Chapter 1

Table 1-2 NSX Use Cases

Table 1-2 NSX Use Cases
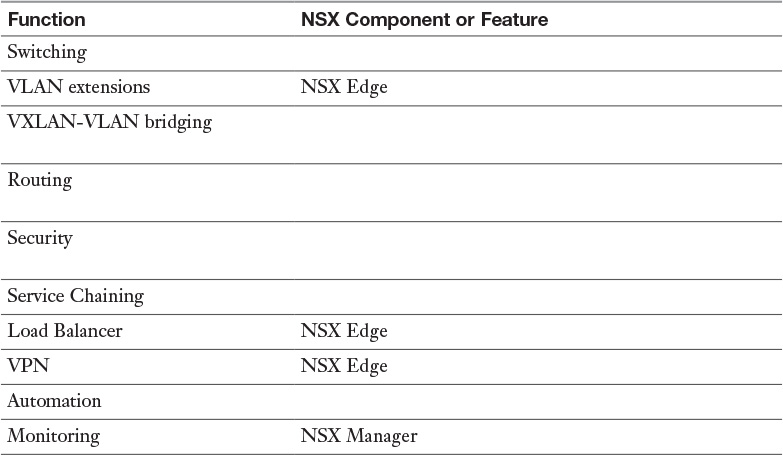
Table 1-3 NSX Network and Security Functions
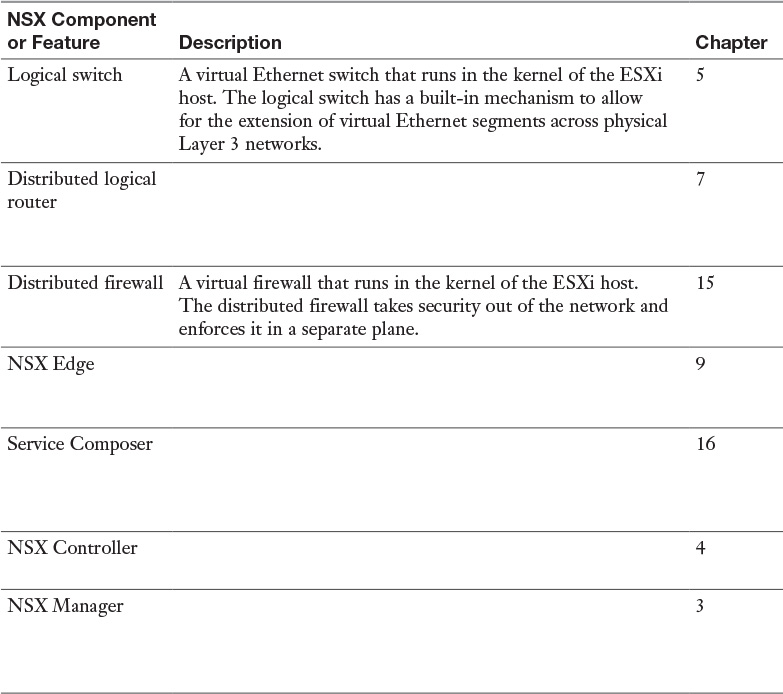
Table 1-4 NSX Components and Features

Table 2-2 LACP Modes
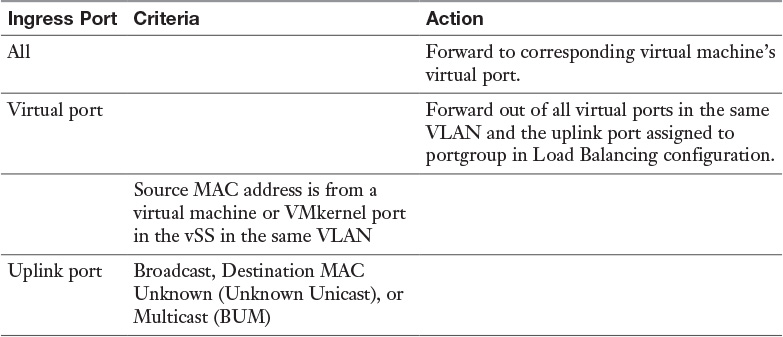
Table 2-3 vSphere Standard Switch Forwarding Decision Rules

Table 2-4 vSphere Standard Switch Portgroup VLAN Settings
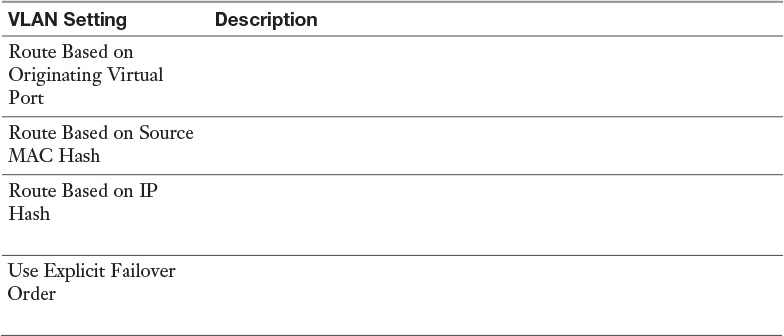
Table 2-5 vSphere Standard Switch Portgroup VLAN Settings

Table 2-6 vSphere Distributed Switch Portgroup VLAN Settings
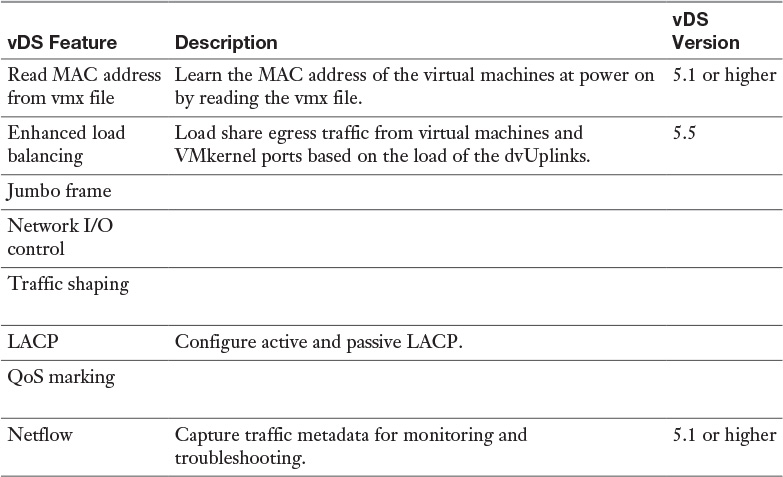
Table 2-7 vSphere Distributed Switch Features Used by NSX
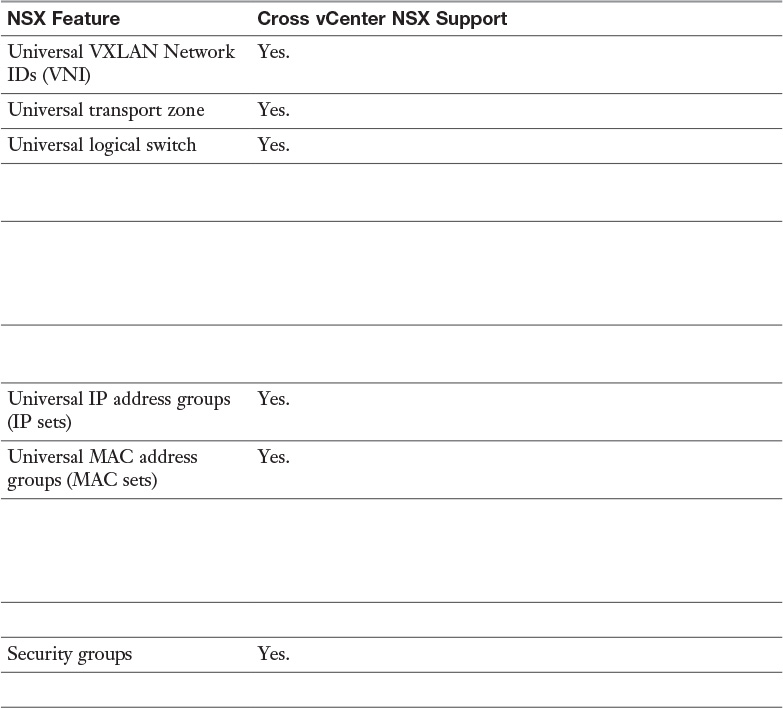
Table 3-3 Cross vCenter NSX Features

Table 4-2 vSphere Versions Supported by the NSX Modules
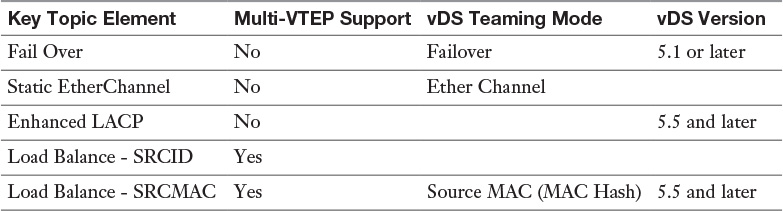
Table 4-3 VMKNic Teaming Policies
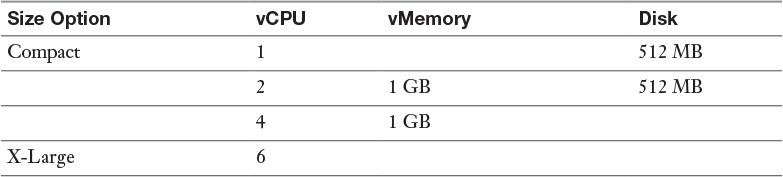
Table 9-2 NSX Edge Virtual Machine Sizes
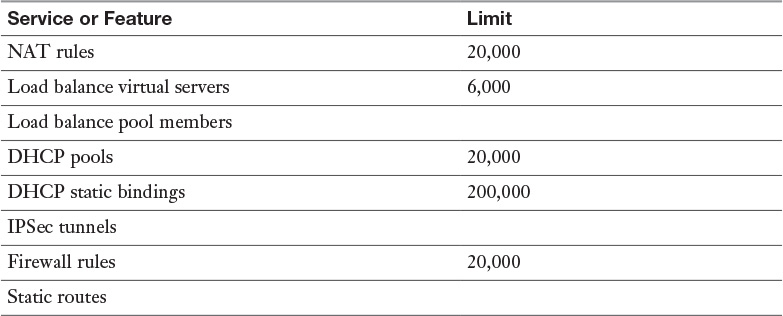
Table 9-3 NSX Edge Service and Feature Limits per NSX Domain
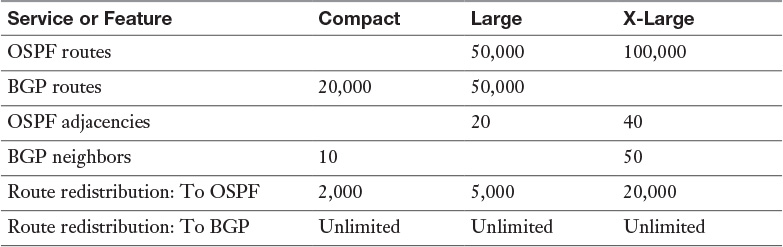
Table 9-4 NSX Edge Service and Feature Limits per Edge Size
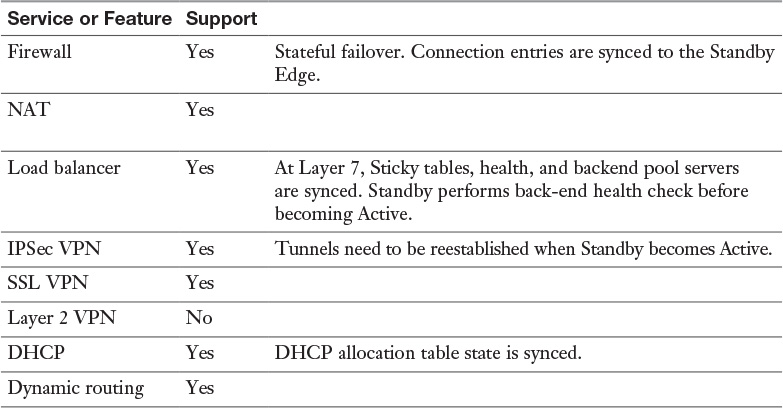
Table 9-5 Impact per Service of Standby Edge Becoming Active Edge

Table 10-2 Layer 2 VPN Supported Encryption Algorithms

Table 10-4 Layer 2 Extension Support
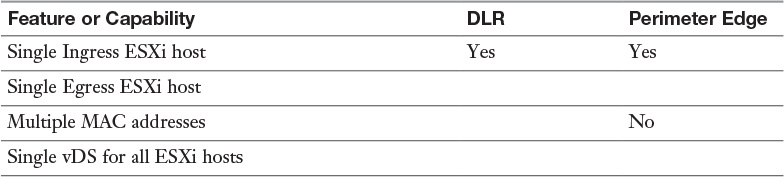
Table 11-2 Features and Capabilities
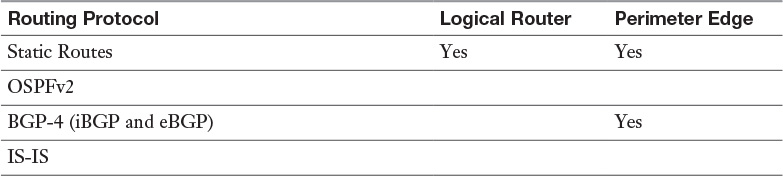
Table 12-2 Routing Protocols
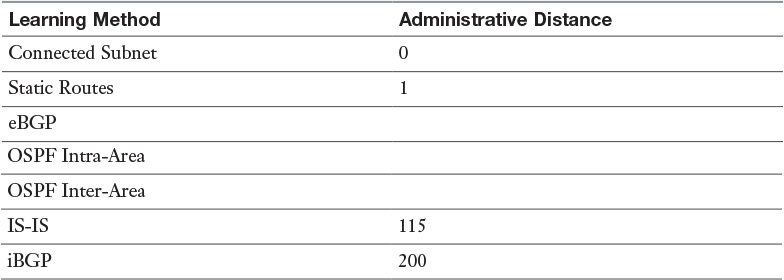
Table 12-3 Administrative Distance

Table 12-4 OSPF Areas

Table 12-5 OSPF Neighbor Parameters
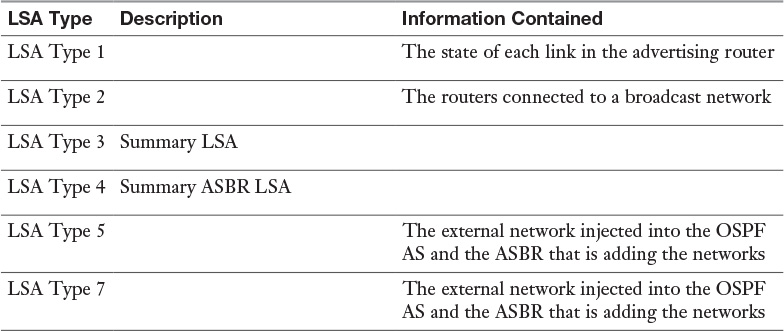
Table 12-6 OSPF LSA Types

Table 12-11 IS-IS Router Types

Table 13-2 IPsec Provided Security Features
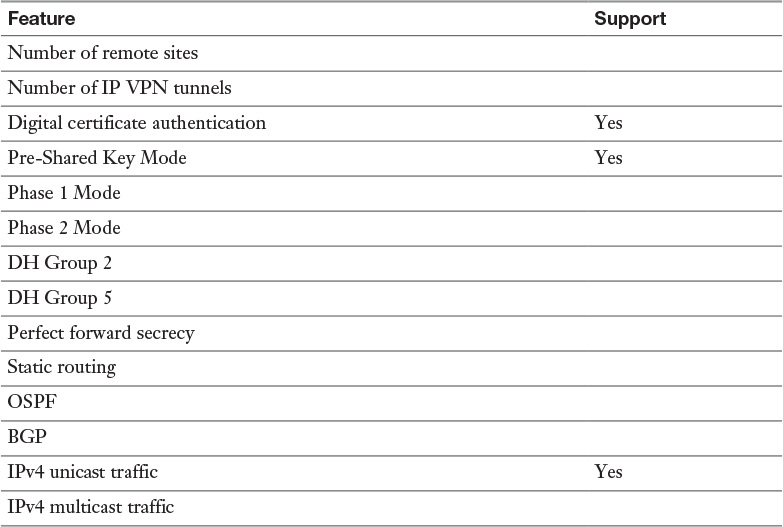
Table 13-3 IPsec VPN Support

Table 13-5 SSL VPN-Plus Components

Table 13-10 Authentication Methods Default Ports

Table 14-2 NSX Edge Load Balancer Support
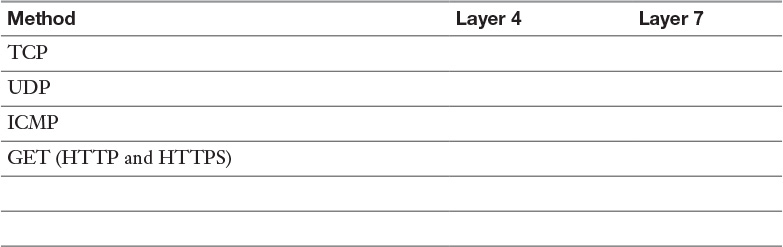
Table 14-3 Health Check Methods

Table 14-4 Persistence States

Table 14-5 Edge Load Balancer Throttle

Table 15-2 Design Compromises: Network Security
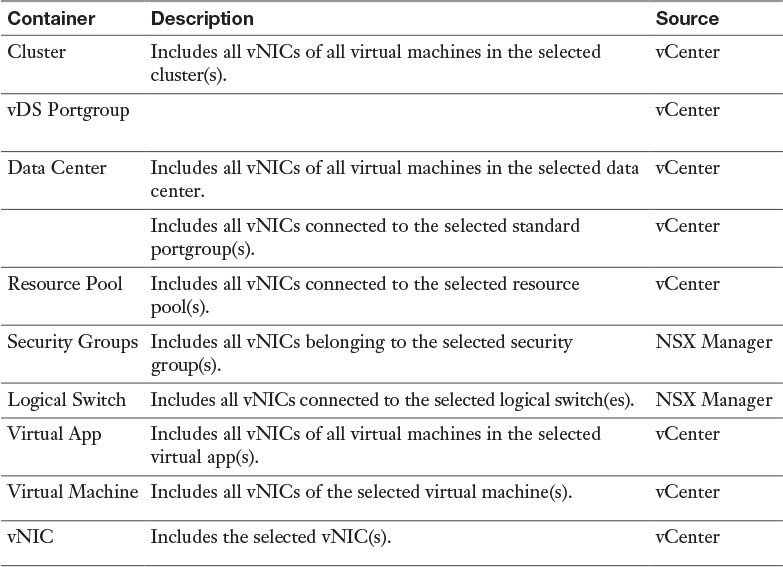

Table 15-5 Local DFW Rule Source and Destination Containers
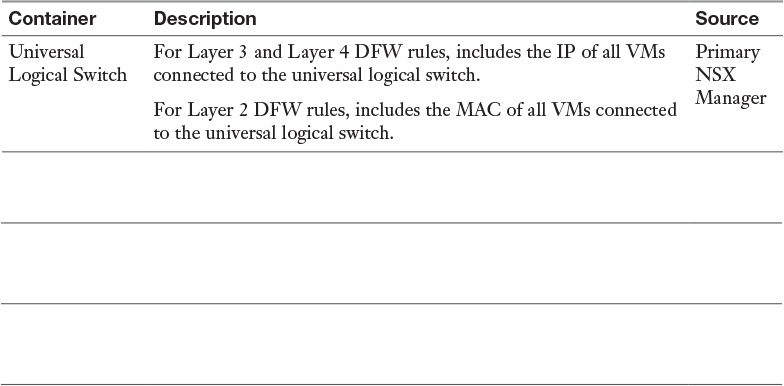
Table 15-6 Local DFW Rule Source and Destination Containers
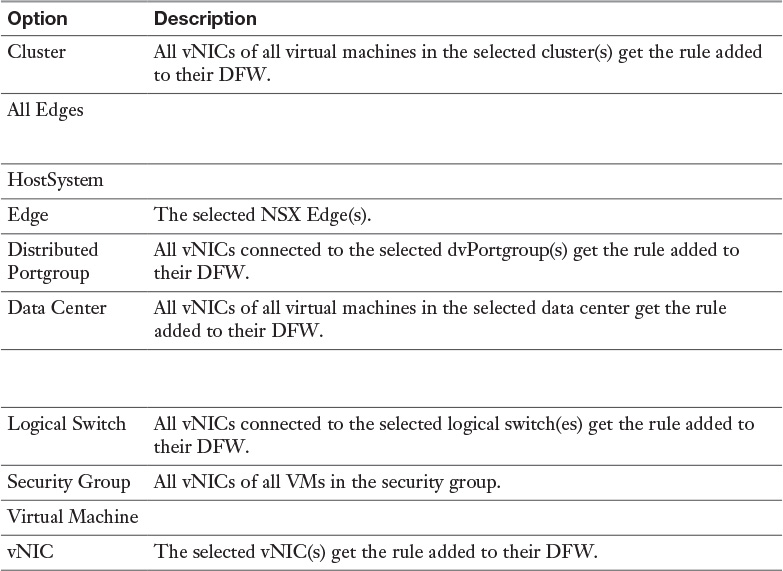
Table 15-7 Firewall Rule Applied To Options
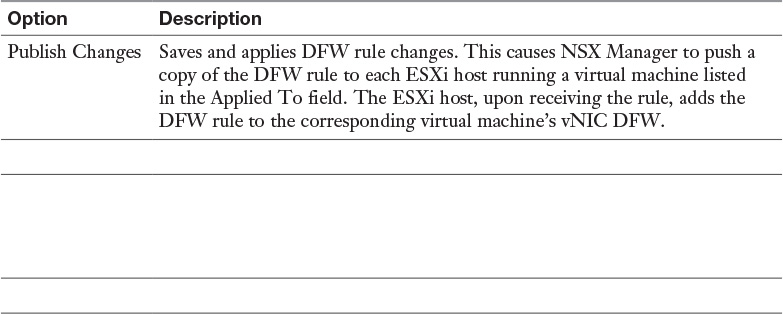
Table 15-9 Rule Change Options

Table 15-10 vsipioctl Command Options
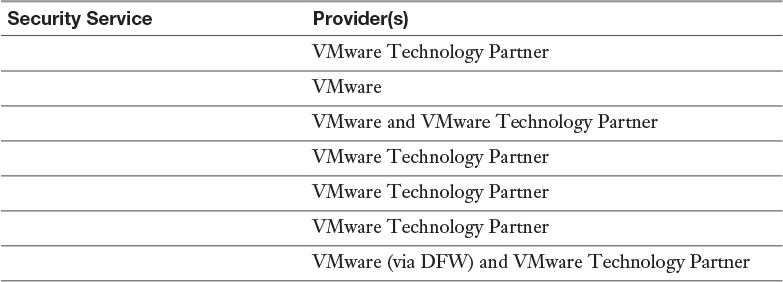
Table 16-2 Security Services
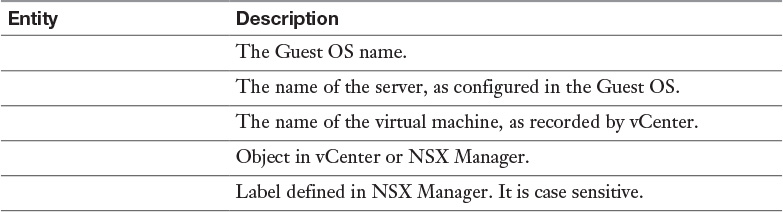
Table 16-3 Dynamic Selection Options

Table 16-4 Matching Criteria Options

Table 16-5 Security Group Object Selection Options
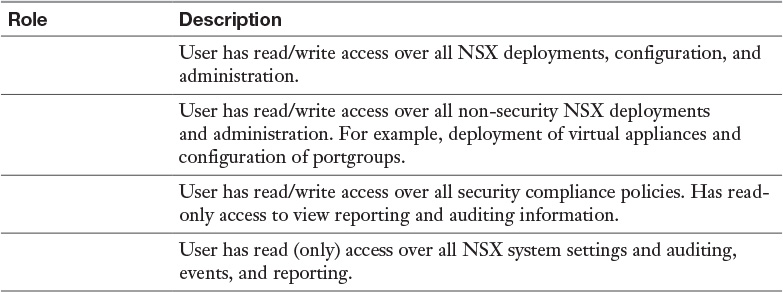
Table 17-3 NSX Roles

Table 18-2 HTTP Methods Supported by NSX APIs
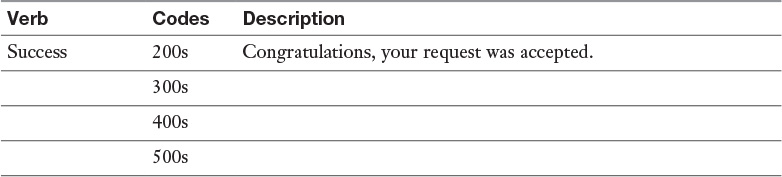
Table 18-3 HTTP Responses