice). This service gives you voicemail and a phone number that you can route to another phone if needed.
Heading off disasters
An old joke about the telegram from a mother reads, “Worry. Details to follow.” When you’re lying awake at night, you can be anxious about all sorts of grim disasters affecting your business: flood, fire, theft, computer virus, you name it. Prevention is always better than a cure, so this section covers steps you can take to prevent problems. But should a problem arise, there are also ways to recover more easily.
Insurance . . . the least you can do
I can think of ways to spend money that are a whole lot more fun than paying insurance premiums. Yet there I am every month, writing checks to protect myself in case something goes wrong with my house, car, body, and so on. And yes, there’s another item to add to the list: protecting my business investment by obtaining insurance that specifically covers me against hardware damage, theft, and loss of data. You can go a step further and obtain a policy that covers the cost of data entry or equipment rental that would be necessary to recover your business information. Here are some specific strategies:
 Make a list of all your hardware and software and how much each item cost, and store a copy of it in a secure place, such as a fireproof safe or safe-deposit box.
Make a list of all your hardware and software and how much each item cost, and store a copy of it in a secure place, such as a fireproof safe or safe-deposit box.
 Take photos of your computer setup in case you need to make an insurance claim, and put them in the same safe place.
Take photos of your computer setup in case you need to make an insurance claim, and put them in the same safe place.
 Save your electronic files on CD or DVD and put the disc in a safe storage location, such as a safe-deposit box.
Save your electronic files on CD or DVD and put the disc in a safe storage location, such as a safe-deposit box.
Investigate the many options available to you for insuring your computer hardware and software. Your current homeowner's or renter's insurance may offer coverage, but make sure the dollar amount is sufficient for replacement. You may also want to look into the computer hardware and software coverage provided by Safeware, The Insurance Agency, Inc. (www.safeware.com).
Think ahead to the unthinkable
The Gartner Group estimates that two out of five businesses that experience a major disaster go out of business within five years. I would guess that the three that are able to get back up and running quickly already had recovery plans in place. Even if your company is small, be prepared for trouble such as floods, hurricanes, or tornadoes. A recovery effort might include the following strategies:
 Back-up power systems: What will you do if the power goes out, and you can’t access the web? You can buy a back-up power system for less than $50 at office supply stores or from Amazon.com.
Back-up power systems: What will you do if the power goes out, and you can’t access the web? You can buy a back-up power system for less than $50 at office supply stores or from Amazon.com.
 Data storage: This is probably the most practical and essential disaster recovery step for small or home-based businesses. Back up your files to the "cloud" using services like Carbonite (
Data storage: This is probably the most practical and essential disaster recovery step for small or home-based businesses. Back up your files to the "cloud" using services like Carbonite (www.carbonite.com). An article in the IT magazine Computerworld compared five of the best-known systems (www.computerworld.com/s/article/9223805/5_online_backup_services_keep_your_data_safewww.computerworld.com/s/article/9223805/5_online_backup_services_keep_your_data_safe).
 Telecommunications: Having an alternate method of communication available in case your phone system goes down ensures that you’re always in touch. The obvious choice is a cell phone. Also set up a voice mailbox so that customers and vendors can leave messages for you even if you can’t answer the phone.
Telecommunications: Having an alternate method of communication available in case your phone system goes down ensures that you’re always in touch. The obvious choice is a cell phone. Also set up a voice mailbox so that customers and vendors can leave messages for you even if you can’t answer the phone.
Creating a plan is a waste of time if you don’t regularly set aside time to keep it up to date. Back up your data on a regular basis, purchase additional equipment if you need it, and make arrangements to use other computers and offices if you need to — in other words, implement your plan. You owe it not only to yourself, but also to your customers to be prepared in case of disaster.
Antivirus protection without a needle
As an online businessperson, you download files, receive disks from customers and vendors, and exchange e-mail with all sorts of people you’ve never met before. Surf safely by installing antivirus programs, such as
 Norton Internet Security by Symantec Corp. (
Norton Internet Security by Symantec Corp. (www.symantec.com/global/products): This application, which includes an antivirus program as well as a firewall and lists for $79.99, automates many security functions and is especially good for beginners. A standalone version, Norton AntiVirus, is available for $49.99, but I highly recommend the more full-featured package, which includes a firewall that blocks many other dangerous types of intrusions, such as Trojan horses.
 AVG AntiVirus by AVG Technologies (
AVG AntiVirus by AVG Technologies (www.avg.com): Many users who find Norton Internet Security too intrusive (it leaves lots of files on your computer and consumes a great deal of memory) turn to this product, which lists for $39.99.
 Avira Free Antivirus (
Avira Free Antivirus (www.avira.com/en/avira-free-antivirus): This is a popular free program.
 VirusScan by McAfee (
VirusScan by McAfee (www.mcafee.com): This is the leading competitor of Norton AntiVirus, which comes bundled with Norton Internet Security. VirusScan is included in McAfee Internet Security, which includes a firewall and costs $67.99.
A visible sign that you’re trustworthy
Like the office assistant whose work is visible only when he or she is not doing a good job, you may be squeaky clean but nobody will know unless there’s a problem . . . or unless you display a “seal of approval” from a reputable online organization. The two best-known seals (which are actually images you add to your web pages to show visitors you’re reputable) are TRUSTe and BBBOnline.
The nonprofit organization TRUSTe was created to boost the degree of trust that web surfers have in the Internet. It does this through a third-party oversight “seal” program. If you demonstrate to TRUSTe that you’re making efforts to keep your visitors’ personal data secure and if you pledge not to share your customers’ data and to publish a privacy statement on your site, TRUSTe issues you a seal of approval that you can place on your site’s home page. The TRUSTe seal is intended to function as the online equivalent of the Good Housekeeping seal of approval on a product.
By itself, the seal doesn't keep hackers from breaking into your site and stealing your data. That's still up to you. Having the seal just makes visitors feel better about using your services. The TRUSTe site provides you with a wizard that leads you through the process of generating a privacy statement for your site. The statement tells visitors how you protect their information. Find out more by visiting the TRUSTe home page (www.truste.com) and clicking the Business Products header link.
BBBOnline, the web-based arm of the Better Business Bureau, has a similar program for commercial websites. The BBBOnline Reliability Seal Program has several eligibility requirements, including a physical location in the United States or Canada, a business record for at least a year, a satisfactory complaint-handling record, membership in the Better Business Bureau, and a commitment to resolve disputes and respond promptly to consumer complaints. Find out more at www.bbb.org.
Installing firewalls and other safeguards
You probably know how important a firewall is in a personal sense. Firewalls filter out unwanted intrusions, such as executable programs that hackers seek to plant on your file system, so they can use your computer for their own purposes. When you’re starting an online business, the objectives of a firewall become different: You’re protecting not just your own information, but also that of your customers. You’re quite possibly relying on the firewall to protect your source of income as well as the data on your computers.
Keeping out Trojan horses and other unwanted visitors
A Trojan horse is a program that enters your computer surreptitiously and then attempts to do something without your knowledge. Some folks say that such programs enter your system through a "back door" because you don't immediately know that they've entered your system. Trojan horses may come in the form of an e-mail attachment with the filename extension .exe (which stands for executable). For example, I once received an e-mail that purported to be from Microsoft Corp. and claimed to contain a security update. The attachment looked innocent enough, but had I saved the attachment to my computer, it would have used my computer as a staging area for distributing itself to many other e-mail addresses.
I didn't run into trouble, however. My firewall program recognized the attachment and alerted me to the danger. I highly recommend that anyone who, like me, has a cable modem, DSL, or other direct connection to the Internet install one right away. You can try out the shareware program ZoneAlarm by Zone Labs, Inc. (www.zonealarm.com), that provides you with basic firewall protection, though more full-featured programs like Norton Internet Security (http://us.norton.com/internet-security) are probably more effective.
Cleaning out spyware
Watch out for software that “spies” on your web surfing and other activities and then reports these activities to advertisers, potentially invading your privacy. Ad-Aware isn’t a firewall, exactly, but it’s a useful program that detects and erases any advertising programs you may have downloaded from the Internet without knowing it. Such advertising programs might be running on your computer, consuming your processing resources and slowing down operations. Some spyware programs track your activities when you surf the web; others simply report that they have been installed. Many users regard these spyware programs as invasions of privacy because they install themselves and do their reporting without your asking for it or even knowing they’re active.
When I ran Ad-Aware the first time, it detected a whopping 57 programs I didn’t know about that were running on my computer and that had installed themselves when I connected to various websites or downloaded software. As you can see in Figure 6-7, when I ran Ad-Aware while I was working on this chapter, sure enough, it found four suspicious software components running.
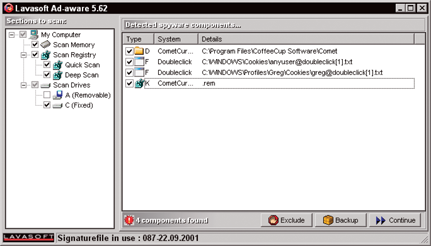
Figure 6-7: Ad-Aware deletes advertising software that, many users believe, can violate your privacy.
I highly recommend Ad-Aware; you can download a version at www.lavasoft.com and try it for free. You can pay for their Personal or Pro Security versions as well. One of this book's editors personally recommends a free anti-spyware tool called SpyBot Search & Destroy (www.safer-networking.org).
Positioning the firewall
These days, most home networks are configured so that the computers on the network can share information as well as the same Internet connection. Whether you run a home-based business or a business in a discrete location, you almost certainly have a network of multiple computers. A network is far more vulnerable than a single computer connected to the Internet: A network has more entry points than a single computer, and more reliance is placed on each of the operators of those computers to observe good safety practices. And if one computer on the network is attacked, others can be attacked as well.
You probably are acquainted with software firewalls, such as Norton Personal Firewall or Zone Alarm. Software firewalls protect one computer at a time. In a typical business scenario, however, multiple computers share a single Internet connection through a router that functions as a gateway. Many network administrators prefer a hardware firewall — a device that functions as a filter for traffic both entering and leaving it. A hardware firewall may also function as a router, but it can also be separate from the router. The device is positioned at the perimeter of the network where it can protect all the company's computers at once. One example of this type of hardware is the WatchGuard Firebox X20e, which costs $572, by WatchGuard (www.watchguard.com).
Keeping your firewall up to date
Firewalls work by means of attack signatures (or definitions), which are sets of data that identify a connection attempt as a potential attack. Some attacks are easy to stop: They’ve been attempted for years, and the amateur hackers who attempt intrusions don’t give much thought to them. The more dangerous attacks are new ones. These have signatures that emerged after you installed your firewall.
You quickly get a dose of reality and find just how serious the problem is by visiting one of the websites that keeps track of the latest attacks, such as the Distributed Intrusion Detection System or DShield (www.dshield.org). On the day I visited, DShield reported that the "survival time" for an unpatched computer (a computer that has security software that isn't equipped with the latest updates called patches) after connecting to the Internet was only 16 minutes. Therefore, such a computer only has 16 minutes before someone tries to attack it. If that doesn't scare you into updating your security software, I don't know what will.
Providing security with public keys
The conversations I overhear while I drive my preteen daughters and their friends to events leave no doubt in my mind that different segments of society use code words that only their peers can understand. Even computers use encoding and decoding to protect information exchanged on the Internet. The schemes used online are far more complex and subtle than the slang used by kids, however. This section describes the security method most widely used on the Internet, and the one you’re likely to use yourself: Secure Sockets Layer (SSL) encryption.
The keys to public-key/private-key encryption
Terms like SSL and encryption might make you want to reach for the remote. But don’t be too quick to switch channels. SSL is making it safer to do business online and boosting the trust of potential customers. And anything that makes shoppers more likely to spend money online is something you need to know about.
The term encryption is the process of encoding data, especially sensitive data, such as credit card numbers. Information is encrypted by means of complex mathematical formulas — algorithms. Such a formula may transform a simple-looking bit of information into a huge block of seemingly incomprehensible numbers, letters, and characters. Only someone who has the right formula, called a key (which is a complex mass of encoded data), can decode the gobbledygook.
Here's a very simple example. Suppose that my credit card number is 12345, and I encode it by using an encryption formula into something like the following: 1aFgHx203gX4gLu5cy.
The algorithm that generated this encrypted information may say something like "Take the first number, multiply it by some numeral, and then add some letters to it. Then take the second number, divide it by x, and add y characters to the result," and so on. (In reality, the formulas are far more complex than this, which is why you usually have to pay a license fee to use them. But this is the general idea.) Someone who has the same formula can run it in reverse, so to speak, to decrypt the encoded number and obtain the original number, 12345.
In practice, the encoded numbers that are generated by encryption routines and transmitted on the Internet are very large. They vary in size depending on the relative strength (or uncrackability) of the security method used. Some methods generate keys that consist of 128 bits of data; a data bit is a single unit of digital information. These formulas are 128-bit keys.
Encryption is the cornerstone of security on the Internet. The most widely used security schemes, such as the Secure Sockets Layer (SSL) protocol, the Secure Electronic Transactions (SET) protocol, and Pretty Good Privacy (PGP), all use some form of encryption.
Getting a certificate without going to school
When you write a check at a retail store, the cashier is likely to make sure you’re preregistered as an approved member and also asks to see your driver’s license. But on the Internet, how do you know people are who they say they are when all you have to go on is a URL or an e-mail address? The solution in the online world is to obtain a personal certificate that you can send to website visitors or append to your e-mail messages.
How certificates work
A certificate, which is also sometimes dubbed a Digital ID, is an electronic document issued by a certification authority (CA). The certificate contains the owner’s personal information as well as a public key that can be exchanged with others online. The public key is generated by the owner’s private key, which the owner obtains during the process of applying for the certificate.
In issuing the certificate, the CA takes responsibility for saying that the owner of the document is the same as the person actually identified on the certificate. Although the public key helps establish the owner’s identity, certificates do require you to put a level of trust in the agency that issues it.
A certificate helps both you and your customers. A certificate assures your customers that you’re the person you say you are, plus it protects your e-mail communications by enabling you to encrypt them.
Obtaining a certificate from VeriSign
Considering how important a role certificates play in online security, obtaining one is remarkably easy. You do so by applying and paying a licensing fee to a CA. One of the most popular CAs is VeriSign, Inc., now part of Symantec, which lets you apply for a certificate called a Class 1 Digital ID.
A Class 1 Digital ID is only useful for securing personal communications. As an e-commerce website owner, you may want a business-class certificate called a 128-bit SSL Global Server ID (www.verisign.com/products-services/index.html). This form of Digital ID works only if your e-commerce site is hosted on a server that runs secure server software — software that encrypts transactions — such as Apache Stronghold. Check with your web host to see whether a secure server is available for your website.
A VeriSign personal certificate, which you can use to authenticate yourself in e-mail, news, and other interactions on the Internet, costs $22.95 per year, and you can try out a free certificate for 60 days. Follow these steps to obtain your Digital ID:
1. Go to the VeriSign, Inc. Digital IDs for Secure E-Mail page at www.symantec.com/verisign/digital-id.
2. Click Buy Online.
The Step 1: Certificate Data page appears.
3. Type your e-mail address and choose a validity period (25 days or one year); then click Next.
If you pick the one-year option, you will be prompted to enter your billing information. Otherwise, the Confirmation page appears.
4. Read the terms and conditions, click Yes to accept the terms, and then click Submit.
The Completion page appears with instructions on how to pick up your Digital ID.
5. Check the e-mail address you entered in Step 3.
You’ll receive two e-mails. Click the link in the first one to go to the Verisign self-service page. Log in to the page with the password that was sent in the second e-mail.
6. The Digital ID for Secure Email login page appears after you click the link in the first e-mail you received. Type the password you received and click Log in.
A page appears reviewing your request status for generating a key pair.
7. Review the key information and then click Generate Key and Install.
Allow a few minutes for the key to generate. When your key is generated, you see the message Successfully generated the private key and installed the certificate to your key store at the top of the window.
8. Click the Install Certificate button.
9. When a dialog box appears saying the certificate has been installed, click OK.
10. To view your certificate, in Microsoft Internet Explorer, choose Tools⇒Internet Options, click Content, and then click Certificates.
The Certificate dialog box appears.
11. Double-click the name of the certificate listed in the Personal tab.
The certificate appears. Figure 6-8 shows my certificate for Internet Explorer. (Copying this ID, or anyone else’s, is pointless because this is only your public key; the public key is always submitted with your private key, which is secret.)

Figure 6-8: A personal certificate assures individuals or websites of your identity.
After you have your Digital ID, what do you do with it? For one thing, you can use it to verify your identity to sites that accept certificate submissions. Some sites that require members to log in use secure servers that give you the option of submitting your certificate rather than entering the usual username and password to identify yourself. You can also attach your Digital ID to your e-mail messages to prove that your message is indeed coming from you. See your e-mail program’s Help files for more specific instructions.
 Microsoft Office gives you access to clip art images that help highlight sales items.
Microsoft Office gives you access to clip art images that help highlight sales items.  If your site doesn't work well, a potential customer can find another site whose pages load more quickly just a few mouse clicks away. Outages can be costly, too. The business and technology website Business Insider (
If your site doesn't work well, a potential customer can find another site whose pages load more quickly just a few mouse clicks away. Outages can be costly, too. The business and technology website Business Insider ( A
A  Companies that want to provide a website the public can visit as well as secure e-mail and other communications services create a secure sub-network of one or more specially
Companies that want to provide a website the public can visit as well as secure e-mail and other communications services create a secure sub-network of one or more specially