An event type is essentially a simple search definition, with no pipes or commands.
To define an event type, first make a search. Let's search for the following:
sourcetype="impl_splunk_gen_SomeMoreLogs" logger=AuthClass
Let's say these events are login events. To make an event type, choose Settings and then Event types, as shown in the following screenshot:
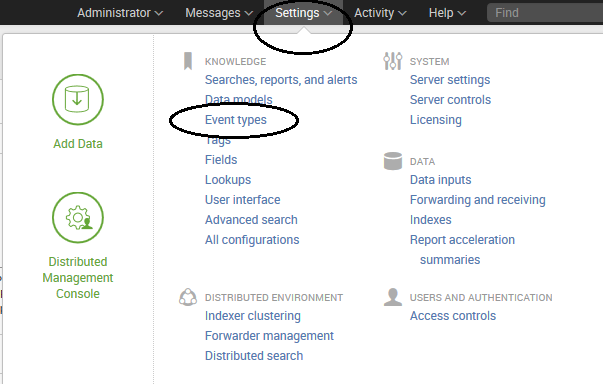
This presents us with the Event types page, where we view existing event types and, as we want to do here, create a new event:

First, click the button labeled New. Splunk will display the Add New page:

Let's name our event type login.
We can now search for the same events using the event type:
eventtype=login
Event types can be used as part of another search, as follows:
eventtype=login loglevel=error
Event type definitions can also refer to other event types. For example, let's assume that all login events that have a loglevel value of error are in fact failed logins. We can now save this into another event type using the same steps mentioned previously. Let's call it failed_login. We can now search for these events using the following:
eventtype="failed_login"
Now, let's combine this event type with the users that we tagged as admin in the previous section:
eventtype="failed_login" tag::user="admin"
This will find all failed logins for administrators. Let's now save this as yet another event type, failed_admin_login. We can now search for these events, as follows:
eventtype="failed_admin_login"
As a final step, let's tag this event type. First, make sure that the field eventtype is visible. Your events should look like this:
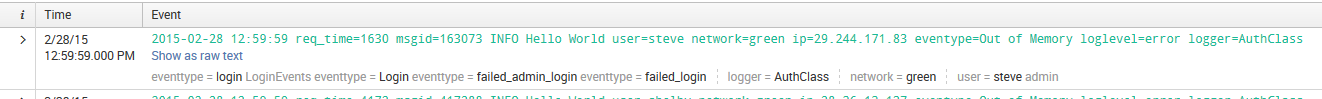
Note the three values of eventtype in this case. We are searching only for eventtype=failed_admin_login, but this event also matches the definitions of eventtype=failed_login and eventtype=login. Also note our tagged user.
We are not searching for the admin tag, but steve matches tag::user=admin, so the value is tagged accordingly.
Following the steps in the previous section, tag eventtype=failed_admin_login with the value actionable:
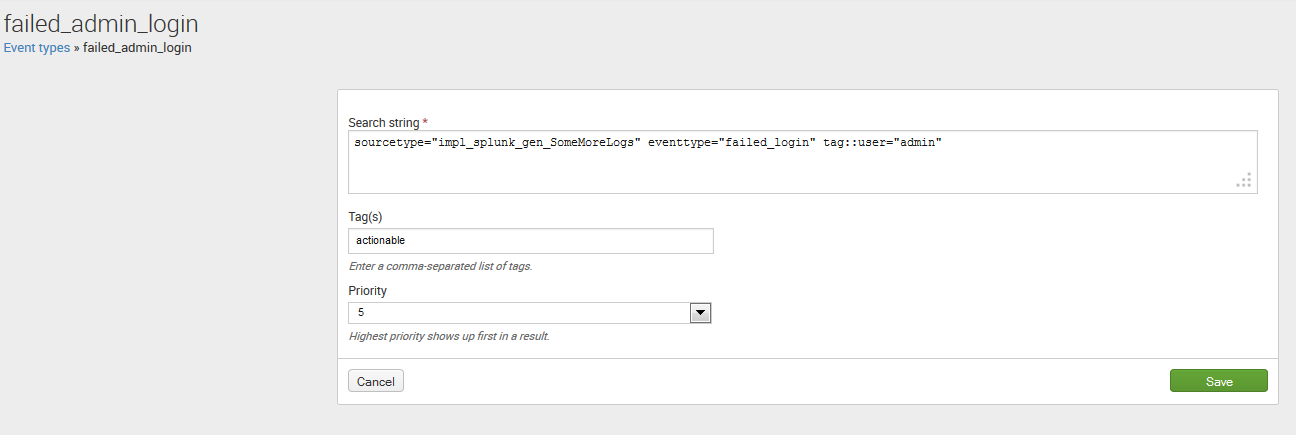
We can now search for these events with the following query:
tag::eventtype="actionable"
This technique is very useful for building up definitions of events that should appear in alerts and reports. For example, consider the following query:
sourcetype="impl_splunk_gen_SomeMoreLogs"
tag::eventtype="actionable" | table _time eventtype user
This will now give us a very useful report, as follows:
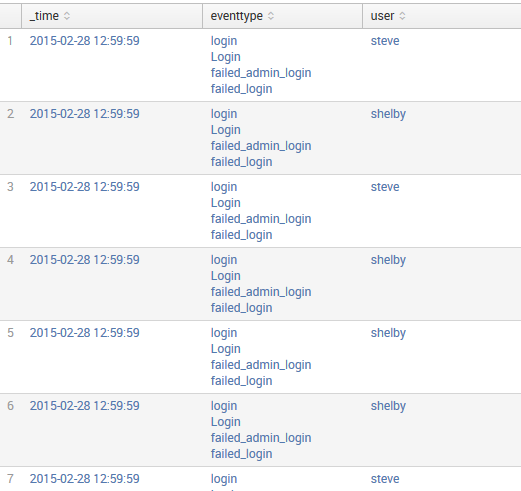
Think about the ways that these event types are being used in this seemingly simple query:
- Search: An event type definition is defined as a search, so it seems only natural that you can search for events that match an event type definition.
- Categorization: As events are retrieved, if the events match the definition of any event type, those events will have the name of that event type added to the eventtype field.
- Tagging: Since event types can also be tagged, tag values assigned to certain event types can be used for both search and categorization. This is extremely powerful for assigning common tags to varied sets of results; for instance, events that belong in a report or should cause an alert.
For clarity, let's unroll this query to see what Splunk is essentially doing under the covers.
The query is expanded from the tag and event type definitions, as follows:
tag::eventtype="actionable" eventtype="failed_admin_login" eventtype="failed_login" tag::user="admin" (eventtype=login loglevel=error) tag::user="admin" ((sourcetype="impl_splunk_gen" logger="AuthClass") loglevel=error) tag::user="admin" ((sourcetype="impl_splunk_gen" logger="AuthClass") loglevel=error) (user=steve OR user=shelby)
Let's explain what happens at each step:
- The initial search.
- All event types that are tagged actionable are substituted. In this case, we only have one, but if there were multiple, they would be combined with OR.
- The definition of the event type failed_admin_login is expanded.
- The definition of failed_login is expanded.
- The definition of login is expanded.
- All values of user with the tag admin are substituted, separated by OR.
Any changes to tagged values or event type definitions will be reflected the next time they are used in any search or report.