15.1. ISO/IEC 27001: An Introduction
ISO/IEC 27001 is a voluntary, international, and certifiable standard defining the requirements needed to set up, implement, and manage an Information Security Management System – ISMS including many aspects on
Logical security: set of measures to preserve integrity and confidentially of digital information;
Physical security: set of solutions whose purpose is to prevent unauthorized access to physical location; and
Organizational security: roles, duties, and responsibilities for defining company security policies and procedures.
An ISMS is part of a global management system based on risk approach, with the aim of setting up, implementing, operating, monitoring, re-examining, maintaining, and improving information security. The management system includes the structure, policies, planning activities, responsibilities, standard approaches and procedures, processes, and resources of the organization (ISO/IEC 27000:2014).
The standard is of general character, since the detailed requirements are applicable to all organizations. Therefore, the implementation of an ISMS can be adjusted to fit organizational variables, set objectives, and security requirements. Also, these aspects varying in time, an ISMS must be modifiable in order to adapt to change.
A fundamental aspect for an ISMS is ongoing improvement. The necessary approach to ensure this objective is the Plan-Do-Check-Act cycle, a cyclical approach to monitor and keep changes under control.
The regulation was drafted by a working group referring both to the International Organisation for Standardization (ISO) and the International Electrotechnical Commission (IEC).
ISO takes care of cross-cutting standardization in all sectors, while IEC focuses on electronics’ environment. The committee in charge of the joint activities of the two bodies is the Joint technical committee 1 (JTC 1), in turn divided into further subcommittees. Specifically, the one related to ISO/IEC 27001 is sub-committee 27.
15.2. History
The international ISO/IEC 27001 standard originates in 1995 with the name BS 7799 “Information security management – Code of practice for information security management,” a British regulation published by the British Standard Institute, following the need of English organizations to catalog security controls related to information safety.
In 1998, the British Standard Institute launched a new version of the BS 7799-2: 1998 “Information security management system – Specifications” standard in which several requisites for the management of information safety have been introduced, such as compliance or system access control requirements. The structure of ISO/IEC 27001 picks up the structure of BS 7799-2: a list of system requirements followed by an appendix containing a series of security controls. A further update in 1999 then managed to specify some previously neglected issues, in particular, technological progress has made security controls obsolete and therefore to be renewed.
In 2002, BS 7799-2 was updated again. This version of the standard was drafted in order to be aligned with ISO 9002 and ISO 14001. Many requisites are in fact picked up by these two versions, with the exception of the appendix.
In 2005, the ISO/IEC committee adopted the BS 7799-2 standard and published the first version of the ISO/IEC 27001:2005 international standard, which does not bring relevant changes with respect to the forerunning BS 7799-2:2002 British standard.
Finally, the current version of ISO/IEC 27001:2013, sees the introduction of the High Level Structure (HLS) and of new requisites on performance evaluation, along with the removal of certain preventive actions and the reduction of requisites pertaining risk assessments.
HLS springs from the need of defining a common structure to develop standards related to management systems because management systems standards published before 2012 are very similar but structured differently. Therefore, in 2009, the Technical Management Board – an ISO technical committee – thanks to the help of the Joint Technical Coordination Group, begins drafting the HLS. In particular, the HLS is published in 2012 in the SL Annex of the ISO/IEC Directives, Part 1, Consolidated ISO Supplement.1
Many standards follow the HLS directives: ISO 9001, ISO 14001, ISO/IEC 27001, ISO 39001, ISO 45001. All of these guidelines pertain to security ISO/IEC 27000-series
ISO/IEC 27001 standard is part of the ISO/IEC 27000-series. We can divide this large family into four main areas according to their purpose:
(1) Terminology
(2) Requisites
ISO/IEC 27001 – “Information security management system – Requirements.” This document contains binding requisites to which an organization intending to submit to a certification process must abide.
ISO/IEC 27006 – “Information technology – Security techniques – Requirements for bodies providing audit and certification of information security management systems.” Specifies the requisites the auditing and certification body must refer to.
ISO/IEC 27009 – “Information technology – Security techniques – Sector-specific application of ISO/IEC 27001.” Describes the requisites for the practice of ISO/IEC 27001 in a specific sector.
(3) General Guidelines
ISO/IEC 27002 – “Information technology – Security techniques – Code of practice for information security management.” Provides guidelines for the management and implementation of information security.
ISO/IEC 27003 – “Information technology – Security techniques – Information security management system implementation guidance.” Provides guidelines for the definition of an implementation project of an ISMS according to what is established in the ISO/IEC 27001 standard.
ISO/IEC 27004 – “Information technology – Security techniques – Information security management – Measurement.” Provides the ways to measure the performance and effectiveness of the ISMS to meet the requirements set in charter 9.1 of the ISO/IEC 27001.
ISO/IEC 27005 – “Information technology – Security techniques – Information security risk management.” Guidelines for the proper evaluation of business risk, in particular information security related risk.
ISO/IEC 27007 – “Information technology – Security techniques – Guidelines for information security management systems auditing.” It is a guideline for accredited standardization bodies to verify the conformity to the requisites of an ISMS established by the ISO/IEC 27001 standard.
ISO/ IEC TR 27008 – “Information technology – Security techniques – Guidelines for auditors on information security controls.” Focuses on the ISMS auditing process.
(4) Sector Specific Guidelines
Refers to a series of sector specific guidelines jointly drafted by ISO and IEC. For example, ISO/IEC 27011 provides guidelines and techniques for telecommunications sector.
15.3. Structure
The ISO/IEC 27001 international standard is structured in ten chapters, with the addition of a final appendix. The first three deal with the scope, normative reference and terms and definitions of the standard recalling the ISO/IEC 27000 standard, while the remaining chapters (from chapter 4 to 10 within the standard) are dedicated to the following key system requisites set by the standard: context of the organization, leadership, planning, support, operation, performance evaluation, and improvement. The appendix is dedicated to the security check to which one must refer.
15.3.1. Scope
The first chapter of the international standard specifies the requisites to which management systems for the security of information (ISMS) must abide.
In order for the requesting organization to be considered compliant to the standard, all aforementioned system requisites must be satisfied. Appendix A requisites can, on the other hand, not be taken into account should they be not necessary and/or considered not applicable.
Finally, it is important to remark once more that the standard is applicable to all types of companies since the requisites are of general character.
For example, the ISMS is adopted to develop and improve adequate and proportionate checks for the security of information in order to protect information assets and set acceptable boundaries for confidentiality, availability and privacy towards clients and all interested parties. To maintain and improve data security levels regarding organisational processes, legal conformity and, by consequence, the reputation of the organisation.
15.3.2. Context of the Organization
The fourth chapter of the ISO/IEC 27001 standard focuses on the organization’s context and the scope of ISMS.
Context, recalling the ISO 9000:2015 definition, is the combination of internal and external factors able to influence the proper achievement of the company’s objectives.
First of all, therefore, it is important to understand what these objectives are and clearly pinpoint them. The standard then requires to highlight all aspects interested to the ISMS and which are the established prerequisites.
The organization is then required to identify and document the scope of the ISMS in detail, meaning the field of application and relative limits. Often, ISMS in many companies refers only to part of the organization.
For example, a supplier of IT services for a financial corporation has decided to implement a system for the management of information security just for the running of systems but not for the aspects related to the physical security of the structure. Taking into consideration that continuous system availability is essential for the proper implementation of the main activities of the company, it is important to set aside economic resources for this purpose and later expand it to other areas.
In determining the area, the internal and external factors just mentioned must be taken into consideration, along with any interested parties and underline the existence of processes entrusted to external subjects and how they interact with the organization.
For example, the maintenance of plant machinery can be outsourced to a qualified external supplier.
15.3.3. Leadership
The fifth chapter focuses on the responsibility of higher management and policy2 in general. Specifically, higher management must:
make sure information security policies and objectives are established and aligned with the strategy of the organization and integrated in their processes;
develop and promote security culture under every aspect by issuing regulations, rules, guidelines, and through constant awareness building of all human resources, understand the fundamental importance of confidentiality, integrity, and data availability of information acquired, developing rules, regulations, and guidelines and adopting the most modern data protection techniques;
define, plan, and implement a system for the identification of risks, the evaluation of risks and then implement the necessary measures for the reduction of risks related to the activities carried out;
ensure the services supplied by external bodies necessary for the implementation of the set objectives meet the established security standards;
ensure the proper availability of financial and human resources necessary for the ISMS;
disseminate the importance of an efficient ISMS and conformity to its requisites; and
direct and guide human resources so that they can contribute to the efficacy and continuous improvement of the system and support all other managerial roles.
The management must also define and clearly convey the roles taken on within the organisztion and the pertaining responsibilities. The appointment of a role is a crucial aspect in organizational dynamics since even a single employee can influence the performance of the ISMS; therefore, he/she must be aware of the tasks and responsibilities he/she is entrusted with and duly report detailed feedback to higher-ranking positions.
Even if the standard does not require to put a person in charge of information security, since the management itself has ultimate responsibility, it is common practice to put someone specific in charge, often dedicated to both information and company security; then identifying those in charge of occupational safety, company image, and so on.
As far as information security policy is concerned, it must:
be appropriate with respect to the organization’s objectives;
establish a detailed framework for the definition of information security objectives;
clearly state the objective of compliance with ISMS requisites and ensure ongoing improvement; and
be documented, disseminated, made available within the organizational context.
The policy can be disseminated toward external parties entirely or partially, making sure not to divulge confidential information.
For example, here are a few parties, external to the organization, to which they communicate the abovementioned policy:
15.3.4. Planning
The sixth chapter of the international standard is dedicated to strategic planning of the management system for the security of information and the management of risk and opportunities.
In general, during the planning phase, the organization must make sure that:
the ISMS reaches the set objective;
there is a malfunction prevention plan;
ongoing improvement is guaranteed; and
corrective actions are taken in case of malfunction, risks and threats, and that the means to integrate and evaluate these actions within the system are defined.
The process of risk assessment is usually carried out following the methodology foreseen in the ISO 31000 “Risk Management” standard.
Risk analysis allows for the:
identification of risk criteria, relative acceptance criteria, and their association to potential confidentiality, integrity and information availability loss;
identification of those responsible for each risk;
identification of risk levels;
comparison of risks with risk criteria3 and their order according to processing priority; and
periodic repetition of the process until correct and coherent results are reached.
In order to discuss risk assessment, the first step must be the definition of “risk.” The ISO/IEC 27000 standard states: “risk: the effect of uncertainty on objectives.” This uncertainty is due to events that can generate negative or positive consequences. If these risks generate positive effects, then we are facing “opportunities.”
An example of an opportunity can be image and reputation improvement following prompt intervention related to a breach in the system.
The evaluation of risk consists in a group of activities aimed at identifying risks/opportunities, calculating its level – an estimation of the effect of the risk’s consequences – and deciding if these are acceptable or not.
The standard then foresees some activities for the treatment of risk and some control measures allowing for these treatments. Once the checks are selected, they must be compared with those present in Appendix A.
The Statement of Applicability (SoA) is then drafted. This document consists in the declaration of checks stated in Appendix A that are applicable and implemented by the organization. The SoA is the document describing requirements and checks relevant and applicable to the ISMS of the organization, and the requirements and checks are those based on the results and conclusions of processes of risk analysis and management.
Finally, the standard requires one to set final objectives in the ISMS, which are consistent with the policy, measurable, updated, and communicated.
Once the objectives are established, the following steps must be taken:
determine actions and procedures needed to reach them;
define a deadline;
identify the necessary resources;
define responsibilities; and
define evaluation modes.
The objectives, coherently with what defined by the ISO/IEC 27000 standard, can be strategic, tactical, or operational. While strategic ones are not directly measurable, they only define company strategy, and the operative and tactical ones must me objectively measurable.
The operational objectives are short-term objectives, while the tactics ones are medium-term whose achievement helps the organization to get closer to the achievement of the strategic objectives.
A strategic objective might consist in guaranteeing systems’ availability every time users use it.
Moreover, a tactical objective could consist in guaranteeing the availability of systems with a level of service up to 99.5% within a year. An operational objective is guaranteeing ongoing updating of operative systems (security patch).
15.3.5. Support
The seventh chapter includes a series of requirements related to the resources used for the ISMS:
competence;
awareness;
communication; and
documentation.
In particular, the organization must possess adequate economic, infrastructural, and human resources to implement the ISMS to the best possible level, keeping in mind continuous improvement.
It is therefore necessary to identify, acquire, and evaluate the specific competences possessed by human resources, meaning the competences that can influence the performance of the ISMS. It is very important that human resources be competent. To ensure this, specific personnel training must be carried out.
Employees must be made aware of the great importance held by company policy, and the relevance of their behavior as a key factor influencing performance, including awareness of how the consequences of incorrect behavior can harm overall results.
Internal and external communication is fundamental for the ISMS, and it is crucial to know when to do so, which are the proper addressees and which topics are to be the object of communication activities, along with understanding the best and most efficient way to proceed.
For example, internal communication plays a very important role when management decides to implement changes in the ISMS management policy. If internal communication activities are not carried out properly, human resources will not be updated on the changes and inevitable misunderstandings can occur.
Effective external communication allows the company to acquire competitive advantage since adequate communication about information security policies improves the company’s reputation and increases stakeholder interest.
The final part of the chapter is dedicated to the documents necessary and procedures to be implemented for the documentation of information. To be more precise, the standard refers to “documented information.” The criteria for the creation, modification, approval, storage, protection, and availability of documents are duly indicated.
For example, a document needing approval is the Memory of Meeting since it must be approved by the meeting’s participants.
When drafting these documents, it is fundamental to be clear, precise, and concise, in order for them to be understood by all interested parties. All documents must be made available through a document management system, for example, a shared filesystem, a sharepoint site, or a content management system.
15.3.6. Operation
The eighth chapter is very brief but very important because it requires to carry out all of the already mentioned activities.
As far as the planning and control of operations goes, the standard specifically requires to implement actions and planned steps in order to reach the objectives set in the sixth chapter. All these activities will have to be documented, monitored, and their effectiveness evaluated.
Risk treatment and evaluation regarding the security of information is then recalled and will have to be carried out periodically and, of course, also after extraordinary occurrences. Again, documentation must be detailed and clear.
Finally, particular attention is given to outsourced activities, which will have to be defined, identified, and monitored. For this reason, it is also very important to monitor suppliers well beyond the more immediate services rendered.
15.3.7. Performance Evaluation
In the ninth chapter, the standard analyzes the monitoring, measurement, analysis, evaluation, internal audits, and review of the management. In former editions, some of these topics were carried out in separate paragraphs.
It is worth focusing on the difference between monitoring and measurement, since the two are often misused as synonyms.
Recalling the definition of the ISO/IEC 27000 standard:
Monitoring: determining the status of a system, a process or an activity and
Measurement: process to determine value.
With reference to a company providing IT services and specializing in data processing, the process of malfunction management can be assessed through:
monitoring: in depth analysis of malfunction modes, focusing on triggering causes, context, and deviations from forecasted data and
measurement: calculating how many times the problem occurs.
It is important to take notice that the analysis focuses on processes and security controls; human resources are not subject to evaluation.
It is therefore necessary to determine what and how to monitor and measure, not concentrating exclusively on processes but also on security checks; when and who must be analyzed and evaluated and finally who must evaluate these results.
Nowadays, numerous softwares for the evaluation and monitoring of data and performance are present on the market, spanning from simple electronic spreadsheets in which the main indicators of system performance are displayed, to very expensive dedicated software programs.
Examples of significant measurements in a ISMS:
risk level;
incident resolution intervals;
number of system failures; and
system availability intervals.
Internal audits must be carried out according to the specifications of the ISO 19011 standard. These audits must first of all verify conformity to specific company requirements and to the International Standard.
The organization must therefore prepare an audit program that takes into account the results of previous audits, the regularity of checks, the set requirements and modalities of reporting results, define “audit criteria” for each audit, meaning the internal procedures necessary; and select expert and unbiased auditors. Reporting, as usual, all documents pertaining to these inspection activities.
Should non-conformities emerge during the audit, it is the management’s burden to plan corrective actions in order to return to conformity as soon as possible.
For example, during an audit of the Data Center of a provider of web services, auditors asked system operators to simulate a blackout to analyze the website’s reaction times under extraordinary conditions. The site turned out to be unusable, since UPS units were not functioning. Because of this malfunction, the audit declared the non-conformity of the Data Center and Management had to plan the acquisition of a new UPS unit.
If this situation had taken place during normal system operations, the effects of this failure would have caused significant loss of client appraisal and would have damaged the company’s reputation.
Finally, aside from periodically revising the functioning of the ISMS, management must also take into consideration actions aimed at monitoring previous checks, internal and external changes, also by setting aside a proper budget for these activities.
Furthermore, it must receive substantial feedback on system performance, in particular: non-conformities and subsequent corrective actions, results of measurements, monitoring, and the implementation, or lack of, of the objectives set in the previous phases. Feedback from all interested parties must also be taken into consideration, along with risk evaluation results and the state of the risk treatment plan.
Given all the abovementioned data, the management must decide how to proceed and look for new opportunities to improve the system.
15.3.8. Improvement
The last chapter, as titled, examines the concept of improvement, according to two different meanings: continual improvement and improvement as a consequence of corrective actions following non-conformity.
Specifically, the concept of non-conformity is to be considered the “non-fulfilment of a requirement” (ISO/IEC 27000: 2018).
There are four types of non-compliance categories:
(1) Process: non-compliance to predefined procedures and to the ISO/IEC 27001 standard.
(2) Production: non-compliance of products to set specifications/projects.
(3) Client complaints: products not satisfying the needs of clients.
(4) Supply: non-compliance of delivered products with respect of what was agreed upon.
Should these situations occur, the organization must proceed with corrective actions. First of all, corrective actions must be taken to amend the problem and deal with its consequences. These actions must guarantee that non-compliance does not occur again, therefore, it is fundamental to pinpoint the source of non-compliance and similar contexts with high failure rates.
Once these actions are taken, it is necessary to monitor the impaired process and evaluate the effectiveness of the action taken. Should a worst-case scenario take form and the corrective action fails to be effective, changes and improvements must be made to the ISMS.
For example, the introduction of a video surveillance system reduces possible risks of malicious access within a sensitive area.
All these steps must be documented and preserved.
As far as ongoing improvement is concerned, it is to be intended as the constant search to improve the suitability, competence, and effectiveness of ISMS.
The concept of continuous improvement is fundamental in ISMS, and it is often mentioned throughout the standard.
15.3.9. Appendix A
Appendix A “Control objectives and controls” contains 114 “controls” to which the organization must abide. To be precise, to comply to the standard, the organization must conform exclusively to those controls deemed applicable, motivating the choice made and the possible exclusion of others.
These controls try to involve all of the company’s sector/departments. They span from policy to security, from the management of human resources to the management of assets, and move on to access control and cryptography. Also contemplated are controls on physical safety, environment and equipment, and security operations and communications security. Guidelines are also given with regard to interactions with suppliers and incident management. Finally, controls for business continuity and compliance are also indicated.
Here is a list of some objectives and controls listed in the Appendix A:
A.5. Information security policies
A.5.1. Management direction for information security
Objective: To provide management direction and support for information security in accordance with business requirements and relevant laws and regulations.
A.5.1.2. Review of the policies for information security
Control: the information security policy shall be reviewed at planned intervals or if significant changes occur to ensure its continuing suitability, adequacy, and effectiveness.
A.6. Organization of information security
A.6.1. Internal organization
Objective: To establish a management framework to initiate and control the implementation and operation of information security within the organization.
A.6.1.2. Segregation of duties
Control: Conflicting duties and areas of responsibility shall be segregated to reduce opportunities for unauthorized modification of the organization’s asset.
A.9. Access control
A.9.1. Business requirements of access control
Objective: To limit access to information and information processing facilities.
A.9.1.2. Access to network and network services
Control: Users shall only be provided with access to the network that they have been specifically authorized to use.
A.12. Operations security
A.12.3. Backup
Objective: To protect against loss of data
A.12.3.1. Information backup
Control: Backup copies of information, software and system images shall be taken and tested regularly in accordance with an agreed backup policy.
15.4. Benefits of the Application of the ISO/IEC 27001
Setting up a management system (ISO 9001, ISO 14001, etc.) brings several benefits to the organization (Orzes et al., 2018; Orzes, Jia, Sartor, & Nassimbeni, 2017; Sartor, Orzes, Di Mauro, Ebrahimpour, & Nassimbeni, 2016; Sartor, Orzes, Touboulic, Culot, Nassimbeni, 2019). In particular, the implementation of an ISMS, will, first of all, help limit the costs of failure (malfunctions which can seriously damage an organization’s profitability).
Containing malfunctions will increase the organization’s reputation by the stakeholders; this will strengthen the bonds with existing clients and help in the acquisition of new ones.
Incidents which could generate negative legal and contractual consequences are lower; for example, a legal sanction due to the violation or loss of sensitive data.
Also, the effort required for the involvement and training of staff later generates overall performance improvement and supports staff’s dedication in the safeguard of information security. Employees, being fully aware of the importance of their role, can in turn bring new and useful contributions to the improvement process.
Risk management, on the other hand, helps the organization minimize malfunctions, thus guaranteeing substantial financial savings and continuity of service.
Seeing the numerous undeniable advantages of this international standard, many organizations at world level have understood the importance of certification. As can clearly be seen in the chart (Fig. 15.1), the trend of ISO/IEC 27001 certifications is constantly rising, reaching 27,500 units at the end of 2015.
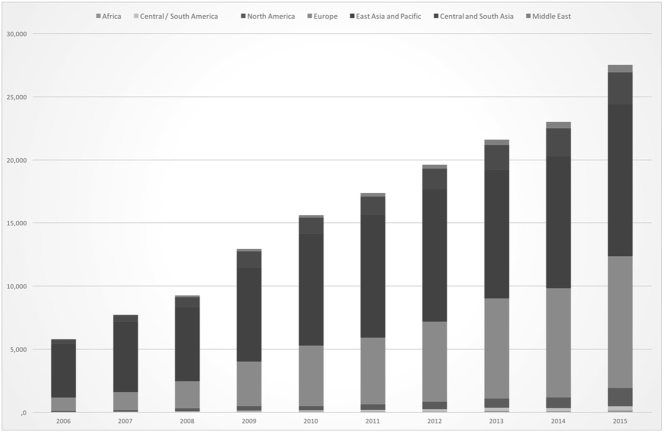
Fig. 15.1: Worldwide Total Number of ISO 27001 Certifications. Source: Adapted from the ISO Survey of Management System Standard Certifications (2006–2015).
It is obvious that Asia and Oceania are the continents with the higher number of certifications: 11,994, in detail, followed by Europe with a substantial number: 10,446.
It is also peculiar to notice that in North and Central America (Mexico, Canada, and the United States of America) the number of certifications is quite low.
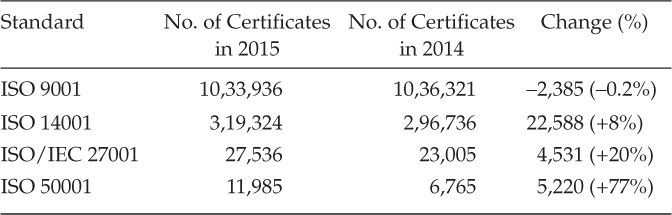
Focusing now in particular on 2014 and 2015 data (Table 15.1), we can see that 4,531 organizations obtained the ISO/IEC 27001 certification, a 20% rise compared to the prior year.
Table 15.1: Number of Valid Certificates to ISO Management System.
15.6. “Integrated Management System”
Lately, many organizations worldwide, drawn to the benefits provided by management systems, are implementing more than a single standard for management systems, therefore, setting up a single integrated management system, which satisfies all requirements set by each single management system and forming an integrated structure.
Fig. 15.2 shows the trend of the number of certified organizations at the same time with three certified standards.
For example, an organization possessing both an ISO/IEC 27001 and an ISO 9001 certification, is already a company implementing a quality management system and an ISMS, and can decide to integrate both systems, thus creating an IMS that will have to comply both to quality and information security requirements.
The first issue organizations must face is how to proceed in order to integrate two or more independent management systems.
All management systems related to the ISO 9001, ISO 14001, ISO/IEC 27001, ISO 45001 (etc.) standards, use the same structure called Annex SL, which facilitates integration by structuring processes and the necessary documentation in a similar way.
Various studies show that organizations reap numerous benefits from the implementation of an IMS: documentation and bureaucracy is lower, as well as costs, since resources are used to their full potential, focused with regard to company objectives improves and a better external and internal communication flow is generated.

Fig. 15.2: “Organization with Three Certification at the Same Time.4 Source: Adapted from Accredia.it.
On the other hand, setting up an IMS can be extremely complicated, especially in the initial phase, where the various interested parties are often reluctant to collaborate and relevant economic resources must be invested.
It is up to the management to evaluate if the organization can truly benefit from the introduction of an IMS or if keeping independent management systems is the best option.
References
Calder, A. (2013). ISO27001/ISO27002 A pocket guide. Cambridgeshire, UK: IT Governance Publishing.
Gallotti, C. (2017). Sicurezza delle informazioni: valutazione del rischio; i sistemi di gestione la norma Iso/Iec 27001:2013, Lulu.com.
Hoy, Z., & Foley, A. (2015). A structured approach to integrating audits to create organisational efficiencies: ISO 9001 and ISO 27001 audits. Total Quality Management & Business Excellence.
Kopia, J., Kompalla, A., & Buchmüllet, M. (2016). Theory and practice of integrating management systems with high level structure.
Orzes, G., Jia, F., Sartor, M., & Nassimbeni, G. (2017). Performance implications of SA8000 certification. International Journal of Operations and Production Management, 37(11), 1625–1653.
Orzes, G., Moretto, A. M., Ebrahimpour, M., Sartor, M., Moro, M., & Rossi, M. (2018). United nations global compact: Literature review and theory-based research agenda. Journal of Cleaner Production, 177, 633–654.
Sartor, M., Orzes, G., Di Mauro, C., Ebrahimpour, M., & Nassimbeni, G. (2016). The SA8000 social certification standard: Literature review and theory-based research agenda. International Journal of Production Economics, 175, 164–181.
Sartor, M., Orzes G., Touboulic, A., Culot, G., Nassimbeni, G., (2019). ISO 14001 standard: Literature review and theory-based research agenda. Quality Management Journal, 26(1), 32–64.


