Chapter 6
Roles and Responsibilities
Abstract
The evaluation and testing roles and responsibilities are defined here in detail for each test, evaluation, and authorization role in the RMF, to include the extra defined roles found in the DOD implementation of RMF.
Keywords
roles and responsibilities
system owner
authorizing official
security officer
security control assessor
The Risk Management Framework acknowledges that organizations have widely varying missions and organizational structures, so there may be differences in naming conventions for risk management-related roles and how specific responsibilities are allocated among organizational personnel (e.g., multiple individuals filling a single role or one individual filling multiple roles). However, the basic functions remain the same. The application of the Risk Management Framework is flexible, allowing organizations to effectively accomplish the intent of the specific tasks within their respective organizational structures to best manage information system-related security risks.
Many risk management roles have counterpart roles defined in the routine system development life cycle processes carried out by organizations. Whenever possible, organizations should align the risk management roles with similar (or complementary) roles defined for the system development life cycle.
Organizational roles
White House
This is the US government executive office given statutory authority to issue Executive Orders, proclamations, Presidential Decision Directive (PDD)/HSPD/Nation Safe Drivers (NSD), and similar documents that initiate action, stop action, or require general notice be given (Fig. 6.1). These directives and orders drive the creation and promulgation of executive policy throughout the Executive Branch and agencies.
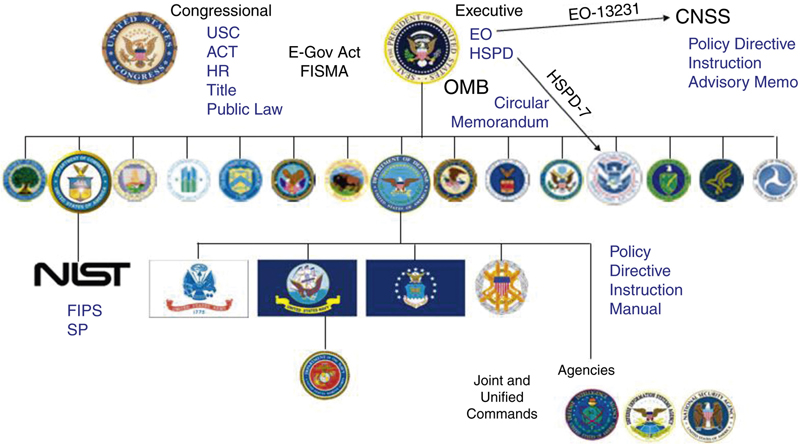
Figure 6.1 General statutory and regulatory agency structure.
Congress
This is the US government legislative body responsible for the US Code and the general, permanent laws of the nation that it contains. Congress’s power to authorize the appropriation of federal spending to carry out government activities drives a lot of the laws and their implementation efforts across the government.
OMB
The Office of Management and Budget is the Executive Branch agency which evaluates expenditure effectiveness, and provides oversight of administration procurement, fiscal management, information management, and regulatory policy, to include management of information systems and their security.
NIST
National Institute of Standards and Technology (NIST), an agency of the US Department of Commerce, has statutory responsibility to ensure that standards and measures are developed to improve performance, and is charged by law with responsibility for information security standards, metrics, tests, and various other means to support Executive Branch agencies’ missions. NIST issues Special Publications (SP), Federal Information Processing Standards (FIPS), Information Technology Laboratory (ITL) Bulletins, NIST Interagency Reports (NISTIR), and other guidance.
CNSS
Formerly known as NSTISSC, the Committee on National Security Systems (CNSS) provides a participative forum to examine national policy and promulgates direction, operational procedures and instructions (CNSSI), and other forms of authoritative guidance for national security systems. The CNSS is composed of 21 agencies with the US government with NSS systems and is chaired by the Department of Defense (DOD) CIO.
NSA
1. The National Security Agency (NSA) is the US government’s formal cryptological organization and is part of the US DOD.
2. The NSA has responsibility for ensuring that all cryptographic methods and systems used to protect US federal government (USFG) information and systems are sufficiently strong, for penetrating adversary systems and codes, and to ensure that all national security information is protected appropriately whether in transit or at rest.
NIAP
National Information Assurance Partnership (NIAP) is an initiative partnership between the NIST (Commerce) and the NSA (DOD) to evaluate and attempt to meet the needs and requirements of IT/IA product producers and consumers to evaluate functionality and pedigree.
DHS
The US Department of Homeland Security is responsible for overseeing the protection of the .gov domain and for providing assistance and expertise to private sector owners and operators. The US Computer Emergency Response Team (US-CERT) is an agency within DHS. The DHS agency’s work benefits the information technology community and the public at large. DHS plays a key role in securing the federal government’s civilian cyber networks and helping to secure the broader cyber ecosystem through:
• Partnerships with owners and operators of critical infrastructure such as financial systems, chemical plants, and water and electric utilities
• The release of actionable cyber alerts
• Investigations and arrests of cybercriminals
• Education about how the public can stay safe online
DOD
The DOD is the US governmental agency responsible for the security of the nation and its allies. It has a long history of developing and providing security to the United States, its citizens, and the general public in the United States and overseas. IT security has always maintained a high profile within DOD and continues so today with many security programs, processes, procedures, and guidance documents. NSA, Defense Intelligence Agency (DIA), and all of the military services are all part of DOD and follow these directives, instructions, and regulations.
Individual roles
The primary individual roles, as defined in SP 800-37, rev. 1, are as follows:
• Authorizing official/DAA
• Authorizing official designated representative
• Chief information officer
• Senior agency information security officer
• Information system owner
• Information system security officer
• Program manager (PM)
• Security control assessor
• User representative
System Owner
The information system owner is an organizational official responsible for the procurement, development, integration, modification, operation, maintenance, and disposal of an information system. The system owner is the singular primary role within the RMF. This role has primary responsibilities for 4.5 of the 6 steps within the RMF and is the lead role for the entire process. DOD has defined this role in DODI 8510.01 at the PM or systems manager (SM) level within the DOD acquisition process.
The primary objectives of the system owner are to:
• Procure, develop, integrate, modify, operate, or maintain an information system
• Prepare the system security plan and conduct risk assessment
• Inform agency officials of the need for certification and accreditation
• Ensure appropriate resources are available
• Provide necessary system-related documentation
• Prepare plan of action and milestones to reduce or eliminate vulnerabilities in the information system
• Assemble final accreditation package and submit to authorizing official
• Also act as user representative – in RMF arena
The information system owner is responsible for addressing the operational interests of the user community (i.e., users who require access to the information system to satisfy mission, business, or operational requirements) and for ensuring compliance with information security requirements.
In coordination with the information system security officer, the information system owner is responsible for the development and maintenance of the security plan and ensures that the system is deployed and operated in accordance with the agreed-upon security controls.
In coordination with the information owner/steward, the information system owner is also responsible for deciding who has access to the system (and with what types of privileges or access rights) and ensures that system users and support personnel receive the requisite security training (e.g., instruction in rules of behavior).
Based on guidance from the authorizing official, the information system owner informs appropriate organizational officials of the need to conduct the security authorization, ensures that the necessary resources are available for the effort, and provides the required information system access, information, and documentation to the security control assessor. The information system owner receives the security assessment results from the security control assessor. After taking appropriate steps to reduce or eliminate vulnerabilities, the information system owner assembles the authorization package and submits the package to the authorizing official or the authorizing official designated representative for adjudication.
Authorizing Official
The authorizing official is a senior official or executive with the authority to formally assume responsibility for operating an information system at an acceptable level of risk to organizational operations and assets, individuals, other organizations, and the nation.
Authorizing officials typically have budgetary oversight for an information system or are responsible for the mission and/or business operations supported by the system.
Through the security authorization process, authorizing officials are accountable for the security risks associated with information system operations.
The primary objectives of the authorizing official are to:
• Executive with authority and ability to evaluate the security risks
• Has either IT business oversight or budgetary responsibility
• Balance cost/benefit
• Must be government employee
• Make accreditation decisions
• Review security status reports from continuous monitoring operations
• Probably initiate reaccreditation actions based on status reports
Accordingly, authorizing officials are in management positions with a level of authority commensurate with understanding and accepting such information system-related security risks. Authorizing officials also approve security plans, memorandums of agreement or understanding, and plans of action and milestones and determine whether significant changes in the information systems or environments of operation require reauthorization. They can deny authorization to operate an information system or if the system is operational, halt operations, if unacceptable risks exist.
Authorizing officials coordinate their activities with the risk executive (function), chief information officer, senior information security officer, common control providers, information system owners, information system security officers, security control assessors, and other interested parties during the security authorization process. With the increasing complexity of missions/business processes, partnership arrangements, and the use of external/shared services, it is possible that a particular information system may involve multiple authorizing officials. If so, agreements are established among the authorizing officials and documented in the security plan.
Authorizing officials are responsible for ensuring that all activities and functions associated with security authorization that are delegated to authorizing official designated representatives are carried out. The role of authorizing official has inherent US government authority and is assigned to government personnel only.
Information System Security Officer
The information system security officer is an individual responsible for ensuring that the appropriate operational security posture is maintained for an information system and as such works in close collaboration with the information system owner.
The primary objectives of the information system security officer are to:
• Be primary advisor to the system owner on security matters
• Manage the security aspects of the information system
• Assist the system owner:
• Develop and enforce security policies for the information system.
• Manage and control changes to the information system and assess the security impacts of those changes.
The information system security officer also serves as a principal advisor on all matters, technical and otherwise, involving the security of an information system.
The information system security officer should have the detailed knowledge and expertise required to manage the security aspects of an information system and, in many organizations, is assigned responsibility for the day-to-day security operations of a system. This responsibility may also include, but is not limited to, physical and environmental protection, personnel security, incident handling, and security training and awareness.
The information system security officer may be called upon to assist in the development of the security policies and procedures and to ensure compliance with those policies and procedures.
In close coordination with the information system owner, the information system security officer often plays an active role in the monitoring of a system and its environment of operation to include developing and updating the security plan, managing and controlling changes to the system, and assessing the security impact of those changes.
Information System Security Engineer
The information system security engineer is an individual, group, or organization responsible for conducting information system security engineering activities.
Information system security engineering is a process that captures and refines information security requirements and ensures that the requirements are effectively integrated into information technology component products and information systems through purposeful security architecting, design, development, and configuration.
The primary objectives of the information system security engineer are to:
• Work as part of the development team
• Employ and install security control best practices
• Coordinate security-related activities:
• Equivalent to DIACAP Information Assurance Office (IAO)
Information system security engineers are an integral part of the development team (e.g., integrated project team), designing and developing organizational information systems or upgrading legacy systems. They employ best practices when implementing security controls within an information system including software engineering methodologies, system/security engineering principles, secure design, secure architecture, and secure coding techniques.
System security engineers coordinate their security-related activities with information security architects, senior information security officers, information system owners, common control providers, and information system security officers.
Security Architect
The information security architect is an individual, group, or organization responsible for ensuring that the information security requirements necessary to protect the organization’s core missions and business processes are adequately addressed in all aspects of enterprise architecture including reference models, segment and solution architectures, and the resulting information systems supporting those missions and business processes.
The primary objectives of the information security architect are to:
• Adequately addresses security requirements in enterprise architecture:
• Reference models
• Segment and solution architectures
• Resulting information systems
• Act as a liaison between the enterprise architect and information system security engineer
• Act as an advisor to senior officials on following topics:
• System boundaries
• Assessing severity of deficiencies
• POAMs
• Risk mitigation approaches
• Security alerts
The information security architect serves as the liaison between the enterprise architect and the information system security engineer and also coordinates with information system owners, common control providers, and information system security officers on the allocation of security controls as system-specific, hybrid, or common controls.
In addition, information security architects, in close coordination with information system security officers, advise authorizing officials, chief information officers, senior information security officers, and the risk executive (function), on a range of security-related issues including, for example, establishing information system boundaries, assessing the severity of weaknesses and deficiencies in the information system, plans of action and milestones, risk mitigation approaches, security alerts, and potential adverse effects of identified vulnerabilities.
Common Control Provider
The common control provider is an individual, group, or organization responsible for the development, implementation, assessment, and monitoring of common controls (i.e., security controls inherited by information systems).
Common control providers are responsible for:
• Documenting the organization-identified common controls in a security plan (or equivalent document prescribed by the organization)
• Ensuring that required assessments of common controls are carried out by qualified assessors with an appropriate level of independence defined by the organization
• Documenting assessment findings in a security assessment report
• Appending a plan of action and milestones for any controls having weaknesses or deficiencies
• Ensuring that common controls within and across systems are properly documented and that documentation and communication are continuous
Security plans, security assessment reports, and plans of action and milestones for common controls (or a summary of such information) are made available to information system owners inheriting those controls after the information is reviewed and approved by the senior official or executive with oversight responsibility for those controls.
Authorizing Official Designated Representative
The authorizing official designated representative is an organizational official that acts on behalf of an authorizing official to coordinate and conduct the required day-to-day activities associated with the security authorization process.
The primary objectives of the authorizing official designated representative are to:
• Selected by the authorizing official
• Make certain decisions:
• Planning and sourcing of the security certification and accreditation activities
• Acceptance of the system security plan
• Determination of risk to agency operations, assets, and individuals
• Prepare accreditation decision letter
• Obtain authorizing official’s signature on appropriate documents
Authorizing official designated representatives can be empowered by authorizing officials to make certain decisions with regard to the planning and resourcing of the security authorization process, approval of the security plan, approval and monitoring of the implementation of plans of action and milestones, and the assessment and/or determination of risk.
The designated representative may also be called upon to prepare the final authorization package, obtain the authorizing official’s signature on the authorization decision document, and transmit the authorization package to appropriate organizational officials.
The only activity that cannot be delegated to the designated representative by the authorizing official is the authorization decision and signing of the associated authorization decision document (i.e., the acceptance of risk to organizational operations and assets, individuals, other organizations, and the nation).
Information Owner/Steward
The information owner/steward is an organizational official with statutory, management, or operational authority for specified information and the responsibility for establishing the policies and procedures governing its generation, collection, processing, dissemination, and disposal.
The information owner:
• Is an agency official with statutory or operational authority
• Is responsible for establishing rules for appropriate use of the information
• May, or may not, be the information system owner
• Can also be known as the data owner in the IC arena
In information-sharing environments, the information owner/steward is responsible for establishing the rules for appropriate use and protection of the subject information (e.g., rules of behavior) and retains that responsibility even when the information is shared with or provided to other organizations. The owner/steward of the information processed, stored, or transmitted by an information system may or may not be the same as the system owner. A single information system may contain information from multiple information owners/stewards. Information owners/stewards provide input to information system owners regarding the security requirements and security controls for the systems where the information is processed, stored, or transmitted.
Risk Executive (Function)
The risk executive (function) is an individual or group within an organization that helps to ensure that:
• Risk-related considerations for individual information systems, to include authorization decisions, are viewed from an organization-wide perspective with regard to the overall strategic goals and objectives of the organization in carrying out its core missions and business functions.
• Managing information system-related security risks is consistent across the organization, reflects organizational risk tolerance, and is considered along with other types of risks in order to ensure mission/business success. The risk executive (function) coordinates with the senior leadership of an organization to:
• Provide a comprehensive, organization-wide, holistic approach for addressing risk – an approach that provides a greater understanding of the integrated operations of the organization
• Develop a risk management strategy for the organization providing a strategic view of information security-related risks with regard to the organization as a whole
• Facilitate the sharing of risk-related information among authorizing officials and other senior leaders within the organization
• Provide oversight for all risk management-related activities across the organization (e.g., security categorizations) to help ensure consistent and effective risk acceptance decisions
• Ensure that authorization decisions consider all factors necessary for mission and business success
• Provide an organization-wide forum to consider all sources of risk (including aggregated risk) to organizational operations and assets, individuals, other organizations, and the nation
• Promote cooperation and collaboration among authorizing officials to include authorization actions requiring shared responsibility
• Ensure that the shared responsibility for supporting organizational mission/business functions using external providers of information and services receives the needed visibility and is elevated to the appropriate decision-making authorities
• Identify the organizational risk posture based on the aggregated risk to information from the operation and use of the information systems for which the organization is responsible
The risk executive (function) presumes neither a specific organizational structure nor formal responsibility assigned to any one individual or group within the organization. The head of the agency/organization may choose to retain the risk executive (function) or to delegate the function to another official or group (e.g., an executive leadership council). The risk executive (function) has inherent US government authority and is assigned to government personnel only.
User Representative
User representatives:
• Represent the operational interests of the user community
• Identify mission and operational requirements:
• Serve as liaisons for the user community
• Assist in the security certification and accreditation
• Comply with the security requirements and security controls
• Are identified in DOD, CNSS, and original 800-37 documents, but not in 800-37, rev. 1
Agency Head
The head of agency (or chief executive officer) is the highest-level senior official or executive within an organization with the overall responsibility to provide information security protections commensurate with the risk and magnitude of harm (i.e., impact) to organizational operations and assets, individuals, other organizations, and the nation resulting from unauthorized access, use, disclosure, disruption, modification, or destruction of:
1. Information collected or maintained by or on behalf of the agency
2. Information systems used or operated by an agency or by a contractor of an agency or other organization on behalf of an agency
Agency heads are also responsible for ensuring that:
1. Information security management processes are integrated with strategic and operational planning processes.
2. Senior officials within the organization provide information security for the information and information systems that support the operations and assets under their control.
3. The organization has trained personnel sufficient to assist in complying with the information security requirements in related legislation, policies, directives, instructions, standards, and guidelines.
Through the development and implementation of strong policies, the head of agency establishes the organizational commitment to information security and the actions required to effectively manage risk and protect the core missions and business functions being carried out by the organization. The head of agency establishes appropriate accountability for information security and provides active support and oversight of monitoring and improvement for the information security program. Senior leadership commitment to information security establishes a level of due diligence within the organization that promotes a climate for mission and business success.
Agency head requirements from A-130 and FISMA are as follows:
• Plan for adequate security.
• Assign responsibilities.
• Review security controls.
• Authorize processing.
Security Control Assessor
The security control assessor is an individual, group, or organization responsible for conducting a comprehensive assessment of the management, operational, and technical security controls employed within or inherited by an information system to determine the overall effectiveness of the controls (i.e., the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system).
The primary objectives of the security control assessor are to:
• Provide an independent assessment
• Assess the security controls:
• Implemented correctly
• Operating as intended
• Producing the desired outcome
• Provide recommended corrective actions
Security control assessors also provide an assessment of the severity of weaknesses or deficiencies discovered in the information system and its environment of operation and recommend corrective actions to address identified vulnerabilities.
In addition to these responsibilities, security control assessors prepare the final security assessment report containing the results and findings from the assessment.
Prior to initiating the security control assessment, an assessor conducts an assessment of the security plan to help ensure that the plan provides a set of security controls for the information system that meet the stated security requirements.
The required level of assessor independence is determined by the specific conditions of the security control assessment. For example, when the assessment is conducted in support of an authorization decision or ongoing authorization, the authorizing official makes an explicit determination of the degree of independence required in accordance with federal policies, directives, standards, and guidelines.
Assessor independence is an important factor in:
• Preserving the impartial and unbiased nature of the assessment process
• Determining the credibility of the security assessment results
• Ensuring that the authorizing official receives the most objective information possible in order to make an informed, risk-based authorization decision
The information system owner and common control provider rely on the security expertise and the technical judgment of the assessor to:
• Assess the security controls employed within and inherited by the information system using assessment procedures specified in the security assessment plan
• Provide specific recommendations on how to correct weaknesses or deficiencies in the controls and address identified vulnerabilities
This role has been named many different titles such as:
1. DIACAP Validator
2. Certifying Agent
3. Certifying Authority
4. System Certifier
Senior Information Security Officer
The senior information security officer is an organizational official responsible for:
• Carrying out the chief information officer security responsibilities under FISMA
• Serving as the primary liaison for the chief information officer to the organization’s authorizing officials, information system owners, common control providers, and information system security officers
The senior information security officer:
• Possesses professional qualifications, including training and experience, required to administer the information security program functions
• Maintains information security duties as a primary responsibility
• Heads an office with the mission and resources to assist the organization in achieving more secure information and information systems in accordance with the requirements in FISMA
The senior information security officer (or supporting staff members) may also serve as authorizing official designated representatives or security control assessors. The role of senior information security officer has inherent US government authority and is assigned to government personnel only.
Chief Information Officer
The chief information officer is an organizational official responsible for:
• Designating a senior information security officer
• Developing and maintaining information security policies, procedures, and control techniques to address all applicable requirements
• Overseeing personnel with significant responsibilities for information security and ensuring that the personnel are adequately trained
• Assisting senior organizational officials concerning their security responsibilities, and, in coordination with other senior officials, reporting annually to the head of the federal agency on the overall effectiveness of the organization’s information security program, including progress of remedial actions
The chief information officer, with the support of the risk executive (function) and the senior information security officer, works closely with authorizing officials and their designated representatives to help ensure that:
• An organization-wide information security program is effectively implemented resulting in adequate security for all organizational information systems and environments of operation for those systems.
• Information security considerations are integrated into programming/planning/budgeting cycles, enterprise architectures, and acquisition/system development life cycles.
• Information systems are covered by approved security plans and are authorized to operate.
• Information security-related activities required across the organization are accomplished in an efficient, cost-effective, and timely manner.
• There is centralized reporting of appropriate information security-related activities.
The chief information officer and authorizing officials also determine, based on organizational priorities, the appropriate allocation of resources dedicated to the protection of the information systems supporting the organization’s missions and business functions. For selected information systems, the chief information officer may be designated as an authorizing official or a coauthorizing official with other senior organizational officials. The role of chief information officer has inherent US government authority and is assigned to government personnel only.
DOD roles
There are some differences in the roles and responsibilities between the NIST-defined roles and the DOD-implemented roles under SP 800-37 and the DODI 8510 regulation. These differences include the DOD-defined roles of Principal Accrediting Authority (PAA), Information Assurance Manager (IAM), and IAO as reflected in Fig. 6.2 from 8510.01.
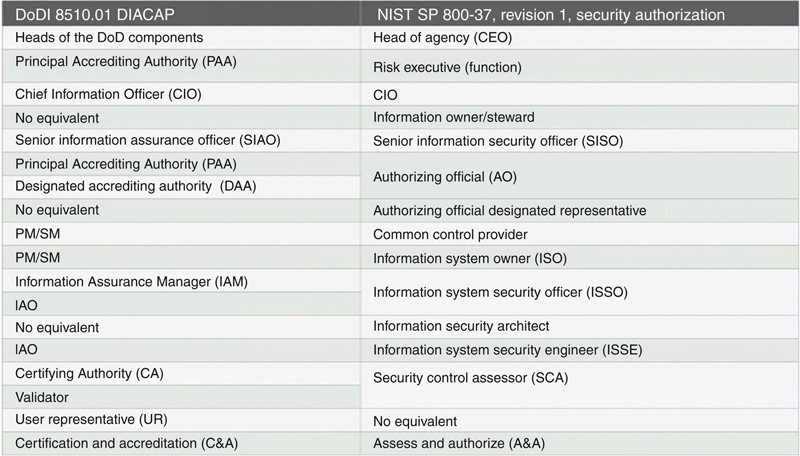
Figure 6.2 DODI 8510.01 roles and acronyms compared with NIST SP 800-37.