Chapter 5
Scanning
CEH EXAM OBJECTIVES COVERED IN THIS CHAPTER:
 II. Analysis/Assessment
II. Analysis/Assessment
 B. Systems analysis
B. Systems analysis
 III. Security
III. Security
 J. Vulnerability scanners
J. Vulnerability scanners
 IV. Tools/Systems/Programs
IV. Tools/Systems/Programs
 J. Port scanning (e.g., nmap)
J. Port scanning (e.g., nmap) M. Vulnerability scanner
M. Vulnerability scanner N. Vulnerability management and protection systems
N. Vulnerability management and protection systems
 Once you’ve completed the footprinting phase and you’ve gathered a good amount of information about your target, it’s time to act on this information. This is the point where you try to ascertain what assets the target has and what is of value.
Once you’ve completed the footprinting phase and you’ve gathered a good amount of information about your target, it’s time to act on this information. This is the point where you try to ascertain what assets the target has and what is of value.
The scanning process is possible in part because of the wealth of information you gathered in Chapter 4, “Footprinting,” and how you are able to interpret that data. Using information found on discussion groups, through emails, at job-posting sites, and other means, you now have an idea of how to fine-tune your scan.
To successfully negotiate the scanning phase, you need a good understanding of networks, protocols, and operating systems. I recommend that if your knowledge of network and system fundamentals is shaky you go back and review Chapter 2, “System Fundamentals,” before you proceed. This chapter brings forward some of that information, but I will place our primary focus on scanning and gaining information, not on past topics.
What Is Scanning?
Scanning is a process that involves engaging and probing a target network with the intent of revealing useful information and then using that information for later phases of the pen test. Armed with a knowledge of network fundamentals, a scanner, and the results of a thorough footprinting, it is possible to get a decent picture of a target.
Types of Scans
Not all scans will be looking for the same thing or attempting to achieve the same result, so it is important that you understand what your options are going into the process. All scans share the same general theme, which is to gain information about a host or group of hosts, but if you dig a little deeper differences start to emerge. Each scan will provide a different level and type of information than the others, and thus each will provide some value to you.
To keep things simple, let’s break the types of scans into three different categories, each with its own characteristics:
Port Scan Port scanning is the process of sending carefully crafted messages or packets to a target computer with the intent of learning more about it. These probes are typically associated with well-known port numbers or those less than or equal to 1024. Through the careful application of this technique, you can learn about the services a system offers to the network as a whole. It is even possible that during this process you can tell systems such as mail servers, domain controllers, and web servers from one another. In this book the primary tool we will use in port scanning is Fyodor’s nmap, which is considered by many to be the definitive port scanner.
More than likely when the topic of scanning is mentioned, this is the type of scan many think of. While many different scanners on the market perform the same task, nmap is far and away the most frequently used.
Network Scan Network scanning is designed to locate all the live hosts on a network (the hosts that are running). This type of scan will identify those systems that may be attacked later or those that may be scanned a little more closely.
Scans that fit into this category are those such as ping sweeps, which rapidly scan a range of IPs and determine if an address has a powered-on host attached to it or not. Tools to perform this type of scan include nmap and Angry IP as well as others.
Vulnerability Scan A vulnerability scan is used to identify weaknesses or vulnerabilities on a target system. This type of scan is quite commonly done as a proactive measure, with the goal of catching problems internally before an attacker is able to locate those same vulnerabilities and act on them. A typical vulnerability scan will discover hosts, access points, and open ports; analyze service response; classify threats; and generate reports.
Vulnerability scans are popular with companies because they can perform them on their own quite easily to assess their systems. Two commonly used vulnerability scanners include Tenable’s Nessus and Rapid7’s Nexpose. In addition there are specialized scanners such as Burp Suite, Nikto, and WebInspect.
What types of information can you expect to come away with as part of a penetration test? There’s no simple answer to that question, but we can make some general assumptions on what may be uncovered. During the scanning process it is possible to encounter information such as the following:
- Live hosts on a network
- Information on the open/closed ports on a host
- Information on the operating system(s) and the system architecture
- Services or processes running on hosts
- Types and seriousness of vulnerabilities
- Information about patches present on a system
- Presence of firewalls
- Addresses of routers and other devices
Looking at this list, it is easy to see why scanning is considered part of the intelligence-gathering process an attacker uses to gain information about a target. Your skill, tenacity, and creativity (in some cases) will determine how successful you will be when performing a scan, so if you hit a roadblock during scanning, rethink the problem and determine your next step. Remember to refer to the information you harvested during the earlier footprinting phase for guidance.
Expect the information that is gathered during this phase to take a good amount of time to analyze, depending on how good you are at reading the resulting information. Your knowledge will help you not only to better target your initial scans but also to better determine how to decipher certain parts of the results, as you will see later.
Checking for Live Systems
To begin, let’s start looking for targets to investigate and probe. Remember that while you may have gathered information during the previous phase that described the IP or range of IPs that an organization owns or is connected to, this does not mean that each address has a host behind it. In order to proceed in any meaningful way, you need to find which IPs actually have a “pulse” and which do not.
So how do you check for live systems in a targeted environment? It turns out that there are plenty of ways to accomplish this task. However, the commonly accepted ways of accomplishing this task are these:
- Wardialing
- Wardriving
- Pinging
- Port scanning
Each of these techniques provides information not obtainable by the other methods, or at least they don’t offer it as easily. Once you understand the differences, you should have a much better idea of how to deploy these methods in a penetration test.
Wardialing
The first type of scan is an old but useful one known as wardialing. Wardialing has existed in an almost unchanged state since the mid-1980s and has stayed around so long because it has proven to be a useful information-gathering tool. In practice, wardialing is extremely simple compared to the other forms of scanning in that it simply dials a block of phone numbers using a standard modem to locate systems that also have a modem attached and accept connections. On the surface, this type of technique seems to be a digital dinosaur, but don’t let that fool you—the technique is still very useful. Understand that modems are still used for a number of reasons, including the low cost of the technology, ease of use, and the availability of phone lines, which are pretty much everywhere. Modems are still so commonly used that an attacker can easily dial a block of phone numbers in just about any town and locate a good number of computers still using dial-up to attach to the outside world.
Once you find a modem and get a response, the question becomes what to do with that information. To answer that, you need to know what devices modems are commonly attached to in the modern world. Private branch exchanges (PBXs) often have modems attached (the nondigital ones), which can provide a good opportunity for mischief on behalf of the attacking party. Other devices that sometimes have modems attached are firewalls, routers, and fax machines. If an attacker dials into a firewall and gains access, an environment can quickly become unprotected.
Something to consider when an attacker gains access to a system is that they may be using it as a pivot point. A pivot point is a compromised system that is then used to target other systems that may be deeper in the targeted environment. In the case of systems such as those mentioned here, it is possible that an attacker could gain access to the device or system and start committing further aggressive actions.
A number of wardialing programs have been created over the years. Here are three of the best-known ones:
ToneLoc A wardialing program that looks for dial tones by randomly dialing numbers or dialing within a range. It can also look for a carrier frequency of a modem or fax. ToneLoc uses an input file that contains the area codes and number ranges you want it to dial.
THC-SCAN A DOS-based program that can use a modem to dial ranges of numbers in search of a carrier frequency from a modem or fax.
NIKSUN’s PhoneSweep One of the few commercial options available in the wardialing market.
Wardialing still works as a valid penetration method into an organization for several reasons, but let’s focus on one of the bigger reasons: the lack of attention or respect these devices get. You may see wardialing or modems as ancient technology, conjuring mental images of slow, screeching connections and dial-up services such as AOL and CompuServe. Although these ancient images are valid, don’t let them lull you into a false sense of security. In today’s corporate world, it is not uncommon to find these devices not only present but in many cases completely unmonitored or even unrecorded, meaning they are off the radar. In many cases, modems exist within a given environment for years until someone in accounting asks why the company is paying for a dial-up connection or who a certain phone number is assigned to.
Using Ping
A more familiar tool to perform scanning is ping. Ping is a utility that can be used to determine network connectivity by determining if a remote host is up or down. While a very simple utility, it is perfect for performing the initial scanning process.
Ping works by using an Internet Control Message Protocol (ICMP) message, which is why this technique is also called ICMP scanning. The process works by using one system to send an ICMP echo request to another system; if that system is live, it will send back an ICMP echo reply. Once this reply is received, the system is confirmed to be up, or live. Pinging is useful because it can tell you not only whether a system is up but also the speed of the packets from one host to another and information about time to live (TTL).
To use the ping command in Windows, enter the following at the command prompt:
ping <target IP>
or
ping <target hostname>
In most Linux versions, the command is essentially the same; however, it will repeatedly ping the remote client until you use Ctrl+C to terminate the process.
There is another way to ping a remote system that you should be aware of: performing a ping using nmap. At the Windows or Linux command prompt, enter the following:
nmap –sn –v <target IP address>
If the command successfully finds a live host, it returns a message stating that the IP address is up and provides the media access control (MAC) address and the network card vendor (if it is able to determine this last piece of information).
Up one level from the ICMP scan is the ping sweep, so named because you use this technique to scan or sweep a range of IPs looking for live hosts. Once again nmap proves helpful by allowing you to perform a quick scan. To do this with nmap, simply enter the following command:
nmap –sP –PE –PA<port numbers> <starting IP/ending IP>
Here’s an example, with port numbers and IP addresses specified:
nmap –sP –PE –PA21,23,80,3389 <192.168.10.1-50>
Ping sweeps are incredibly effective in that they can build an inventory of systems quickly; however, there are some potential drawbacks. First, you must overcome the fact that many network administrators block ping at the firewall, so pinging hosts from outside the network is impossible without extra effort. Second, an intrusion-detection system (IDS) or intrusion-prevention system (IPS) will often be present on larger networks or in enterprise environments, and these systems will alert the system owner and/or shut your scan down. Finally, due to the way the scan works, there really isn’t any capability in the scan to detect systems that are down; in such cases the ping will hang for a few moments before informing you that it cannot reach a host.
Hping3: the Heavy Artillery
Ping is not the only game in town. In fact, it is limited somewhat, and therefore a more advanced tool such as hping3 can be useful. In a nutshell, hping is a command-line-based TCP/IP packet crafter. This means it not only has the ability to send packets across a network but also allows for the creation of customized packets that can be used to assess the behavior of a remote host. hping isn’t only able to send ICMP echo requests like ping; rather it supports TCP, UDP, ICMP, and RAW-IP protocols, has a traceroute mode, and has the ability to transfer files.
While we will examine hping again in coming chapters, let’s take a look at a couple of its features that will prove useful at this point.
First, let’s see how we can make hping3 act like ping. The following command will cause the utility to transmit an ICMP request and receive a reply:
hping3 -1 <domain name>
Next, let’s check to see if there is a firewall blocking ping requests. We can do this by attempting to get a packet with an ACK flag sent to the target. In this example the switches used are -A for ACK, -V for verbose, -p followed by a target port number, and -s for the port on the source computer where the packet will originate. In this example port 80 on the target and port 5050 on the attacker system are used:
hping3 -c 1 -V -p 80 -s 5050 -A <domain name>
If this command receives a reply, then the system is alive and the port target is open. However, if no response is returned, there may very well be a firewall in between the scanner and the target.
Once you have found a live system, you can perform a port scan to check for open ports.
Checking the Status of Ports
Once you have located live systems on a network, it is time to take a closer look at these hosts to determine if there are any open ports that may prove useful. Essentially what we are doing when we zoom in on each live host is “rattling the doorknobs” on each to see what ports are open and closed. And while we may be seeing which are open and closed, we are not yet at the point where we are “turning the handle and peeking inside”; that is still ahead.
Before we start to perform some port scans, let’s take a moment or two to review some fundamentals. Back in Chapter 2 you learned about TCP and UDP and their context within the TCP/IP suite of protocols. If you recall, TCP is a connection-oriented protocol and UDP is connectionless in nature. Knowing how these protocols function and the significance of each will make fine-tuning and choosing the correct scan that much easier for you and definitely more productive to boot.
Starting things off is the process used exclusively by TCP known as the three-way handshake.
The three-way handshake is performed when you’re trying to establish a TCP connection to a system or, specifically, a port on the system. The handshake establishes a successful and reliable connection between two systems. The process involves three steps, as shown in Figure 5.1.
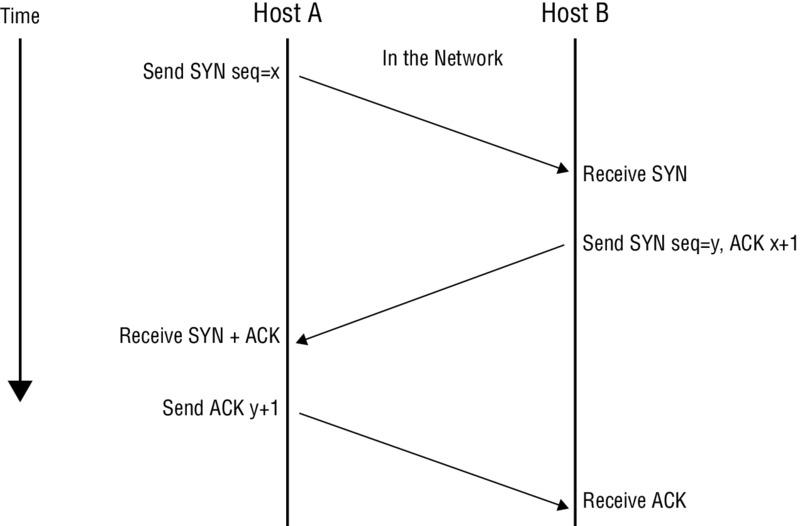
Figure 5.1 The three-way handshake
Let’s take a closer look at the steps to see what is occurring:
- Host A sends a SYN packet to Host B as a request to establish a connection.
- Host B responds with a SYN-ACK as an acknowledgment of the request.
- Host A responds with an ACK, which serves to fully establish the connection.
If these steps complete without error, then the TCP connection is established successfully and information flow can occur.
If you were paying close attention to Figure 5.1 and the steps listed, you noticed the inclusion of what seemed like acronyms in the form of SYN and ACK. SYN and ACK are two of the indicators on a packet known as flags. These flags are essentially bits that are set to on or off in the header of a TCP packet. The receiving system will use these flags to determine how to process that specific packet. In a TCP packet it is possible to have every packet turned on or every packet turned off, with any variation of on and off allowed in most cases. This basic information is vital to you from this point forward because it will have a direct impact on how useful your scanning process actually is when all is said and done. Table 5.1 explains TCP flags.
Table 5.1 TCP flags
| Flag | Use |
| SYN | Initiates a connection between two hosts to facilitate communication. |
| ACK | Acknowledges the receipt of a packet of information. |
| URG | Indicates that the data contained in the packet is urgent and should be processed immediately. |
| PSH | Instructs the sending system to send all buffered data immediately. |
| FIN | Tells the remote system that no more information will be sent. In essence, this gracefully closes a connection. |
| RST | Resets a connection. |
This information can be helpful in many areas, especially when you are using a packet crafter. A packet crafter is a utility designed to create a packet with the flags you specify set to on or off. You can use it to create custom packets with the flags set in different ways in order to observe how a targeted system responds to the packet and what types of results are returned.
Among the simplest utilities you can use are hping2 and hping3. Both of these utilities are command-line only and offer a tremendous advantage in creating custom packets for testing. Using hping3, for example, it is possible to generate many different types of packets and send them to a target:
Create an ACK packet and send it to port 80 on the victim:
hping3 –A <target IP address> -p 80
Create a SYN scan against different ports on a victim:
hping3 -8 50-56 –S <target IP address> -v
Create a packet with FIN, URG, and PSH flags set and send it to port 80 on the victim:
hping3 –F –P -U <target IP address> -p 80
The Family Tree of Scans
With a good and hopefully firm grasp of flags and their significance in hand, we can now move forward to analyzing and attempting some of the different types of scans. Now that you have seen the various types of flags and how a packet crafter works in the form of hping2 and hping3, let’s see how this information comes together.
Full-Open Scan
The first type of scan is known as a full-open scan, which is a fancy way of saying that the systems involved initiated and completed the three-way handshake. The advantage of a full-open scan is that you have positive feedback that the host is up and the connection is complete. In many cases new penetration testers will attempt a full-open scan against a target either on purpose or accidentally; this can be bad and even fatal to your test because it can be detected and logged by firewalls and an IDS.
This process will complete the handshake for open ports, but what does it do for closed ports? When a closed port is encountered, the sending party will transmit an ACK packet to a specific port on the remote host; when this request encounters the closed port, an RST will be sent back, terminating the attempt.
In order to perform a full-open scan you must choose to perform a TCP Connect scan using the –sT switch, where the –s indicates the scan and the capital T states that the scan type is TCP Connect.
The command to execute this scan type is:
nmap –sT <ip address or range>
When this command is executed, the host will be scanned and a report returned. Keep in mind that when you perform this type of scan, it is very “noisy” and will show up in logs just waiting to be discovered. Use this scan sparingly when no other scan will work or is appropriate.
Stealth or Half-Open Scan
In this type of scan, the process is similar to the full-open scan with a major difference: It is less noisy than a full-open scan. Thus, this scan type is also sometimes known as stealth scanning or by the oft-used name SYN scan.
A half-open scan works by the same process as the full-open scan all the way up to the end, where it differs in regard to the final step of the three-way handshake. Whereas the full-open scan completes the three-way handshake with a final ACK message in response to a SYN-ACK, the half-open does not. In a half-open scan the scanning system responds with an RST message to the SYN-ACK message. This has the effect of informing the target that the requesting party does not want to establish a connection. The result is that there is a lot less to log, and since the final ACK packet was never sent, an open port has still been confirmed, but no active connection has been made.
However, if a port is closed rather than open, the three-way handshake starts with the attacker sending a SYN, only to have the victim respond with an RST packet indicating that the port is closed and not taking connections. Figure 5.2 illustrates this scanning technique for open and closed ports.
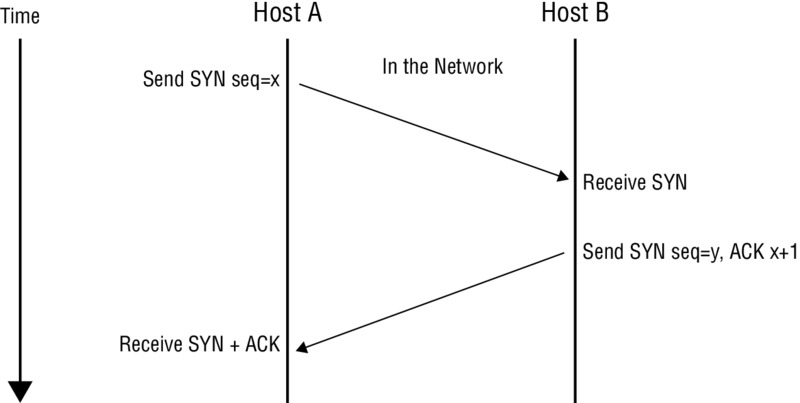
Figure 5.2 Half-open scan against closed and open ports
As stated previously, the main advantage of this particular type of scanning is that it is less likely to trigger detection mechanisms or end up being logged, but the downside is that it is a little less reliable than a full-open scan, because confirmation is not received during this process due to the lack of the final ACK.
To perform this type of scan in nmap use the syntax:
nmap –sS <ip address or range>
Xmas Tree Scan
This next scan gets its name from the phrase “lit up like a Christmas (Xmas) tree,” meaning that numerous flags are set. In this type of scan, multiple flags are activated. In other words, a single packet is sent to the client with URG, PSH, and FIN all set to on. Having all the flags set creates an illogical or illegal combination, and the receiving system has to determine what to do when this occurs. In most modern systems this simply means that the packet is ignored or dropped, but on some systems the lack of response tells you a port is open, whereas a single RST packet tells you the port is closed. Figure 5.3 shows this process.
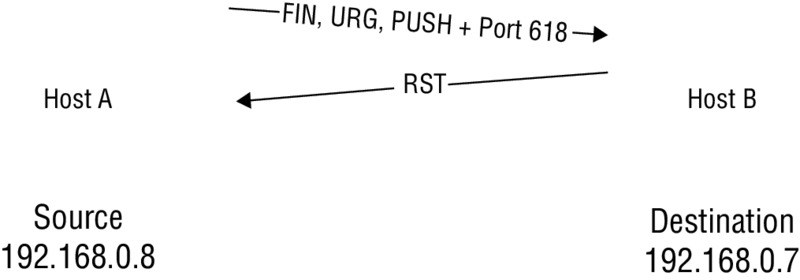
Figure 5.3 Xmas tree scan
To perform a Xmas tree scan with nmap, enter the following at the command line:
nmap –sX –v <target IP address>
So why do systems not respond to Xmas tree packets if the port is open but do respond if it is closed? Since the combination of flags is essentially bogus, there really is no adequate response. However, in the case of a closed port, a connection attempt is still just that, an attempt, and thus the closed port will respond to indicate that connections of any type aren’t allowed.
One thing to keep in mind with Xmas tree scans is that they don’t always illicit the same response from all targets. The response can vary just a little or a lot from operating system to operating system. The cause of this variance is that the developers of operating systems and devices do not always strictly adhere to the Internet Protocol standard (RFC 791 or 793) that defines the expected behavior of the protocol. Since many vendors choose to adjust their interpretation a bit here and there, the responses can be different when closely analyzed. The benefit of this is that this can reveal the specific OS in use on the target system.
In addition, an indicator that this type of scan is targeting your systems is that it consumes more processing power on the part of the target. Not to mention that not only does the increased processing power indicate something is amiss, but the fact that the packets should not exist under normal circumstances makes them suspect.
FIN Scan
In this type of scan, the attacker sends packets to the victim with the FIN flag set. The concept behind this type of scan is that SYN scans are still very visible (though not as visible as TCP connect scans); in order to obtain a lower profile, a packet with a FIN flag set can be used. This type of scanning technique is effective not only because it is less obvious, but also because it can reliably pass through firewalls without alteration and then right on toward the intended target. SYN packets, on the other hand, are likely to get higher levels of scrutiny when they encounter a firewall.
The result is somewhat similar to what happens in a Xmas tree scan. The victim’s response depends on whether the port is open or closed. Much like the Xmas tree scan, if an FIN is sent to an open port, there is no response, but if the port is closed, the victim returns an RST. Figure 5.4 illustrates this process.

Figure 5.4 An FIN scan against a closed port and an open port
An FIN scan in nmap can be performed by issuing the following command:
nmap –sF <target IP address>
NULL Scan
In this type of scan, the attacker sends frames to the victim with no flag set. The result is somewhat similar to what happens in an FIN scan. The victim’s response depends on whether the port is open or closed. Much like the FIN and Xmas tree scans, if no flags are set on a frame that is sent to an open port, there is no response, but if the port is closed, the victim returns an RST. Figure 5.5 illustrates this process.
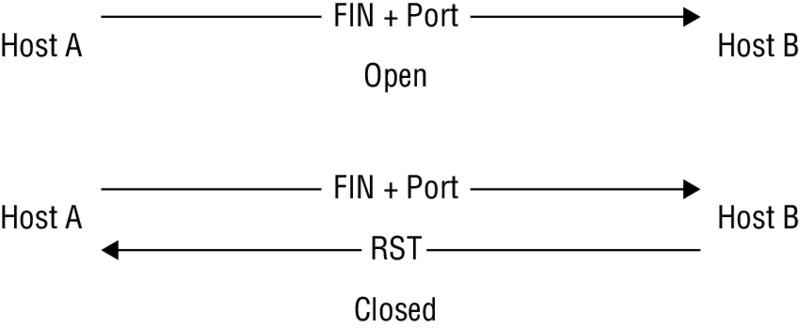
Figure 5.5 A NULL scan against a closed and an open port
In nmap, to perform a NULL scan issue the following command:
nmap –sN <target IP address>
In practice, when this scan is being performed it is relatively easy to detect when running. This ease of detection is primarily due to the fact that there is no reason for a TCP packet with no flags set to exist on the network. TCP packets need flags set in order for the receiver to determine what to do with the information received. All a defender needs to do to become aware when this type of scan is running is to configure their countermeasures to notify them when such a packet is encountered.
Idle Scanning
One type of scanning that is unique and very powerful is known as the idle scan. This type of scan is effective because of its high degree of stealthiness as compared to other scans. The way it achieves this ability to keep such a low profile is due to how it performs the scan.
An idle scan is known for its ability to hide the identity of the attacking party by not sending the packets from the actual attacking system. In practice this process is performed by bouncing the scan off another host (commonly called a zombie) and then on toward the target. If the victim of the scan investigates the activity generated by the process, they will trace the scan back not to the actual attacker but to the zombie system instead. Besides being extraordinarily stealthy, this scan permits discovery of IP-based trust relationships between machines.
While idle scanning is much more complex than any of the previously introduced scanning techniques, it is not incredibly difficult to understand in practice.
The scan depends on three basic points:
- One way to determine whether a TCP port is open is to send an SYN (session establishment) packet to the port. The target machine will respond with an SYN/ACK (session request acknowledgment) packet if the port is open, and an RST (reset) if the port is closed.
- A machine that receives an unsolicited SYN/ACK packet will respond with an RST. An unsolicited RST will be ignored.
- Every IP packet on the Internet has a fragment identification number (IP ID). Since many operating systems simply increment this number for each packet they send, probing for the IP ID can tell an attacker how many packets have been sent since the last probe.
It is through the application and combination of these properties that the attacking party can spoof their identity and cast blame on another system, which in this case is the zombie. To an outside observer, the zombie will look like the originator of the attack.
The Breakdown
An idle scan consists of three steps that would be repeated for each port to be scanned:
- Probe the zombie’s IP ID and record it.
- Forge a SYN packet from the zombie and send it to the desired port on the target. Depending on the port state, the target’s reaction may or may not cause the zombie’s IP ID to be incremented.
- Probe the zombie’s IP ID again. The target port state is then determined by comparing this new IP ID with the one recorded in step 1.
After this process, the zombie’s IP ID should have incremented by a value of either one or two. An increase of one indicates that the zombie hasn’t sent out any packets, except for its reply to the attacker’s probe. This lack of sent packets means that the port is not open (the target must have sent the zombie either an RST packet, which was ignored, or nothing at all). An increase of two indicates that the zombie sent out a packet between the two probes. This extra packet usually means that the port is open (the target presumably sent the zombie an SYN/ACK packet in response to the forged SYN, which induced an RST packet from the zombie). Increases larger than two usually signify a bad zombie host. It might not have predictable IP ID numbers, or it might be engaged in communication unrelated to the idle scan.
Even though what happens with a closed port is slightly different from what happens with a filtered port, the attacker measures the same result in both cases, namely, an IP ID increase of one. Therefore, it is not possible for the idle scan to distinguish between closed and filtered ports. When nmap records an IP ID increase of one, it marks the port closed|filtered.
ACK Scanning
Up to this point we have mentioned that some scans can be detected or even blocked, so what should you do if you encounter a situation where this happens? We will look at the blocking issue first.
In many cases when a scan is blocked from reaching a target, a firewall may be present and a specific type at that. If a firewall is preventing your scans (such as those mentioned here), it is generally indicative of a stateful firewall being present.
Stateful firewalls—and those that perform stateful packet inspection (SPI)—are those that track the state of all network connections transiting the device. The firewall is designed to tell the difference between legitimate connections and those that are not. Any packets not matching a known active connection will be dropped, while those that do match will be allowed to pass.
ACK scanning is designed to test for the presence of SPI based on how the flags and SPI function. In normal operation an ACK packet would be sent only in response to a connection being established or in response to some existing TCP connection. This means that if an ACK packet is sent to a target and no connection currently exists between the scanner and the target, then it shouldn’t be present.
When this scan is performed and an ACK is sent to a target, the results will tell us what we want to know (hopefully). When an ACK is able to make it all the way to its target, an RST packet will be returned whether the port is open or closed (it is because an RST is returned for both open and closed ports that this scan is not used to detect the actual status of ports). It is also possible that if an ACK reaches its target, then a scanner such as nmap will return a message stating the port is unfiltered. If the target cannot be reached by the ACK message, then no response will be returned at all, indicating that it did not reach its intended target. In the case of the ACK not reaching its target, the other potential response may come in the form of an ICMP error message (such as type 3, code 0, 1, 2, 3, 9, 10, or 13) or is labeled “filtered.”
When a Scan Is Blocked
So what do you do as a pentester if packet filters, firewalls, and other devices start to pick up evidence of your attack? Many methods are available to evade or minimize the risk of detection when scanning. For example, fragmenting works by breaking a packet into multiple pieces with the goal of preventing detection devices from seeing what the original unfragmented packet intends to do. Think of it as taking a large picture and cutting it into little pieces like a jigsaw puzzle. If you don’t know what the original picture looks like, you have to reassemble a bunch of pieces to figure it out.
In nmap, if you wish to fragment a packet, you can do so by using the –f switch as follows:
nmap –sS –T4 –A –f –v <target IP address>
Other tools that can perform fragmenting are fragtest and fragroute. These last two are command-line-only tools, but they perform the same function as the other fragmenting tools.
UDP Scanning
While TCP-based scans offer their own features and capabilities, there are also other types of scans that you can do, namely UDP-based scans. If you recall from Chapter 2, “System Fundamentals,” UDP is a connectionless protocol, unlike TCP, which is connection oriented. Whereas TCP is designed to react to transmissions depending on the way flags in a packet are sent, UDP is not; in fact, UDP does not even have flags. This difference means that a change of strategy and thinking is required.
To adjust your strategy, think of how UDP works in relation to ports. In TCP, many different responses can occur based on numerous factors. In UDP, once a packet leaves a system, that’s the end of things, or so we have been taught. In reality, when a UDP packet is sent, no response is returned if the port on the target to which it is being sent is open. However, if the port is closed, a response will be returned in the form of a “Port Unreachable” message. Table 5.2 shows the different responses.
Table 5.2 Results of UDP scanning against closed and open ports
| Port status | Result |
| Open | No response |
| Closed | ICMP “Port Unreachable” message returned |
Note the differences in the results as opposed to TCP scanning. With TCP scanning you get different responses than you see here, but the connectionless UDP does not react the same way to probe requests.
OS Fingerprinting
So now that you have done some scans and noted the information that was returned (you are documenting this stuff, right?), we can move to a new task, which is to attempt to identify systems a bit better. Behind those open and closed ports is an operating system, and we now want to confirm the nature of the operating system by performing some fingerprinting.
This process is called fingerprinting for a very good reason: It tries to identify an operating system by the unique “fingerprints” that it returns. Those fingerprints (much like those on humans) can be compared to a database of known fingerprints to determine with varying degrees of accuracy what operating system the target is running. In practice there’s enough information to clearly show what a specific system is. We just have to know how to look for these unique details and determine what they mean.
First, know that there are two types of fingerprinting: passive and active. Table 5.3 compares the two.
Table 5.3 Active vs. passive fingerprinting
| Active | Passive | |
| How it works | Uses specially crafted packets. | Uses sniffing techniques to capture packets coming from a system. |
| Analysis | Responses are compared to a database of known responses. | Responses are analyzed, looking for details of the OS. |
| Chance of detection | High, because it introduces traffic onto the network. | Low, because sniffing does not introduce traffic onto the network. |
To make this easier, just know that all fingerprinting techniques are based on detecting the subtle differences in packets generated by different operating systems.
Common techniques are based on analyzing the following:
- IP TTL values
- IP ID values
- TCP Window size
- TCP options (generally, in TCP SYN and SYN+ACK packets)
- DHCP requests
- ICMP requests
- HTTP packets (generally, the User-Agent field)
- Running services
- Open port patterns
Active Fingerprinting with Nmap
One of the easiest ways to detect a remote OS is to use nmap. nmap contains many features, and OS detection happens to be a useful capability to help with this part of the process. To perform this fingerprinting nmap fires a range of TCP and UDP packets at the target system and then looks for responses to be returned. The responses are analyzed in depth to look for clues as to the nature of the OS. Once the range of tests has been completed, nmap compares the findings to the database that ships with the product to look for matches. Once a match is found, it presents the results to the user. These results will contain as much information as can be extracted in addition to the OS itself, such as uptime and information about whether the system is a computer or a hardware device.
To perform OS detection with nmap perform the following:
nmap -O <ip address>
This command yields results such as the following. For illustrative purposes, this scan has been performed against a hardware device:
Device type: WAP|general purpose|router|printer|broadband router Running (JUST GUESSING) : Linksys Linux 2.4.X (95%), Linux 2.4.X|2.6.X (94%), MikroTik RouterOS 3.X (92%), Lexmark embedded (90%), Enterasys embedded (89%), D-Link Linux 2.4.X (89%), Netgear Linux 2.4.X (89%) Aggressive OS guesses: OpenWrt White Russian 0.9 (Linux 2.4.30) (95%), OpenWrt 0.9 - 7.09 (Linux 2.4.30 - 2.4.34) (94%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (94%), Linux 2.4.21 - 2.4.31 (likely embedded) (92%), Linux 2.6.15 - 2.6.23 (embedded) (92%), Linux 2.6.15 - 2.6.24 (92%), MikroTik RouterOS 3.0beta5 (92%), MikroTik RouterOS 3.17 (92%), Linux 2.6.24 (91%), Linux 2.6.22 (90%)
Note how nmap not only guesses the OS; it even ranks the possibilities in decreasing order of confidence. Also note that the results specifically call out the device as well.
Passive Fingerprinting an OS
In order to perform a passive analysis of an OS, a change in strategy is required, which means closer analysis of the subtle variations in network traffic observed. Among the many methods is the inspection of the initial time to live (TTL) value in the header of a packet. Another item that can be analyzed in the header of a packet is the window size used in TCP packets during the SYN and SYN+ACK steps of the three-way handshake.
Table 5.4 shows some typical initial TTL values and window sizes of common operating systems.
Table 5.4 Initial values for common OS versions
| Operating System | IP Initial TTL | TCP Window Size |
| Linux | 64 | 5840 |
| Google customized Linux | 64 | 5720 |
| FreeBSD | 64 | 65535 |
| Windows XP | 128 | 65535 |
| Windows Vista, 7 and Server 2008 | 128 | 8192 |
| Cisco Router (iOS 12.4) | 255 | 4128 |
One Linux-based tool that is very effective at performing passive fingerprinting is p0f. This tool is used to passively analyze network traffic and display the information regarding the operating systems that are passing information. Since the utility doesn’t directly target a host and only observes traffic, it is highly stealthy.
Because TCP traffic can be identified by different combination of flags and other properties, when packets are intercepted by p0f they are compared against a database of known attributes, which will determine what operating system sent them.
In order to use p0f you will need access to the Linux operating system. While there are many versions of Linux available, the demos in this book assume that you are using Kali Linux version 2.0. Any Linux utility in this book can be loaded on the majority of other versions, however.
Now that you have seen how p0f works in practice, you can try it without using a web browser. Also try using other tools or simply connecting to a network share or other resource. You will see the same type of activity from p0f in every case.
Banner Grabbing
With operating system information in hand as well as data about open ports, we have the stage set to dig a little deeper. What we can engage in is known as banner grabbing. Banner grabbing is designed to determine information about the services running on a system and is extremely useful to ethical hackers during their assessment process. Typically, the technique is undertaken using Telnet to retrieve banner information about the target that reveals the nature of the service.
A banner is what a service returns to the requesting program to give information about the service itself. Information that the banner reveals can be varied, but in the case of HTTP it can include the type of server software, version number, when it was modified last, and similar information.
In many cases Telnet is the client of choice in retrieving this information. Although there are other tools (a few of which we’ll discuss in a moment), we’ll focus on Telnet because it is the most common and the simplest. Most operating systems come with the ability to establish Telnet sessions, so that is one of the primary ways that banner grabbing is performed. Whether Telnet or another program is used, banners are grabbed by connecting to a host and then sending a request to a port that is associated with a particular service, such as port 80 for HTTP.
So how do you use Telnet to grab a banner from a system? Use the following command to open a Telnet connection to a remote client to pull the services banner:
telnet <ip address>:<port> HEAD / HTTP/1.1
To retrieve the document as well as the headers, use GET instead of HEAD. If you want the root document, use GET / HTTP/1.1 (or HEAD / HTTP/1.1).
HTTP/1.1 200 OK Date: Feb, 22 Jan 2015 22:13:05 GMT Server: Apache/1.3.12-Turbo Connection: close Content-Type: text/html
This process is started by using Telnet with the following syntax:
telnet <target IP address or hostname> 80 head/http/1.0
Here’s an example:
telnet www.someexamplesite.com 80 head/http/1.0
Figure 5.6 shows the results of a banner grab.
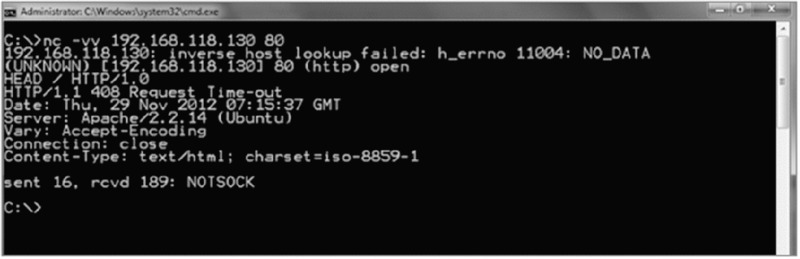
Figure 5.6 Results of a banner grab
If you look closely at Figure 5.6, you will notice that the line marked Server contains information on the type of server itself. You’ll find this information useful in targeting your attack.
Telnet is not the only way to gather this information, but it is the most basic and straightforward method available. Here are some other tools that you should take a moment to examine:
Netcraft This is an online tool designed to gather information about servers and web servers. You saw this tool back in the footprinting phase, but it is also useful here.
Xprobe This is a Linux utility that can retrieve information about a system and provide it to the collector.
p0f This utility is available on the Linux platform; it analyzes the traffic passing back and forth from client to server. It provides real-time analysis of traffic that can be viewed onscreen or saved to a file for later analysis.
Maltego This software is available on both Linux and Windows, and provides the ability to not only gather information but also to visualize the relationships between each item. This software has the ability to view web server information as well as the technology that a website relies on to run.
Countermeasures
So how can you counter the grabbing of banners from exposed resources? There are a few options available that you can deploy.
First, disable or change the banner that the server is exposing. Since we have been looking at various services, it is worth noting that many can have their information changed. For example, in the case of Internet Information Server (IIS) it is possible to remove or alter the contents of the banner so the system does not appear to be the same to scans or banner grabs. Utilities such as IIS Lockdown, ServerMask, and others can remove this valuable information.
Second, it is possible to hide file extensions on systems such as web servers. The purpose of this technique is to hide the technology used to generate the web pages. Technologies such as ASP.NET and JavaServer Pages (JSP) can be readily identified by viewing their file extensions in the web browser. Removing this detail creates one more obstacle that an attacker must overcome to get into the inner workings of a server. Technologies such as PageXchanger for IIS are designed to assist in the removal of page extensions.
Vulnerability Scanning
So how do you find all the vulnerabilities that exist in an environment, especially with the ever-increasing complexity of technologies? Many techniques are available to help you, some of them manual or scripted in nature (many of which we have already discussed), but automated tools such as vulnerability scanners are also available.
Vulnerability scanners are a special type of automated utility designed to identify problems and holes in operating systems and applications. This is done by checking coding, ports, variables, banners, and many other potential problem areas. A vulnerability scanner is intended to be used by organizations to find out if there is a possibility of being successfully attacked and what needs to be fixed to remove the vulnerability. Although vulnerability scanners are used to check software applications, they also can check entire operating environments, including networks and virtual machines.
Vulnerability scanners can be a great asset, but there are drawbacks. The scanners are designed to look for a specific group of known issues, and if they don’t find those issues, then they may leave the false impression that there are no problems. Therefore, it is wise to verify the results of these applications using all the techniques discussed in this text.
Vulnerability scanners are mentioned here only to talk about them in context with the other scanning techniques. Much like nmap, there are popular vulnerability scanners in the form of Nessus, OpenVAS, Nexpose, Retina, and a few others.
Mapping the Network
Once you have ascertained the network environment and have figured out live IPs and services, you can start mapping the network. This phase is designed to help you fully visualize the network environment and start getting a clearer picture of what the network looks like. With this information in hand, you can find any holes and deficiencies that can be exploited.
Network mappers combine the scanning and sweeping techniques explained in this chapter to build a complete picture. Keep in mind that mappers can easily reveal the presence of the ethical hacker on the network due to the traffic that they generate, so mappers should be used sparingly to avoid detection. Figure 5.7 shows the results of a network mapper in action.
![Screenshot of window for [D:\work\LANState\Maps\demobest.Ism] - LANState Pro has several connections of computers connected to hubs in start topology.](images/ec05f007.jpg)
Figure 5.7 A network map built by a network-mapping software package
Using Proxies
The last topic that needs to be discussed as far as successful scanning is concerned is the use of proxies. A proxy is a system acting as a stand-in between the scanner and the target. The proxy acts as an agent for the scanning party, thus providing a degree of anonymity for the scanning party. Proxy servers can perform several functions, including these:
- Filtering traffic in and out of the network
- Anonymizing web traffic
- Providing a layer of protection between the outside world and the internal network
Proxy servers are typically used to maintain anonymity, which helps scanners. A vigilant network administrator who is checking logs and systems will see the agent or proxy but not the actual scanning party behind the proxy.
Setting up a proxy is easy and can be accomplished in a number of ways, depending on the situation.
Setting a Web Browser to Use a Proxy
Use the following steps to set your browser to use a proxy:
- Log on to www.whatismyip.com and write down your current IP address. Or you can use ipconfig to gain this information.
- Enter proxies in your favorite search engine to find a site providing a list of publicly available proxies. Each proxy in the list consists of an IP address and a port.
- Randomly select a proxy from the list and write down its IP address and port number.
- In your browser, find the proxy settings and manually configure the browser to use the information from step 3.
- Check out www.whatismyip.com again to see how the proxy now hides your actual IP address.
You can configure proxies in other web browsers the same way.
Other proxy options are available to you as well that may be useful in certain situations. An important one is The Onion Router (Tor). Tor is an older technology, but it is still effective and widely used. To better understand this technology, read the following description from the Tor Project’s website (https://www.torproject.org/about/overview.html.en):
Tor is a network of virtual tunnels that allows people and groups to improve their privacy and security on the Internet. It also enables software developers to create new communication tools with built-in privacy features. Tor provides the foundation for a range of applications that allow organizations and individuals to share information over public networks without compromising their privacy.
So how does it work? Again, let’s let the developer describe the process (from the same website):
To create a private network pathway with Tor, the user’s software or client incrementally builds a circuit of encrypted connections through relays on the network. The circuit is extended one hop at a time, and each relay along the way knows only which relay gave it data and which relay it is giving data to. No individual relay ever knows the complete path that a data packet has taken. The client negotiates a separate set of encryption keys for each hop along the circuit to ensure that each hop can’t trace these connections as they pass through.
So you see that TOR provides you with a good amount of protection as well as the ability to obscure or encrypt traffic, making it much more difficult to detect.
One more software product that may prove useful at hiding some or all of your presence during the information gathering process is Psiphon. This software relies on VPN technologies to hide the activity of the user from outside parties.
Summary
Acting on the information gathered from the footprinting phase, you can perform network scanning with a much more targeted and purposeful strategy. Scanning represents an aggressive approach to gaining information about a system, because you are interacting directly with a target. You are probing the network and systems looking to see what you can find. Vulnerability scans, network mapping, port scans, and OS fingerprinting give you insight into the system and tell you the potential paths you can take with your testing.
Exam Essentials
Remember the basic concept of scanning. Scanning is designed to reveal the nature of system networks as well as the vulnerabilities that are present in the environment.
Understand the targets. Know which resources can be targeted. Know what is present and start making plans on how to attack.
Know the vulnerabilities. Understand that vulnerabilities change based on the operating system, network design, and other factors present in an environment.
Understand the different scanning types. Know the difference between the various scan types and the strengths and weaknesses of each. Not all scans are created equal, nor are they meant to perform the same task.
Know when to use each scan. Each scan has its own benefits and drawbacks that make it a good or bad choice for a given situation. Know when to use each.
Know the preventive measures. Know the preventive measures available and the actions each one takes to prevent the attack.
Know your tools and terms. The CEH exam is drenched with terms and tool names; in the case of scanners, there are quite a few available. However, the one you should be most familiar with and have experience using is nmap. Familiarize yourself with the switches and techniques used to operate this scanner prior to taking the exam.
Review Questions
-
Which of the following is used for banner grabbing?
- Telnet
- FTP
- SSH
- Wireshark
-
Which of the following is used for identifying a web server OS?
- Telnet
- Netcraft
- Fragroute
- Wireshark
-
Which of the following is used to perform customized network scans?
- Nessus
- Wireshark
- AirPcap
- nmap
-
Which of the following is not a flag on a packet?
- URG
- PSH
- RST
- END
-
An SYN attack uses which protocol?
- TCP
- UDP
- HTTP
- Telnet
-
Which of the following types of attack has no flags set?
- SYN
- NULL
- Xmas tree
- FIN
-
What is missing from a half-open scan?
- SYN
- ACK
- SYN-ACK
- FIN
-
During an FIN scan, what indicates that a port is closed?
- No return response
- RST
- ACK
- SYN
-
During a Xmas tree scan what indicates a port is closed?
- No return response
- RST
- ACK
- SYN
-
What is the three-way handshake?
- The opening sequence of a TCP connection
- A type of half-open scan
- A Xmas tree scan
- Part of a UDP scan
-
A full-open scan means that the three-way handshake has been completed. What is the difference between this and a half-open scan?
- A half-open uses TCP.
- A half-open uses UDP.
- A half-open does not include the final ACK.
- A half-open includes the final ACK.
-
What is the sequence of the three-way handshake?
- SYN, SYN-ACK, ACK
- SYN, SYN-ACK
- SYN, ACK, SYN-ACK
- SYN, ACK, ACK
-
What is an ICMP echo scan?
- A ping sweep
- A SYN scan
- A Xmas tree scan
- Part of a UDP scan
-
Which best describes a vulnerability scan?
- A way to find open ports
- A way to diagram a network
- A proxy attack
- A way to automate the discovery of vulnerabilities
-
What is the purpose of a proxy?
- To assist in scanning
- To perform a scan
- To keep a scan hidden
- To automate the discovery of vulnerabilities
-
What is Tor used for?
- To hide web browsing
- To hide the process of scanning
- To automate scanning
- To hide the banner on a system
-
Why would you need to use a proxy to perform scanning?
- To enhance anonymity
- To fool firewalls
- Perform half-open scans
- To perform full-open scans
-
A vulnerability scan is a good way to do what?
- Find open ports
- Find weaknesses
- Find operating systems
- Identify hardware
-
A banner can do what?
- Identify an OS
- Help during scanning
- Identify weaknesses
- Identify a service
-
nmap is required to perform what type of scan?
- Port scan
- Vulnerability scan
- Service scan
- Threat scan