1 Introduction
Internet of Things (IoT), which is defined as the “worldwide network of interconnected objects” [1], extends connectivity from human-to-machine to machine-to-machine communication. IoT offers large scale of integration of heterogeneous networks and devices, which apart from the obvious opportunities, introduces great security and privacy challenges. These challenges are not new as they have been well-studied in the relevant literature in different IoT domains (such as e-Health, Smart City, Smart Grid) [2–6]. Among the various security challenges in IoT, access control is a crucial and open challenge [7].
Scalability stems from the exponential growth in IoT which also results to an increased network connectivity requirement. According to Gartner, the number of Internet-connected devices will reach 20–50 billion devices by 2020 [8]. As a result, this exacerbates the security challenges in IoT by requiring more effort and resources required by the security controls (such as the access control mechanism) to address them [9].
Heterogeneity and interoperability in IoT derive from the different technologies and networks (such as RFID, WSN, GSM) that exist in IoT. Thus, enabling seamless and secure integration of these different platforms is a challenge, as the degree of complexity increases dramatically when different technologies are merged to form a complex network. Similarly, interoperability brings new challenges to the field of data access control [10]. For example, in Vehicle-To-Vehicle (V2V) communication moving from one geographical domain (e.g. UK) to another (e.g. France) can cause data access problem, due to the interoperability issues between inter-domain public key infrastructures [11].
Dynamism in IoT stems from the fact that the interconnected things need to interact with each other in a real-time manner. Therefore, the need for an appropriate response to rapid changes in the physical world which are caused by those interactions poses new technological challenges not only for access control but also for any context-aware services [12].
Resource sharing in different IoT domains (e.g. smart grids, smart city) is inevitable [13, 14]. For example, resource sharing in grid environments through Virtual Organizations (VOs) creates added value by improving performance with less investment. Besides advantages it poses permission misuse and insider threats against VOs [13]. The same threats can be exposed to smart city where traffic information is shared or in V2V communication where two or more vehicles share their resources (e.g. information about their locations) [14].
Data communication loss due to the network or device failure in IoT enabling technologies like Wireless Sensor Network (WSN), and Radio-Frequency Identification (RFID) leads to incomplete and imprecise data. Incompleteness and imprecision inherent in the above-mentioned sources can hinder precise access control decisions [15].
The focus of this work is to introduce “Indeterminacy”, a new and neglected challenge in IoT that affects access control. Indeterminacy in IoT comes to play where an access control decision needs to be made based on incomplete or imprecise information. In other words, indeterminacy is introduced in the access control mechanism when the required information for access decision is not sufficient or not precise enough to be used in order to make a correct access decision.
We regard that a subset of the abovementioned inherent IoT characteristics exaggerate the indeterminacy in access control. In specific, dynamism may result in indeterminacy because real-time tracking of the rapid changes (joining, disjoining, displacement of entities) is not easily achievable in a scalable environment like IoT. Therefore, the lack of information caused by the inability of tracking those changes results in indeterminacy. Scalability can increase dynamism in a way that having complete information to make access decision is imposible. Network and Service dependency in a heterogeneous environment like IoT can cause delay and latency in network delivery. If a real-time access decision depends on the information, which is delivered with delay or suffers from latency, it will suffer from indeterminacy in access control. Finally, regarding the inherent heterogeneity of IoT introduces different soruces of data communication loss. For example, data may be lost in RFID due to the following reasons [16]: (1) Missing reading caused by tag collision, metal/liquid effect. (2) Data inconsistency caused by reading data from various readers simultaneously. (3) Ghost data caused by frequency reflection in the reading area. Incompleteness and imprecision inherent in the above-mentioned sources are conceived as the main causes of indeterminacy [15].
In this context, this work contributes by: studying the adaptability of traditional and emerging access control models in IoT, defining indeterminacy, uncertainty and ambiguity in access control for IoT, analyzing resilient access control paradigms and proposing a conceptual framework to address indeterminacy in access control in the context of IoT.
The rest of the chapter is organized as follows: Sect. 2, discusses the preliminaries in the field of access control. Section 3 analyses the concept of uncertainty and ambiguity. This section also defines these concepts in the context of access control and discusses different paradigms in the field of resilient access control. Finally, the conceptual framework is proposed at the end of this chapter to cover both uncertainty and ambiguity in the access control. The chapter concludes in Sect. 4.
2 Background
2.1 An Introduction to Access Control
- 1.
Authentication, which is defined as a verification process to check whether the credentials of an entity is valid. In some texts, identification was introduced as the process of identity verification, which should be completed before the authentication process.
- 2.
Authorisation, which is defined as a process of granting the access right to an entity to use a resource.
- 3.
Auditing, which is defined as the process of reviewing the access control system records and activities to detect any security breach. Auditing is necessary to ensure that the defined access policies are compliant with the operational security of the system.
- 1.
Delegation, which is the act of granting an access right (full or part of) from one subject to another subject in the system.
- 2.
Revocation, namely the act of removing from a subject the access right to a resource.
- 3.
Granularity, i.e., the level of details that can be used for making access decision. If the required details are explicit and limited, then the type of granularity is referred as coarse-grained. On the contrary, fine-grained access control needs more details such as subject or object attributes to make a decision about the access and govern it.
- 4.
Flexibility is the ability of the access control system to adapt itself to a different situation and to govern both planned and spontaneous interactions between subjects and objects.
- 5.
Scalability, i.e., the ability of an access control system to be extensible in terms of the number of subjects, objects and access right policies. Another dimension of scalability is the ability of an access control system to extend its structure and scope of operation.
- 6.
Lightweight, which reflects the computational complexity or volume of network traffic that an access control mechanism imposes to the system.
- 7.
Heterogeneity, which is defined as the ability of the access control system to be used in different domains, platforms, networks and technologies.
- 8.
Context-aware, namely the ability of the access control system to use contextual attributes of the environment such as time and location to make an access decision.
In the field of IoT, any access control system must be scalable, heterogeneous, lightweight and context-aware due to the characteristics of IoT itself.
2.2 Access Control Models
Since Lampson’s access matrix was introduced in the late 1960s, a number of access control models have been proposed. This subsection briefly describes traditional access control models before moving to emerging access control models. In a number of texts, DAC, MAC, Biba, BLP, Clark-Wilson, Chinese Wall and RBAC were classified as traditional access control models while ABAC is titled as “relatively recent” access control model [21]. This work refers to ABAC and other models that were proposed after ABAC as emerging access control models. It also discusses their adaptability in a scalable, heterogeneous and dynamic environment like IoT.
The traditional access control models include:
Discretionary Access Control (DAC)
In DAC the access policy for any object is defined based on the discretion of the object’s owner [22]. The earliest implementation of DAC was the Access Control List (ACL), proposed in 1971. Modern operating systems like Windows utilize this ACL-based approach. Contrary to Mandatory Access Control, in DAC a subject with certain access permission is able to delegate and revoke its permission to another subject [23].
Mandatory Access Control (MAC)
In MAC, which was proposed in 1973, the access policy is enforced by the system and the access to a resource is granted if the security clearance of the subject is greater than the security level of the object. The subject who has the clearance to access the object cannot delegate her access to another subject or make any change in the access policy. In this model, multi-level security (MLS) structure is defined by the system [24]. Although traditional MAC protects the confidentiality of information, it cannot protect the integrity of information since subjects with lower clearance can modify the objects that are accessible by the subjects with higher clearance [24]. To address this problem, Bell-La Padula model embodies two major principles: (a) no-read-up, meaning that resources can be read only by subjects with clearance greater than or equal to the resource’s classification, and (b) no-write-down meaning that resources can be written only by subjects with clearance less than or equal to resource’s classification. In contrary to DAC, another major drawback of MAC is that a subject cannot delegate or revoke its access rights to another subject [25]. Security-Enhanced Linux (SELinux) and Mandatory Integrity Control are two examples of using MAC.
Bel La Padula (BLP)
BLP model was proposed in 1973 to focus on the confidentiality of data. For this reason, BLP enforces two main security policies known as “No Read Up” and “No Write Down”. “No Read Up” ensures that read access is granted if the security level of the subject must dominate the security classification of the object. The “No Write Down” is defined for both “append” and “write” operations. In the former, “No Write Down” ensures that the security level of objects must dominate the security level of the subject. For the latter, it ensures that security levels of subject and objects are equal. BLP supports both MAC, by determining the access rights from the security levels associated with subjects and objects, and DAC, by governing access rights based on the access matrix.
Biba model [26] was proposed in 1977 to ensure the integrity of data. For this reason, Biba rules control the transfer of data between integrity levels. To meet this goal, subjects cannot read objects of lower integrity level, which is known as “No Read Down” policy. Also, subjects in lower integrity level cannot get write access to the objects at higher integrity level, which is known as the “No Write-Up” policy.
Clark-Wilson model was proposed [27] in 1989 to protect the integrity and uses programs as a layer between users and data items. Users are authorized to execute a specific set of programs and data items can be accessed only via those programs. The focus of this model is on the security requirements of commercial applications.
Chinese Wall access control model was proposed in 1989 to avoid conflicts of interest when dealing with different subjects [28]. Conflicts arise when some companies are in competition and want to access or have accessed in the past the same objects. The model can address the “conflict of interest” for both MAC and DAC. The Chinese-Wall policy combines commercial discretion with legally enforceable mandatory controls.
Role Based Access Control (RBAC)
Ferraiolo et al. [29] proposed RBAC in 1992 to address the management complexity of DAC and MAC [30]. In RBAC access is regulated based on the roles of the individuals within an organization. In other words, individuals performing specific roles can request access to specific resources that are necessary for this role. RBAC supports scalability and granularity and enforces the principle of least privilege [31]. According to the principle of least privilege, a subject should operate using the minimum set of privileges necessary to complete the task. Enforcing this principle mitigates the damage of unintended errors. Furthermore, RBAC supports separation of duties by ensuring that at least two different individuals are responsible for carrying out the various steps of any critical task [32].
The emerging access control models include:
Attribute-Based Access Control (ABAC)
In the ABAC model when a subject request access to an object, the decision will be made based on the subject’s attributes, the object’s attributes and the environment’s attributes [33]. ABAC is widely used in the current Internet because it supports fine-grained access policies [34].
Capability Based Access Control (CapBAC)
CapBAC was introduced in [35] and governs access requests based on tokens. The subject must have a valid token to request access to a resource and the token must be tamper proof. In this chapter, we classify those capability-based access control as “emerging access control” that benefit from using lightweight encryption algorithms like Elliptical Curve Cryptography (ECC) to create an attribute-based encryption (ABE) access control models. In CapBAC, the subject needs to show the resource owner its token prior to performing corresponding resource request operations. This model and has been used in several large-scale projects like IoT@WORK.1
Access Control based on Usage Control (UCON)
In this model, an access decision will be made using three factors [36]: (a) authorization rules which define the access policy based on the subject and object attributes not only prior to the access but also during the access, (b) Obligations which is responsible to verify mandatory requirements for a subject before or during an access, and (c) conditions that evaluate current environment or system status for usage function. The most important aspect of this model is that if the access attributes change while the access is granted, and this change leads to a security breach, then the granted access is revoked, and the usage is cancelled. This holds because the subject and object attributes are mutable. Mutable attributes can change as a consequence of an access [37].
Organizational Based Access Control Model (OrBAC)
OrBAC proposed by A. Kalam et al. [38] is an extension of the RBAC model in a way that organization is considered as a new dimension. Contrary to DAC, MAC and RBAC, in this model policies are not restricted to static access rules only, but also include contextual rules related to access permissions, prohibitions, obligations and recommendations.
- 1.
Dynamism: If the access decision must change, due to the changes in the subject, object or environment attributes, while the access is granted, then, the access control system is classified as dynamic. Otherwise, if the changes do not affect the access decision, then the access control system is static. Considering dynamism in IoT access control models is important, due to the rapid changes of contextual parameters that occur in this paradigm.
- 2.
Scalability: Scalability in access control must be evaluated by three dimensions, namely an access controls has: (a) Subject/Object (entities) scalability if increasing the number of entities does not lead to an overhead in processing time or workload, (b) Policy rules scalability: if increasing the number of access rules does not lead to overhead in terms of processing time or workload., and (c) Extensibility if it has the ability to extend its structure to cover more sub-systems and domains. The third form of scalability can be achieved through building de-centralized structure rather than centralized structure in scalable environments like IoT.
- 3.
Heterogeneity/Interoperability: In IoT, entities have dependencies and their workflows are tightly convergent, which increases complexity. For this reason, any access control breach in IoT can be more disruptive compared to traditional networks [39]. Furthermore, as IoT is composed of different platforms, enabling technologies and domains, designing an access control model to regulate access inter/intra domains or technologies is a must.
- 4.
Context-Aware: It refers to the ability of the access control system to take contextual attributes to make an access decision. Considering contextual parameters in access decision brings flexibility in terms of tracking subject, object and environment changes if those changes have impacts on the decision.
Evaluation of traditional and emerging access control models against IoT specific criteria
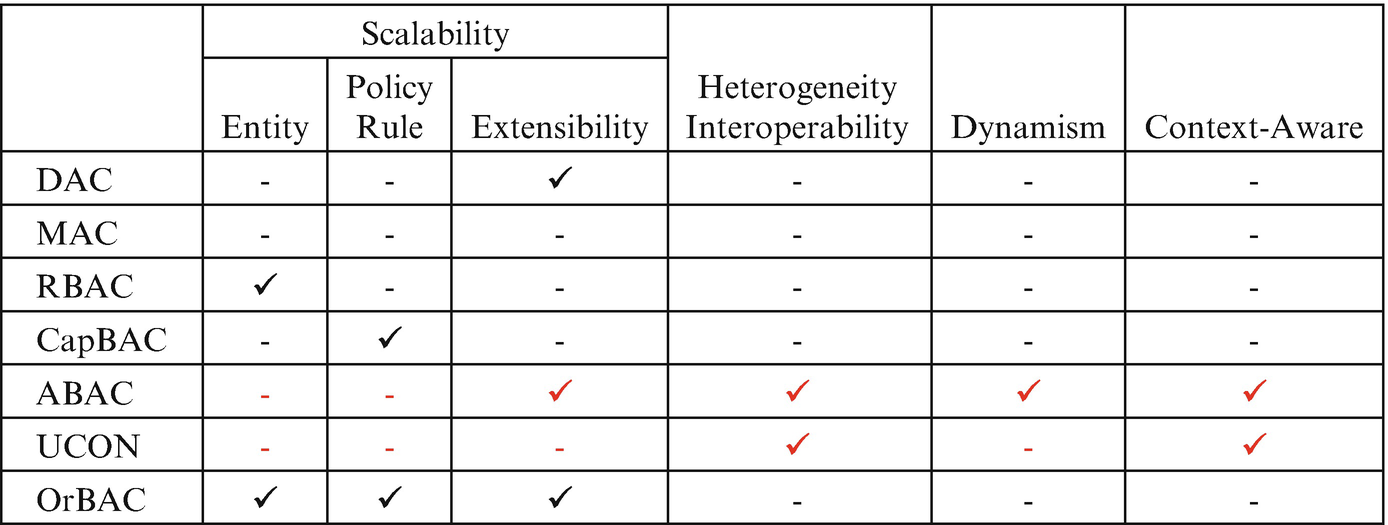
RBAC also does not take contextual parameters into account during access decision. Despite the advantages of ABAC, i.e., fine-grained access control, ease of use in a collaborative environment and flexibility, the adaption of ABAC in IoT is hindered due to overhead. Specifically, applying ABAC in IoT has a limitation in terms of computational overhead because it’s authorization process has high complexity, due to the consideration of attributes of subject, object and environment in the access decision. Thus, applying ABAC in a highly dynamic, real-time environment like IoT is infeasible due to the computational complexity that arises from the number of rules that rapidly increase with entities and contextual attributes, which may change frequently [41–43].
CapBAC is a coarse-grained access control model and does not consider contextual attributes therefore cannot satisfy the flexibility criterion. Moreover, even by applying lightweight cryptography algorithms, like Elliptic-curve cryptography (ECC), using CapBAC brings overhead to the system in scalable scenarios. Another concern about CapBAC is the distribution of token in heterogeneous networks that is not straightforward. Also, the model fails the interoperability criterion as the model cannot be applied in a heterogeneous environment. The reason is that each domain has a dedicated public key infrastructure (PKI) and there is a trust issue in inter-domain interaction between those PKIs [44]. UCON has the same limitations as ABAC in terms of scalability and extensibility. Finally, OrBAC suffers from the same limitation in terms of policy rules scalability as RBAC, as well as fails the interoperability criterion.
The above evaluation, which is summarized in Table 1, highlights the need of a new access control that supports mentioned characteristics for IoT domains.
3 Indeterminacy in Access Control
Indeterminacy has not had the attention that deserves as a challenge in IoT, compared to other challenges that are well-studied in the relevant literature, such as scalability, heterogeneity, interoperability and dynamism [2–6]. However, as this work stresses indeterminacy should be considered when making an access control decision in IoT. Otherwise, if the decision is based on deterministic rules regardless of the indeterminacy concept it can lead to a binary decision (Access/Deny), which does not fit in dynamic environment like IoT.
According to [45], there are at least two facets for indeterminacy: uncertainty and ambiguity. In this work we consider that uncertainty is caused by the lack of information about the likelihood of an event occurring. Also, ambiguity is caused by the lack of precision in the required information to make a decision. In the rest of this section, uncertainty and ambiguity in access control are discussed.
3.1 Uncertainty in Access Control
Aleatory Uncertainty, which refers to an observed phenomenon that occurs randomly, therefore it is impossible to predict.
Epistemic Uncertainty, which refers to the lack of information and knowledge about the properties and conditions of the phenomenon.
Inconsistent Uncertainty, which refers to conflicting testimonies. The notion of inconsistency here describes the case where there is “too much” information available but this information is logically inconsistent.
In the context of a system, uncertainty leads to a situation in which an analyst cannot describe or foresee an event in the system due lack of information about it. Therefore, the main motivation for measuring uncertainty is decision making [47]. The relevant literature includes five main approaches to measure uncertainty, namely: (a) Probability theory, (b) Information Theory, (c) Evidence theory [48, 49], (d) Possibility theory [50], and (e) Uncertainty theory [51].
To define uncertainty in access control, it is essential to differentiate between its effect in the authentication and authorization phases of access control. It should be noted that as discussed in Sect. 2, an access control typically includes three phases: authentication (which encompasses identification), authorization and auditing. Auditing deals with the analysis of the other two phases to detect security violations, thus we consider that uncertainty cannot be considered in this phase.
Uncertainty in authentication stems from the incompleteness of information regarding the likelihood of whether the acceptance of an authentication request leads to an incident. For instance, assume that “Alice” attempts to authenticate to a system. We assume that authenticating her, endangers the system (the access exposes an asset to a threat) with a probability 60%.
Uncertainty in authorization stems from the incompleteness of information regarding the likelihood that an authorized action of a subject could lead to an incident. Assume that “Bob” is an authenticated subject in the system and he wants to perform the “append” operation on a file. We assume that this action could cause harm with a probability of 30%.
In this work we consider that access control methods used in IoT need to treat uncertainty to be classified as uncertainty-resilient access control. This holds true, as the access control approaches that are based on a set of deterministic policies defined by system administrator cannot effectively deal with the unpredicted data access scenarios [52]. In other words, making a binary access decision based on deterministic information (e.g. credential, tokens) cannot cope with the new challenges in access control in a scalable and dynamic enviroment like IoT. To meet this goal in authentication and authorization, three uncertainty-resilient models have been proposed in the literature [53, 54]: (a) Break-The-Glass Access Control (b) Optimistic Access Control, and (c) Risk-Aware Access Control.
Break-the-Glass Access Control
Ferreira [55] proposed a model called Break-The-Glass (BTG) to allow policy overrides. The aim of this model is to allow unanticipated access to be provided in unexpected situations. The main application of this method is in the emergency situations in the healthcare system [56]. One of the most important problems with the BTG is the scalability of policy overriding. By increasing the number of policy overriding in a scalable environment like IoT, the access monitoring and misuse detection become impossible [57]. Another concern about BTG arises from interoperability in heterogeneous environments. Specifically, in a heterogeneous environment consisting of different networks and platforms one entity may be assigned with an overriding policy to handle emergency condition and at the same time be denied by another overriding policy from another domain. These conflicts highlight the need to accurately determine the overall decision is vital [39].
Optimistic Access Control
In cases such as emergency healthcare services, the capability of an access control system to provide openness and availability is more necessary than confidentiality [58]. In this context, optimistic access control has been proposed, which assumes that most access requests will be legitimate. An optimistic approach permits the requesters to exceed their normal access rights. Therefore, putting additional control layer to protect the asset from misuse is recommended for optimistic access control. This approach suffers from the lack of scalability in terms of policy rules. This holds true as implementing defence layers in a scalable environment needs additional resources and causes computational complexity. The optimistic access control also suffers from the lack of interoperability in heterogeneous environment, as defining exceptions for access scenarios that fall between two or more domains with conflict of interests is not straightforward [53].
Risk-Aware Access Control (RAAC)
The closest concept to uncertainty is “Risk”. In one hand, risk is defined as a measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of: (a) the adverse impacts that would arise if the circumstance or event occurs; and (b) the likelihood of occurrence [59]. On the other hand, uncertainty is defined as the lack of information about the likelihood of an event occurring. Therefore, “likelihood of event occurring” is common between these two concepts. Moreover, risk considers the impact of an event. For example, the value of risk in authentication phase is assessed using the following formula:

- 1.
Class A: The risk is calculated based on three parameters: (1) Likelihood of threat (LT), (2) Vulnerability of the asset (V), (3) Impact of the threat (IT), Score of the risk = LT × V × IT
- 2.
Class B: The risk is calculated based on the security requirements of the asset. In this method the vulnerability related to the asset (V) and the impact of the threat (IT) are involved in the calculation of the risk: Score of the risk = V × IT
- 3.
Class C: The risk is calculated in conjunction with the financial loss considerations. To meet this goal, likelihood of the threat (LT) and the average financial loss caused by the threat (FT) are taken into consideration: Score of the Risk = LT × FT
- 4.
Class D: In this class, the risk is calculated only for critical assets. The way of calculating the score of the risk for critical assets is the same as Class B.
- 5.
Class E: The concepts of threat and vulnerability are combined to create a new concept called “Incident”. The score of the risk for this class is calculated using the likelihood of the incident (LI) and the impact of the incident (II): Score of the risk: LI × II
According to [66], RAAC methods can be divided into two types, non-adaptive and adaptive. In non-adaptive, the calculated risk value for each access request remains unchanged even if any risk factor value changes during access session. This means that the access control mechanism cannot follow the changes of risk parameters after granting access. On the contrary, in the Adaptive approach the calculated risk value for each access request may change upon changes in the risk factor value or the detection of abnormal behaviour. Therefore, adaptive RAAC continiously monitor the activities to detect any suspicious event after granting access.
Most existing RAAC approaches rely on manual processes and thus are unable to provide high degree of automation in risk assessment [67–69]. This lack of automation in risk assessment leads to the requirement of manual configuration from analysts, which is costly, error-prone, and vulnerable to a social engineering attack. Moreover, the related work on RAAC that provides a conceptual framework [70] or focuses on only a domain-specific solution cannot be reused in other knowledge domains, and supports only restricted outcomes (i.e., permit or deny) [71]. Therefore, these approaches suffer from lack of generalizability.
3.2 Ambiguity in Access Control
The terms “Uncertainty” and “Ambiguity” are used interchangeably in a number of studies [72, 73]. More importantly, the proposed approaches to address them are used also used interchangeably. This stems from the fact that current there is no clarity in the differentiation between these two concepts.
Ambiguity in authentication stems from the lack of precision in the information regarding the subject requesting to authenticate in the system. In other words, it aims to answer the question of ‘to what extent we can trust the subject in order to authenticate him?’. Assume that “Alice” attempts to authenticate and according to her access history, she has successfully authenticated seven times in the past out of her ten attempts. If the average of successful authentication successes in the system is 60%, then Alice is classified as “trusted” subject.
Ambiguity in authorization stems from the lack of precision in information regarding whether or not the subject performs an action aligned with the purpose that the subject was authorized for. Assume that “Bob” is an authenticated subject in the system and he wants to perform the “append” operation on a file. We assume that our system detects that the trustworthiness reequipment of the file is higher than the trustworthiness of Bob at the time of access. As a result, the “append” operation on the resource is classified as “Untrusted” action for Bob and the action is stopped.
Traditionally, ambiguity has been evaluated with the use of trust analysis. There are two classes of trust analysis [13, 77], (a) credential-based trust analysis and (b) behavioural-based trust analysis. In credential-based trust analysis, trust is established by verifying certain credentials. Upon the credential verification trust is established and access rights to different resources are granted, based on the access policy. This class of trust analysis is widely used in access control systems with static and pre-defined policies. Behavioral based trust analysis uses the past behavior of the subjects to predict how the subject will behave in the future. In authentication, behavioral based analysis takes the history profile of successful and unsuccessful access requests for a given subject as a metric to calculate its trust value. Reputation-based and recommendation-based trust are the subsets of this class of trust analysis that use cumulative knowledge about the past behavior of a subject [78].
Trust metrics can vary from one domain to another. In the context of access control, the following metrics have been used in the literature [79–82]: (a) Number of authentication/authorization failures, (b) subject anonymity, (c) frequency of access request, and (d) degree of trustworthiness for subject and object.
3.3 Proposed Framework
As discussed in the Sects. 3.1 and 3.2, uncertainty and ambiguity cannot be treated in the same way as they are different in nature. Uncertainty must be treated as a risk-based problem. Also, ambiguity focuses on situations in which the assumptions necessary for decision making are not met. In other words, if the decision is made based on imprecise information we are in the vague state of decision making.
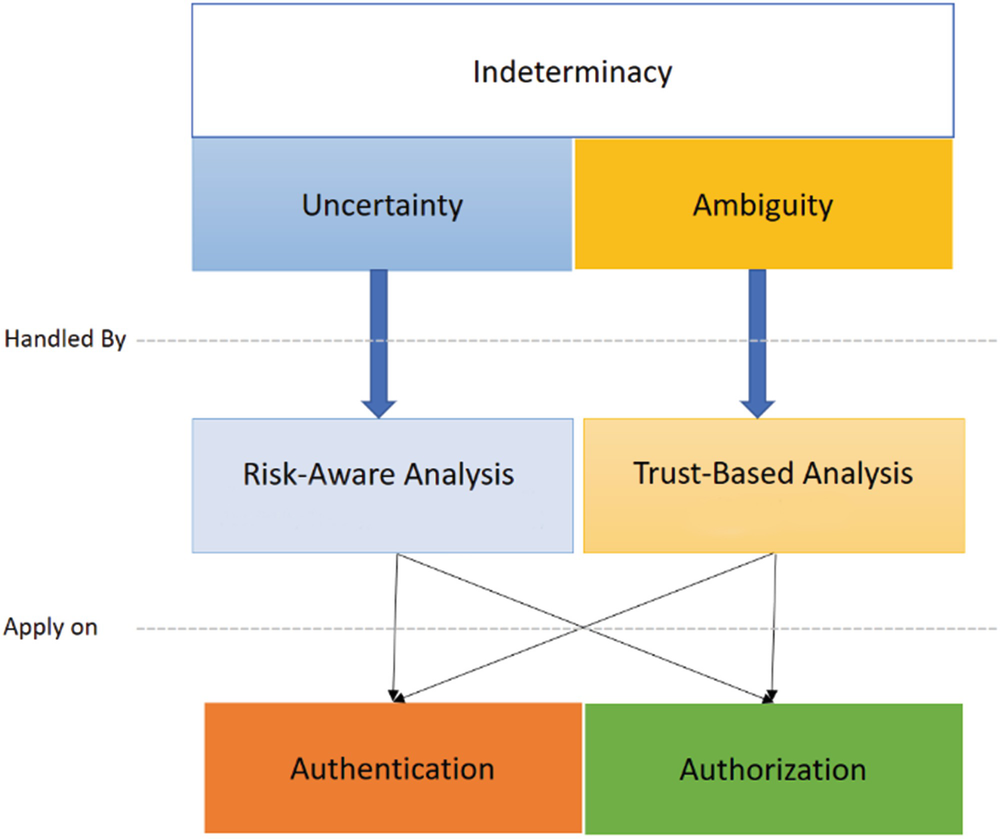
Proposed framework for indeterminacy handling in the field of IoT Access Control
4 Conclusion
In this chapter, traditional and emerging access control were analysed against a set of criteria to see whether they fit in IoT. Then, besides well-studied IoT challenges in the field of access control, we introduced indeterminacy in IoT. We have also discussed how known IoT characteristics, such as scalability, heterogeneity and dynamism, exaggerate indeterminacy in IoT and make real-time access decision for such an indeterminate environment difficult. Three resilient access control paradigms including break-the-glass, optimistic access control and risk-aware access control were discussed to see whether they are able address indeterminacy in access control. Among them, risk-aware access control paradigm is able to address only one facet of indeterminacy i.e. uncertainty. This holds true as risk and uncertainty have one thing in common: “likelihood of an event occurring”. We discussed that another pillar for indeterminacy, i.e. ambiguity, can be handled through trust-based analysis. Finally, we defined indeterminacy (uncertainty and ambiguity) for authentication and authorization phases of access control and proposed a conceptual framework for handling indeterminacy.