8
SURVEILLING AMERICANS
RIGHT AFTER 9/11, HIGH-RANKING OFFICIALS IN THE BUSH administration devised an illicit eavesdropping program and cast as wide a net possible, covering both foreign and domestic communications. The NSA began eavesdropping inside the United States—without court order. Congress soon passed Section 215 of the USA PATRIOT Act that provided for the bulk collection by the NSA of all telephony metadata held by American telecommunications companies like AT&T, Verizon, and Sprint. The FBI began a massive campaign of information gathering targeting over five thousand Muslims. Local police departments, such as the NYPD, implemented surveillance programs directed at mosques and Muslim communities, and began infiltrating domestic Muslim organizations. Through both digital and analog methods, the government turned total information awareness on the American people.
The linchpin of a domesticated counterinsurgency is to bring total information awareness home. Just as it was developed abroad, it is total surveillance alone that makes it possible to distinguish the active minority on domestic soil from the passive masses of Americans. A fully transparent population is the first requisite of the counterinsurgency method. In General Petraeus’s field manual, it received a full chapter early on, “Intelligence in Counterinsurgency,” with a pithy and poignant epigraph: “Everything good that happens seems to come from good intelligence.” And as the manual began, so it ended, with the following simple mantra: “The ultimate success or failure of the [counterinsurgency] mission depends on the effectiveness of the intelligence effort.”1
The government is supposed to treat domestic surveillance differently than foreign intelligence—which explains, among other things, the separation and different legal standards that apply to the FBI and the CIA. Under federal law, domestic communications receive greater protections and require a warrant from a judicial officer to intercept. Foreign communications related to terrorism investigations pass through a more expedited process at the Foreign Intelligence Surveillance Court (FISC), but nevertheless also require approval from that court. Stringent but graduated rules on domestic and foreign intelligence gathering had been put in place in the 1970s as a result of illicit domestic wiretapping programs like COINTELPRO and the subsequent investigation and recommendations of the Church Committee. Limits had been placed especially on domestic surveillance as a result of the excesses of Hoover’s FBI investigations into the personal lives of Martin Luther King and others.
Despite all of these restrictions, after 9/11 the government swept aside many of the intelligence reforms from the 1970s and put in place a massive surveillance network at the local, national, and global level to achieve total information awareness of the American people. Programs created after 9/11 for foreign intelligence gathering were turned on Americans. Plus, new technological capabilities made it possible to sweep Americans up with foreign surveillance—both incidentally and intentionally. The digital revolution made the intelligence community’s wildest dreams come true. The perceived crisis of global terrorism, of course, naturalized and justified the gradual encroachments. But the domestication of total surveillance had deeper roots in the very logic of counterinsurgency warfare. The fact is, in this new governing paradigm, every American is a potential insurgent.
Constant vigilance of the American population is necessary—hand in hand with the appearance of trust. Appearances are vital. A domesticated counterinsurgency must suspect everyone in the population, but not let it be known. This posture, developed in counterinsurgency theory decades ago, was at the core of the paradigm. David Galula had refined it to a witty statement he would tell his soldiers in Algeria: “One cannot catch a fly with vinegar. My rules are: outwardly you must treat every civilian as a friend; inwardly you must consider him as a rebel ally until you have positive proof to the contrary.”2 This mantra has become the rule today—at home.
In the wake of the Twin Tower attacks, the NYPD started surveilling hundreds of mosques, Muslim businesses, associations, and student groups—infiltrating dozens of them—without any evidence they were tied to terrorism or had engaged in wrongdoing. The NYPD recruited “mosque crawlers” to infiltrate and monitor Islamic places of worship, and “rakers” to infiltrate Muslim bookstores, cafés, and bars. (They were called rakers because the head of intelligence, who came from the CIA, would say he wanted his unit to “rake the coals, looking for hot spots.”) The NYPD infiltrated student groups at Brooklyn College and City College of New York, and accessed student records under false pretenses.3
“Place Mosque under observation before and during Jumma (Friday Prayers), record license plates and capture video and photographic record of those in attendance. Pay special attention to all NY State License plates.” Those were the directions given to NYPD undercover agents in the “Target of Surveillance” directive regarding the Majid Omar Mosque in Patterson, New Jersey.4 An “NYPD Secret Weekly MSA Report” dated November 22, 2006, recounted the activities of the Muslim Student Associations at Buffalo, at NYU, and at Rutgers–Newark.5 The NYPD intelligence officer reported visiting, in his words, “as a daily routine,” the websites, blogs, and forums of the Islamic student organizations there and at Albany University, Baruch College, Brooklyn College, Columbia University, LaGuardia Community College, University of Pennsylvania, Rutgers–New Brunswick, Stony Brook, SUNY Potsdam, Syracuse University, Yale University, and others. He detailed an upcoming scholarly conference at the Toronto Convention Center, discussing the background and visa status of the invited speakers.
In a secret intelligence briefing for the head of intelligence, dated April 25, 2008, the NYPD reported being worried about the verdict in the Sean Bell case—the acquittal of three NYPD detectives charged in the multiple-shooting death of an unarmed man in Jamaica, Queens. The briefing reported that the agency was “especially concerned with and keying on our convert mosques i.e. Ikhwa, Taqwa, Iqquamatideen and MIB (Mosque of Islamic Brotherhood)” and asked a confidential informant to get “involved with the New Black Panther Party.”6
The same briefing detailed another covert NYPD operation to infiltrate a whitewater rafting-trip by students at City College of New York. The briefing recounted that an undercover NYPD operative, named “OP# 237,” left for the “Whitewater Rafting trip Monday, April 21, 2008 and returned Wednesday night April 23, 2008.” It explained, “The trip was hosted by the EXTREMEGOERS CCNY SPORTS GROUP; which is essentially run by the MSO [Muslim Student Organization].” It detailed the names and status of many of the nineteen CCNY students, noting that “Ali Ahmed was in charge and did orchestrate the events.” It emphasized, “In addition to the regularly scheduled events (Rafting), the group prayed at least four times a day, and much of the conversation was spent discussing Islam and was religious in nature.”7 Although the report spoke in conspiratorial terms, there was no prior reason—and none developed—to suspect the college students of anything.
The NYPD prepared analytic reports with maps and intelligence covering every mosque within one hundred miles of the city, including in Newark, New Jersey, and Suffolk and Nassau Counties, detailing their addresses, telephone numbers, pictures, ethnic affiliation, and “information of note,” with entries such as “During visit 3 African Muslim males and an Egyptian male customer were observed dining within” and “Observed a lot of products made in Egypt were sold inside the location.”8 These secret “Demographics Unit” reports mapped mosques, madrassahs, and Muslim population density by ethnicity. They included surveillance photos and intelligence notes on every mosque and Muslim businesses (see surveillance reports on next page).
The Associated Press described the program, in a Pulitzer Prize–winning series, as a “human mapping program” of American Muslims that amounted to “an unusual partnership with the CIA that has blurred the line between foreign and domestic spying.” This kind of monitoring of Muslims without any suspicion would have run afoul if it had been done by the federal government, which may explain, as AP suggested, why the CIA worked surreptitiously with the NYPD to ramp up this domestic spying program and also why the federal government gave the NYPD more than $1.6 billion over the decade following 9/11.9
Several years later, in August 2016, the Office of the Inspector General for the NYPD issued a report detailing the extent of the targeting of Muslims. It reviewed a random sample of NYPD intelligence investigations from 2010 to 2015 and found that 95 percent of the investigations of political activities targeted Muslims or activity associated with Islam.10 It also found that over 50 percent of those investigations continued after outliving their authorization.
Following the revelations by the AP, the ACLU filed suit in June 2013 on behalf of plaintiffs challenging the surveillance of mosques. The litigation captured well the historical trajectory of the domestication of counterinsurgency practices. The 2013 case, Raza v. City of New York, was folded back into an earlier federal case known as the Handschu litigation. The Handschu case had been filed in 1971 and challenged NYPD surveillance of the Black Panthers, antiwar protesters, the ACLU, NAACP, and others.11 Handschu addressed precisely the first domestic uses of counterinsurgency strategies—the early antecedents to today’s more coordinated and systemic counterinsurgency. It would serve as the framework to assess the new more systematic surveillance programs targeting mosques, Muslims, and Islamic-related businesses and student groups.


NYPD surveillance report on mosque and Islamic businesses in Newark, New Jersey (redacted here to protect privacy). (NYPD Intelligence Division, Demographics Unit, “Newark, New Jersey, Demographics Report,” September 25, 2007, pp. 31, 46.)
Federal judge Charles S. Haight Jr. of the Southern District of New York oversaw the Handschu litigation from its inception, including a settlement agreement in 1985 that led to the famous Handschu guidelines for oversight of the NYPD’s investigations of political activity. For years, the police department was under an agreement that prevented its intelligence unit from instigating investigations of political activity, and required that any such investigations be based on evidence of a crime. That original agreement was modified shortly after 9/11 to allow the NYPD more flexibility in its investigations of political activity. But even under those more relaxed standards, the NYPD surveillance of mosques and student groups pushed the boundaries of legality, resulting in new modifications of the Handschu guidelines.
In various interviews during the 2016 presidential campaign, President Donald Trump endorsed the continued surveillance of mosques and Muslim groups. President Trump indicated that he favored increased surveillance of American Muslims, possible registration of American Muslims in a government database, and even issuing special identifications for Muslims noting their religious faith.12 “You’re going to have to watch and study the mosques, because a lot of talk is going on in the mosques,” Trump told MSNBC’s Morning Joe in November 2015. Referring specifically to the NYPD intelligence programs that monitored New York’s Muslims, Trump said that “from what I heard, in the old days—meaning a while ago—we had a great surveillance going on in and around the mosques of New York City.”13
While the NYPD was ramping up a dragnet surveillance program of Muslims with the aid of the CIA, the FBI and federal prosecutors launched a massive nationwide information gathering campaign targeting Middle Eastern men from predominantly Muslim countries living in the United States on nonimmigrant visas. About two months after 9/11, US attorney general John Ashcroft announced a national campaign to interview as many as five thousand of these men. Federal authorities in Michigan rapidly responded and started the initiative, sending out over 560 letters to the targeted minority, identified as men being between the ages of eighteen and thirty-three from Middle Eastern Muslim countries. Here too, the authorities had no evidence or any reason to believe that any one of them was connected to terrorism or wrongdoing; in fact, the federal officials emphasized as much in those letters, saying, “We have no reason to believe that you are, in any way, associated with terrorist activities.”14 But despite the complete absence of suspicion, the federal authorities pressured the men to meet and talk to federal agents and local police. In order to conduct all these interviews, Ashcroft had asked local police enforcement to pitch in, further domesticating the strategies.
“Please contact my office to set up an interview at a location, date, and time that is convenient for you,” the letter stated. “While this interview is voluntary, it is crucial that the investigation be broad-based and thorough, and the interview is important to achieve that goal. We need to hear from you as soon as possible—by December 4. Please call my office between 9 a.m. to 5 p.m. any day, including Saturday and Sunday. We will work with you to accommodate your schedule.” Signed by the US attorney for the eastern district of Michigan, these letters couched voluntariness in terms of “needing” to hear back within a week. And given that the targeted men were on nonimmigrant visas, these invitations in truth read as commands.
In addition to these local and domestic national surveillance programs, foreign-style intelligence collection was turned on the American masses. The Bush administration put in place an infamous NSA eavesdropping program inside the United States without prior court approval or any court orders. Congress passed the Section 215 program that collected data from American telecommunications companies. The NSA put in place a number of signal intelligence programs that captured and monitored all telecommunications data including that of American citizens. Through private sector cooperation with Microsoft, AT&T, and social media, the FBI and NSA increasingly get backdoor access to e-mail services and cloud storage facilities, and direct access to the servers of Yahoo, Google, Facebook, etc.
The NSA’s core programs worked in tandem and piggy-backed off the collection and mining of all our personal data by social media and retailers. Since the advent of free e-mail, storage, and social-media services, such as Gmail by Google, Outlook and SkyDrive by Microsoft, or Facebook, these digital giants began collecting all our personal data that crossed their servers. Their business models depended on it, insofar as the only source of income related to these free services was digital advertising. Other digital merchants, such as Amazon, Netflix, and other online retailers, also began capturing all their customers’ personal information as well, for purposes of advertising and pushing targeted products on consumers. All of these private giants of the digital age began collecting everyone’s data for their own commercial interests. The NSA, who figured this out quickly, soon received access to this data through licit and illicit means. Through programs like PRISM and UPSTREAM, the NSA gained total access to their servers and to the cables through which all of this data streamed.
The PRISM program, discussed earlier in the context of foreign intelligence collection, allowed the NSA to directly access the servers of most of the American digital giants, meaning that agents at the NSA and delegated consultants could directly access the servers of these companies to field inquiries and searches on foreigners as well as Americans. The agency gained direct access to the content of e-mails, attachments, VoIP calls, and all digital communications, allowing access to the personal data of foreigners as well as the information of American citizens. The UPSTREAM program provided the NSA with a copy of all the digital traffic going through undersea cables. And other NSA programs for the collection and mining of our personal digital data proliferated, resulting in a stunning level of access to the private information of Americans.
The invasiveness of today’s digital surveillance is truly breathtaking. The creation of these programs coincided with the explosive growth of digital technologies, all of which are rooted in and enable invasive surveillance of those who use them. Our network service providers, search engines, and social-media companies monitor our every digital trace to recommend products, sell advertisements, and fuel consumption. Google collects and mines our Gmail e-mails, attachments, contacts, and calendars. Netflix and Amazon use our data to recommend films, and Twitter tracks our Internet activity on all the websites that carry its little icon. Facebook’s smartphone app collects information from our other phone apps and pushes advertisements onto them. Instagram verifies ad impressions, measures their success, and provides feedback to the advertisers as to which are most effective. Neighbors use packet sniffers or free Mac software, like Eavesdrop, to tap into our unsecured networks. Google’s street-view cars captured and recorded our usernames, passwords, and personal e-mails on unencrypted Wi-Fi traffic.
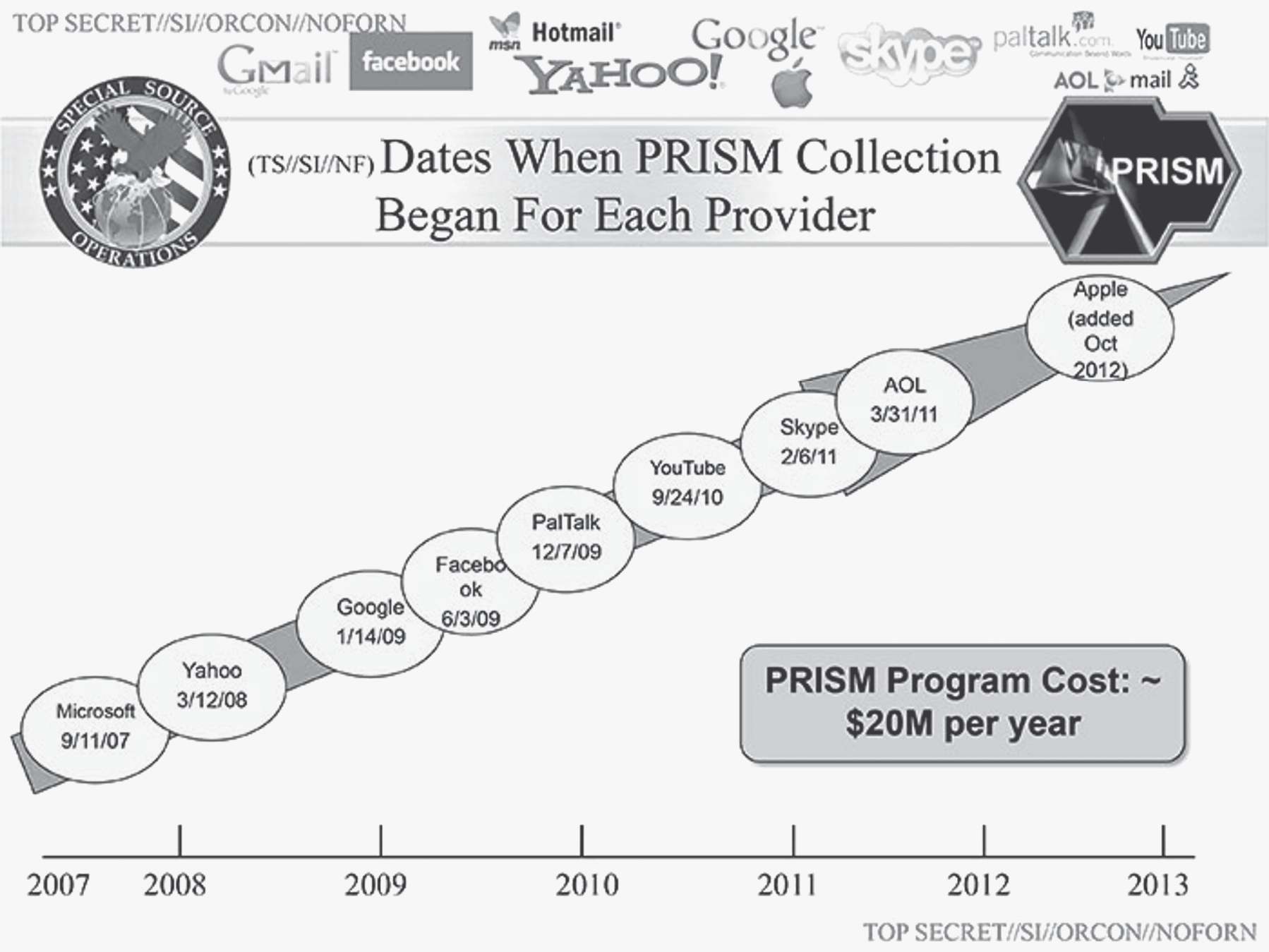
And as Edward Snowden’s revelations demonstrated, the NSA has practically free access to all of this information through multiple means. A quick look at the top-secret PRISM slides reminds us of the reach into our personal lives: Microsoft, Yahoo, Google, Facebook, Paltalk, YouTube, Skype, AOL, Apple, etc. All of these companies gave the NSA access to communications conducted through them under the PRISM program, and they did so for a trifling sum. According to the Snowden revelations, the entire PRISM program cost the NSA a mere $20 million per year. For that tiny amount, the NSA had direct access to their servers—over and above the cutting and splicing into telecom cables that gave the NSA direct access to all digital communications.
As a result, in the United States today, ordinary citizens face a multifaceted web of surveillance. Social media, retailers, smartphone applications, Internet providers, and web browsers are all collecting our private data, and making them available to the intelligence agencies. Most new technology and apps—even games, like Pokémon GO—thrive on accessing our contacts, our GPS location, our calendar, our webcam, and all our private information. We are surrounded by a Lernaean Hydra of telecoms, social media, Google platforms, Facebook apps, Microsoft products, retailers, data brokers, multinational corporations, hackers—including foreign government hackers—and our own intelligence agencies, each of which is trying to outdo the other to collect and mine our personal information, each of them pursuing total information awareness with unparalleled vigor.
NSA PowerPoint slide on PRISM program history (2013). (“NSA Slides Explain the PRISM Data-Collection Program,” Washington Post, June 6, 2013.)
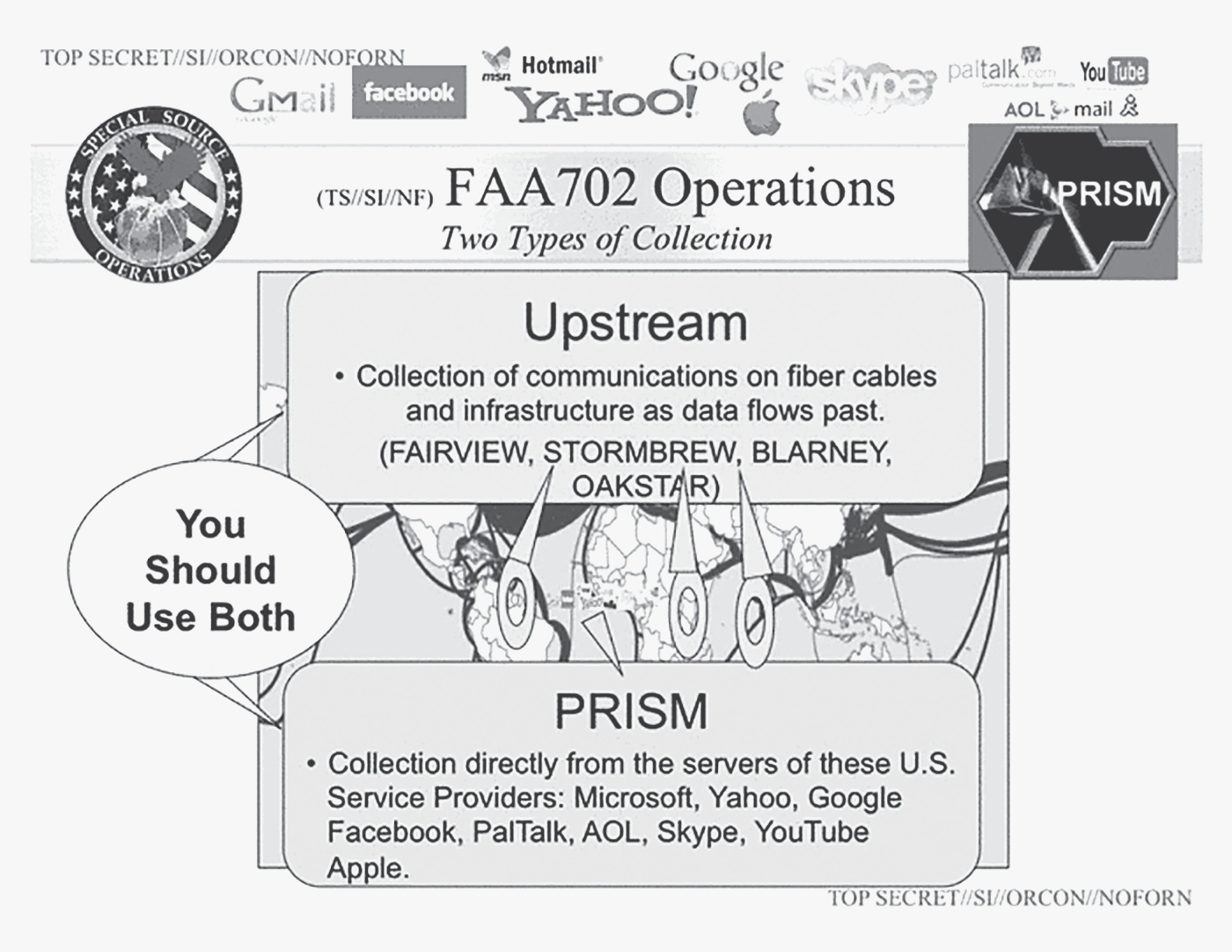
NSA PowerPoint slide on PRISM and UPSTREAM programs (2013). (“NSA Slides Explain the PRISM Data-Collection Program,” Washington Post, June 6, 2013.)
In Exposed, I proposed a new way to understand how power circulates in the digital age and, especially, a new way to comprehend our willingness to expose ourselves to private corporations and the government alike. The metaphors commonly used to describe our digital condition, such as the “surveillance state,” Michel Foucault’s panopticon prison, or even George Orwell’s Big Brother, are inadequate, I argued there. In the new digital age we are not forcibly imprisoned in panoptic cells. There is no “telescreen” anchored to the wall of our apartments by the state. No one is trying to crush our passions, or wear us down into submission with the smell of boiled cabbage and old rag mats, coarse soap, and blunt razors. The goal is not to displace our pleasures with hatred—with “hate” sessions, “hate songs,” “hate weeks.” Today, instead, we interact by means of “likes,” “shares,” “favorites,” “friending,” and “following.” We gleefully hang smart TVs on the wall that record everything we say and all our preferences. The drab uniforms and grim grayness of Orwell’s 1984 have been replaced by the iPhone 5c in its radiant pink, yellow, blue, and green. “Colorful through and through,” its marketing slogan promises, and the desire for color-filled objects—for the sensual swoosh of a sent e-mail, the seductive click of the iPhone camera “shutter,” and the “likes,” clicks, and hearts that can be earned by sharing—seduce us into delivering ourselves to the surveillance technologies.
And as the monitoring and marketing of our private lives changes who we are, power circulates in a new way. Orwell depicted the perfect totalitarian society. Guy Debord described ours rather as a society of the spectacle, in which the image makers shape how we understand the world and ourselves. Michel Foucault spoke instead of “the punitive society” or what he called “panopticism,” drawing on Jeremy Bentham’s design of the panoptic prison. Gilles Deleuze went somewhat further and described what he called “societies of control.” But in our digital age, total surveillance has become inextricably linked with pleasure. We live in a society of exposure and exhibition, an expository society.
It is precisely the pleasure and attractions, the seductions of the digital age that make us expose ourselves so willingly. And even those of us who do not partake in the rich world of social media, or hesitate to leave traces, end up sharing our intimate lives and political views digitally. It is practically impossible to have a social or family life without at least text messages, cell phones, and/or e-mail. It is almost impossible to live in today’s world without searching the web, buying online, swiping an access card, retrieving money from an ATM. It is virtually impossible to have a professional life without filling out Doodles and SurveyMonkeys, or responding to Paperless Post.
Confronting the expository society requires looking both at and beyond the state to social media, corporate and retail interests, Silicon Valley, AT&T, and beyond these to ourselves, with our apparently insatiable and irresistible impulses, urges, and jouissance to exhibit ourselves. The problem today is not only the state; it is also all of us, we who give ourselves away to total surveillance. And not only us, but our gadgets as well: our smartphones that emit GPS data and allow Facebook to cull data from all other apps, or from virtual reality games like Pokémon GO. These devices have become powerful entry points into a treasure trove of personal information and interconnected geo-located data.
In August 2015, leaked documents revealed that the American telecommunications giant, AT&T, had willingly worked with the NSA as recently as 2013 to provide access “to billions of e-mails as they have flowed across its domestic networks.” AT&T voluntarily installed cable-splicing equipment at its communications hubs in the United States. AT&T was particularly solicitous, the New York Times noted. “AT&T was the first partner to turn on a new collection capability that the NSA said amounted to a ‘live’ presence on the global net.”15
Early on, AT&T’s partnership fueled an intelligence program that, in a single month, captured and sent to the NSA four hundred billion Internet metadata records. On a daily basis, more than a million e-mails were processed through the keyword selection system at NSA’s headquarters in Fort Meade, Maryland. According to the NSA’s internal documents, which cover periods ranging from 2003 to 2013, AT&T’s “corporate relationships provide unique accesses to other telecoms and I.S.P.s” as well. As the New York Times added, with a twist of irony, “One document reminds NSA officials to be polite when visiting AT&T facilities, noting, ‘This is a partnership, not a contractual relationship.’”
These new revelations were a fitting capstone to the passage of the USA FREEDOM Act by the US Congress two months earlier in June 2015. The FREEDOM Act was Congress’s attempt to redress the balance between privacy and security in the wake of the Edward Snowden leaks two years earlier. It targeted one and only one of the NSA’s surveillance platforms, the Section 215 program of the USA PATRIOT Act, a provision that authorized the domestic bulk collection of telephony metadata in the United States.
President Obama heralded the FREEDOM Act as an important measure that would “strengthen civil liberty safeguards and provide greater public confidence in these programs.”16 The Guardian reported that “privacy and reform activists hailed the bill as a ‘milestone’ achievement, the first reform of surveillance programs in more than a decade.”17 In its most significant provision, the FREEDOM Act modified the Section 215 program so that, from now on, it would be the telecom companies, companies like AT&T, that will hold and maintain Americans’ telephony metadata.
It is hard to miss the irony. It is now AT&T who protects us. The same telecom company that had gone out of its way to collaborate, often in illicit ways, for years if not decades, with US signal intelligence services to provide access to private telecommunications and personal data. The same company that, according to the newly leaked documents, enthusiastically and voluntarily cooperated with the NSA and “installed surveillance equipment in at least 17 of its Internet hubs on American soil.”
And as if that were not enough, in the fine print of the landmark legislation, it turns out that we, American taxpayers, will compensate AT&T for holding their data. As Reuters reported, “The FREEDOM Act does contain a provision to compensate companies for costs they incur holding and turning over such data, which is something the carriers made clear they wanted in return for agreeing to store the data.”18 That arrangement was baked into the compromise early on. President Obama’s advisers—a committee composed of an eclectic range of former officials and academics—had originally recommended this remunerative arrangement. In their report, Liberty and Security in a Changing World, Obama’s advisers wrote that “it would be in the interests of the providers and the government to agree on a voluntary system that meets the needs of both”; but, they added, if such a mutually agreeable deal could not be worked out, “the government should reimburse the providers for the cost of retaining the data.”19
And that’s what happened: taxpayers would pay the telecoms to hold the data for the government. So, before, AT&T surreptitiously provided our private personal digital data to the intelligence services free of charge. Now, American taxpayers will pay them to collect and hold on to the data for when the intelligence services need them. A neoliberal win-win solution for everyone—except, of course, the ordinary, tax-paying citizen who wants a modicum of privacy or protection from the counterinsurgency.
We live in a new digital age that has fundamentally transformed every aspect of society and politics as we know it—and that will continue to. It is estimated that digital technologies and artificial intelligence will eliminate 40 to 50 percent of all jobs and employment over the next decades. These technologies have already radically transformed our leisure and punishment practices, and exposed us and our every whim to the watchful eyes of marketers, advertisers, social media, and intelligence services. The monitoring and marketing of our private lives here, on American soil, not only by the NSA, but also by Facebook, Google, Microsoft, Apple, etc., is stunning. The digital age has effectively inserted the surveillance capability into practically every daily routine.
In my previous book, however, I failed to fully grasp how our expository society fits with the other features of our contemporary political condition—from torture, to Guantánamo, to drone strikes, to digital propaganda. In part, I could not get past the sharp contrast between the fluidity of our digital surfing and surveillance on the one hand, and the physicality of our military interventions and use of torture on the other. To be sure, I recognized the deadly reach of metadata and reiterated those ominous words of General Michael Hayden, former director of both the NSA and the CIA: “We kill people based on metadata.”20 And I traced the haunting convergence of our digital existence and of correctional supervision: the way in which the Apple Watch begins to function like an electronic bracelet, seamlessly caging us into a steel mesh of digital traces. But I was incapable then of fully understanding the bond between digital exposure and analog torture.
It is now clear, though, that the expository society fits seamlessly within our new paradigm of governing. The expository society is precisely what allows the counterinsurgency strategies to be applied so impeccably “at home” to the very people who invented modern warfare. The advent of the expository society, as well as the specific NSA surveillance programs, makes domestic total information awareness possible, and in turn lays the groundwork for the other two prongs of counterinsurgency in the domestic context.