Figure 4.1 Steps to Manage a Cyber Incident

In the previous chapters, we have discussed the importance of cyber security and the need for cyber crisis management in the world of digitisation. As the world is shifting towards digitisation to develop and make things easier for everyone, there are people who are trying to create problems for organisations by hacking their computer systems.
Not Possible to Secure Everything!
Cyber security plays a huge role in securing the data of an organisation. By this, we can secure our data to some extent but even after keeping layers of securities, we cannot ignore the fact that cyberattacks happen. It is not possible to secure everything. Despite adopting the best cyber-security practices, there are always chances that a cyber crisis may arise in an organisation. Proper management of such a situation is essential because it directly determines the chances of the organisation to recover from such a cyber incident and, in turn, its business continuity.
Need for Planning
To manage any situation, you need to plan for it in advance because these situations don’t come knocking at your door to alert their presence. You need to ask the following questions: Where to start from? How to identify the problems? How to tackle those problems?
Once you have planned everything, you need to test to what extent your plan works whenever a cyberattack happens. You should know how to properly manage a cyber incident, which involves right decision-making at the right time. This decides the future of your organisation and would also help you to recover all the losses and damages.
Stay calm at the time of a cyber crisis!
How to Manage a Cyber Incident?
Somebody must have advised you to stay calm in difficult situations at some point in your life so that you can take the right decisions. Similarly, it is very important to stay calm at the time of a cyber crisis, if you don’t want things to get worse. People tend to panic at this time and lose control of their minds, which only worsen things. So, it is very important to take the right decision to deal with the cyberattack.
Did You Know?
The amount of damage done by data breaches is stunning! In 2017, 1,293 data breaches, responsible for exposing more than 174 million confidential records, was recorded in the US, which was 45% more breaches than 2016.
Source: ‘2018 Data Breaches—The Worst of Last Year’. https://www.identityforce.com/blog/2018-data-breaches
Every organisation has its own way of dealing with cyber crises or cyber incidents; though some prove to be successful and some do not. Here are some steps that could be taken to deal with a cyber incident:
Did You Know?
The 2017 Annual Data Breach Preparedness Study of Ponemon Institute revealed that 88% of companies had a data-breach response plan in place, but only 49% viewed such plans as effective.
Source: ‘Fifth Annual Study: Is Your Company Ready for a Big Data Breach?’ https://www.experian.com/assets/data-breach/white-papers/experian-fifth-annual-preparedness-study-2018.pdf
Did You Know?
According to a 2018 global study, the total average cost of a data breach rose from $3.62 million in 2017 to $3.86 million in 2018, which was a 6.4% increase. Plus, having an Incident Response (IR) team was identified as the top cost-saving factor, reducing the cost by $14 per compromised record.
Source: ‘2018 Cost of a Data Breach Study: Global Overview’. https://www.ibm.com/downloads/cas/861MNWN2
Figure 4.1 Steps to Manage a Cyber Incident

Importance of Managing Cyber Incidents
It is common observation that an organisation does not pay attention to important things unless it affects its operations or it has suffered financial damage. Similarly, managing a cyber incident almost always signifies post-crisis management wherein the cyberattack has already happened and now needs to be dealt with.
The manner in which an organisation deals with a cyber crisis determines its ability to regain customer loyalty.
This is a very crucial part for any organisation since it decides the fate of the concerned organisation post-attack. The manner in which an organisation deals with a cyber crisis determines whether it will be able to continue its business operations and regain the loyalty of its customers, investors and other stakeholders, or it will succumb to the ill-effects of the cyberattack and never recover.
Did You Know?
According to a 2018 global research study exploring the factors and challenges of being a cyber resilient organisation, it was found that 77% of the firms that were surveyed lacked proper incident response plans; while 69% reported that funding for cyber resiliency was insufficient.
Source: ‘The Third Annual Study on the Cyber Resilient Organization’. https://www.ibm.com/downloads/cas/D3RGN4AJ
Hence, an organisation should always be prepared to face and counteract these types of crisis situations. Cyberattacks can happen with anyone and anywhere; so, it becomes very important to secure your IT systems with all possible security measures. Your readiness should be such that your security measures are able to counter an attack as soon as it happens without any delay!
An organisation should be ready at any given time to face and counteract cyber-crisis situations!
Learn from Prior Cyber Incidents
They say that in life everything counts, and here, every decision counts because one wrong decision could damage the entire business, and that would directly lead to irrecoverable loss. So, you need to keep your eyes, ears and your mind open to take the next decision because the entire development of your organisation, its profit and goodwill depend on that.
An organisation should learn from its mistakes.
It is said that people learn through their mistakes. Even if the organisation has secured its system with high security measures, there is always a possibility that such systems could be hacked. An organisation should always learn from the incident that happens with them. This will help them to acquire knowledge on methods of strengthening the security of their systems and the types of data which require more stringent security, in order to save their systems from getting hacked again.
Important Factors That an Organisation Should Consider to Manage a Cyber Incident
There are many additional details which an organisation should focus on to ensure the effective management of a cyber incident:
An organisation should conduct training programmes on cyber-security practices.
Did You Know?
In a 2017 research survey conducted by SecureAuth Corp, the market leader in adaptive access control, jointly with Wakefield Research, it was revealed that 81% of the people surveyed used the same password for more than one account; whereas 92% of millennials surveyed reported using the same password across multiple accounts.
Source: ‘SecureAuth Survey: Majority Of Americans Reuse Passwords And Millennials Are The Biggest Culprits’. https://globenewswire.com/news-release/2017/07/19/1054094/0/en/SecureAuth-Survey-Majority-of-Americans-Reuse-Passwords-and-Millennials-Are-the-Biggest-Culprits.html
Worst Password Mistakes!
Las Gatos based cyber-security firm, SplashData, evaluates millions of leaked passwords every year to determine and provide a list of the most easily hacked, and thus, worst-protected passwords. The 2018 list includes:
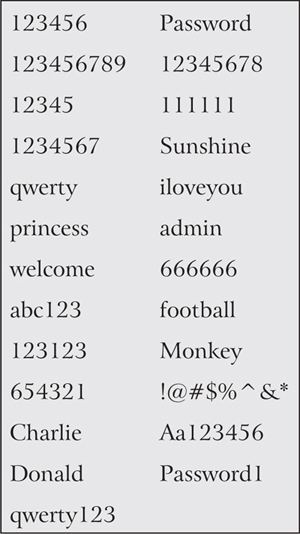
Experts recommend using different passwords for different logins and passphrases of at least 12 characters with mixed types of characters such as numerals, alphabets in different cases and special characters.
Some Cyber Incidents from Around the World
Let us take a look at some cyber incidents from around the world:
Sony PlayStation network attack
There are many organisations who do not use e-security or multi-factor authentication to protect their user accounts—this is a big risk taken by them. They feel that their conventional technique of securing the network is enough. But things went awry in the case of the Sony PlayStation network attack.
Biggest Mistake
Sony did not bother to protect their network!
In 2011, hackers broke into the system and personal information of approximately 77 million accounts were hacked and published. The only resort left for Sony was to shut down their networks for a few weeks. Their only mistake became their biggest mistake ever—they did not bother to protect their network. Hence, they became the victim of a major cyberattack.
Hackers, who attacked the system, said that it was a very easy task as there was not much of security and their sole objective was to show how insecure Sony systems were. The most challenging phase for Sony was to gain the trust of their customers again and to reassure them that their data was safe with them after the incident.
Things to Learn from This Case
No one should ever think that just one layer of security is enough to protect their systems from getting attacked. As cyber-security measures are progressing with technology, even the hackers are updating their ways and techniques of attacking the system. So, one should always put on multiple layers of security since no one can guarantee the safety of their data. Hence, all possible ways of data protection should be implemented to minimise the chances of hacking.
Attack on the Maharashtra government’s official website
In 2007, the official website of the Maharashtra government was hacked. The website obviously contained important information about sensitive state matters, confidential information of the department, critical reports, etc. In this case, the cybercrime branch in Mumbai was also involved as it was a big issue that a government site had been hacked. After the investigation, the officials revealed that the website had been earlier affected by viruses on multiple occasions. It was also discovered that the website had no firewall. This was followed by catching the hackers and getting the website on track.
Things to Learn from This Case
The risk of not protecting the website should never be taken especially when the website contains valuable information. In this case, it was revealed that the website was affected by virus attacks on several occasions even prior to the hacking incident. So, it is crucial that your IT systems have adequate safety measures which are capable of detecting any form of cyber threat or intrusion, and take immediate actions to stop further injury and contain the attack.
Uber case
It is safe to assume that we are well acquainted with Uber, a transportation network company. In 2016, Uber was hacked. Personal information of approximately 57 million users and 6,00,000 drivers was published. It was revealed that the manner in which the cyber incident was handled, worsened the after-effects of the attack. The breach was made public after a year of its occurrence. They even paid $1,00,000 to the hackers to destroy the data. Both their reputation and money were at stake.
Things to Learn from This Case
This case teaches us about the necessity of an organisation to handle a cyber incident efficiently. An organisation must respect the 3 R’s of cyber crisis management: readiness, response and recovery.
The attack on JPMorgan Chase
JPMorgan Chase (JPM) is one of the largest banking institutions of the US. In 2014, JPM was hacked, which compromised the data of approximately 83 million accounts which included names, email addresses, phone numbers and other confidential information of the users. The hackers attacked the root of the system and executed activities, such as closing accounts or transferring funds. The hackers were caught and a case was registered against them.
Things to Learn from This Case
An organisation must protect its IT system in an efficient manner to avoid spilling of private and confidential information in the public domain or into the hands of unscrupulous elements.
The cyberattack on Bayer
According to reports, infectious software was detected on the computer networks of Bayer, a popular German manufacturer of drugs and pesticides, in early 2018. A hacker group known as Winnti was suspected to have conducted the cyberattack. Reports of Bayer’s Cyber Defense Centre, however, stated that there was no evidence of data theft, and Bayer’s cyber security was restored without any major damage. Prior to Bayer, the Winnti group was also reported to have attacked the cyber network at Thyssenkrupp, a renowned German technology group, in 2016.
Things to Learn from This Case
Any organisation, irrespective of its scale and size, may be victimised by cyber criminals. Thus, cyber security must not be taken for granted, and adequate steps must be taken to upgrade existing cyber-security measures of an organisation to protect its computer networks from vulnerabilities. It is possible to prevent damages caused by cyberattacks if they are detected and contained at an early stage, which can be achieved only if a strong cyber-security system exists in an organisation.
Facetime eavesdropping bug
Recently, a major security flaw was discovered in Apple’s FaceTime. The bug, which was initially reported on 28 January 2019, allowed a user to eavesdrop on another individual via FaceTime by connecting the service’s video and audio, even after the rejection of the FaceTime call by the other user. Apple has reportedly resolved the issue by releasing a software patch and conducting a thorough security audit.
Things to Learn from This Case
Organisations must act quickly in order to contain or mitigate cyber-security breaches. In the present case, further damage was prevented when Apple disabled its FaceTime services.
After reading the above cases of cyberattacks on various well-known and large-scale business organisations as well as on a government website, it is clear that organisations must implement cyber-security measures along with a proper cyber crisis management plan.
Major Cyber-incident Managing Mistakes
It is excellent to have a cyber-incident response team, but there are times when they could also commit errors and mistakes. You can formulate the best plan out of every available resource, but the success of such a plan depends upon how well-thought and practically executable it is.
The following box describes some major cyber-incident managing mistakes:
Did You Know?
In 2017, 91% of cyberattacks started with a phishing email.
Source: ‘91% of Cyber-Attacks Start with a Phishing Email: Here’s How to Protect Against Phishing’. https://digitalguardiancom/blog/91-percent-cyber-attacks-start-phishing-email-heres-how-protect-against-phishing
Difficulties Faced by Small-scale Organisations During a Cyberattack
Small-scale business organisations usually tend to think that they are not prone to cyberattacks owing to their size as compared to larger corporations, but they fail to realise that hackers do not care about the size of an organisation. The aim of the hackers is to prove that they are capable of hacking into network systems of any and every organisation, big or small, and thereby, wreak havoc in the organisation by stealing, destroying or otherwise tampering with important confidential data and/or causing financial and reputational loss of the company.
Reasons why small organisations are more prone to cyberattacks:
These factors could also be identified as reasons why small organisations are not able to grow, develop or increase their customers because how would any one place their trust in such organisations which do not have a good reputation, do not have their systems secured properly and which cannot guarantee the safety of their data and personal information. It’s like wasting money even after knowing the consequences.
Did You Know?
According to a 2017 cyber risk report, on a global average, companies around the world take 146 days to detect a cyberattack whereas companies in the EU take 3 times longer than the global average—469 days to detect a cyber intrusion.
Source: ‘2017 Cyber Threats: A Perfect Storm About to Hit Europe?’ https://www.fireeye.com/content/dam/fireeye-www/global/en/current-threats/pdfs/rpt-world-eco-forum.pdf
Tips for Small Organisations
Small organisations should have a cyberinsurance policy.
Did You Know?
Cybersecurity Ventures, a leading researcher on global cyber economy, estimates that cybercrime damages will cost the world $6 trillion annually by 2021, increasing from $3 trillion in 2015.
Source: ‘Cybercrime Damages $6 Trillion By 2021’. https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/
Let us now look into a case which shows that proper management of a cyber incident by an organisation is crucial to ensure its business continuity. An organisation of any size and nature may fall prey to a cyberattack, but the key to recovering from such an attack is to mitigate it efficiently using an effective cyber crisis management plan. The victim organisation may be a large corporation, but if it is unable to properly manage a cyber incident, chances are that it may never regain the loyalty of its customers/ other stakeholders, and in extreme cases, suffer losses huge enough to suspend/ shut down its business operations.
Case Study
The DigiNotar cyber-security attack in 2011 was one of the biggest digital disasters in the Netherlands. DigiNotar is a Netherlands-based certificate authority which was established in 1997. Also known as a Trusted Third Party (TTP), a Certificate Authority (CA) is entrusted with the task of issuing digital certificates after verifying the identity of the recipient (whether a person or an entity) requesting such a digital certificate. This implies that a CA guarantees the authenticity of a certificate issued by it, and such a certificate can be considered digitally safe and secure. In the present case, DigiNotar was responsible for issuing three kinds of digital certificates—standard, qualified and Dutch government certificates otherwise known as PKIoverheid certificates.
The timeline of the DigiNotar cyber-security breach is as follows:
17 June 17–1 July: Cyberattackers gain access to the internal network of DigiNotar systems by breaching the perimeter network.
10 July: Attackers generate the first fraudulent certificate.
10–22 July: Cyberattackers hack into all certificate-signing systems of DigiNotar and generate around 531 fraudulent/ rogue certificates for about 53 different Internet domains.
19 July: DigiNotar discovers a mismatch between issued certificates and its administrative records, and thus detects the attack. DigiNotar, however, keeps silent about the intrusion.
27 July–27 August: Fraudulent certificates generated by DigiNotar are used in Man-In-The-Middle (MITM) attacks on an estimated 3,00,000 users who were exclusively located in Iran. A MITM attack involves the attacker inserting him/herself into a conversation between two parties and by way of impersonating both parties, gaining access to information that either party means to be received by the other. This implied that the traffic intended for Google subdomains were redirected and intercepted using the MITM attack, thus leading to potential exposure of the traffic contents and Google credentials of all the affected users.
28 August: An Iranian user receives a warning from his web browser, Google Chrome, regarding the trustworthiness of the certificate when he tries to log into his Gmail account. The user notifies Google and upon investigation, it is found that the certificate is indeed corrupt.
29 August: The break-in is detected by Mozilla as well. CERT-Bund the German national computer emergency response team informs its Dutch counterpart, GovCERT of the attack. DigiNotar goes public about its cyber-security breach. 3 September: DigiNotar is officially renounced by the Dutch government as a trustworthy certificate authority.
14 September: Dutch authority on telecommunications revokes DigiNotar’s license to issue qualified certificates.
20 September: DigiNotar files for bankruptcy due to irreparable damage of its trustworthiness in generating authentic digital certificates which was its primary business product.
Cyber forensics attributed the massive breach of DigiNotar to the following factors:
Cyber Security Is a Never-ending Battle!
By now, we have understood that cyber security is a never-ending battle. There is no permanent solution to it as of now but we can fight against it by formulating appropriate cyber-incident response plans and accordingly implement them. Organisations should be updated on the latest hacking techniques, and they can accordingly secure their data and information. Therefore, managing a cyber incident is an ongoing process rather than a one-off incident.
A well-secured and strongly protected system is always a challenge for hackers as they have to spend more time hacking them as compared to weakly protected systems and thus have to try and initiate new techniques, which is very time-consuming.
Cyber security is an issue which needs interdisciplinary understanding from all spheres.
Cyber security is an issue which needs understanding from all spheres, such as economics, organisational behaviour, sociology, engineering, law and not just information technology and computer science. Just as it is important to know about the technical aspects of a cyberattack, it is adequately important to know how a cyberattacker operates, such as the common or popular security vulnerabilities that most hackers usually exploit or what are the security measures which hackers have managed to bypass in the past.
It is thus of paramount importance that organisations, irrespective of their size and nature, have a cyber-incident management plan in place, to ensure smooth functioning of their business operations. Let us now understand the relation between cyber security and the Internet of Things in the next chapter.