Figure 10-1: Business-use case.
Chapter 10
Software Applications
In This Chapter
 Examining software
Examining software
 Seeing what you actually need
Seeing what you actually need
 Checking out potential vendors
Checking out potential vendors
 Implementing guidelines
Implementing guidelines
The sheer volume of information that companies have to deal with, in combination with legal requirements and regulatory compliance, has made the task of records and information management a daunting challenge. In today’s business environment, attempting to manage information without the help of technology makes the task even more difficult.
This chapter provides a comprehensive approach to assessing your need for software, as well as clues you in on how to evaluate vendors and their applications. (For good measure, I throw in some tips for a successful implementation.) Using software to manage your records and information will create efficiencies and help ensure that you are in compliance with laws and regulations by automating policies and many existing manual processes.
Examining Software Options
In the following sections, I first examine the fundamentals of Records and Information Management software so that you understand the differences between the applications and the functionality they provide. Later in this chapter, I analyze the process for documenting your software requirements. Although technology shouldn’t dictate your requirements, it’s a good idea to understand what the software applications are capable of doing.
During the past 15 years, companies have experienced the impact of significant growth in information as well as laws and regulations. The growth in these areas and the resulting organizational needs that such growth has created haven’t gone unnoticed by software vendors. It only takes a single Internet search to see how many vendors are in the business of providing Records and Information Management software.
Numerous software applications are designed to meet specific records and information management needs. It’s important to be able to differentiate between the different systems and their capabilities. Some software provides comprehensive records and information management functionality, while other applications only address certain areas.
Laying the software foundation
 Document management: Sometimes the term Document Management software is used synonymously with Records Management software. Although they complement each other, a distinct difference exists. Document Management software provides functionality that helps manage document storage, retrieval, processing, and collaboration, but does not provide any records management functionality.
Document management: Sometimes the term Document Management software is used synonymously with Records Management software. Although they complement each other, a distinct difference exists. Document Management software provides functionality that helps manage document storage, retrieval, processing, and collaboration, but does not provide any records management functionality.
 Records management: Records Management software provides functionality that’s focused on compliance-related issues, such as information holds, retention monitoring, and disposition (the “managing” part of records management, as it were).
Records management: Records Management software provides functionality that’s focused on compliance-related issues, such as information holds, retention monitoring, and disposition (the “managing” part of records management, as it were).
For many years, Document Management and Records Management applications were provided as two separate software packages. However, over the past decade, they have joined forces. Vendors and clients realized that the functionality offered by each type of system could significantly enhance the other. Admittedly, a limited number of reputable vendors still provide separate Document and Records Management software applications, but most organizations are making the choice to purchase and implement comprehensive solutions.
 Premises-based: This option refers to the client purchasing the software and using its data center (its premises) and equipment to run the application.
Premises-based: This option refers to the client purchasing the software and using its data center (its premises) and equipment to run the application.
 Hosted: In a hosted environment, the client purchases the software, but the vendor operates the software in its (the vendor’s) data center.
Hosted: In a hosted environment, the client purchases the software, but the vendor operates the software in its (the vendor’s) data center.
 Subscription and hosted: Some software vendors allow companies to subscribe or “rent” their software. The software is then operated in the vendor’s data center.
Subscription and hosted: Some software vendors allow companies to subscribe or “rent” their software. The software is then operated in the vendor’s data center.
Types of software
Several types of software are used to manage records and information. The following list of software categories are used in many medium- and large-sized organizations:
 Records management (paper and electronic): This type of software focuses on the classification, storage, retrieval, and disposition (permanent archiving, destruction, and deletion) of organizational records.
Records management (paper and electronic): This type of software focuses on the classification, storage, retrieval, and disposition (permanent archiving, destruction, and deletion) of organizational records.
 Document management: Document Management software is designed to manage the classification, storage, and retrieval of company information. This includes records and nonrecord content. Document Management software by itself doesn’t provide records management functionality.
Document management: Document Management software is designed to manage the classification, storage, and retrieval of company information. This includes records and nonrecord content. Document Management software by itself doesn’t provide records management functionality.
 eDiscovery: This type of software has comprehensive search tools and the ability to isolate information relevant or potentially relevant to a lawsuit.
eDiscovery: This type of software has comprehensive search tools and the ability to isolate information relevant or potentially relevant to a lawsuit.
 Enterprise content management (ECM): Enterprise Content Management applications provide comprehensive records and information management functionality designed to support certain organizational operations or the entire company.
Enterprise content management (ECM): Enterprise Content Management applications provide comprehensive records and information management functionality designed to support certain organizational operations or the entire company.
Records Management software
Records Management software functionality focuses primarily on compliance-related matters such as information holds, retention monitoring, and disposition, rather than on features found in Document Management applications. The following list highlights the functionality common to most Records Management software:
 Classification: Records Management software applications provide users with the ability to apply classifications to records. This involves assigning a categorization or code to different record types.
Classification: Records Management software applications provide users with the ability to apply classifications to records. This involves assigning a categorization or code to different record types.
 Security: To ensure that records are protected from unauthorized use, the software provides security settings at an individual user or departmental level. This allows only authorized employees to search and request boxes of records or files.
Security: To ensure that records are protected from unauthorized use, the software provides security settings at an individual user or departmental level. This allows only authorized employees to search and request boxes of records or files.
 Box storage (physical): The software provides users who have onsite storage areas or facilities used for boxed record storage to configure their shelving units (including bar-coded locations) in the system. The software accounts for your boxed record inventory, allowing you to track its location and movement throughout the organization. Tracking functionality can be used for records stored on-site as well as with an offsite storage vendor.
Box storage (physical): The software provides users who have onsite storage areas or facilities used for boxed record storage to configure their shelving units (including bar-coded locations) in the system. The software accounts for your boxed record inventory, allowing you to track its location and movement throughout the organization. Tracking functionality can be used for records stored on-site as well as with an offsite storage vendor.
 File management: Records Management software applications provide the ability to account for records at the file level, including files located in cabinets, boxes, or (electronically) in the application repository. Typically, the systems will create a parent-child (hierarchical) relationship between boxed records and the files they contain. This allows you to search the system and request a specific file located in a box.
File management: Records Management software applications provide the ability to account for records at the file level, including files located in cabinets, boxes, or (electronically) in the application repository. Typically, the systems will create a parent-child (hierarchical) relationship between boxed records and the files they contain. This allows you to search the system and request a specific file located in a box.
 Search/request (physical): The software creates an inventory of all boxes of records and files accounted for in the system. This allows users to search their inventory based on their security and privilege settings and submit retrieval requests.
Search/request (physical): The software creates an inventory of all boxes of records and files accounted for in the system. This allows users to search their inventory based on their security and privilege settings and submit retrieval requests.
 Check-out/check-in (physical): Records Management software applications provide the ability to check boxes and files out to requestors and check them back in to a storage location after the requestor is finished reviewing or processing the information. The system uses bar-code technology and optional hand-held bar-code readers to scan the boxes and files when they are delivered to the requestor and when they are sent back to storage. In each case, the scanned information is uploaded into the software application so that the location of boxes or files can always be determined.
Check-out/check-in (physical): Records Management software applications provide the ability to check boxes and files out to requestors and check them back in to a storage location after the requestor is finished reviewing or processing the information. The system uses bar-code technology and optional hand-held bar-code readers to scan the boxes and files when they are delivered to the requestor and when they are sent back to storage. In each case, the scanned information is uploaded into the software application so that the location of boxes or files can always be determined.
 Record holds: The software enables Information Hold orders to be placed on records and files. This prevents the items from appearing on Destruction Eligibility reports produced automatically by the application. In addition, most systems have the ability to assign specific Hold Order titles to related groups of records that are placed on hold for the same lawsuit or investigation.
Record holds: The software enables Information Hold orders to be placed on records and files. This prevents the items from appearing on Destruction Eligibility reports produced automatically by the application. In addition, most systems have the ability to assign specific Hold Order titles to related groups of records that are placed on hold for the same lawsuit or investigation.
 Audit controls: This feature lets organizations track and report on data and setting changes, including information about who made changes and when they occurred. For example, if a classification is assigned a new retention period, the system will record what the previous retention was, what it was changed to, who made the change, and when it was changed.
Audit controls: This feature lets organizations track and report on data and setting changes, including information about who made changes and when they occurred. For example, if a classification is assigned a new retention period, the system will record what the previous retention was, what it was changed to, who made the change, and when it was changed.
 Retention management: When a classification is created in the system, it’s assigned a corresponding retention period. For example, you create a classification of “Invoice” and assign it a seven-year retention period. When a box of invoice records or an invoice file or document is entered into the application, the Invoice classification is applied and the date ranges of the information are entered. After this occurs, the software will begin the process of automatically monitoring the retention of the records and will generate a notification when the information is eligible to be destroyed or deleted.
Retention management: When a classification is created in the system, it’s assigned a corresponding retention period. For example, you create a classification of “Invoice” and assign it a seven-year retention period. When a box of invoice records or an invoice file or document is entered into the application, the Invoice classification is applied and the date ranges of the information are entered. After this occurs, the software will begin the process of automatically monitoring the retention of the records and will generate a notification when the information is eligible to be destroyed or deleted.
Document Management software
The lines between Records Management and Document Management software systems are often blurred. Each type of application possesses some of the same capabilities as the other, but also has some distinct differences. The objective of a Document Management application is to make it easier to find electronic information, while the objective of a Records Management system is to apply records management principles to the content.
Both systems allow you to store, classify, search, and retrieve documents. However, a Document Management system provides additional features that enhance the overall management process:
 Annotations: This feature allows you to attach electronic notes and watermarks to documents. The annotation is an overlay of metadata that becomes connected to a document, but doesn’t alter the document. Annotations can be helpful in providing additional information about a document.
Annotations: This feature allows you to attach electronic notes and watermarks to documents. The annotation is an overlay of metadata that becomes connected to a document, but doesn’t alter the document. Annotations can be helpful in providing additional information about a document.
 Redactions: A redaction involves the blacking-out of sensitive information on a document. The redaction is an overlay that doesn’t alter the underlying document in any fundamental way.
Redactions: A redaction involves the blacking-out of sensitive information on a document. The redaction is an overlay that doesn’t alter the underlying document in any fundamental way.
 Keywords: This feature provides the ability to assign multiple keywords (indexes) to a document type for efficient retrieval. For example, if you are attempting to locate an employee file, you don’t want to look through every active and inactive file. By using keywords, you can assign the employee ID, name, and date of hire to the document. Subsequently, if you need to locate the document, you can enter the keyword information, which will retrieve the specific file you need.
Keywords: This feature provides the ability to assign multiple keywords (indexes) to a document type for efficient retrieval. For example, if you are attempting to locate an employee file, you don’t want to look through every active and inactive file. By using keywords, you can assign the employee ID, name, and date of hire to the document. Subsequently, if you need to locate the document, you can enter the keyword information, which will retrieve the specific file you need.
 Full-text searching: Full-text searching provides additional search capability beyond the use of keywords. This feature allows you to search for specific words and phrases in the body of a document. Full-text searching is commonly used in Legal departments for contract reviews and disputes.
Full-text searching: Full-text searching provides additional search capability beyond the use of keywords. This feature allows you to search for specific words and phrases in the body of a document. Full-text searching is commonly used in Legal departments for contract reviews and disputes.
 Workflow: Workflow software allows an organization to programmatically automate existing manual processes. Workflow is a feature that can significantly enhance organizational efficiency. Through the use of business rules and preconfigured software functions, workflow allows you to automate processes that are currently performed manually. For example, in most organizations, invoice routing and processing may involve several manual steps. By implementing workflow, the invoice can be imaged and then automatically attached to the purchase order that was previously imaged along with the packing slip. The scanned packet of information is then sent through the workflow to an invoice processor. If the invoice is over a certain dollar limit, it can route to a second approver and then be automatically sent for payment.
Workflow: Workflow software allows an organization to programmatically automate existing manual processes. Workflow is a feature that can significantly enhance organizational efficiency. Through the use of business rules and preconfigured software functions, workflow allows you to automate processes that are currently performed manually. For example, in most organizations, invoice routing and processing may involve several manual steps. By implementing workflow, the invoice can be imaged and then automatically attached to the purchase order that was previously imaged along with the packing slip. The scanned packet of information is then sent through the workflow to an invoice processor. If the invoice is over a certain dollar limit, it can route to a second approver and then be automatically sent for payment.
 Software integration: This feature gives companies the ability to integrate Document Management software with other organizational applications. For example, if you are in your Financial or Accounting system and you’re reviewing a vendor payment dispute, you can access an image of the invoice, which resides in the Document Management system, without leaving the financial application.
Software integration: This feature gives companies the ability to integrate Document Management software with other organizational applications. For example, if you are in your Financial or Accounting system and you’re reviewing a vendor payment dispute, you can access an image of the invoice, which resides in the Document Management system, without leaving the financial application.
 Version control: Document Management systems allow you to create and track document revisions. This feature allows a document to be checked out by an employee, revised, and then checked back in. During the time the document is checked out, other employees can view it, but it can’t be modified until it is checked in. The software tracks the revisions made to a document so that employees know whether they’re viewing the most updated version.
Version control: Document Management systems allow you to create and track document revisions. This feature allows a document to be checked out by an employee, revised, and then checked back in. During the time the document is checked out, other employees can view it, but it can’t be modified until it is checked in. The software tracks the revisions made to a document so that employees know whether they’re viewing the most updated version.
 Access: Vendors provide two primary methods for accessing their application: thick client and thin client. A thick client approach requires that each computer used to access the system must have files loaded on it. The process of distributing the files to each computer can take a significant amount of time and IT effort unless an organization has the ability to programmatically distribute the files.
Access: Vendors provide two primary methods for accessing their application: thick client and thin client. A thick client approach requires that each computer used to access the system must have files loaded on it. The process of distributing the files to each computer can take a significant amount of time and IT effort unless an organization has the ability to programmatically distribute the files.
Most companies prefer thin clients. A thin client allows you to access an application through the organization’s intranet, eliminating the need to load files on each computer. In addition to thick and thin clients, more vendors are now offering cloud-based solutions. Cloud applications are hosted on the vendor’s network and allow organizations to access applications via the Internet. This eliminates the need for companies to purchase and maintain servers needed to support the vendor applications.
Some Document Management systems are designed for small businesses and departmental use, while other applications are developed for use throughout an organization. You find more on these types of applications in the section “Enterprise Content Management software,” later in this chapter.
Discovering eDiscovery software
Traditionally, medium- to large-sized organizations have outsourced eDiscovery to vendors or outside law firms that specialize in the process. However, in recent years, companies have made a push to bring eDiscovery back in-house. In the United States, the move is primarily due to the 2006 changes in the Federal Rules of Civil Procedures (FRCP).
The changes to the FRCP focused on electronically stored information (ESI) and how it is to be handled during eDiscovery. Whereas for years organizations viewed eDiscovery as a one-off or individual event based on the nature of a lawsuit, the changes to FRCP brought structure to the process. Organizations now treat eDiscovery as a routine event that has repeatable procedures. This has led to companies bringing eDiscovery back in-house and purchasing software to manage the process and control costs.
Enterprise Content Management software
Enterprise Content Management (ECM) software supports the overall ECM concept of bringing people, processes, and technologies together to capture, manage, store, preserve, and deliver information throughout a company. Enterprise Content Management software can provide organizations with extensive web, collaborative, records management, and document management functionality.
Enterprise Content Management systems use two approaches for managing unstructured content residing in multiple repositories, such as Microsoft SharePoint, e-mail servers, and Records and Document Management systems:
 In-place: Managing content in-place means that information can be managed by the ECM application while residing in other software repositories or locations. For example, a document that currently resides in Microsoft SharePoint can be declared a record in the ECM system through software integration. The document can continue to reside in SharePoint while the ECM system monitors its retention.
In-place: Managing content in-place means that information can be managed by the ECM application while residing in other software repositories or locations. For example, a document that currently resides in Microsoft SharePoint can be declared a record in the ECM system through software integration. The document can continue to reside in SharePoint while the ECM system monitors its retention.
 Centralized: In a centralized environment, content that’s declared a record or content that needs to be managed by the ECM system must be moved to the ECM software repository. After the information is transferred from the source repository, the ECM system creates a pointer to the information for use by the source application. A pointer gives employees the ability to continue to access the content from the source repository although the content is in the ECM system.
Centralized: In a centralized environment, content that’s declared a record or content that needs to be managed by the ECM system must be moved to the ECM software repository. After the information is transferred from the source repository, the ECM system creates a pointer to the information for use by the source application. A pointer gives employees the ability to continue to access the content from the source repository although the content is in the ECM system.
Most ECM applications are module based. Modules are add-ons or plug-ins that provide additional functionality. In some cases, the software comes out of the box with basic capabilities such as content storage and retrieval. The module-based approach can be beneficial for companies that want to pay for only what they currently need with the option to add additional functionality in the future.
Point-and-click configuration allows non-IT employees, knowledgeable in the system’s operation, to administer the majority of the application’s functions. Traditional ECM systems require a significant amount of IT programming to configure an application for initial and ongoing use. Point-and-click configuration systems have the necessary programming already embedded in the application, which significantly reduces the need for IT programming.
Most organizations don’t have a problem creating content; they have a problem subsequently finding information and sharing it. A key feature of ECM software is enterprise search. Internet search engines such as Bing, Google, and Yahoo! locate content from millions of websites based on your search criteria. Enterprise search works in a similar fashion. Enterprise Content Management systems have the ability to search for relevant content that resides in multiple organizational repositories as well as on external websites. Content Management systems perform enterprise searches by integrating with other organizational applications.
An additional benefit of system integration is the ability to deduplicate data. Deduplication is the process of identifying duplicate or near-duplicate content located in the same repository or multiple repositories. Deduplication is performed by using a crawler — a program that runs through the company’s unstructured repositories, identifying duplicate and potentially duplicate information. The program uses algorithms that analyze content metadata. For example, if you send an e-mail with an attachment to ten employees within the organization, the deduplication crawler will identify the duplicate copies and only store one instance of the e-mail message and attachment. This process reduces the amount of information that must be stored, backed up, and collected during eDiscovery.
Assessing Your Needs
Records, Document, and Enterprise Content Management systems can provide many benefits to companies. Numerous software vendors and options are available. The costs range from several thousand to millions of dollars. The issue is determining what software package is right for your organization.
Calculating the return on investment (ROI)
The requirements analysis can help you determine your return on investment (ROI). Due to the significant investment of money and time related to the implementation of a Records, Document, or Enterprise Content Management system, senior management may require you to calculate and document the initiative’s ROI.
Calculating the ROI for these types of software applications has historically been difficult. For example, Records Management software systems typically don’t reduce costs or improve the efficiencies of routine operational processes, but focus on improving compliance to laws and regulations. Attempting to calculate cost savings related to compliance is at best an educated guess. However, Document and Enterprise Content Management applications can help organizations realize significant monetary savings. Some areas where a company’s bottom line could be improved include the following:
 Process automation: Using imaging and workflow to automate manual processes can produce significant savings through the reduction in labor costs.
Process automation: Using imaging and workflow to automate manual processes can produce significant savings through the reduction in labor costs.
 Reduction in copying and faxing: Document Management and ECM applications improve an organization’s access to information, reducing labor and paper costs involved with printing and physically distributing documents to recipients. The ability to electronically route information can eliminate the need to fax documents, which can reduce equipment needs and costs.
Reduction in copying and faxing: Document Management and ECM applications improve an organization’s access to information, reducing labor and paper costs involved with printing and physically distributing documents to recipients. The ability to electronically route information can eliminate the need to fax documents, which can reduce equipment needs and costs.
 Improved search and retrieval: Through the use of Document Management and ECM applications, you reduce the instances of lost or misfiled information, reducing the labor costs involved with searching for content.
Improved search and retrieval: Through the use of Document Management and ECM applications, you reduce the instances of lost or misfiled information, reducing the labor costs involved with searching for content.
A number of so-called “soft-dollar” benefits are derived from these types of applications, but they are more difficult to quantify. They may include enhanced decision-making, customer service, and compliance. Even if you are unable to determine their value, they should be mentioned in the ROI document.
Identifying your “pain points”
In most cases, when an organization reaches a position where it is considering the purchase of software to manage its records and information, it’s because the company is attempting to address pain points. Pain points in this case are specific records and information management issues. Common issues organizations face include
 Too much paper
Too much paper
 Lost documents
Lost documents
 Compliance concerns
Compliance concerns
 Multiplying document versions
Multiplying document versions
 Inefficient processes
Inefficient processes
Conducting a requirements analysis
The requirements analysis lays the foundation for documenting your records and information needs. The analysis is comprised of two parts — operational and technical. The operational analysis addresses specific business issues such as compliance and processes, while the technical analysis addresses attributes that software must possess to be supported in the company’s IT infrastructure.
1. Justification: This step involves documenting the business case for software. During this phase, you should calculate a preliminary return on investment, or ROI. (Keep in mind that the ROI can be modified as additional information is gathered in subsequent steps.)
2. Committee: To ensure that the requirements you document are accurate and comprehensive, it’s recommended that a committee or group representing relevant stakeholders be established.
3. Requirements gathering: This step involves meeting with different operational areas to determine their current and anticipated pain points as well as the nature of their content and how it’s used.
4. Business-use cases: After operational requirements have been gathered, you should develop business-use cases in conjunction with the committee. Business-use cases are operational scenarios that are used to test vendor applications. In addition, the committee should develop a testing document that is to be used to indicate the results of testing each vendor’s system against the business-use cases. Note: More information is provided on business-use cases later in this chapter.
5. Initial research: After the business-use cases and testing document have been developed, you should begin conducting vendor research to develop a list of prospective vendors. You can research vendors and their applications by using the Internet, colleague recommendations, and research reports from firms such as Forrester and Gartner. It’s recommended that you limit your list to three or four prospective vendors.
6. RFI/RFP: After you have compiled a list of prospective vendors, you should submit a request for information (RFI) or request for proposal (RFP) to each vendor. The RFI instructs a vendor to provide information about his company and applications. The RFP provides the vendor with your requirements and asks the vendor to submit a proposal indicating specifically how his applications will meet your requirements and resolve your pain points. Note: You should enter into a nondisclosure agreement (NDA) with each vendor whom you supply with your requirements and information. The NDA helps to ensure that the vendor doesn’t inappropriately divulge any of your organization’s confidential information during or after the evaluation process.
7. Vendor review and selection: Upon return of the RFI or RFP from the vendor, it’s time to begin the evaluation process, with the objective of selecting a vendor that best meets your organization’s records and information management needs. The process usually involves narrowing the list of prospective vendors to one or two. The evaluation process may include a request to the vendor to configure a test system within your organization. This approach is referred to as a proof of concept (POC). It allows the committee and end users to test the system within your own IT environment. In addition, a POC can be established for a cloud-based approach.
Evaluating Vendors
Approaching the vendor evaluation with the appropriate tools and knowledge of business content and processes can help ensure that the correct application is selected. To provide you with what you need to know to make the evaluation process a success, I provide you with examples of business-use cases and a comprehensive test plan in the following sections.
Determining your evaluation approach
 Demos: This approach involves reviewing and evaluating an application through demonstrations conducted by the vendor. This isn’t an optimal approach because it doesn’t allow you to evaluate the application at your own pace. It also doesn’t let you use your own data or determine how the system will perform within your IT infrastructure.
Demos: This approach involves reviewing and evaluating an application through demonstrations conducted by the vendor. This isn’t an optimal approach because it doesn’t allow you to evaluate the application at your own pace. It also doesn’t let you use your own data or determine how the system will perform within your IT infrastructure.
 Sandbox: The term sandbox refers to having the vendor set up its application within your facility, running on your network. This approach is preferred. It provides all employees involved in the evaluation process with access to the application. A sandbox allows you to determine how the system will perform on your network and enables you to import your own data for testing. If your organization is interested in a cloud-based solution, you can have the vendor provide the evaluation team with access to the application. This approach gives the team the ability to evaluate the application’s functionality, as well as to determine the performance of the vendor’s cloud system.
Sandbox: The term sandbox refers to having the vendor set up its application within your facility, running on your network. This approach is preferred. It provides all employees involved in the evaluation process with access to the application. A sandbox allows you to determine how the system will perform on your network and enables you to import your own data for testing. If your organization is interested in a cloud-based solution, you can have the vendor provide the evaluation team with access to the application. This approach gives the team the ability to evaluate the application’s functionality, as well as to determine the performance of the vendor’s cloud system.
Using business-use cases
Business-use cases are essential for evaluating vendor applications. They provide the testing road map that you need to assess system functionalities and capabilities (see Figure 10-1). Business-use cases are developed by determining current and anticipated organizational pain points and requirements. The best business-use cases cover a comprehensive range of items and issues.
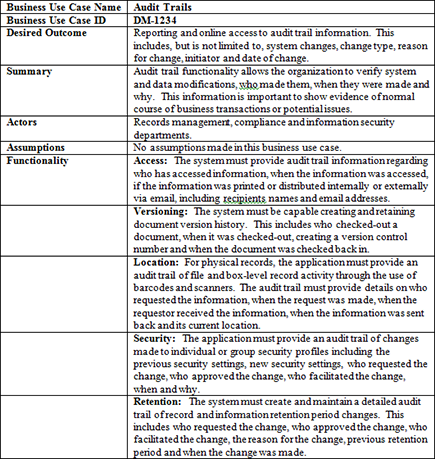
Detailing the results
The business-use cases should be used in conjunction with a detailed test plan. As illustrated in Figure 10-2, the test plan is used to document the results of your business-use case testing. The results of the test plan should be used to communicate your testing results to the vendor. One of the primary objectives of the test plan is to expose functionality gaps in the vendor’s application.
Figure 10-2: Test plan.

Functionality gaps may involve the complete inability of the application to meet a specific requirement, or it may be that the application partially meets a specific requirement. In either situation, the evaluation team should communicate the results to the vendor to allow the vendor to address what steps can be taken to resolve the gaps.
It’s not all about functionality
 Vendor/reseller: Prior to investing in a Records, Document, or Enterprise Content Management system, you should get to know the vendor. This includes understanding its stability. Over the past decade, numerous software vendor acquisitions have occurred. Although it’s difficult to predict whether a vendor will be acquired, you can use business-reporting agencies such as Dun & Bradstreet to obtain information regarding a vendor’s financial stability and strength.
Vendor/reseller: Prior to investing in a Records, Document, or Enterprise Content Management system, you should get to know the vendor. This includes understanding its stability. Over the past decade, numerous software vendor acquisitions have occurred. Although it’s difficult to predict whether a vendor will be acquired, you can use business-reporting agencies such as Dun & Bradstreet to obtain information regarding a vendor’s financial stability and strength.
It’s important to know how long the vendor has been in operation and how many installations of its application are in use. You should obtain references for organizations currently using the application. When contacting references, ensure that you inquire about the vendor’s performance as well as the application’s performance.
In many cases, vendors use resellers to market, sell, and support their products. You should take the same approach to evaluating a reseller as you would if you were evaluating the vendor.
 Support: In addition to evaluating the functionality of an application, you should assess the vendor’s ability to support the system after implementation. This includes the number, type, and experience of employees the vendor uses to support its application. You should obtain an understanding of its service response times and the support staff’s ability to assist you with your additional programming needs. When you decide upon an application, it’s recommended that you include Service Level Agreement (SLA) language in the contract that clearly states your expected response and resolution times to issues.
Support: In addition to evaluating the functionality of an application, you should assess the vendor’s ability to support the system after implementation. This includes the number, type, and experience of employees the vendor uses to support its application. You should obtain an understanding of its service response times and the support staff’s ability to assist you with your additional programming needs. When you decide upon an application, it’s recommended that you include Service Level Agreement (SLA) language in the contract that clearly states your expected response and resolution times to issues.
 Cost: In many cases, the cost of the software is just the tip of the proverbial iceberg. Depending on the size of your organization, licensing costs can significantly exceed the cost of the application. Therefore, it’s essential to understand the vendor’s licensing requirements and cost structure. Most software vendors offer two primary license types — named and concurrent. Named licenses are assigned to a specific user such as a system administrator, while concurrent licenses aren’t assigned to specific employees but to any user with access to the system. For example, if you purchase 20 concurrent licenses, this allows 20 employees who are not specifically assigned to a license to access and use the system. In addition, some vendors require that you purchase additional license types for functionality such as workflow and software integration.
Cost: In many cases, the cost of the software is just the tip of the proverbial iceberg. Depending on the size of your organization, licensing costs can significantly exceed the cost of the application. Therefore, it’s essential to understand the vendor’s licensing requirements and cost structure. Most software vendors offer two primary license types — named and concurrent. Named licenses are assigned to a specific user such as a system administrator, while concurrent licenses aren’t assigned to specific employees but to any user with access to the system. For example, if you purchase 20 concurrent licenses, this allows 20 employees who are not specifically assigned to a license to access and use the system. In addition, some vendors require that you purchase additional license types for functionality such as workflow and software integration.
Maintenance is an additional cost you will incur with the acquisition of a Records, Document, or Enterprise Content Management system. This is an annual cost charged by the vendor or reseller. In most cases, it ranges from 15 to 20 percent of your total software and license costs. For example, if you purchase $150,000 in software and licenses, you can expect to pay approximately $27,000 in annual maintenance fees. It’s recommended that you negotiate the annual maintenance percentage. It is common for vendors to offer discounts on their software. If this is the case, ask for your maintenance fees to be based on the discounted software price.
Professional services refers to the services offered by the vendor or reseller. This includes services for customizing its software, consulting, programming, and training. Professional services costs are high. They typically range from $1,000 to $2,000 per day. Therefore, it’s important to understand the vendor or reseller’s cost structure. You should negotiate and include the agreed-upon rate in your contract.
 Scalability: As your organization grows, it’s important to select an application that can keep pace with your records and information management needs. Scalability refers to the software’s ability to handle an increased workload without diminished performance. Over time, it’s common for most organizations to increase the number of users of an application and add significant amounts of data that need to be managed. You should ensure that the application can appropriately handle the increase. Load testing or stress testing can be used to rate an application’s performance under increased transactional and volume conditions. Some companies provide software specifically designed to load-test applications. It’s recommended that you consult with your IT department to determine how to appropriately load-test an application.
Scalability: As your organization grows, it’s important to select an application that can keep pace with your records and information management needs. Scalability refers to the software’s ability to handle an increased workload without diminished performance. Over time, it’s common for most organizations to increase the number of users of an application and add significant amounts of data that need to be managed. You should ensure that the application can appropriately handle the increase. Load testing or stress testing can be used to rate an application’s performance under increased transactional and volume conditions. Some companies provide software specifically designed to load-test applications. It’s recommended that you consult with your IT department to determine how to appropriately load-test an application.
Comparing the results
Figure 10-3: Vendor application comparison grid.
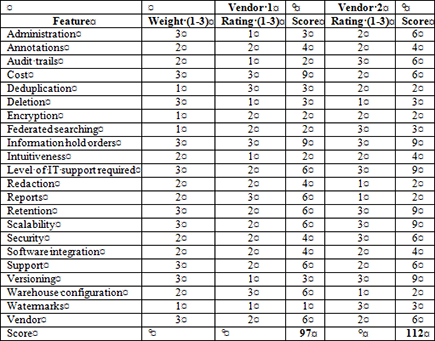
Guiding You through Implementation
Researching, planning, and managing expectations are the keys to a successful implementation. The following sections address each of these topics and provide you with tips for ensuring that your implementation succeeds.
Why implementations fail
 Lagging adoption: One of the most important factors that determines the success or failure of an implementation is user adoption. If the application doesn’t provide a convenient end-user experience, employees won’t use the system. Convenience is a relative term. Any new system will require employees to perform some aspects of their job differently; employees understand this. However, if employees perceive that the changes outweigh the benefits, they will be reluctant to adopt the system.
Lagging adoption: One of the most important factors that determines the success or failure of an implementation is user adoption. If the application doesn’t provide a convenient end-user experience, employees won’t use the system. Convenience is a relative term. Any new system will require employees to perform some aspects of their job differently; employees understand this. However, if employees perceive that the changes outweigh the benefits, they will be reluctant to adopt the system.
 Big bang: An additional factor at the root of implementation failure is the big bang. The big bang refers to a large-scale initial implementation. Implementing an application across multiple departments at one time can create significant operational problems if an unforeseen problem with the application occurs.
Big bang: An additional factor at the root of implementation failure is the big bang. The big bang refers to a large-scale initial implementation. Implementing an application across multiple departments at one time can create significant operational problems if an unforeseen problem with the application occurs.
 Overcustomization: Overcustomization of an application can significantly delay implementation as well as future upgrades of the system.
Overcustomization: Overcustomization of an application can significantly delay implementation as well as future upgrades of the system.
 Faulty evaluation and testing: If the wrong business scenarios are evaluated and tested, this will result in the application not meeting the company’s needs.
Faulty evaluation and testing: If the wrong business scenarios are evaluated and tested, this will result in the application not meeting the company’s needs.
 Lack of strategic thinking: It’s essential to ensure that the application be aligned with and be able to support the organization’s strategies. For Records and Departmental Document Management system implementations, most organizations have a relatively clear understanding of how the systems will be used to support the business. However, most companies don’t have a comprehensive vision or strategy for enterprise content management or how ECM software can support their objectives.
Lack of strategic thinking: It’s essential to ensure that the application be aligned with and be able to support the organization’s strategies. For Records and Departmental Document Management system implementations, most organizations have a relatively clear understanding of how the systems will be used to support the business. However, most companies don’t have a comprehensive vision or strategy for enterprise content management or how ECM software can support their objectives.
 Budget shortfalls: In this context, budget includes money and labor resources. Implementations that run over budget or require additional employee time and effort may cause senior management to rethink whether to proceed with the project.
Budget shortfalls: In this context, budget includes money and labor resources. Implementations that run over budget or require additional employee time and effort may cause senior management to rethink whether to proceed with the project.
How to ensure that your implementation is a success!
The following items are proven steps and guidelines that you should evaluate and incorporate to ensure that your implementation is a success:
 Plan well. Implementing applications of this type requires extensive planning and involves many different employees. It’s essential to appoint a project manager and establish a project plan. This approach helps to ensure that the proper resources are allocated to the project and that the initiative stays on track.
Plan well. Implementing applications of this type requires extensive planning and involves many different employees. It’s essential to appoint a project manager and establish a project plan. This approach helps to ensure that the proper resources are allocated to the project and that the initiative stays on track.
 Focus on adoption. During the evaluation of an application, it’s critical to consider the end-user experience. Employees should be involved in the evaluation and testing process to receive their feedback on how the system meets their needs and to incorporate modification or configuration changes to the software. However, if possible, you should avoid or minimize actual system customization.
Focus on adoption. During the evaluation of an application, it’s critical to consider the end-user experience. Employees should be involved in the evaluation and testing process to receive their feedback on how the system meets their needs and to incorporate modification or configuration changes to the software. However, if possible, you should avoid or minimize actual system customization.
 Try a pilot program first. A pilot involves implementing the system in one or two departments and evaluating its performance over a period of time. This approach allows you to quickly respond to any issues that occur and take immediate corrective action if needed.
Try a pilot program first. A pilot involves implementing the system in one or two departments and evaluating its performance over a period of time. This approach allows you to quickly respond to any issues that occur and take immediate corrective action if needed.
 Avoid customization. You should avoid or minimize customization to the software. This approach can help expedite the implementation and make future software upgrades easier.
Avoid customization. You should avoid or minimize customization to the software. This approach can help expedite the implementation and make future software upgrades easier.
 Do the right evaluation and testing. It’s important that appropriate business-use cases be used to evaluate and test an application. The evaluation team, as well as end users, should develop them to ensure that they are comprehensive and that they accurately reflect the proper business scenarios. In addition, end users should be involved in the evaluation and testing process. This provides two benefits: Employees understand their business functions, and they want a system that can meet their needs. In addition, this can improve the end-user adoption rate.
Do the right evaluation and testing. It’s important that appropriate business-use cases be used to evaluate and test an application. The evaluation team, as well as end users, should develop them to ensure that they are comprehensive and that they accurately reflect the proper business scenarios. In addition, end users should be involved in the evaluation and testing process. This provides two benefits: Employees understand their business functions, and they want a system that can meet their needs. In addition, this can improve the end-user adoption rate.
 Strategize. As part of the project process, the evaluation team should partner with senior management and other key stakeholders to understand and document the organization’s near- and long-term initiatives and strategies to ensure how they impact the management of records and information. This can enable the evaluation team to select an application that best supports the company’s efforts.
Strategize. As part of the project process, the evaluation team should partner with senior management and other key stakeholders to understand and document the organization’s near- and long-term initiatives and strategies to ensure how they impact the management of records and information. This can enable the evaluation team to select an application that best supports the company’s efforts.
 Budget correctly. Properly evaluating and testing an application’s functionality before implementation increase your ability to accurately forecast the implementation time frame and employee involvement. The evaluation team should work closely with senior management on the project and frequently communicate status updates.
Budget correctly. Properly evaluating and testing an application’s functionality before implementation increase your ability to accurately forecast the implementation time frame and employee involvement. The evaluation team should work closely with senior management on the project and frequently communicate status updates.
 Provide awareness and training. During the evaluation and testing phases of the project, the evaluation team should begin the process of bringing awareness of the initiative to employees who will ultimately be using the application. This helps to gradually prepare employees for the upcoming change. As the implementation phase grows closer, the evaluation team should develop a training curriculum and schedule employee training sessions.
Provide awareness and training. During the evaluation and testing phases of the project, the evaluation team should begin the process of bringing awareness of the initiative to employees who will ultimately be using the application. This helps to gradually prepare employees for the upcoming change. As the implementation phase grows closer, the evaluation team should develop a training curriculum and schedule employee training sessions.


 Without the proper planning, you run the risk of selecting an application that doesn’t meet your records and information management needs or long-term objectives. The following sections focus on how to identify and document your current and forecasted needs and requirements in an effort to ultimately select a software system that will make your organization more compliant and efficient.
Without the proper planning, you run the risk of selecting an application that doesn’t meet your records and information management needs or long-term objectives. The following sections focus on how to identify and document your current and forecasted needs and requirements in an effort to ultimately select a software system that will make your organization more compliant and efficient.